Total Network Monitor Documentation
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

COMP11 Lab 1: What the Diff?
COMP11 Lab 1: What the Diff? In this lab you will learn how to write programs that will pass our grading software with flying colors. Navigate into your COMP11 directory and download the starter code for this lab with the following command: pull-code11 lab01 (and then to see what you've got) cd lab01 ls You Do Like We Do (15 mins) There is nothing magical about how we test and grade your programs. We run your program, give it a preselected input, and check to see if its output matches our expectation. This process is repeated until we're convinced that your solution is fully functional. In this lab we will walk you through that process so that you can test your programs in the same way. Surely you recall running our encrypt demo program in Lab 0. Run this program again and specify the word \tufts" as the word to encrypt (recall that you must first enter \use comp11" if you have not added this command to your .cshrc profile). Nothing new here. But what if you wanted to do that again? What if you wanted to do it 100 more times? Having to type \tufts" during every single execution would get old fast. It would be great if you could automate the process of entering that input. Well good news: you can. It's called \redirecting". The basic concept here is simple: instead of manually entering input, you can save that input into a separate file and tell your program to read that file as if the user were entering its contents. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -
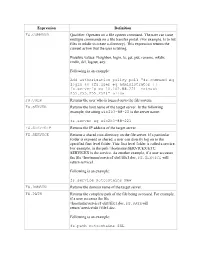
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Andv's Favorite Milk Oualitv Dairv Comp Commands Bulk Tank SCC
Andv's Favorite Milk Oualitv Dairv Comp Commands Bulk Tank SCC Contribution: Command: ECON Select 6 This gives you the contribution of each cow to the bulk tank SCC. I find in most herds, the top 1% high SCC cows usually contribute less than 20o/o of the total SCC. When you see the number go to 25o/o or higher. you know that high producing cows are the main contributors. You can see the effect of removins cows from the herd on the bulk tank SCC. General Herd Information Command: Sum milk dim scc lgscc prvlg logl drylg for milk>o lact>O by lctgp This gives you a quick summary of each lactation to review. It puts all factors on one page so you can determine areas of concern. Herd SCC Status: Command: Sum lgscc=4 lgscc=6 for lgscc>O by lctgp This gives you the status of the SCC of all cows on test by lactation group and by herd. It will show you the number and percentage of cows with SCC of 200,000 and less, the number and percentage of cows with SCC of 201,000 to 800,000 and the number and percentage of cows with SCC over 800,000. My goal is to have at least 80% of all animals in the herd under 200,000. I want at least 85% of first lactation animals, 80% of second lactation animals, andl5o/o of third/older lactation animals with SCC under 200,000. New Infection Rate: Command: Sum lgscc:4 prvlg:4 for lgscc>O prvlg>O by lctgp This command only compares cows that were tested last month to the same cows tested this month. -

Beyond Compare User Guide
Copyright © 2012 Scooter Software, Inc. Beyond Compare Copyright © 2012 Scooter Software, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Published: July 2012 Contents 3 Table of Contents Part 1 Welcome 7 1 What's. .N..e..w............................................................................................................................. 8 2 Standa..r.d.. .v..s. .P..r..o..................................................................................................................... 9 Part 2 Using Beyond Compare 11 1 Home. .V...i.e..w.......................................................................................................................... -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Command Window – Basic Commands
Command Window – Simple Commands help lists all commands p: switch to your P-drive c: switch to the computer’s C-drive dir list all files in a directory (aka “folder”); e.g. dir (list all files in current directory) dir myfolder (list all files in subdirectory myfolder) cd change directory; e.g. cd myfolder (move to subdirectory myfolder) cd .. (move up one directory level) md make (create) a directory; e.g. md myfolder (make a subdirectory called myfolder) copy copy files; e.g. copy oldfile newfile copy source.f90 myfolder\source.f90 ren rename files; e.g. ren oldfile newfile erase erase (delete) a file; e.g. (or del) erase unwanted.txt fc file compare; e.g. fc file1 file2 type list the contents of a file type somefile.txt type somefile.txt ¦ more (list contents, one page at a time) Wildcards (* and ?) Can be used to match length-unspecified strings (*) or individual letters (?); e.g. copy *.f90 *.bak dir solve.f?? Command Syntax and Options Most commands have various options; e.g. dir /p – list files, one page at a time To find the syntax and options available for any particular command use the /? option; e.g. dir /? History Use the and arrows on keyboard to recover previous commands. Use F7 to get a list of previous commands and arrow up and down to choose one to reissue. Editors An editor called notepad comes with the operating system: notepad myfile.f90 Running Programs You can run any program simply by typing its name; e.g. to run windows explorer: explorer Batch Files To avoid having to type a long sequence of commands it is convenient to put them all in a batch file – identified by the .bat extension. -

Session 1171-2017
Paper 1171-2017 Let SAS® Do Your DIRty Work Richann Watson, Experis ABSTRACT Making sure that you have saved all the necessary information to replicate a deliverable can be a cumbersome task. You want to make sure that all the raw data sets and all the derived data sets, whether they are Study Data Tabulation Model (SDTM) data sets or Analysis Data Model (ADaM) data sets, are saved. You prefer that the date/time stamps are preserved. Not only do you need the data sets, you also need to keep a copy of all programs that were used to produce the deliverable, as well as the corresponding logs from when the programs were executed. Any other information that was needed to produce the necessary outputs also needs to be saved. You must do all of this for each deliverable, and it can be easy to overlook a step or some key information. Most people do this process manually. It can be a time-consuming process, so why not let SAS® do the work for you? INTRODUCTION Making a copy of all information needed to produce a deliverable is time-consuming and is normally done using • Windows® Explorer: copy and paste to a new folder for archiving • Command interpreter (CMD shell)*: copy or move commands Both of these methods require you to create an archive directory and either copy or move the files manually. Most people go the route of using Windows Explorer due to familiarity. This can tie up your computer while the files are being archived. CMD is faster and commands can be set to run in the background if you know how to access CMD and know the necessary commands. -

Layer Comps Layer Comps a Layer Comp Allows Us to Save the Current State of a File So That We Can Switch Between Various Versions of the Document
video 32 Layer Comps Layer Comps A layer comp allows us to save the current state of a file so that we can switch between various versions of the document. Layer comps can keep track of three things: the position of layers, the visibility of layers and the layer styles (layer ef- fects). Note that layer comps will not keep track of the stacking order of layers. When working with layer comps, you’ll need to open the Layer Comps panel, which can be accessed via the Window menu at the top of the interface. To create a layer comp, first set up your document so that it’s in a state you would like Photoshop to remem- ber. Then, click on the New icon at the bot- tom of the Layer Comps panel. A dialog will appear where you can give the layer comp a name and specify what you’d like it to keep track of. There are check boxes for Visibil- The Layer Comps Panel. ity, Position and Appearance (Layer Style). When you’re done, click the OK button and you will see the name of the comp appear in the Layer Comps panel. To the right of the layer comp name are three icons which indicate what information the comp is keeping track of. From left to right, the icons represent layer visibility, position and styles. When one of the icons is grayed out, it means that the layer comp is not keeping track of that information. You can update the settings for a layer comp at any time by double-clicking to The icons to the right of the name indicate the right of the layer comp name. -

Learning Objectives ECHO Commands. Command. 10. Explain
. SA Learning Objectives After completing this chapter you will be able to: 1. List commands used in batch files. 2. List and explain batch file rules. 3. Use a batch file with a shortcut. 3. Explore the function of the REM, 4. Use the SHIFT command to move param- ECHO commands. eters. 4. Explain the use of batch files with shortcuts. 5. Use the IF command with strings for condi- 5. Explain the purpose and function of the tional processing. GOTO command. 6. Test for null values in a batch file. 6. Explain the purpose and function of the 7. Use the IF EXIST /IF SHIFT command. test for the existence of a file or a 7. Explain the purpose and function of the IF subdirectory. command. 8. Use the SET command. 8. Explain the purpose and function of the IF 9. Use the environment and environmental EXIST /IF variables in batch files. 9. Explain the purpose and function of the IF 10. Use the IF ERRORLEVEL command ERRORLEVEL command. XCOpy to write a batch file for testing exit 10. Explain the purpose and function of writing codes. programs. 11. Use the FOR...IN...OO command for repeti- 11. Explain the purpose and function of the tive processing. environment and environmental variables. 12. Use the CALL command in a batch file. 12. Explain the use of the SET command. 13. Explain the purpose and function of the Chapter Overview FOR...IN...OO command. You learned in Chapter 10 how to write simple 14. Explain the purpose and function of the batch files and use replaceable parameters. -

UNC COMP 590-145 Midterm Exam 3 Solutions Monday, April 6, 2020
UNC COMP 590-145 Midterm Exam 3 Solutions Monday, April 6, 2020 1 / 26 General comments Haven't quite finished grading E3 (sorry), but will by Wednesday. But let's walk through the solutions. Random question order and answer order UNC COMP 590-145 Midterm Exam 3 Solutions 2 / 26 Exam 3 solutions Question 3: Write a protocol Write a Clojure protocol for git objects using defprotocol, including methods and parameters. Assume that the implementation will provide a way to access the type and data of a git object. (Hint: what does your program need to do with every git object, regardless of what type it is?) (defprotocol GitObject (address [_]) (write-object [_])) UNC COMP 590-145 Midterm Exam 3 Solutions 3 / 26 Exam 3 solutions Question 4: Testing Write a test for the following code using Speclj. Use a different namespace. (ns math) (defn product "Compute the product of a function mapped over a sequence of numbers. example, (product inc [1 2 3]) is 24, and (product inc []) is 1." [f xs] (reduce * 1 (map f xs))) UNC COMP 590-145 Midterm Exam 3 Solutions 4 / 26 Exam 3 solutions Question 4: Testing (ns math-spec (:require [speclj.core :refer [describe it should=]] [math :as sut])) (describe "product" (it "returns 1 when the sequence is empty" (should= 1 (sut/product inc []))) (it "returns the correct answer for a non-empty sequence" (should= 24 (sut/product inc [1 2 3])))) UNC COMP 590-145 Midterm Exam 3 Solutions 5 / 26 Exam 3 solutions Question 5: Implement a protocol Implement the following protocol for lists (which have type clojure.lang.PersistentList).