Post-Quantum TLS Without Handshake Signatures Full Version, May 7, 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lectures on the NTRU Encryption Algorithm and Digital Signature Scheme: Grenoble, June 2002
Lectures on the NTRU encryption algorithm and digital signature scheme: Grenoble, June 2002 J. Pipher Brown University, Providence RI 02912 1 Lecture 1 1.1 Integer lattices Lattices have been studied by cryptographers for quite some time, in both the field of cryptanalysis (see for example [16{18]) and as a source of hard problems on which to build encryption schemes (see [1, 8, 9]). In this lecture, we describe the NTRU encryption algorithm, and the lattice problems on which this is based. We begin with some definitions and a brief overview of lattices. If a ; a ; :::; a are n independent vectors in Rm, n m, then the 1 2 n ≤ integer lattice with these vectors as basis is the set = n x a : x L f 1 i i i 2 Z . A lattice is often represented as matrix A whose rows are the basis g P vectors a1; :::; an. The elements of the lattice are simply the vectors of the form vT A, which denotes the usual matrix multiplication. We will specialize for now to the situation when the rank of the lattice and the dimension are the same (n = m). The determinant of a lattice det( ) is the volume of the fundamen- L tal parallelepiped spanned by the basis vectors. By the Gram-Schmidt process, one can obtain a basis for the vector space generated by , and L the det( ) will just be the product of these orthogonal vectors. Note that L these vectors are not a basis for as a lattice, since will not usually L L possess an orthogonal basis. -

The Order of Encryption and Authentication for Protecting Communications (Or: How Secure Is SSL?)?
The Order of Encryption and Authentication for Protecting Communications (Or: How Secure is SSL?)? Hugo Krawczyk?? Abstract. We study the question of how to generically compose sym- metric encryption and authentication when building \secure channels" for the protection of communications over insecure networks. We show that any secure channels protocol designed to work with any combina- tion of secure encryption (against chosen plaintext attacks) and secure MAC must use the encrypt-then-authenticate method. We demonstrate this by showing that the other common methods of composing encryp- tion and authentication, including the authenticate-then-encrypt method used in SSL, are not generically secure. We show an example of an en- cryption function that provides (Shannon's) perfect secrecy but when combined with any MAC function under the authenticate-then-encrypt method yields a totally insecure protocol (for example, ¯nding passwords or credit card numbers transmitted under the protection of such protocol becomes an easy task for an active attacker). The same applies to the encrypt-and-authenticate method used in SSH. On the positive side we show that the authenticate-then-encrypt method is secure if the encryption method in use is either CBC mode (with an underlying secure block cipher) or a stream cipher (that xor the data with a random or pseudorandom pad). Thus, while we show the generic security of SSL to be broken, the current practical implementations of the protocol that use the above modes of encryption are safe. 1 Introduction The most widespread application of cryptography in the Internet these days is for implementing a secure channel between two end points and then exchanging information over that channel. -

Multi-Device for Signal
Multi-Device for Signal S´ebastienCampion3, Julien Devigne1, C´elineDuguey1;2, and Pierre-Alain Fouque2 1 DGA Maˆıtrisede l’information, Bruz, France [email protected] 2 Irisa, Rennes, France, [email protected], [email protected] Abstract. Nowadays, we spend our life juggling with many devices such as smartphones, tablets or laptops, and we expect to easily and efficiently switch between them without losing time or security. However, most ap- plications have been designed for single device usage. This is the case for secure instant messaging (SIM) services based on the Signal proto- col, that implements the Double Ratchet key exchange algorithm. While some adaptations, like the Sesame protocol released by the developers of Signal, have been proposed to fix this usability issue, they have not been designed as specific multi-device solutions and no security model has been formally defined either. In addition, even though the group key exchange problematic appears related to the multi-device case, group solutions are too generic and do not take into account some properties of the multi-device setting. Indeed, the fact that all devices belong to a single user can be exploited to build more efficient solutions. In this paper, we propose a Multi-Device Instant Messaging protocol based on Signal, ensuring all the security properties of the original Signal. Keywords: cryptography, secure instant messaging, ratchet, multi-device 1 Introduction 1.1 Context Over the last years, secure instant messaging has become a key application ac- cessible on smartphones. In parallel, more and more people started using several devices - a smartphone, a tablet or a laptop - to communicate. -

NTRU Cryptosystem: Recent Developments and Emerging Mathematical Problems in Finite Polynomial Rings
XXXX, 1–33 © De Gruyter YYYY NTRU Cryptosystem: Recent Developments and Emerging Mathematical Problems in Finite Polynomial Rings Ron Steinfeld Abstract. The NTRU public-key cryptosystem, proposed in 1996 by Hoffstein, Pipher and Silverman, is a fast and practical alternative to classical schemes based on factorization or discrete logarithms. In contrast to the latter schemes, it offers quasi-optimal asymptotic effi- ciency and conjectured security against quantum computing attacks. The scheme is defined over finite polynomial rings, and its security analysis involves the study of natural statistical and computational problems defined over these rings. We survey several recent developments in both the security analysis and in the applica- tions of NTRU and its variants, within the broader field of lattice-based cryptography. These developments include a provable relation between the security of NTRU and the computa- tional hardness of worst-case instances of certain lattice problems, and the construction of fully homomorphic and multilinear cryptographic algorithms. In the process, we identify the underlying statistical and computational problems in finite rings. Keywords. NTRU Cryptosystem, lattice-based cryptography, fully homomorphic encryption, multilinear maps. AMS classification. 68Q17, 68Q87, 68Q12, 11T55, 11T71, 11T22. 1 Introduction The NTRU public-key cryptosystem has attracted much attention by the cryptographic community since its introduction in 1996 by Hoffstein, Pipher and Silverman [32, 33]. Unlike more classical public-key cryptosystems based on the hardness of integer factorisation or the discrete logarithm over finite fields and elliptic curves, NTRU is based on the hardness of finding ‘small’ solutions to systems of linear equations over polynomial rings, and as a consequence is closely related to geometric problems on certain classes of high-dimensional Euclidean lattices. -

A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based on Elliptic Curve Cryptography
applied sciences Article A Novel Asymmetric Hyperchaotic Image Encryption Scheme Based on Elliptic Curve Cryptography Haotian Liang , Guidong Zhang *, Wenjin Hou, Pinyi Huang, Bo Liu and Shouliang Li * School of Information Science and Engineering, Lanzhou University, Lanzhou 730000, China; [email protected] (H.L.); [email protected] (W.H.); [email protected] (P.H.); [email protected] (B.L.) * Correspondence: [email protected] (G.Z.); [email protected] (S.L.); Tel.: +86-185-0948-7799 (S.L.) Abstract: Most of the image encryption schemes based on chaos have so far employed symmetric key cryptography, which leads to a situation where the key cannot be transmitted in public channels, thus limiting their extended application. Based on the elliptic curve cryptography (ECC), we proposed a public key image encryption method where the hash value derived from the plain image was encrypted by ECC. Furthermore, during image permutation, a novel algorithm based on different- sized block was proposed. The plain image was firstly divided into five planes according to the amount of information contained in different bits: the combination of the low 4 bits, and other four planes of high 4 bits respectively. Second, for different planes, the corresponding method of block partition was followed by the rule that the higher the bit plane, the smaller the size of the partitioned block as a basic unit for permutation. In the diffusion phase, the used hyperchaotic sequences in permutation were applied to improve the efficiency. Lots of experimental simulations and cryptanalyses were implemented in which the NPCR and UACI are 99.6124% and 33.4600% Citation: Liang, H.; Zhang, G.; Hou, respectively, which all suggested that it can effectively resist statistical analysis attacks and chosen W.; Huang, P.; Liu, B.; Li, S. -

Performance Evaluation of RSA and NTRU Over GPU with Maxwell and Pascal Architecture
Performance Evaluation of RSA and NTRU over GPU with Maxwell and Pascal Architecture Xian-Fu Wong1, Bok-Min Goi1, Wai-Kong Lee2, and Raphael C.-W. Phan3 1Lee Kong Chian Faculty of and Engineering and Science, Universiti Tunku Abdul Rahman, Sungai Long, Malaysia 2Faculty of Information and Communication Technology, Universiti Tunku Abdul Rahman, Kampar, Malaysia 3Faculty of Engineering, Multimedia University, Cyberjaya, Malaysia E-mail: [email protected]; {goibm; wklee}@utar.edu.my; [email protected] Received 2 September 2017; Accepted 22 October 2017; Publication 20 November 2017 Abstract Public key cryptography important in protecting the key exchange between two parties for secure mobile and wireless communication. RSA is one of the most widely used public key cryptographic algorithms, but the Modular exponentiation involved in RSA is very time-consuming when the bit-size is large, usually in the range of 1024-bit to 4096-bit. The speed performance of RSA comes to concerns when thousands or millions of authentication requests are needed to handle by the server at a time, through a massive number of connected mobile and wireless devices. On the other hand, NTRU is another public key cryptographic algorithm that becomes popular recently due to the ability to resist attack from quantum computer. In this paper, we exploit the massively parallel architecture in GPU to perform RSA and NTRU computations. Various optimization techniques were proposed in this paper to achieve higher throughput in RSA and NTRU computation in two GPU platforms. To allow a fair comparison with existing RSA implementation techniques, we proposed to evaluate the speed performance in the best case Journal of Software Networking, 201–220. -

Making NTRU As Secure As Worst-Case Problems Over Ideal Lattices
Making NTRU as Secure as Worst-Case Problems over Ideal Lattices Damien Stehlé1 and Ron Steinfeld2 1 CNRS, Laboratoire LIP (U. Lyon, CNRS, ENS Lyon, INRIA, UCBL), 46 Allée d’Italie, 69364 Lyon Cedex 07, France. [email protected] – http://perso.ens-lyon.fr/damien.stehle 2 Centre for Advanced Computing - Algorithms and Cryptography, Department of Computing, Macquarie University, NSW 2109, Australia [email protected] – http://web.science.mq.edu.au/~rons Abstract. NTRUEncrypt, proposed in 1996 by Hoffstein, Pipher and Sil- verman, is the fastest known lattice-based encryption scheme. Its mod- erate key-sizes, excellent asymptotic performance and conjectured resis- tance to quantum computers could make it a desirable alternative to fac- torisation and discrete-log based encryption schemes. However, since its introduction, doubts have regularly arisen on its security. In the present work, we show how to modify NTRUEncrypt to make it provably secure in the standard model, under the assumed quantum hardness of standard worst-case lattice problems, restricted to a family of lattices related to some cyclotomic fields. Our main contribution is to show that if the se- cret key polynomials are selected by rejection from discrete Gaussians, then the public key, which is their ratio, is statistically indistinguishable from uniform over its domain. The security then follows from the already proven hardness of the R-LWE problem. Keywords. Lattice-based cryptography, NTRU, provable security. 1 Introduction NTRUEncrypt, devised by Hoffstein, Pipher and Silverman, was first presented at the Crypto’96 rump session [14]. Although its description relies on arithmetic n over the polynomial ring Zq[x]=(x − 1) for n prime and q a small integer, it was quickly observed that breaking it could be expressed as a problem over Euclidean lattices [6]. -

Trivia: a Fast and Secure Authenticated Encryption Scheme
TriviA: A Fast and Secure Authenticated Encryption Scheme Avik Chakraborti1, Anupam Chattopadhyay2, Muhammad Hassan3, and Mridul Nandi1 1 Indian Statistical Institute, Kolkata, India [email protected], [email protected] 2 School of Computer Engineering, NTU, Singapore [email protected] 3 RWTH Aachen University, Germany [email protected] Abstract. In this paper, we propose a new hardware friendly authen- ticated encryption (AE) scheme TriviA based on (i) a stream cipher for generating keys for the ciphertext and the tag, and (ii) a pairwise in- dependent hash to compute the tag. We have adopted one of the ISO- standardized stream ciphers for lightweight cryptography, namely Triv- ium, to obtain our underlying stream cipher. This new stream cipher has a state that is a little larger than the state of Trivium to accommodate a 128-bit secret key and IV. Our pairwise independent hash is also an adaptation of the EHC or \Encode-Hash-Combine" hash, that requires the optimum number of field multiplications and hence requires small hardware footprint. We have implemented the design in synthesizable RTL. Pre-layout synthesis, using 65 nm standard cell technology under typical operating conditions, reveals that TriviA is able to achieve a high throughput of 91:2 Gbps for an area of 24:4 KGE. We prove that our construction has at least 128-bit security for privacy and 124-bit security of authenticity under the assumption that the underlying stream cipher produces a pseudorandom bit stream. Keywords: Trivium, stream cipher, authenticated encryption, pairwise independent, EHC, TriviA. 1 Introduction The emergence of Internet-of-Things (IoT) has made security an extremely im- portant design goal. -

Cryptanalysis of Globalplatform Secure Channel Protocols
Cryptanalysis of GlobalPlatform Secure Channel Protocols Mohamed Sabt1;2, Jacques Traor´e1 1 Orange Labs, 42 rue des coutures, 14066 Caen, France fmohamed.sabt, [email protected] 2 Sorbonne universit´es,Universit´ede technologie de Compi`egne, Heudiasyc, Centre de recherche Royallieu, 60203 Compi`egne,France Abstract. GlobalPlatform (GP) card specifications are the de facto standards for the industry of smart cards. Being highly sensitive, GP specifications were defined regarding stringent security requirements. In this paper, we analyze the cryptographic core of these requirements; i.e. the family of Secure Channel Protocols (SCP). Our main results are twofold. First, we demonstrate a theoretical attack against SCP02, which is the most popular protocol in the SCP family. We discuss the scope of our attack by presenting an actual scenario in which a malicious entity can exploit it in order to recover encrypted messages. Second, we inves- tigate the security of SCP03 that was introduced as an amendment in 2009. We find that it provably satisfies strong notions of security. Of par- ticular interest, we prove that SCP03 withstands algorithm substitution attacks (ASAs) defined by Bellare et al. that may lead to secret mass surveillance. Our findings highlight the great value of the paradigm of provable security for standards and certification, since unlike extensive evaluation, it formally guarantees the absence of security flaws. Keywords: GlobalPlatform, secure channel protocol, provable security, plaintext recovery, stateful encryption 1 Introduction Nowadays, smart cards are already playing an important role in the area of in- formation technology. Considered to be tamper resistant, they are increasingly used to provide security services [38]. -

The RSA Algorithm
The RSA Algorithm Evgeny Milanov 3 June 2009 In 1978, Ron Rivest, Adi Shamir, and Leonard Adleman introduced a cryptographic algorithm, which was essentially to replace the less secure National Bureau of Standards (NBS) algorithm. Most impor- tantly, RSA implements a public-key cryptosystem, as well as digital signatures. RSA is motivated by the published works of Diffie and Hellman from several years before, who described the idea of such an algorithm, but never truly developed it. Introduced at the time when the era of electronic email was expected to soon arise, RSA implemented two important ideas: 1. Public-key encryption. This idea omits the need for a \courier" to deliver keys to recipients over another secure channel before transmitting the originally-intended message. In RSA, encryption keys are public, while the decryption keys are not, so only the person with the correct decryption key can decipher an encrypted message. Everyone has their own encryption and decryption keys. The keys must be made in such a way that the decryption key may not be easily deduced from the public encryption key. 2. Digital signatures. The receiver may need to verify that a transmitted message actually origi- nated from the sender (signature), and didn't just come from there (authentication). This is done using the sender's decryption key, and the signature can later be verified by anyone, using the corresponding public encryption key. Signatures therefore cannot be forged. Also, no signer can later deny having signed the message. This is not only useful for electronic mail, but for other electronic transactions and transmissions, such as fund transfers. -

Optimizing NTRU Using AVX2
Master Thesis Computing Science Cyber Security Specialisation Radboud University Optimizing NTRU using AVX2 Author: First supervisor/assessor: Oussama Danba dr. Peter Schwabe Second assessor: dr. Lejla Batina July, 2019 Abstract The existence of Shor's algorithm, Grover's algorithm, and others that rely on the computational possibilities of quantum computers raise problems for some computational problems modern cryptography relies on. These algo- rithms do not yet have practical implications but it is believed that they will in the near future. In response to this, NIST is attempting to standardize post-quantum cryptography algorithms. In this thesis we will look at the NTRU submission in detail and optimize it for performance using AVX2. This implementation takes about 29 microseconds to generate a keypair, about 7.4 microseconds for key encapsulation, and about 6.8 microseconds for key decapsulation. These results are achieved on a reasonably recent notebook processor showing that NTRU is fast and feasible in practice. Contents 1 Introduction3 2 Cryptographic background and related work5 2.1 Symmetric-key cryptography..................5 2.2 Public-key cryptography.....................6 2.2.1 Digital signatures.....................7 2.2.2 Key encapsulation mechanisms.............8 2.3 One-way functions........................9 2.3.1 Cryptographic hash functions..............9 2.4 Proving security......................... 10 2.5 Post-quantum cryptography................... 12 2.6 Lattice-based cryptography................... 15 2.7 Side-channel resistance...................... 16 2.8 Related work........................... 17 3 Overview of NTRU 19 3.1 Important NTRU operations................... 20 3.1.1 Sampling......................... 20 3.1.2 Polynomial addition................... 22 3.1.3 Polynomial reduction.................. 22 3.1.4 Polynomial multiplication............... -

Post-Quantum TLS Without Handshake Signatures Full Version, September 29, 2020
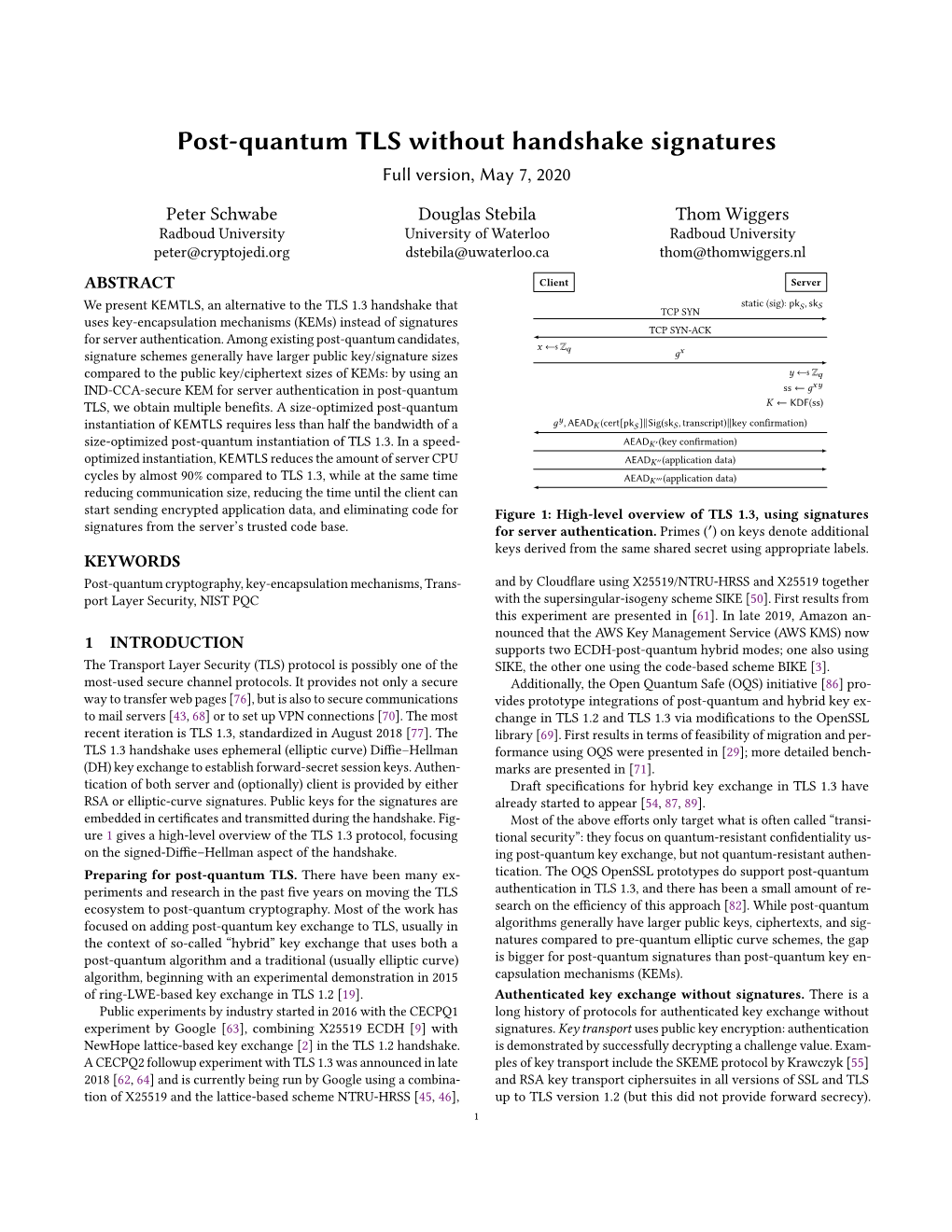
Post-Quantum TLS Without Handshake Signatures Full version, September 29, 2020 Peter Schwabe Douglas Stebila Thom Wiggers Max Planck Institute for Security and University of Waterloo Radboud University Privacy & Radboud University [email protected] [email protected] [email protected] ABSTRACT Client Server static (sig): pk(, sk( We present KEMTLS, an alternative to the TLS 1.3 handshake that TCP SYN uses key-encapsulation mechanisms (KEMs) instead of signatures TCP SYN-ACK for server authentication. Among existing post-quantum candidates, G $ Z @ 6G signature schemes generally have larger public key/signature sizes compared to the public key/ciphertext sizes of KEMs: by using an ~ $ Z@ ss 6G~ IND-CCA-secure KEM for server authentication in post-quantum , 0, 00, 000 KDF(ss) TLS, we obtain multiple benefits. A size-optimized post-quantum ~ 6 , AEAD (cert[pk( ]kSig(sk(, transcript)kkey confirmation) instantiation of KEMTLS requires less than half the bandwidth of a ss 6~G size-optimized post-quantum instantiation of TLS 1.3. In a speed- , 0, 00, 000 KDF(ss) optimized instantiation, KEMTLS reduces the amount of server CPU AEAD 0 (application data) cycles by almost 90% compared to TLS 1.3, while at the same time AEAD 00 (key confirmation) reducing communication size, reducing the time until the client can AEAD 000 (application data) start sending encrypted application data, and eliminating code for signatures from the server’s trusted code base. Figure 1: High-level overview of TLS 1.3, using signatures CCS CONCEPTS for server authentication. • Security and privacy ! Security protocols; Web protocol security; Public key encryption.