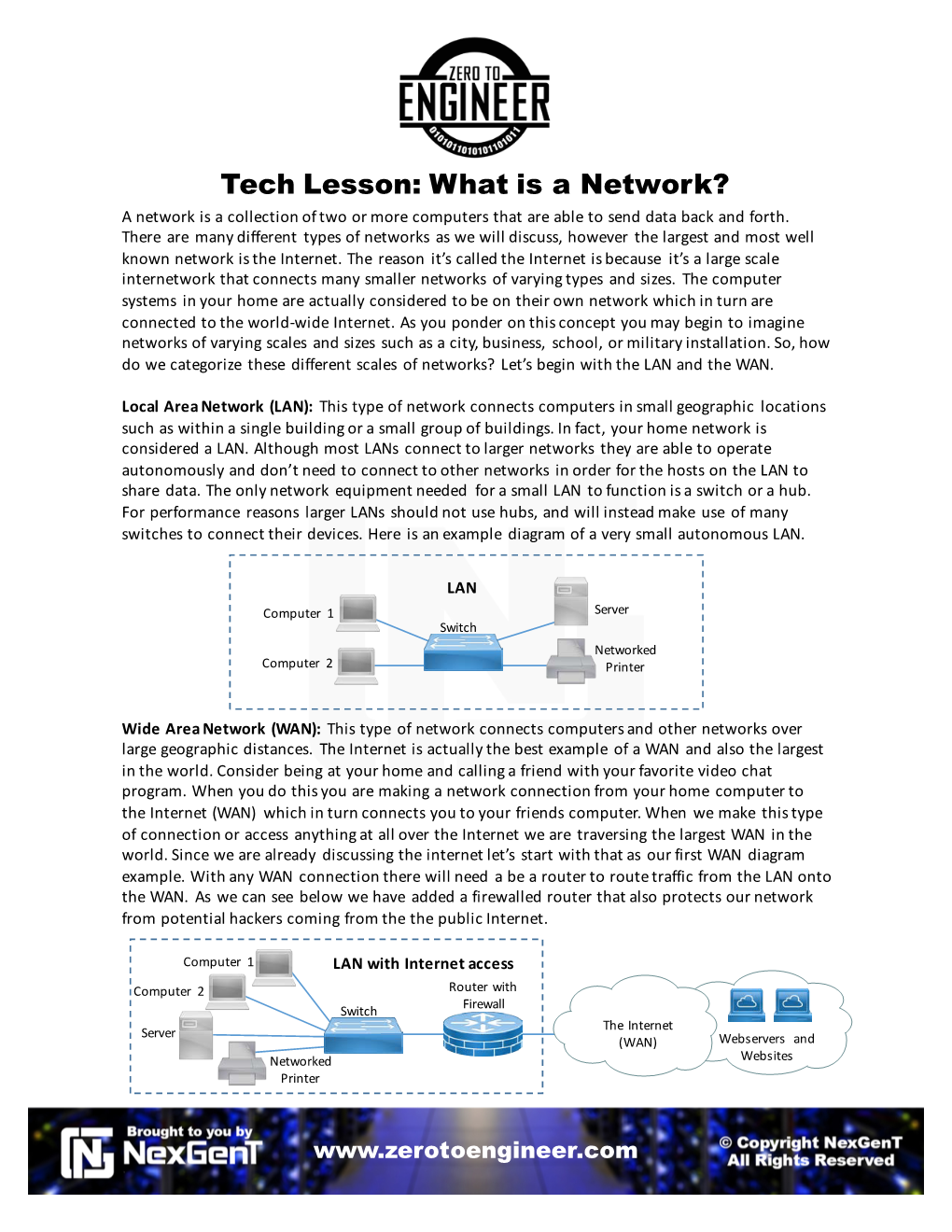
What Is a Network? a Network Is a Collection of Two Or More Computers That Are Able to Send Data Back and Forth
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Expand and Enhance Your Home Network with Gigabit Powerline
Expand and Enhance Your Home Network with Gigabit Powerline • The HomePlug AV2 standard creates The ZyXEL PLA5405 1200 Mbps Powerline Gigabit Ethernet Adapter is based on the latest powerline networks with data HomePlug AV2 standard and features data transfer rates of up to 1200 Mbps*. The Powerline transfer rates of up to 1200 Mbps* adapter plugs into an existing power outlet and instantly enables high-speed network access • Enjoy high-speed networking through a home’s electrical lines. The device offers a perfect solution for streaming HD movies, and complete coverage through playing online games and enjoying other network-intensive applications—all without the hassle of Line-Natural/Line-Ground MIMO** installing cables throughout the residence. Featuring the latest HomePlug AV2 MIMO** technology, technology the PLA5405 utilizes multiple lines from your home’s existing electrical wiring, whereas non-MIMO • No extra wires or configuration based HomePlug AV technology uses a single line. This enables the PLA5405 adapter to perform at required up to twice the speed of existing 600 Mbps* Powerline products. • Perfect for connecting smart TVs and playing online games Benefits • QoS enhances media streaming Enjoy high-speed networking and increased coverage through MIMO quality capabilities** • Single push-and-secure button for With advanced HomePlug AV2 technology, the ZyXEL PLA5405 provides users with steady, high-speed easy security setup data transfer rates of up to 1200 Mbps* and is backward compatible with HomePlug AV and IEEE • Compliant with IEEE 1901 and 1901-based products. The new HomePlug AV2 Multiple Input Multiple Output (MIMO) feature increases HomePlug AV technology throughput and coverage. -

Approved Modem List
Approved Modem List Internet Only Cable Modems* SMC Networks D3CM1604 This broadband modem supports downstream speeds up to 640Mbps and 120Mbps on the upstream. The extreme speed allows faster streaming HD videos, file downloads and high-speed gaming. The D3CM1604 is the ideal solution for your house or small home business. hitron CDA3-35 The CDA3-35 is the perfect choice for cable operators who want to offer high-speed broadband access to their customer base economically. It delivers speeds of up to 1.2Gbps (32×8) with thirty-two bonded downstream channels over its DOCSIS interface. Arris CM3200 The CM3200 is well-suited to the home user – offering the speeds to stream multimedia content to multiple devices and the responsiveness to keep you “in the game” for online gaming. However, the CM3200 is also a serious commercial solution, ready to meet the challenging demands of small business. Cable Modems with WIFI* Arris SURFboard® Modem & Wi-F® Router SBG6580 High-speed Internet and Wireless N at your fingertips. The SURFboard SBG6580 Wi-Fi Cable Modem is 3 products in one device: DOCSIS 3.0 Cable Modem, Dual-Band 802.11n Wi-Fi Access Point and 4-port Gigabit Ethernet Router. Arris DG2470 Wireless Gateway The Touchstone DG2470 is a DOCSIS3.0 home data gateway supporting 24 x 8 channel bonding for up to 960Mbps of broadband data. It combines a 4-port gigabit router, MoCA 2.0 over coax, and a dual band 802.11ac wireless access point. Arris TG2472 Wireless Gateway The Touchstone TG2472 is a DOCSIS3.0 home telephony gateway supporting 24 x 8 channel bonding for up to 960Mbps of broadband data. -

Best Practices for Keeping Your Home Network Secure1
BEST PRACTICES FOR KEEPING YOUR HOME 1 NETWORK SECURE Don't be a victim; cyber criminals may leverage your home network to gain access to personal, private, and confidential information. Help protect yourself and your family by observing some basic guidelines and implementing the following mitigations on your home network. COMPUTING AND ENTERTAINMENT DEVICE RECOMMENDATIONS Electronic computing devices including computers, laptops, printers, mobile phones, tablets, security cameras, home appliances, cars and other “Internet of Things” devices must all be secured in order to prevent attack. Most home entertainment and utility devices, such as home monitoring systems, baby monitors, Internet of Things (IoT), Smart Devices, Blu-ray™2 players, streaming video players, and video game consoles are capable of accessing the Internet, recording audio, and/or capturing video. Implemented security measures can ensure these devices don’t become the weak link in your home protection. 1. Upgrade to a Modern Operating System and Keep it Up-To-Date The most recent version of any operating system (OS) inevitably contains security features not found in previous versions. Many of these security features are enabled by default and help prevent common attack vectors. Increase the difficulty for an adversary to gain privileged access by utilizing the latest available and supported OS for desktops, laptops, and other devices. Enable automatic update functionality inside the OS. If automatic updates are not possible, download and install patches and updates from a trusted vendor minimally on a monthly basis. 2. Exercise Secure User Habits To minimize ransomware threat, backup data on external drives and portable media. Disconnect external storage when not in use. -
Wireless WAN Branches Rely on LTE & 5G First
Wireless WAN Branches Rely on LTE & 5G First In branch stores and offices, wired connectivity isn’t agile enough. Enterprises that can’t function without access to laptops, printers, IoT devices, and cloud applications have been embracing a cellular-driven approach to maximize connection reliability and flexibility. The new standard is the Wireless WAN Branch, which puts LTE and 5G first and is delivered through all-in-one, cloud-managed wireless edge routers. of organizations are investigating business cases and defining use cases or service portfolios based on 5G. — Infosys The Requirements of Today’s Connection-Reliant Branches Integrated Our financial planning offices require flexible WAN capabilities, as well as the ability to protect sensitive client information with a small IT Security team. We require an all-in-one solution that provides the security features we need to comply with wide-ranging regulations. During emergencies, we must be ready to set up a temporary Hybrid WAN command center at a moment’s notice. Pop-up cellular solutions allow us to focus on protecting the community and our officers Flexibility instead of worrying about where the nearest cable plug-in is located. Management With restaurants in every state, it’s impossible to send an IT specialist to address every issue. To troubleshoot, push out security updates, or From change a configuration, we use a cloud-based network management Anywhere system. We monitor locations nationwide from easy-to-read dashboards. It’s the only way to manage such a large network. Our clinics must have excellent Wi-Fi coverage for doctors and High- nurses to use technologies and access patient data anywhere in the building. -

AT&T and Cradlepoint Deliver One of the First and the Most
AT&T and Cradlepoint Deliver One of the First and the Most Comprehensive Portfolio of Enterprise-Tailored 5G Solutions in the U.S. Expanding Current Offerings with IT-Focused 5G Enterprise Solutions for Branch and Mobile Dallas, Texas, and Boise, Idaho – April 27, 2021 – AT&T (NYSE:T) and Cradlepoint are expanding their joint network offerings with one of the first and the most comprehensive portfolio of 5G solutions in the U.S. using AT&T Wireless Broadband – the first nationwide business-focused broadband network with 5G coverage to over 230 million people in 14,000 cities and towns. The new solutions combine clean-slate-designed Cradlepoint 5G wideband adapters and routers, and its NetCloud Service, with AT&T's nationwide wireless broadband network, data plans, and an AT&T management option for Cradlepoint devices. Together with AT&T Wireless Broadband, these comprehensive, enterprise-tailored 5G solutions give businesses the flexibility to choose the solution, speed, quality of service, and management structure that fits their needs, with no overage charges. Built for 5G, Built for I.T. When it comes to 5G wireless wide-area network (Wireless WAN) connectivity, enterprises want more than just a simple work-from-home solution and one-size-fits-all data plans. They want to support a broad set of branch and mobile use cases. They need increased end-to-end security and the tools to manage the entire Wireless WAN lifecycle – from deployment to daily operations – or to use an AT&T-managed service to do it for them. Together, AT&T and Cradlepoint offer a comprehensive portfolio of end-to-end 5G solutions in the U.S. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

WWAN Device Management with Wavelink Avalanche Manage Your Mobile Devices Both Inside and Outside the Four Walls
WWAN Device Management with Wavelink Avalanche Manage Your Mobile Devices Both Inside and Outside the Four Walls Wavelink Avalanche® is the industry’s leading solution for automated wireless device management. A comprehensive, vendor-independent management solution for the wireless enterprise, Avalanche eases the configuration, deployment and management of wireless networks, while offering extensive flexibility by supporting a wide range of mobile devices and infrastructure. With Avalanche you are able to bring all your mobile devices under the control of a management system that provides provisioning, maintenance and security. The power of Avalanche can reach well beyond the four-walls of an enterprise. Avalanche is designed to work seamlessly across networks, whether they are on a managed WLAN, using Wi-Fi or over more diverse wireless WAN connections such as cellular networks. Delivering success over the Wireless Wide Area Network Unlike dealing with a wireless LAN which is under your total control, a wireless WAN presents new challenges as coverage cannot be assumed. As a result, these challenges require a management solution that is robust enough to operate over any kind of network that carriers operate. Avalanche provides device management support regardless of the medium available. Whether the connection is via Wi-Fi or WWAN, Avalanche allows administrators to seamlessly carry out their duties without ever inhibiting end-user productivity. Avalanche is also built to be sensitive to the characteristics of a WWAN connection, allowing for limited bandwidth and variable latency. Security Management of any kind over a network should be secure, but encryption over a public medium such as the Internet or over a wide area connection is critical. -

The Future of Personal Area Networks in a Ubiquitous Computing World
Copyright is owned by the Author of the thesis. Permission is given for a copy to be downloaded by an individual for the purpose of research and private study only. The thesis may not be reproduced elsewhere without the permission of the Author. The Future of Personal Area Networks in a Ubiquitous Computing World A thesis presented in partial fulfillment of the requirements for the degree of Master of Information Sciences in Information Systems at Massey University, Auckland New Zealand Fei Zhao 2008 ABSTRACT In the future world of ubiquitous computing, wireless devices will be everywhere. Personal area networks (PANs), networks that facilitate communications between devices within a short range, will be used to send and receive data and commands that fulfill an individual’s needs. This research determines the future prospects of PANs by examining success criteria, application areas and barriers/challenges. An initial set of issues in each of these three areas is identified from the literature. The Delphi Method is used to determine what experts believe what are the most important success criteria, application areas and barriers/challenges. Critical success factors that will determine the future of personal area networks include reliability of connections, interoperability, and usability. Key application areas include monitoring, healthcare, and smart things. Important barriers and challenges facing the deployment of PAN are security, interference and coexistence, and regulation and standards. i ACKNOWLEDGEMENTS Firstly, I would like to take this opportunity to express my sincere gratitude to my supervisor – Associate Professor Dennis Viehland, for all his support and guidance during this research. Without his advice and knowledge, I would not have completed this research. -

Computer Networking 101 (HH – Rev1)
Computer Networking 101 (HH – rev1) Henrietta Hankin Library 215 Windgate Drive Chester Springs, PA 19425 Phone: (610) 321-1700 [email protected] www.ccls.org/hankin https://www.facebook.com/HankinBranchLibrary Computer Networking 101 Page 1 Computer Networking 101 (HH – rev1) Workshop Topics: Fundamentals Network Protocols Home Network Components Diagnostics Outline of Workshop: 1. Fundamentals a. What is a computer network? b. Local Area Networks (LANs) c. Wide Area Networks (WANs) d. Virtual Private Network (VPN – AKA Tunneling) e. The Internet f. Peer-to-Peer Networks g. Server-based Networks h. Wireless Local Area Networks (WLANs) 2. Network Protocols a. TCP/IP b. Ethernet c. Ethernet Standards (802.3, 10BaseT, 100BaseT) d. Wireless Protocols (802.11xxx) 3. Home Network Components - Hardware a. PC/Laptop with Network interface Card (NIC) b. Cable Modem c. Router, Switch, Hub d. LAN Cabling e. Network Printer 4. Home Network Components – Software a. Peer-to-peer b. Domain Name Server (DNS) c. Dynamic Host Configuration Protocol (DHCP) d. Firewall 5. Network Diagnostics a. ipconfig command b. ping command c. Command to identify all active network components d. Wireshark Page 2 Computer Networking 101 (HH – rev1) Fundamentals What is a computer network? A computer network consists of a collection of computers, printers and other devices that are connected together so that they can talk to each other. Local Area Networks (LANs), Wide Area Networks (WANs) and Virtual Private Networks (VPNs) are all examples of computer networks. Local Area Networks (LANs) LANs connect computers and other devices that are located physically close to each other. A computer network in a house or office is an example of a LAN. -

Home Network System FAQ 20170202
FAQ Home Network System As of February 2, 2017 FAQ for quick setup and easier use - Index STEP 1 Open the package and confirm the accessories Accessories Page 2-5 Basic Concept Page 7-11 & Operation STEP 2 Set up main unit (Hub) System Initial Setup Page 12-14 STEP 3 Install the Home Network app. Application Page 15-18 STEP 4 Make sure your mobile device is connected to Application Page 15-18 your Wi-Fi® network. STEP 5 Cordless Handset Page 19-28 Set up accessories HUB Page 29-33 Indoor Camera Page 34-41 Outdoor Camera Page 42-49 Motion Sensor Page 50-53 Window / Door Sensor Page 54-56 Water Leak Sensor Page 57 Class Break Sensor Page 58 Indoor Siren Page 59 Access Keypad Page 60 Keychain Remote Page 61 Backup Battery Page 62 Smart Plug Page 63-64 Full HD Camera Page 65-67 1 Accessories - What are the accessories for? HUB (KX-HNB600) Indoor Camera (KX-HNC200/210) • Full color camera with night vision and built-in microphone • Joins all system devices together for live monitoring and recording • Connects to your landline for making and receiving calls • Built-in motion sensor (visual detection), sound sensor, • Supports SD card connection for recording camera video and temperature sensor can be used to trigger other and audio. actions (camera recording, turning on a light, etc.) • Built-in microphone and speaker for two-way communication Outdoor Camera (KX-HNC600) Window / Door Sensor (KX-HNS101) • Full color camera with night vision and built-in microphone for live monitoring and recording • Detects when the corresponding window or door is • Built-in motion sensor (visual detection), sound opened. -

Wireless Networks DCAP607/DCAP311
Wireless Networks DCAP607/DCAP311 Edited by: Dr. Manmohan Sharma WIRELESS NETWORKS Edited By Dr. Manmohan Sharma Printed by EXCEL BOOKS PRIVATE LIMITED A-45, Naraina, Phase-I, New Delhi-110028 for Lovely Professional University Phagwara SYLLABUS Wireless Networks Objectives: Sr. No. Topics 1. Introduction to Wireless Networks. IEEE Standards for Wireless Networks. Wireless Networks Applications. Types of Wireless Networks. Benefits of Wireless Networks. 2. Wireless System Architecture: Wireless System Components, Network Architecture. Information Signals. Radio Frequency and Light Signal Fundamentals: Wireless Transceivers, understanding RF Signals, Working of Light Signals 3. Types of Wireless Networks: WPAN, WLAN, WMAN Wireless PAN: Components: User Devices, Radio NIC, USB Adapters, Wireless Routers, Bluetooth Dongles etc. Wireless PAN Systems: SOHO Equipments, Printing, Accessing Internet, Accessing PDA’s, Mobile Phones Wireless PAN Technologies: IEEE 802.15. Bluetooth Version 1 and Version 2. 4. Wireless LAN: Meaning, Components: User Devices, Radio NIC’s, Access Points, Routers, Repeaters, And Antennae. SOHO Applications: Internet Access, Printing, Remote Accessing. Public Wireless LAN’s, and AdHoc Wireless LAN’s 5. Wireless MAN: Meaning and Components: Bridges, Bridges Vs. Access Points, Ethernet to Wireless Bridges, Workgroup Bridges 6. Wireless MAN Systems: Point to Point Systems, Point to Multi Point, Packet Radio Systems. 7. Wireless WAN: WAN User Devices, Base Stations, Antennae. Wireless WAN Systems: Cellular-Based Wireless WANs, First-Generation Cellular, Second-Generation Cellular, Third-Generation Cellular. 8. Space-Based Wireless WANs: Satellites, Meteor Burst Communications 9. Wireless Networks Security: Security Threats, Unauthorized Access, Middle Attacks, DoS Attack (Denial of Service). Sr. No. Topics 1. Introduction to Wireless Networks. IEEE Standards for Wireless Networks. -

Introduction
Introduction NES440 Wireless Networks NES440 Wireless Networks 1 NES440 Wireless Networks 3 Outline What is “Wireless and Mobile Networking”? What is wireless networking? What is Mobility? Degrees of Mobility History of Wireless Types of Wireless Networks Categories of Wireless Networks Comparison among the types of wireless networks Wireless Spectrum Why go wireless? Ubiquitous computing Benefits of Wireless Networking Applications of Wireless networks Statistics and Trends of Wireless Networks NES440 Wireless Networks 5 What is “Wireless and Mobile Networking”? NES440 Wireless Networks 6 What is Wireless Networking? NES440 Wireless Networks 7 What is Wireless Networking? Enabling people to communicate and access applications and information without wires Information is transmitted using electromagnetic (EM) waves Providing people with the freedom of movement and ability to easily and dynamically extend applications to different parts of a building, city, or anywhere in the world Also called tether-less (or tether-free) communication Characteristics on an EM wave: Travels in the air at the speed of light (c = 3x108 m/s) Has a frequency (f) and wavelength (l) l is the distance occupied by a single cycle of the signal l = c / f Example: for the 2.4GHz Wi-Fi signals, l = 12.5 cm NES440 Wireless Networks 8 What is Mobility? Initially, the Internet and Telephone Networks were designed assuming that the user terminals are stationary. That is: No change of location during a call or connection User terminals access