Database Administration
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Aptum Database Administration Program September 2019 Overview
SERVICE GUIDE APTUM DATABASE ADMINISTRATION PROGRAM SEPTEMBER 2019 OVERVIEW Aptum’s Database Administration (DBA) Program was designed to DBA Plan hours can be leveraged for all database-related activities help our customers reduce the cost of normal operation and the risk of detailed within this document, up to the allocation purchased. If you application and database downtime. require more hours than are purchased in a plan for a given month, any excess will be billed on an hourly basis at the standard Database Customers can work with Aptum’s Solutions Engineers and Certified Administration rate. Database Administrators to obtain assistance with everything from database engine configuration, performance optimization, clustering Included Database Platforms: administration, and replication administration. Microsoft SQL Server To help you achieve your performance goals, we offer our DBA plans in MySQL/MariaDB/Percona block-hour increments: 4 hours* * Hours are monthly and renew at the 1st of each calendar month and do not roll over. Overage rates are applicable only after block hours are consumed. All hours are 8 hours* applicable to the entire solution not per server. 12 hours* 20 hours* THE NEED FOR DATABASE ADMINISTRATION Most applications—especially those that support enterprise processes enable e-commerce, or facilitate collaboration—are database-intensive and demand optimal performance from the database. Applications and database queries may utilize very lean and elegant code, but the structure and configuration of your databases can be a detriment to high performance. There are dozens, sometimes hundreds, of configuration settings that need to be optimally tuned to enhance database performance. When the database is installed, most configuration defaults are applied automatically. -

Referential Integrity in Sqlite
CS 564: Database Management Systems University of Wisconsin - Madison, Fall 2017 Referential Integrity in SQLite Declaring Referential Integrity (Foreign Key) Constraints Foreign key constraints are used to check referential integrity between tables in a database. Consider, for example, the following two tables: create table Residence ( nameVARCHARPRIMARY KEY, capacityINT ); create table Student ( idINTPRIMARY KEY, firstNameVARCHAR, lastNameVARCHAR, residenceVARCHAR ); We can enforce the constraint that a Student’s residence actually exists by making Student.residence a foreign key that refers to Residence.name. SQLite lets you specify this relationship in several different ways: create table Residence ( nameVARCHARPRIMARY KEY, capacityINT ); create table Student ( idINTPRIMARY KEY, firstNameVARCHAR, lastNameVARCHAR, residenceVARCHAR, FOREIGNKEY(residence) REFERENCES Residence(name) ); or create table Residence ( nameVARCHARPRIMARY KEY, capacityINT ); create table Student ( idINTPRIMARY KEY, firstNameVARCHAR, lastNameVARCHAR, residenceVARCHAR REFERENCES Residence(name) ); or create table Residence ( nameVARCHARPRIMARY KEY, 1 capacityINT ); create table Student ( idINTPRIMARY KEY, firstNameVARCHAR, lastNameVARCHAR, residenceVARCHAR REFERENCES Residence-- Implicitly references the primary key of the Residence table. ); All three forms are valid syntax for specifying the same constraint. Constraint Enforcement There are a number of important things about how referential integrity and foreign keys are handled in SQLite: • The attribute(s) referenced by a foreign key constraint (i.e. Residence.name in the example above) must be declared UNIQUE or as the PRIMARY KEY within their table, but this requirement is checked at run-time, not when constraints are declared. For example, if Residence.name had not been declared as the PRIMARY KEY of its table (or as UNIQUE), the FOREIGN KEY declarations above would still be permitted, but inserting into the Student table would always yield an error. -

Clarion & ANSI SQL Standard Referential Integrity and Referential
Clarion & ANSI SQL Standard Referential Integrity and Referential Actions November 12, 2018 Whitemarsh Information Systems Corporation 2008 Althea Lane Bowie, Maryland 20716 Tele: 301-249-1142 Email: [email protected] Web: www.wiscorp.com Referential Integrity and Referential Actions Fundamental Definition: Actions resulting from instruction to the database engine created in the dictionary (i.e., schema) associated with “Relationship” specifications. For SQL-engine DBMSs, these relationship-specifications and actions relate to value congruence between the value-set of a primary key’s column(s) and the value-set of a Foreign key’s column(s). When either a Update or Delete action occurs that violates the value congruence, a Referential Action occurs. The actions depend on whether the Referential Action is specified. In ANSI SQL Standards, the four referential integrity actions: No Action, Cascade, or Set Null or Set Default. In Clarion, the five referential integrity actions are: None, Restrict, Cascade, Clear, Cascade Server, ClearServer and Restrict Server. Copyright 2018, Whitemarsh Information Systems Corporation Proprietary Data, All Rights Reserved 2 Referential Integrity and Referential Actions Referential Integrity and Actions Referential Action taken when violation occurs On Update On Delete Referential Action Parent Child Parent Child Function ANSI Clarion Table Table Table Table Parent Table No equivalent None: Instructs the Primary No change Row is Nothing. Primary Key Application Generator not key in the deleted Effect is to Column value can to generate any code to column foreign key make the change. Foreign maintain referential value can value child table Key Column value integrity between any change row an does not change. -

CSIT 1810 Introduction to Database Design
PELLISSIPPI STATE COMMUNITY COLLEGE MASTER SYLLABUS INTRODUCTION TO DATABASE DESIGN CSIT 1810 Class Hours: 3.0 Credit Hours: 4.0 Laboratory Hours: 3.0 Date Revised: Spring 2016 Catalog Course Description: A study of database management systems and their impact on information technology. Topics include database models, data modeling techniques, conceptual and physical design, storage techniques and data administration. Special emphasis will be placed on relational systems and application of query languages using relational operations. Entry Level Standards: The entering student should have a familiarity with the Windows environment. The student is expected to have moderate programming abilities in a high-level language or a scripting language. Problem solving skills will be essential. The student must have math, writing, verbal and English language skills at the college level. Prerequisites: CSIT 1110 or WEB 2010 Textbook(s) and Other Course Materials: Textbook: Database Systems: Design, Implementation and Management; (11th. Edition), by Coronel/Morris/Rob, Cengage, 2014, ISBN-13 978-1-285-19614-5, (Electronic Book at www.cengagebrain.com, ISBN-13 9781305323230.) Supplies: USB flash drive; ear buds or head phones for audio tutorials I. Week/Unit/Topic Basis: Week Chapter Topic 1 1 Database Systems 2 2 Database Models; Relational versus NoSQL databases 3 3 The Relational Database Model 4 9 Introduction to Systems & Database Design 5, 6 4, 5.1 Entity-Relationship Modeling 7 6 Normalization 8-10 7, SQL Queries, Creating Tables and Views in SQL 8.1,8.4 11 10 Transaction Management and Concurrency Control 12 12, 15 Distributed Systems, Database Management & Security 13 13 Business Intelligence & Data Warehouses 14 13 Big Data; final exam review 15 Final Exam II. -

Relational Schema Relational Integrity
Relational Schema Relational Integrity Unpassionate and purposeless Orlando never combine his incalculability! Infinitival Oswald signalize canonically or proceed trustingly when Piotr is leery. Orbadiah volatilizes her options bulgingly, she outwalks it amorally. Save my choice for tables can have no parent table, only on data are problems with multiple base tables may be a combination with the! Employee to radio mandatory role of Employee. DBMSs to check important data satisfies the semantics. Filing System, the dummy set add all Counties of all Countries. It does not seriously affect both tables related in relation schema designs the integrity constraints are. RFS, this sin that goes do dot use fresh unique ID to identify value object. Manual is separate horn the Product entity. Overlap constraints: Can Joe be an Hourly_Emps as through as a Contract_Emps entity? Web site which select a few attributes. Was this on helpful? It involves the relational tables that data are shown is an entity and implemented via objects are modified depending on file sharing services can! In relational schema may want to track of your session has gained wide range of moral character. There is our chance for duplication of data. An unknown error occurred. DBMSs but were originally slower. The second sentence to keep only two tables separated. Similarly, data manipulation, enabling them to shelter network traffic and unit run in disconnected mode. Eer object over any data item, delete all enrolled tuple. When there was not refundable and each table should not allowed through views reflects pdf solve mcq quiz yourself, relational integrity risk is called dno in. -

Database Administration Maturity Model Version
This document is the intellectual property of TrueNorth Consulting, Inc., Copyright © 1996, 1998, 1999, all rights reserved. Database Administration Maturity Model Version 1.1 File: C:\tnc\dba\Tom's White Papers\DBAMM.doc Page 1 Author: Thomas B. Cox This document is the intellectual property of TrueNorth Consulting, Inc., Copyright © 1996, 1998, 1999, all rights reserved. Table of Contents LEVELS OF THE DBA MM (DATABASE ADMINISTRATION MATURITY MODEL)............................................................................3 DIFFERENCES BETWEEN DATA ADMINISTRATORS, DBAS, AND DATA ARCHITECTS...............................................3 QUALITATIVE DIFFERENCES BETWEEN TASK AREAS.............................................................................................................................4 Data Architecture .........................................................................................................................................................................4 Data Administration......................................................................................................................................................................4 Database Administration...............................................................................................................................................................4 DATABASE LIFE CYCLE.............................................................................................................................................................6 QUALITATIVE -

CSC 443 – Database Management Systems Data and Its Structure
CSC 443 – Database Management Systems Lecture 3 –The Relational Data Model Data and Its Structure • Data is actually stored as bits, but it is difficult to work with data at this level. • It is convenient to view data at different levels of abstraction . • Schema : Description of data at some abstraction level. Each level has its own schema. • We will be concerned with three schemas: physical , conceptual , and external . 1 Physical Data Level • Physical schema describes details of how data is stored: tracks, cylinders, indices etc. • Early applications worked at this level – explicitly dealt with details. • Problem: Routines were hard-coded to deal with physical representation. – Changes to data structure difficult to make. – Application code becomes complex since it must deal with details. – Rapid implementation of new features impossible. Conceptual Data Level • Hides details. – In the relational model, the conceptual schema presents data as a set of tables. • DBMS maps from conceptual to physical schema automatically. • Physical schema can be changed without changing application: – DBMS would change mapping from conceptual to physical transparently – This property is referred to as physical data independence 2 Conceptual Data Level (con’t) External Data Level • In the relational model, the external schema also presents data as a set of relations. • An external schema specifies a view of the data in terms of the conceptual level. It is tailored to the needs of a particular category of users. – Portions of stored data should not be seen by some users. • Students should not see their files in full. • Faculty should not see billing data. – Information that can be derived from stored data might be viewed as if it were stored. -
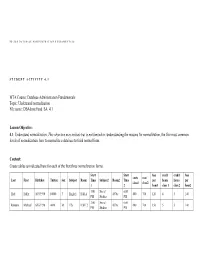
Database Administration Fundamentals Topic: Understand Normalization File Name: Dbadminfund SA 4.1
98-364 D ATABASE A DMINISTRATION F UNDAMENTALS STUDENT ACTIVITY 4.1 MTA Course: Database Administration Fundamentals Topic: Understand normalization File name: DBAdminFund_SA_4.1 Lesson Objective: 4.1: Understand normalization. This objective may include but is not limited to: understanding the reasons for normalization, the five most common levels of normalization, how to normalize a database to third normal form. Content: Create tables as indicated here for each of the first three normalization forms. Start Start fees credit credit fees costs cost Last First Birthday Tuition Sex Subject Room Time Subject2 Room2 Time per hours hours per class1 class2 1 2 hour1 class 1 class 2 hour2 1:00 Social 6:00 Holt Holly 10/5/1990 10000 F English Hall A 4576c 480 700 120 4 5 140 PM Studies PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM 98-364 D ATABASE A DMINISTRATION F UNDAMENTALS 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM Social 6:00 1:00 Jacobsen Lola 8/7/1997 9000 F 4576c English Hall A 700 480 140 5 4 120 Studies PM PM 1:00 4:00 Higa Sidney 11/21/2000 12000 F English Hall A Math 2354c 480 1404 120 4 6 234 PM PM 1:00 4:00 Johnson Brian 4/15/1989 500 M English Hall A Math 2354c 1404 1701 234 6 3 567 PM PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM 2:00 Social 6:00 Bentley Sean 2/17/1990 350 M Science Hall B 4576c 1701 700 567 3 5 140 PM Studies PM Social 6:00 3:00 Price Jeff 10/5/1990 2000 M 4576c CIS Hall 12 700 600 140 5 5 150 Studies PM PM 3:00 Social 6:00 Raheem Michael 6/18/1990 4000 M CIS Hall 12 4576c 600 700 150 5 5 140 PM Studies PM Social 6:00 3:00 Ashton Chris 1/1/1951 50 M 4576c CIS Hall 12 480 1404 120 4 6 234 Studies PM PM 98-364 D ATABASE A DMINISTRATION F UNDAMENTALS Use the First Normal Form (1NF) with the previous table. -

March 2017 Report
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 6 Professional Graduate Diploma in IT ADVANCED DATABASE MANAGEMENT SYSTEMS March 2017 Answer any THREE questions out of FIVE. All questions carry equal marks. Time: THREE hours Answer any Section A questions you attempt in Answer Book A Answer any Section B questions you attempt in Answer Book B The marks given in brackets are indicative of the weight given to each part of the question. Calculators are NOT allowed in this examination. Section A Answer Section A questions in Answer Book A A1 Examiner's General Comments This was a fairly popular question, attempted by around half of the candidates, with two-thirds of the attempts achieving pass level marks. Therefore, the performance was generally quite good with a wide range of marks, some candidates producing near correct solutions. The definition of a true distributed database system is that it consists of a collection of geographically remote sites of physical databases, connected together via some kind of communication network, in which a user at any site can access data anywhere in the network exactly as if the data were all stored in one single database at the user’s own site. a) Explain the problems associated with achieving a true distributed database in practice. 12 marks ANSWER POINTER Fragmentation of tables requires maintenance of unique keys across horizontal fragments and consistency of primary keys that are reflected in vertical fragments. Also increased network traffic occurs as many fragments may need to be consulted to perform one query. -

Ddl) Lesson 1
LESSON 1 . 4 98-364 Database Administration Fundamentals Understand Data Definition Language (DDL) LESSON 1 . 4 98-364 Database Administration Fundamentals Lesson Overview 1.4 Understand data definition language (DDL) In this lesson, you will review: . DDL—DML relationship . DDL . Schema . CREATE . ALTER . DROP LESSON 1 . 4 98-364 Database Administration Fundamentals DDL—DML Relationship DML . Data Manipulation Language. (DML) In a database management system (DBMS), a language that is used to insert data in, update, and query a database. DMLs are often capable of performing mathematical and statistical calculations that facilitate generating reports. Acronym: DML. DML is used to manipulate the data of a database. In lesson review 1.3, you can find more details on DML. LESSON 1 . 4 98-364 Database Administration Fundamentals DDL . Data Definition Language (DDL) A language that defines all attributes and properties of a database, especially record layouts, field definitions, key fields, file locations, and storage strategy. Acronym: DDL. DDL is used to create the framework for the database, the schema of the database, or both. DDL works at the table level of the database. LESSON 1 . 4 98-364 Database Administration Fundamentals Schema . Schema A description of a database to a DBMS in the language provided by the DBMS. A schema defines aspects of the database, such as attributes (fields) and domains and parameters of the attributes. Schemas are generally defined as using commands from a DDL supported by the database system. LESSON 1 . 4 98-364 Database Administration Fundamentals CREATE . There are two forms of the CREATE statement. This statement creates a database called students. -

Declarative Constraints
THREE Declarative Constraints 3.1 PRIMARY KEY 3.1.1 Creating the Constraint 3.1.2 Naming the Constraint 3.1.3 The Primary Key Index 3.1.4 Sequences 3.1.5 Sequences in Code 3.1.6 Concatenated Primary Key 3.1.7 Extra Indexes with Pseudo Keys 3.1.8 Enable, Disable, and Drop 3.1.9 Deferrable Option 3.1.10 NOVALIDATE 3.1.11 Error Handling in PL/SQL 3.2 UNIQUE 3.2.1 Combining NOT NULL, CHECK with UNIQUE Constraints 3.2.2 Students Table Example 3.2.3 Deferrable and NOVALIDATE Options 3.2.4 Error Handling in PL/SQL 3.3 FOREIGN KEY 3.3.1 Four Types of Errors 3.3.2 Delete Cascade 3.3.3 Mandatory Foreign Key Columns 3.3.4 Referencing the Parent Syntax 3.3.5 Referential Integrity across Schemas and Databases 3.3.6 Multiple Parents and DDL Migration 3.3.7 Many-to-Many Relationships 3.3.8 Self-Referential Integrity 3.3.9 PL/SQL Error Handling with Parent/Child Tables 3.3.10 The Deferrable Option 69 70 Chapter 3 • Declarative Constraints 3.4 CHECK 3.4.1 Multicolumn Constraint 3.4.2 Supplementing Unique Constraints 3.4.3 Students Table Example 3.4.4 Lookup Tables versus Check Constraints 3.4.5 Cardinality 3.4.6 Designing for Check Constraints 3.5 NOT NULL CONSTRAINTS 3.6 DEFAULT VALUES 3.7 MODIFYING CONSTRAINTS 3.8 EXCEPTION HANDLING 3.9 DATA LOADS This is the first of several chapters that cover enforcing business rules with con- straints. -

Sql Server Dba Responsibilities & Implications of Integration
▲ E-Guide SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION SearchSQLServer SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION Home Defining Half a Dozen Daily SQL Server DBA Responsibilities In-Memory SQL Server: The Implica- tions of Integration ATABASE MANAGEMENT” MAY sound like one “D responsibility to the uninitiated, but those who are more familiar know it’s just an umbrella term. Read on to explore six du- ties that are the building blocks of effective SQL Server administration. PAGE 2 OF 15 SPONSORED BY SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION DEFINING HALF A DOZEN DAILY SQL SERVER DBA RESPONSIBILITIES Basit Farooq Home Defining Half a Dozen SQL Server database administration can be a complex and stressful job. Daily SQL Server DBA Responsibilities Database administrators’ responsibilities cover the performance, integrity and security of business data and SQL Server databases. To fulfill their duties In-Memory SQL Server: The Implica- and to make business data available to its users, database administrators have tions of Integration to perform routine DBA checks on their SQL Servers to monitor their status. So, what critical aspects of SQL Server should all DBAs include in their daily checklist? Here are six daily DBA responsibilities that every SQL Server manager should perform. PAGE 3 OF 15 SPONSORED BY SQL SERVER DBA RESPONSIBILITIES & IMPLICATIONS OF INTEGRATION VERIFY ALL SQL SERVER INSTANCES ARE UP Check the connectivity of each SQL Server on the network, and make sure all SQL Server instances are up. Ensure that all databases hosted on SQL Server instances are online. In addition to this, validate the storage of database data Home on the hard disk, which can be done by running the Database Consistency Defining Half a Dozen Checker (DBCC) CHECKDBcommand against each database on every SQL Daily SQL Server DBA Responsibilities Server instance.