Integrity of Electronic Voting Systems: Fallacious Use of Cryptography
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Election Code
Iowa State University STUDENT GOVERNMENT OFFICIAL ELECTION CODE Last Revised on November 5, 2020 Table of Contents CHAPTER 1: General Provisions and Definitions ...................................................................... 3 Scope and Purpose; Election Law .................................................................................................... 3 Definitions ..................................................................................................................................... 4 CHAPTER 2: Senatorial Candidate Registration, Seminars, and Liaison Assignment ................. 6 CHAPTER 3: Executive Slate Registration and Seminars .......................................................... 7 CHAPTER 4: Petitions and Ballots ........................................................................................... 8 CHAPTER 5: Debates ............................................................................................................ 10 CHAPTER 6: Financial Regulations, Disclosure and Reimbursement....................................... 11 CHAPTER 7: Endorsements and In-Kind Donations ................................................................ 13 CHAPTER 8: Campaigning Regulations .................................................................................. 14 CHAPTER 9: Write-in Candidates .......................................................................................... 19 CHAPTER 10: Referenda Questions and Student Initiatives .................................................. -

Supreme Court Clarifies Rules for Electoral College: States May Restrict Faithless Electors
Legal Sidebari Supreme Court Clarifies Rules for Electoral College: States May Restrict Faithless Electors July 10, 2020 On July 6, 2020, the Supreme Court unanimously held that states may punish or replace presidential electors who refuse to cast their ballots for the candidate chosen by the voters of their state. In the case Chiafalo v. Washington, a majority of the Court held that the State of Washington’s constitutional authority to appoint electors includes the power to impose a $1,000 fine against electors who violate their pledge to support the candidate chosen in the state’s popular vote. In the related case Colorado Department of State v. Baca, the Court upheld on the same grounds Colorado’s policy of replacing electors who attempt to cast a ballot for a person who did not win the state’s popular vote. This Legal Sidebar explains the Court’s decisions and reviews their broader implications. Background Article II of the Constitution provides, “Each State shall appoint, in such Manner as the Legislature thereof may direct, a Number of Electors, equal to the whole Number of Senators and Representatives to which the State may be entitled in the Congress.” Under the Twelfth Amendment, the electors “meet in their respective states and vote by ballot for President and Vice-President, one of whom, at least, shall not be an inhabitant of the same state with themselves.” Today, states employ a two-step process to appoint their electors. First, states ask each political party to submit a slate of electors that it would like to represent the state. -

City Council Election Methods in Order to Ensure That the Election Please Do Not Hesitate to Contact Us
The Center for Voting and Democracy City 6930 Carroll Avenue, Suite 610 – Takoma Park, MD 20912 Phone: (301) 270-4616 – Fax: (301) 270-4133 Council Email: [email protected] Website: http://www.fairvote.org Election This Manual is intended to assist Charter Review Comissions, city officials, and other community Methods leaders in determining what electoral systems will best meet the needs and goals of their community. Given that no system can accomplish every goal, this manual will help you analyze the INTRODUCTION consequences of adopting one system over The range of options that exists for electing a municipal government is broader than many people realize. Voting systems can have a another and will aid you in comparing the features striking impact on the type of candidates who run for office, how of various electoral systems. representative the council is, which candidates are elected, which parties control the city council, which voters feel well represented, Should you desire more information about any of and so on. This booklet is intended to aid in the evaluation of possible the voting systems discussed within this manual, city council election methods in order to ensure that the election please do not hesitate to contact us. method is determined by conscious choice, not inertia. A separate companion booklet, Mayoral Election Methods , deals with the selection of an executive. A summary of this booklet can be found in the city council election method evaluation grid at Page 11. 1 CRITERIA FOR EVALUATING CITY COUNCIL ELECTION METHODS 1. VOTER CHOICE Different election methods will encourage different numbers of It is important to recognize from the outset that no election candidates to run, and will thus impact the level of choice which method is perfect. -

STRATEGIES UNDER a NEW ELECTORAL SYSTEM the Labor Party in the 1996 Israeli Elections
06 – Torgovnik 4/1/00 12:11 pm Page 95 PARTY POLITICS VOL 6. No.1 pp. 95–106 Copyright © 2000 SAGE Publications London Thousand Oaks New Delhi RESEARCH NOTE STRATEGIES UNDER A NEW ELECTORAL SYSTEM The Labor Party in the 1996 Israeli elections Efraim Torgovnik ABSTRACT Structural systemic factors, including a tie between the two major political blocs in Israel and the change to direct election of the prime minister, generated an on-line personal campaign, making memory-based retrospective assessment of the positive past performance of Labor and its candidate, Shimon Peres, a lesser electoral issue. The direct elections for the prime minister overshadowed the party and its campaign. Concerns for personal security, raised during the campaign by terrorism, enhanced the electoral chances of the opposition Likud party and its candidate, Binyamin Netanyahu. Emotions became dominant in such symbolic-normative electoral dimensions as religious nationalism and fear. This was apparent in the success of the opposition candidate, Netanyahu, who was against the Oslo peace process, in entering the peace space by calling for a safe peace; he made peace a derivative of security. This undermined the key campaign position issue of incumbent Prime Minister Peres, which made security a derivative of peace. Emotions and terrorism contributed to a negative prospective voter assessment of the peace process and overshadowed retrospective dimensions of perform- ance, state of the economy and leadership. Analysis of campaign- generated issues indicates that election campaigns do make a difference. KEY WORDS n campaign strategies n electoral systems n Israel The 1996 Israeli national elections were held under a new and unique elec- toral rule: the prime minister was elected through personal elections in one 1354-0688(200001)6:1;95–106;011276 06 – Torgovnik 4/1/00 12:11 pm Page 96 PARTY POLITICS 6(1) national constituency while the parties ran in a national proportional rep- resentation system. -

Frankfurter, Abstention Doctrine, and the Development of Modern Federalism: a History and Three Futures Lael Weinberger†
ARTICLE Frankfurter, Abstention Doctrine, and the Development of Modern Federalism: A History and Three Futures Lael Weinberger† In its first century and a half, the Supreme Court never used the term “feder- alism” in its opinions. The Court had talked about federal-state relations before, but the concept had gone unlabeled. That changed in 1939. Something new was hap- pening, thanks in large part to Justice Felix Frankfurter. Just a month after joining the Court, Frankfurter authored the Court’s first opinion using the term “federal- ism.” Frankfurter introduced federalism as a key concept for analyzing the relation- ship between state courts and federal courts. Before long, Frankfurter would rely on federalism to fashion an original and enduring doctrine of judicial federalism: ab- stention, which requires federal courts to sometimes refrain from hearing cases that are within their jurisdiction. This Article provides a historical study of Frankfurter’s contribution to the modern law of judicial federalism. It documents Frankfurter’s theory of federalism in his judicial opinions with a focus on the abstention cases. It also shows how the abstention cases and their concept of federalism were rooted in Frankfurter’s Pro- gressive politics. They were a reaction to what he perceived as the federal courts’ anti-regulatory and anti-labor attitudes. The history—relevant today as the political discussion around the courts again echoes the Progressive Era—sets the stage for considering the future of abstention. I suggest three possibilities. The first, an originalist future, would more or less main- tain the contemporary Supreme Court’s status quo on abstention, somewhat more modest than what Frankfurter envisioned: a cautious use of abstention in a rela- tively small number of equitable cases. -

Voting System Failures: a Database Solution
B R E N N A N CENTER FOR JUSTICE voting system failures: a database solution Lawrence Norden Brennan Center for Justice at New York University School of Law about the brennan center for justice The Brennan Center for Justice at New York University School of Law is a non-partisan public policy and law institute that focuses on fundamental issues of democracy and justice. Our work ranges from voting rights to campaign finance reform, from racial justice in criminal law to presidential power in the fight against terrorism. A singular institution – part think tank, part public interest law firm, part advocacy group – the Brennan Center combines scholarship, legislative and legal advocacy, and communication to win meaningful, measurable change in the public sector. about the brennan center’s voting rights and elections project The Brennan Center promotes policies that protect rights, equal electoral access, and increased political participation on the national, state and local levels. The Voting Rights and Elections Project works to expend the franchise, to make it as simple as possible for every eligible American to vote, and to ensure that every vote cast is accurately recorded and counted. The Center’s staff provides top-flight legal and policy assistance on a broad range of election administration issues, including voter registration systems, voting technology, voter identification, statewide voter registration list maintenance, and provisional ballots. The Help America Vote Act in 2002 required states to replace antiquated voting machines with new electronic voting systems, but jurisdictions had little guidance on how to evaluate new voting technology. The Center convened four panels of experts, who conducted the first comprehensive analyses of electronic voting systems. -

Annual and Extraordinary General Shareholders'meeting to Be Held On
CNPJ nº 97.837.181/0001-47 A Public Listed Company ANNUAL AND EXTRAORDINARY GENERAL SHAREHOLDERS’MEETING TO BE HELD ON APRIL 29, 2021 SYNTHETIC VOTING MAP CONSOLIDATED BY THE COMPANY DURATEX S.A., pursuant to CVM Instruction 481/09, discloses the synthetic voting map consolidating voting instructions transmitted by the shareholders through their respective custodian agents to the central depositary and the registrar and the ballots transmitted directly to the company. In accordance with article 21-W, Third Paragraph, of the CVM Instruction 481/09, the charters attached herein identify how many approvals, rejections or abstentions received each item in the ballot paper in the matters to be submitted to the deliberation of the Annual and Extraordinary General Stockholders’ Meeting to be held on April 29, 2021. São Paulo (SP), April 28, 2021. Carlos Henrique Pinto Haddad Vice President of Administration, Finance and Investor Relations Page 1 CNPJ nº 97.837.181/0001-47 A Public Listed Company AGENDA OF THE ANNUAL GENERAL MEETING COMMON SHARES % OVER DESCRIPTION OF DELIBERATION VOTE DELIBERATION QUANTITY TOTAL VOTES Approve 434.125,274 96.75% Take cognizance of the management accounts and examine, discuss and 1 vote on the Financial Statements related for the fiscal year ended on Reject 81,900 0.02% 12.31.2020 Abstain 14,510,776 3.23% Resolve upon the Board of Directors' proposal for the allocation of profit Approve 448,717,950 100.00% for 2020, including the ratification of the interim distribution of interest of interest capital, as detailed in the Manual Meeting available at https: 2 //www.duratex. -
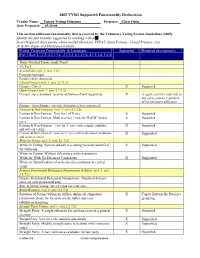
Identify the Voting Variations Supported by the Liberty Control System By
2005 VVSG Supported Functionality Declaration Vendor Name: __Unisyn Voting Solutions___________ Preparer: _Chris Ortiz_______________________ Date Prepared: __05/26/08________________________ This section addresses functionality that is covered by the Voluntary Voting System Guidelines (2005). Identify the functionality supported by marking with a . Insert Required descriptions where needed (Rotation, VVPAT, Open Primary, Closed Primary, etc). (P & M= Paper and Marksense ballots) Voting Variations Functionality & Languages Supported Required description(s) Vol. 1 Sect 2.1.7.2, 2.2.1.3.a, 2.3.3.3, 4.1.5.1.b, 4.1.5.1.d, 5.4.4 Voter Verified Paper Audit Trails VVPAT Accessibility (vol. 1. sect. 3.2) Forward Approach Parallel (Side) Approach Closed Primary (vol. 1. sect. 2.1.7.2) Primary: Closed X Supported Open Primary (vol. 1. sect. 2.1.7.2) Primary: Open Standard (provide definition of how supported) X A registered voter may vote in any party primary regardless of his own party affiliation Primary: Open Blanket (provide definition of how supported) Partisan & Non-Partisan: (vol. 1. sect. 2.1.7.2) Partisan & Non-Partisan: Vote for 1 of N race X Supported Partisan & Non-Partisan: Multi-member (“vote for N of M”) board X Supported races Partisan & Non-Partisan: “vote for 1” race with a single candidate X Supported and write-in voting Partisan & Non-Partisan “vote for 1” race with no declared candidates X Supported and write-in voting Write-In Voting: (vol. 1. sect. 2.1.7.2) Write-in Voting: System default is a voting position identified X Supported for write-ins. -

Making Sure Every Vote Counts: a Guide to the Laws on Certifying and Counting Presidential Electors for the in 2020 Election
MAKING SURE EVERY VOTE COUNTS: A GUIDE TO THE LAWS ON CERTIFYING AND COUNTING PRESIDENTIAL ELECTORS FOR THE IN 2020 ELECTION BY THE DEMOCRATIC TRANSITION WORKING GROUP OF THE UNIVERSITY OF DAYTON SCHOOL OF LAW INTRODUCTION Understanding and following the law in ways that give effect to all legally cast ballots is crucial to protecting our democracy. Lawyers, judges and public officials play a critical role in assuring that protracted legal disputes do not prevent counting the votes by the statutory deadlines or erode public confidence in the election by allowing political influence to inappropriately affect the outcomes. Towards these ends, this summary (1) provides a simple explanation of a complex electoral process, (2) raises important legal issues that could arise in a close and disputed election, and (3) gives legal resources to assist those beginning more in-depth legal research. PRESIDENTIAL ELECTORAL PROCESS – SIMPLIFIED A. Overview of the Presidential Electoral System. The President is selected based on a majority vote of “electors” chosen every four years by each state under the laws of that state. Currently, every state’s law provides that its popular vote determines the selection of electors. After the popular vote, the electors meet separately in their respective states and vote as the “Electoral College.” Each state is allotted a number of electors equal to the number of Representatives that state has in the House plus its two Senators. The District of Columbia also has three electoral votes, so there are presently 538 electors (435 + 100 + 3). The majority of electoral votes needed to become President is therefore 270. -

Final Synthetic Voting Map
CNPJ 61.532.644/0001-15 A Publicly Listed Company FINAL SYNTHETIC VOTING MAP ORDINARY GENERAL STOCKHOLDERS’ MEETING HELD ON APRIL 30, 2021 ITAÚSA S.A., pursuant to CVM Instruction 481/09, discloses the final synthetic vote map consolidating: (i) the voting instructions transmitted by the shareholders through their respective custodian agents to the central depositary, the security registrar, directly to the Company; and (ii) the votes cast by the shareholders through the digital platform during the Assembly, identifying how many approvals, rejections or abstentions received each item in the ballot paper in the matters submitted to the deliberation of the Ordinary General Stockholders’ Meeting held on April 30, 2021. São Paulo (SP), April 30, 2021. ALFREDO EGYDIO SETUBAL Investor Relations Officer ITAÚSA S.A. Final Synthetic Voting Map Ordinary General Shareholders’s Meeting held on April 30, 2021 at 11 a.m. % OVER SPECIES OF VOTE SHARES DESCRIPTION OF DELIBERATION TOTAL SHARE DELIBERATION QUANTITY VOTES Yes 2,619,350,804 100.00% 1. To authorize the drafting of the minutes of this Meeting in summarized form, pursuant to Paragraph 1, Article 130 of Law 6.404 of 1976? Common No 0 0.00% Abstain 188 0.00% Yes 2,619,350,804 100.00% To authorize the publication of the minutes of this Meeting, omitting the names of the shareholders, pursuant to Paragraph 2, Article 130 of Law 2. Common No 0 0.00% 6.404 of 1976? Abstain 188 0.00% Approve 2,619,350,788 100.00% Take cognizance of the management accounts and examine, discuss, and vote on the Financial Statements for the fiscal year ending December 31, 3. -

Traditional Political Committee Guide
A Guide for Political Committees Contact Us Address: State Elections Enforcement Commission 20 Trinity Street Hartford, Connecticut 06106-1628 Main Telephone: 860-256-2940 Toll Free (outside Hartford area): 866-SEEC-INFO Main Fax: 860-256-2981 Website: https://portal.ct.gov/seec E-Mail: [email protected] Cite this publication as: Understanding the Connecticut Campaign Finance Laws: A Guide for Traditional Political Committees. (Connecticut State Elections Enforcement Commission), Hartford, Connecticut, August 2019. Table of Contents I. Introduction 1 A. Changes in the Law 1 B. Changes in this Guide 2 C. Requesting Compliance Advice 2 II. Requirement to Form a Political Committee 5 A. Incidental Spenders: Individuals & Preexisting Groups 5 1. An Individual Acting Alone Spending Personal Funds 5 2. Preexisting Groups 6 3. Filing Requirements for Incidental Spenders 7 B. Political Committees: Two or More Individuals Acting Together & Raising Funds for Candidates, Referenda, and/or Political Parties 8 1. Two or More Individuals 8 a. Independent Expenditure Political Committees 8 b. Traditional Political Committees 9 2. Preexisting Groups 9 a. Independent Expenditure Political Committees 10 b. Traditional Political Committees 10 III. Responsibilities of the Committee Chairperson 11 A. Designation and Registration of a Traditional Political Committee 11 1. When and What to File 11 2. Where to File 11 3. Amendments to Registration 12 B. Designation of a Depository Institution 12 C. Designation of a Treasurer and Deputy Treasurer 12 1. Appointment of a Treasurer and Deputy Treasurer 12 2. Resignation and Replacement of a Treasurer 13 3. Who May Not Be a Treasurer or Deputy Treasurer 13 D. -

ANNUAL SHAREHOLDERS MEETING April 28, 2020 10:00 A.M
ANNUAL SHAREHOLDERS MEETING April 28, 2020 10:00 A.M. Synthetic Voting Map The Management of SANTOS BRASIL PARTICIPAÇÕES S.A. (“Company” or “SBPAR”), in accordance with article 21-W, paragraph 3 of CVM Instruction 481, of December 17, 2009, and later amendments, informs its Shareholders that it received on the date hereof, directly at the company and from the transfer agent of Company’s shares, Itaú Corretora de Valores S.A. (“Itaú” or “Transfer Agent”), the synthetic voting map consolidating the voting instructions given to the shareholders, according to the spreadsheet attached. São Paulo, April 27, 2020 SANTOS BRASIL PARTICIPAÇÕES S.A. DANIEL PEDREIRA DOREA Chief Financial and Investor Relations Officer www.santosbrasil.com.br Resolutions taken at the Annual Shareholders' Meeting: 1 – To take the management accounts, examine, discuss and vote on the Financial Statements of the Company for the fiscal year ended December 31, 2019. 2 – To resolve on the approval of the capital budget, pursuant to article 196 of Federal Law 6,404/76. 3 – To resolve on the allocation of the net income for the year and distribution of dividends. 4 – To resolve on the definition of number of members of the Board of Directors in order to maintain the current number of members, of which seven (7) sitting members and seven (7) alternate members. 5 – Do you wish to request the adoption of cumulative voting to elect the Board of Directors, in accordance with Article 141 of Federal Law 6,404/76? 6 – Nomination of each slate and all names comprising it 7 – If any