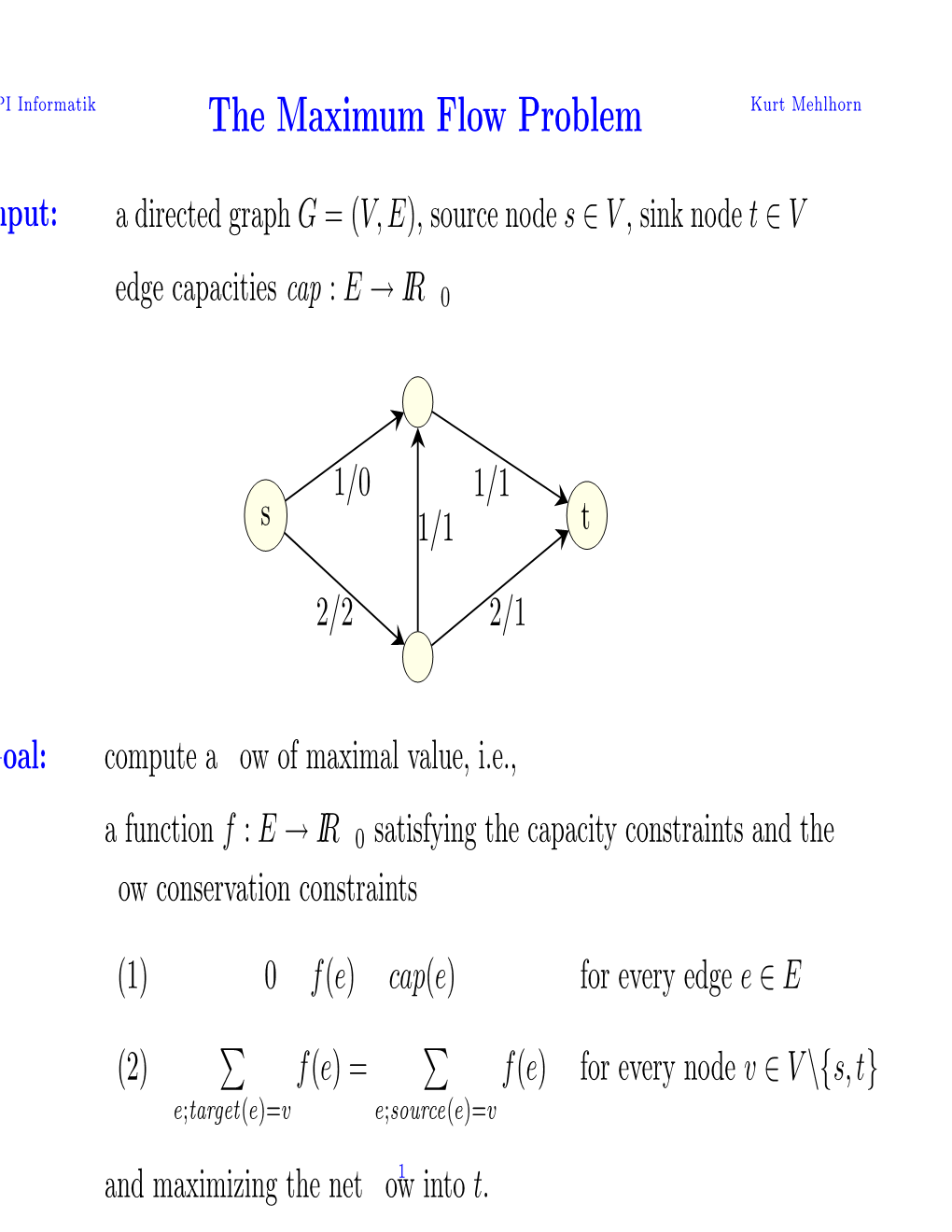
The Maximum Flow Problem Kurt Mehlhorn Nput: � a Directed Graph G =(V,E), Source Node S ∈ V , Sink Node T ∈ V
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

‣ Max-Flow and Min-Cut Problems ‣ Ford–Fulkerson Algorithm ‣ Max
7. NETWORK FLOW I ‣ max-flow and min-cut problems ‣ Ford–Fulkerson algorithm ‣ max-flow min-cut theorem ‣ capacity-scaling algorithm ‣ shortest augmenting paths ‣ Dinitz’ algorithm ‣ simple unit-capacity networks Lecture slides by Kevin Wayne Copyright © 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos Last updated on 1/14/20 2:18 PM 7. NETWORK FLOW I ‣ max-flow and min-cut problems ‣ Ford–Fulkerson algorithm ‣ max-flow min-cut theorem ‣ capacity-scaling algorithm ‣ shortest augmenting paths ‣ Dinitz’ algorithm ‣ simple unit-capacity networks SECTION 7.1 Flow network A flow network is a tuple G = (V, E, s, t, c). ・Digraph (V, E) with source s ∈ V and sink t ∈ V. Capacity c(e) ≥ 0 for each e ∈ E. ・ assume all nodes are reachable from s Intuition. Material flowing through a transportation network; material originates at source and is sent to sink. capacity 9 4 15 15 10 10 s 5 8 10 t 15 4 6 15 10 16 3 Minimum-cut problem Def. An st-cut (cut) is a partition (A, B) of the nodes with s ∈ A and t ∈ B. Def. Its capacity is the sum of the capacities of the edges from A to B. cap(A, B)= c(e) e A 10 s 5 t 15 capacity = 10 + 5 + 15 = 30 4 Minimum-cut problem Def. An st-cut (cut) is a partition (A, B) of the nodes with s ∈ A and t ∈ B. Def. Its capacity is the sum of the capacities of the edges from A to B. cap(A, B)= c(e) e A 10 s 8 t don’t include edges from B to A 16 capacity = 10 + 8 + 16 = 34 5 Minimum-cut problem Def. -

Network Algorithms: Maximum Flow
Maximum flow Algorithms and Networks Hans Bodlaender Teacher • 2nd Teacher Algorithms and Networks • Hans Bodlaender • Room 503, Buys Ballot Gebouw • Schedule: – Mondays: Hans works in Eindhoven A&N: Maximum flow 2 This topic • Maximum flow problem (definition) • Variants (and why they are equivalent…) • Applications • Briefly: Ford-Fulkerson; min cut max flow theorem • Preflow push algorithm • (Lift to front algorithm) A&N: Maximum flow 3 1 The problem Problem Variants in notation, e.g.: • Directed graph G=(V,E) Write f(u,v) = -f(v,u) • Source s ∈ V, sink t ∈ V. • Capacity c(e) ∈ Z+ for each e. • Flow: function f: E → N such that – For all e: f(e) ≤ c(e) – For all v, except s and t: flow into v equals flow out of v • Flow value: flow out of s • Question: find flow from s to t with maximum value A&N: Maximum flow 5 Maximum flow Algoritmiek • Ford-Fulkerson method – Possibly (not likely) exponential time – Edmonds-Karp version: O(nm2): augment over shortest path from s to t • Max Flow Min Cut Theorem • Improved algorithms: Preflow push; scaling • Applications • Variants of the maximum flow problem A&N: Maximum flow 6 1 Variants: Multiple sources and sinks Lower bounds Variant • Multiple sources, multiple sinks • Possible s1 t1 maximum flow out of certain G t sources or into s some sinks s k t • Models logistic r questions A&N: Maximum flow 8 Lower bounds on flow • Edges with minimum and maximum capacity – For all e: l(e) ≤ f(e) ≤ c(e) l(e) c(e) A&N: Maximum flow 9 Finding flows with lower bounds • If we have an algorithm for flows (without -

An Approach to Efficient Network Flow Algorithm for Solving Maximum Flow Problem
An Approach to Efficient Network Flow Algorithm for Solving Maximum Flow Problem Thesis submitted in partial fulfillment of the requirements for the award of degree of Master of Engineering in Computer Science & Engineering By: Chintan Jain (800832020) Under the supervision of: Dr. Deepak Garg Assistant Professor, CSED & Mrs. Shivani Goel Assistant Professor, CSED COMPUTER SCIENCE AND ENGINEERING DEPARTMENT THAPAR UNIVERSITY PATIALA – 147004 JUNE 2010 Abstract Network Flow Problems have always been among the best studied combinatorial optimization problems. These problems are central problems in operations research, computer science, and engineering and they arise in many real world applications. Flow networks are very useful to model real world problems like, current flowing through electrical networks, commodity flowing through pipes and so on. Maximum flow problem is the classical network flow problem. In this problem, the maximum flow which can be moved from the source to the sink is calculated without exceeding the maximum capacity. Once, the maximum flow problem is solved it can be used to solve other network flow problems also. Maximum flow problem is thoroughly studied in this thesis and the general algorithm is explained in detail to solve it. Then other network flow problems like, Minimam Cost Flow, Transshipment, Transportation, and Assignment problems are also briefly explained and shown that how they can be converted into maximum flow problem. The Ford-Fulkerson algorithm is the general algorithm which can solve all the network flow problems. The improvement of the Ford Fulkerson algorithm is Edmonds-Karp algorithm which uses BFS procedure instead of DFS to find an augmenting path. -

Faster Divergence Maximization for Faster Maximum Flow
Faster Divergence Maximization for Faster Maximum Flow Yang P. Liu Aaron Sidford Stanford University Stanford University [email protected] ∗ [email protected] † April 16, 2020 Abstract In this paper we provide an algorithm which given any m-edge n-vertex directed graph with integer capacities at most U computes a maximum s-t flow for any vertices s and t in m4/3+o(1)U 1/3 time. This improves upon the previous best running times of m11/8+o(1)U 1/4 (Liu Sidford 2019), O(m√n log U) (Lee Sidford 2014), and O(mn) (Orlin 2013) when the graph is not too dense or has large capacities. To achieve the resultse this paper we build upon previous algorithmic approaches to maxi- mum flow based on interior point methods (IPMs). In particular, we overcome a key bottleneck of previous advances in IPMs for maxflow (Mądry 2013, Mądry 2016, Liu Sidford 2019), which make progress by maximizing the energy of local ℓ2 norm minimizing electric flows. We gener- alize this approach and instead maximize the divergence of flows which minimize the Bregman divergence distance with respect to the weighted logarithmic barrier. This allows our algorithm to avoid dependencies on the ℓ4 norm that appear in other IPM frameworks (e.g. Cohen Mądry Sankowski Vladu 2017, Axiotis Mądry Vladu 2020). Further, we show that smoothed ℓ2-ℓp flows (Kyng, Peng, Sachdeva, Wang 2019), which we previously used to efficiently maximize energy (Liu Sidford 2019), can also be used to efficiently maximize divergence, thereby yielding our desired runtimes. We believe both this generalized view of energy maximization and generalized flow solvers we develop may be of further interest. -

Network Flow Algorithms Andrew V
Network Flow Algorithms Andrew V. Goldberg, Eva Tardos and Robert E. Tarjan 0. Introduction Network flow problems are central problems in operations research, computer Reprint from science, and engineering and they arise in many real world applications. Starting Algorithms and Combinatorics with early work in linear programming and spurred by the classic book of Volume 9 Ford and Fulkerson [26], the study of such problems has led to continuing Paths, Rows, and VLSI-Layout improvements in the efficiency of network flow algorithms. In spite of the long Volume Editors: history of this study, many substantial results have been obtained within'trie last B. Kone, L Lovasz, H J. Prb'mel. and A. Schrijver several years. In this survey we examine some of these recent developments and the ideas behind them. £ Sprmger-Verlag Berlin Heidelberg 1990 Printed in the United Slates of America Not for Sale We discuss the classical network flow problems, the maximum flow problem and the minimum-cost circulation problem, and a less standard problem, the generalized flow problem, sometimes called the problem of flows with losses and gains. The survey contains six chapters in addition to this introduction. Chapter 1 develops the terminology needed to discuss network flow problems. Chapter 2 discusses the maximum flow problem. Chapters 3, 4 and 5 discuss different aspects of the minimum-cost circulation problem, and Chapter 6 discusses the generalized flow problem. In the remainder of this introduction, we mention some of the history of network flow research, comment on some of the results to be presented in detail in later sections, and mention some results not covered in this survey. -

The Maxflow Problem and a Generalization to Simplicial
The Maxflow problem and a generalization to simplicial complexes Fabi´anLatorre 2012 arXiv:1212.1406v1 [math.CO] 5 Dec 2012 1 Acknowledgements Gracias a la cigue~nay quienes, no siendo su decisi´on,han tenido que vivir en mi tiempo y beber junto a m´ıy junto a Baco. Gracias por ser mis contempor´aneos,y que la casualidad nos haya llevado a conocernos y tal vez, ver un poco m´asque un aut´omatael uno en el otro. Gracias a mi asesor Mauricio Velasco a quien ha dedicado gran parte de su tiempo a gu´ıar este proyecto, a mis padres y hermanos. 2 CONTENTS CONTENTS Contents 1 Introduction 4 2 Preliminaries 5 2.1 Flow in a network . 5 2.2 The problem of MAXFLOW . 6 3 MAXFLOW algorithms 12 3.1 The Ford-Fulkerson algorithm . 12 3.2 The Goldberg-Tarjan algorithm . 14 3.3 Hochbaum's pseudoflow . 16 4 Applications 23 4.1 Hall's Marriage Theorem . 23 4.2 Counting disjoint chains in finite posets . 24 4.3 Image segmentation . 25 5 A Generalization of Maxflow 28 5.1 Preliminaries . 28 5.2 Higher Maxflow . 29 5.3 As an LP problem . 31 5.4 Further examples and conjectures . 32 3 1 INTRODUCTION 1 Introduction The problem of Maxflow was formulated by T.E. Harris in 1954 while studying the Soviet Union's railway network, under a military research program financed by RAND, Research and Development corporation. The research remain classified until 1999. The Maxflow problem is defined on a network which is a directed graph together with a real positive capacity function defined on the set of edges of the graph and two vertices s; t called the source and the sink. -

Graph Algorithms
Graph Algorithms PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Wed, 29 Aug 2012 18:41:05 UTC Contents Articles Introduction 1 Graph theory 1 Glossary of graph theory 8 Undirected graphs 19 Directed graphs 26 Directed acyclic graphs 28 Computer representations of graphs 32 Adjacency list 35 Adjacency matrix 37 Implicit graph 40 Graph exploration and vertex ordering 44 Depth-first search 44 Breadth-first search 49 Lexicographic breadth-first search 52 Iterative deepening depth-first search 54 Topological sorting 57 Application: Dependency graphs 60 Connectivity of undirected graphs 62 Connected components 62 Edge connectivity 64 Vertex connectivity 65 Menger's theorems on edge and vertex connectivity 66 Ear decomposition 67 Algorithms for 2-edge-connected components 70 Algorithms for 2-vertex-connected components 72 Algorithms for 3-vertex-connected components 73 Karger's algorithm for general vertex connectivity 76 Connectivity of directed graphs 82 Strongly connected components 82 Tarjan's strongly connected components algorithm 83 Path-based strong component algorithm 86 Kosaraju's strongly connected components algorithm 87 Application: 2-satisfiability 88 Shortest paths 101 Shortest path problem 101 Dijkstra's algorithm for single-source shortest paths with positive edge lengths 106 Bellman–Ford algorithm for single-source shortest paths allowing negative edge lengths 112 Johnson's algorithm for all-pairs shortest paths in sparse graphs 115 Floyd–Warshall algorithm -

Max Flow, Min Cut Two Very Rich Algorithmic Problems
Maximum Flow and Minimum Cut Max flow and min cut. Max Flow, Min Cut Two very rich algorithmic problems. Cornerstone problems in combinatorial optimization. Beautiful mathematical duality. Minimum cut Nontrivial applications / reductions. Network connectivity. Maximum flow Network reliability. Bipartite matching. Max-flow min-cut theorem Security of statistical data. Data mining. Ford-Fulkerson augmenting path algorithm Distributed computing. Open-pit mining. Edmonds-Karp heuristics Egalitarian stable matching. Airline scheduling. Bipartite matching Distributed computing. Image processing. Many many more . Project selection. Baseball elimination. Princeton University • COS 226 • Algorithms and Data Structures • Spring 2004 • Kevin Wayne • http://www.Princeton.EDU/~cos226 2 Soviet Rail Network, 1955 Minimum Cut Problem Network: abstraction for material FLOWING through the edges. Directed graph. Capacities on edges. Source node s, sink node t. Min cut problem. Delete "best" set of edges to disconnect t from s. 2 9 5 15 10 4 15 10 source s 5 3 8 6 10 t sink capacity 15 4 6 15 10 Source: On the history of the transportation and maximum flow problems. 4 30 7 Alexander Schrijver in Math Programming, 91: 3, 2002. 3 4 Cuts Cuts A cut is a node partition (S, T) such that s is in S and t is in T. A cut is a node partition (S, T) such that s is in S and t is in T. capacity(S, T) = sum of weights of edges leaving S. capacity(S, T) = sum of weights of edges leaving S. 2 9 5 2 9 5 10 10 4 15 15 10 4 15 15 10 s 5 3 8 6 10 t s 5 3 8 6 10 t S S 4 6 15 4 6 15 15 10 15 10 Capacity = 30 Capacity = 62 4 30 7 4 30 7 5 6 Minimum Cut Problem Maximum Flow Problem A cut is a node partition (S, T) such that s is in S and t is in T. -

A New Algorithm for the Maximum Flow Problem
OPERATIONS RESEARCH INFORMS Vol. 00, No. 0, Xxxxx 0000, pp. 000{000 doi 10.1287/xxxx.0000.0000 issn 0030-364X j eissn 1526-5463 j 00 j 0000 j 0001 °c 0000 INFORMS The Pseudoflow algorithm: A new algorithm for the maximum flow problem Dorit S. Hochbaum Department of Industrial Engineering and Operations Research and Walter A. Haas School of Business, University of California, Berkeley [email protected], http://www.ieor.berkeley.edu/ hochbaum/ We introduce the pseudoflow algorithm for the maximum flow problem that employs only pseudoflows and does not generate flows explicitly. The algorithm solves directly a problem equivalent to the minimum cut problem { the maximum blocking cut problem. Once the maximum blocking cut solution is available, the additional complexity required to ¯nd the respective maximum flow is O(m log n). A variant of the algorithm is a new parametric maximum flow algorithm generating all breakpoints in the same complexity required to solve the constant capacities maximum flow problem. The pseudoflow algorithm has also a simplex variant, pseudoflow-simplex, that can be implemented to solve the maximum flow problem. One feature of the pseudoflow algorithm is that it can initialize with any pseudoflow. This feature allows it to reach an optimal solution quickly when the initial pseudoflow is \close" to an optimal solution. The complexities of the pseudoflow algorithm, the pseudoflow-simplex and the parametric variants of pseudoflow and pseudoflow-simplex algorithms are all O(mn log n) on a graph with n nodes and m arcs. Therefore, the pseudoflow-simplex algorithm is the fastest simplex algorithm known for the parametric maximum flow problem. -

Linear Programming II 1 Introduction 2 Maximum Flow Problem
A Theorist's Toolkit (CMU 18-859T, Fall 2013) Lecture 14: Linear Programming II October 23, 2013 Lecturer: Ryan O'Donnell Scribe: Stylianos Despotakis 1 Introduction At a big conference in Wisconsin in 1948 with many famous economists and mathematicians, George Dantzig gave a talk related to linear programming. When the talk was over and it was time for questions, Harold Hotelling raised his hand in objection and said \But we all know the world is nonlinear," and then he sat down. John von Neumann replied on Dantzig's behalf \The speaker titled his talk `linear programming' and carefully stated his axioms. If you have an application that satisfies the axioms, well use it. If it does not, then don't." [Dan02] Figure 1: A cartoon Dantzig's Stanford colleagues reported as hanging outside his of- fice [Coo11] In this lecture, we will see some examples of problems we can solve using linear program- ming. Some of these problems are expressible as linear programs, and therefore we can use a polynomial time algorithm to solve them. However, there are also some problems that can- not be captured by linear programming in a straightforward way, but as we will see, linear programming is still useful in order to solve them or \approximate" a solution to them. 2 Maximum Flow Problem Max (s-t) Flow Problem is an example of a true linear problem. The input is a directed graph G = (V; E) with two special vertices, a \source" s V , and a \sink" t V . Moreover, 2 2 1 Figure 2: An example of an input to the Max Flow problem ≥0 each edge (u; v) E has a \capacity" cuv Q . -

Maximum Flow
Algorithms ROBERT SEDGEWICK | KEVIN WAYNE 6.4 MAXIMUM FLOW ‣ introduction ‣ Ford-Fulkerson algorithm Algorithms ‣ maxflow-mincut theorem FOURTH EDITION ‣ analysis of running time ‣ Java implementation ROBERT SEDGEWICK | KEVIN WAYNE http://algs4.cs.princeton.edu ‣ applications 6.4 MAXIMUM FLOW ‣ introduction ‣ Ford-Fulkerson algorithm Algorithms ‣ maxflow-mincut theorem ‣ analysis of running time ‣ Java implementation ROBERT SEDGEWICK | KEVIN WAYNE http://algs4.cs.princeton.edu ‣ applications Mincut problem Input. An edge-weighted digraph, source vertex s, and target vertex t. each edge has a positive capacity capacity 9 4 15 15 10 10 s 5 8 10 t 15 4 6 15 10 16 3 Mincut problem Def. A st-cut (cut) is a partition of the vertices into two disjoint sets, with s in one set A and t in the other set B. Def. Its capacity is the sum of the capacities of the edges from A to B. 10 s 5 t 15 capacity = 10 + 5 + 15 = 30 4 Mincut problem Def. A st-cut (cut) is a partition of the vertices into two disjoint sets, with s in one set A and t in the other set B. Def. Its capacity is the sum of the capacities of the edges from A to B. 10 s 8 t don't count edges from B to A 16 capacity = 10 + 8 + 16 = 34 5 Mincut problem Def. A st-cut (cut) is a partition of the vertices into two disjoint sets, with s in one set A and t in the other set B. Def. Its capacity is the sum of the capacities of the edges from A to B. -

Graph Theory, an Antiprism Graph Is a Graph That Has One of the Antiprisms As Its Skeleton
Graph families From Wikipedia, the free encyclopedia Chapter 1 Antiprism graph In the mathematical field of graph theory, an antiprism graph is a graph that has one of the antiprisms as its skeleton. An n-sided antiprism has 2n vertices and 4n edges. They are regular, polyhedral (and therefore by necessity also 3- vertex-connected, vertex-transitive, and planar graphs), and also Hamiltonian graphs.[1] 1.1 Examples The first graph in the sequence, the octahedral graph, has 6 vertices and 12 edges. Later graphs in the sequence may be named after the type of antiprism they correspond to: • Octahedral graph – 6 vertices, 12 edges • square antiprismatic graph – 8 vertices, 16 edges • Pentagonal antiprismatic graph – 10 vertices, 20 edges • Hexagonal antiprismatic graph – 12 vertices, 24 edges • Heptagonal antiprismatic graph – 14 vertices, 28 edges • Octagonal antiprismatic graph– 16 vertices, 32 edges • ... Although geometrically the star polygons also form the faces of a different sequence of (self-intersecting) antiprisms, the star antiprisms, they do not form a different sequence of graphs. 1.2 Related graphs An antiprism graph is a special case of a circulant graph, Ci₂n(2,1). Other infinite sequences of polyhedral graph formed in a similar way from polyhedra with regular-polygon bases include the prism graphs (graphs of prisms) and wheel graphs (graphs of pyramids). Other vertex-transitive polyhedral graphs include the Archimedean graphs. 1.3 References [1] Read, R. C. and Wilson, R. J. An Atlas of Graphs, Oxford, England: Oxford University Press, 2004 reprint, Chapter 6 special graphs pp. 261, 270. 2 1.4. EXTERNAL LINKS 3 1.4 External links • Weisstein, Eric W., “Antiprism graph”, MathWorld.