0.5.1 - 2016-09-05 Dionaea • Don’T Report ‘Connection.Free’ Incident to Early to Prevent Segmentation Faults
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Scapy–A Python Tool for Security Testing
ien r Sc ce & te S u y p s t m e o m C s Journal of Bansal and Bansal, J Comput Sci Syst Biol 2015, 8:3 f B o i l o a DOI: 10.4172/jcsb.1000182 l o n r g u y o J Computer Science & Systems Biology ISSN: 0974-7230 Research Article Article OpenOpen Access Access Scapy–A Python Tool For Security Testing Shipra Bansal1* and Nitin Bansal2 1Department of Computer Applications, Lovely Professional University, Jalandhar, India 2Department of Management, Lovely Professional University, Jalandhar, India Abstract Security Testing is the essential method of any information System and this method is used to detect flaws in the security measures in an Information System which protect the data from an unauthorized access. Passing through the Security testing method does not ensure that flaws are not present in the System. Python is a new emerging Programming language. This research paper looks into the tool named Scapy which is based on Python language; lists out some vital commands, explanation with examples and uses of Security Testing. This research paper, being introductory one tries to give a brief description and understandable usage of the security Testing tool. Keywords: Security testing; Python; Scapy; Flaws Stackless is used for concurrency and PyPy has greater speed execution than CPython. Its extension is .py normally. Introduction Introduction to scapy Security is defined as “No unauthorized Access of information”. Security is very essential to maintain the integrity of System [1,2]. Scapy is a tool for manipulating interactive packets. This tool is Security Testing is the first step to detect flaws in the security measures totally based on Python language. -

Build Network Packets with Scapy
SharkFest ’18 Europe Handcrafted packets build network packets with Scapy Uli Heilmeier Krones AG #sf18eu#sf18eu •• ImperialImperial RidingRiding SchoolSchool RenaissanceRenaissance ViennaVienna •• OctOct 2929 -- NovNov 22 Scan me... pak=IP(dst="10.80.49.*")/ \ TCP(dport=[23,21], \ sport=RandShort(),flags="SAUFP") ans,unansw=sr(pak, timeout=1) #sf18eu • Imperial Riding School Renaissance Vienna • Oct 29 - Nov 2 Stacking layers dnspkt= \ Ether()/ \ IPv6(dst="2001:db8::1")/ \ UDP()/ \ DNS(rd=1,qd= \ DNSQR(qname="wireshark.org")) #sf18eu • Imperial Riding School Renaissance Vienna • Oct 29 - Nov 2 #sf18eu • Imperial Riding School Renaissance Vienna • Oct 29 - Nov 2 Working with packets dnspkt[UDP] #or dnspkt[2] dnspkt[DNSQR].qtype="AAAA" dnspkt[IPv6].payload dnspkt[Ether].payload.payload dnspkt[UDP].chksum=0xffff dnspkt[UDP].chksum del(dnspkt[UDP].chksum) #sf18eu • Imperial Riding School Renaissance Vienna • Oct 29 - Nov 2 Working with packets dnspkt.sprintf("Destination IP is %IPv6.dst%") dnspkt.summary() ls(dnspkt) dnspkt.command() dnspkt.pdfdump(filename="../dns.pdf") #sf18eu • Imperial Riding School Renaissance Vienna • Oct 29 - Nov 2 ff ff ff ff ff ff 00 00 00 00 00 00 86 dd 60 00 Ethernet 00 00 00 27 11 40 00 00 00 00 00 00 00 00 00 00 dst ↵:↵:↵:↵:↵:↵ 00 00 00 00 00 00 20 01 0d b8 00 00 00 00 00 00 src 00:00:00:00:00:00 00 00 00 00 00 01 00 35 00 35 00 27 ff ff 00 00 type 0x86dd 01 00 00 01 00 00 00 00 00 00 09 77 69 72 65 73 IPv6 68 61 72 6b 03 6f 72 67 00 00 01 00 01 version 6 tc 0 fl 0 plen 39 nh UDP hlim 64 src :: dst 2001:db8::1 -

Packet Crafting Using Scapy
Packet Crafting using Scapy by William Zereneh Bachelor of Science, Toronto, 2006 A thesis Presented to Ryerson University in partial fulfillment of the requirements for the degree of Master of Engineering in the Program of Computer Networks Toronto, Ontario, Canada, 2011 ©William Zereneh 2011 Abstract This paper will introduce both Packet Crafting as a testing methodology and the tool that will be used to accomplish all four aspects of this methodology; Packet Assembly, Packet Editing, Packet Re-Play and Packet Decoding. Scapy is an Open Source network programming language based on Python programming language, will be used in this project. The tool will be used to capture packets off the wire, create others by layering protocols as needed, altering the content of Ethernet, Dot3, LLC, SNAP, IP, UDP and ICMP header fields as required and finally launching such packets onto the network. In some cases the responses gathered as a result of launching such packets will not be decoded. As a result of this project, some network vulnerabilities will be explored to fully demonstrate the power of the methodology using Scapy, but never exploited to cause any damage. ii Authorʼs declaration I hereby declare that I am the sole author of this thesis I authorize Ryerson University to lend this thesis to other institutions or individuals for the purpose of scholarly research. William Zereneh I further authorize Ryerson University to reproduce this thesis by photocopying or by other means, in total or in part, at the request of other institutions or individuals for the purpose of scholarly research. William Zereneh iii Acknowledgments This paper would have not be possible if it were not for the constant reminder by my wife and kids that my “home work” has to be done first. -

Scapy Documentation Release 2.0.1
Scapy Documentation Release 2.0.1 Philippe Biondi and the Scapy community October 24, 2009 CONTENTS 1 Introduction 3 1.1 About Scapy........................................3 1.2 What makes Scapy so special...............................3 1.3 Quick demo........................................5 1.4 Learning Python......................................7 2 Download and Installation9 2.1 Overview..........................................9 2.2 Installing Scapy v2.x....................................9 2.3 Installing Scapy v1.2.................................... 10 2.4 Optional software for special features........................... 11 2.5 Platform-specific instructions............................... 12 3 Usage 19 3.1 Starting Scapy....................................... 19 3.2 Interactive tutorial..................................... 19 3.3 Simple one-liners...................................... 42 3.4 Recipes........................................... 46 4 Advanced usage 51 4.1 ASN.1 and SNMP..................................... 51 4.2 Automata.......................................... 60 5 Build your own tools 67 5.1 Using Scapy in your tools................................. 67 5.2 Extending Scapy with add-ons............................... 68 6 Adding new protocols 71 6.1 Simple example...................................... 71 6.2 Layers........................................... 72 6.3 Dissecting......................................... 75 6.4 Building.......................................... 79 6.5 Fields........................................... -

Development of a Fuzzing Tool for the 6Lowpan Protocol César Bernardini, Abdelkader Lahmadi, Olivier Festor
Development of a fuzzing tool for the 6LoWPAN protocol César Bernardini, Abdelkader Lahmadi, Olivier Festor To cite this version: César Bernardini, Abdelkader Lahmadi, Olivier Festor. Development of a fuzzing tool for the 6LoW- PAN protocol. [Technical Report] RR-7817, 2011, pp.50. hal-00645948 HAL Id: hal-00645948 https://hal.inria.fr/hal-00645948 Submitted on 29 Nov 2011 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. INSTITUT NATIONAL DE RECHERCHE EN INFORMATIQUE ET EN AUTOMATIQUE Development of a fuzzing tool for the 6LoWPAN protocol César Bernardini — Abdelkader Lahmadi — Olivier Festor N° 7817 September 2011 Networks and Telecommunications apport technique ISSN 0249-0803 ISRN INRIA/RT--7817--FR+ENG Development of a fuzzing tool for the 6LoWPAN protocol∗ César Bernardini , Abdelkader Lahmadi , Olivier Festor Theme : Networks and Telecommunications Équipe-Projet Madynes Rapport technique n° 7817 — September 2011 — 47 pages Abstract: In this report we detail the development of a fuzzing tool for the 6LoWPAN protocol which is proposed by the IETF as an adaptation layer of IPv6 for Low power and lossy networks. Our tool is build upon the Scapy’s[2] packets manipulation library. -

Packet Inspection and Manipulation for Fun and Profit
Playing With Your Traffic: Exploring the Software- Defined Packet Control Within the IETF Joe Clarke, Distinguished Services Engineer BRKSDN-3014 Abstract This talk covers technology being discussed and developed within the Internet Engineering Task Force (IETF). It is not currently available in a Cisco product release. Software Defined Networking (SDN) combined with Network Function Virtualization (NFV) provide unprecedented programmatic access to drive networks in new and exciting ways. These capabilities lead to dynamic service creation, with Service Function Chaining (SFC) completing the programmable picture, creating a “whole stack” view. Service chaining realizes network virtualization, allowing network services to exchange metadata and be seamlessly deployed into the packet path independent of their physical location. Service chaining, and its underlying standards such as Network Service Header (NSH) offer a innovative way to "software define" packet processing. This session will show the value of service creation and the power that software-defined packet processing can afford. This session will describe a journey that starts by looking at how to program devices and virtual services using both Service Function Chaining and the Network Service Header. Further, this session will explore details of how policy and declarative intent drives the creation of service chains. Examples will be shown on how to inspect traffic, manipulate packets, and inject new flows. This session will focus heavily on programming. Code examples will be provided -
2020– 2022 Batch)
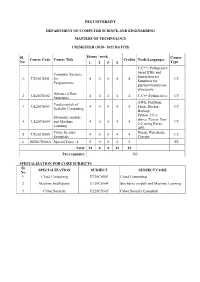
PES UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING MASTERS OF TECHNOLOGY I SEMESTER (2020– 2022 BATCH) Sl. Hours / week Course Course Code Course Title Credits Tools/Languages No. L T P S Type C/C++/ Python/java based IDEs and Computer Systems Instruction set 1. UE20CS501 for 4 0 0 4 4 CC Simulator for Programmers pipelined multicore processors. Advanced Data 2. UE20CS502 4 0 0 4 4 C,C++,Python,Java. CC Structures AWS, PostMan, Fundamentals of 3. UE20CS503 4 0 0 4 4 Flask, Docker, CC Scalable Computing Hadoop. Python 3.5 or Stochastic models above, Tensor flow 4. UE20CS504 and Machine 4 0 0 4 4 CC 2.0, using Keras Learning API. Cyber Security Nmap, Wireshark, 5. UE20CS505 4 0 0 4 4 CC Essentials Claynet. 6. UE20CS506A Special Topic - I 2 0 0 2 2 ST Total 22 0 0 22 22 Pre-requisites Nil SPECIALIZATION FOR CORE SUBJECTS Sl. SPECIALIZATION SUBJECT SUBJECT CODE No. 1. Cloud Computing UE20CS503 Cloud Computing. 2. Machine Intelligence UE20CS504 Stochastic models and Machine Learning 3. Cyber Security UE20CS505 Cyber Security Essentials M. Tech II SEMESTER COMPUTER SCIENCE & ENGINEERING:(BATCH : 2020-2022) Hours / Credits Tools/Languages Course Sl. No. Course Code Course Title week Type L T P S 1. UE20CS551 Topics in Advanced 4 0 0 4 4 C,C++ CC Algorithms * 2. UE20CS552 Distributed 4 0 0 4 4 Wireshark/ C Compiler with CC Computing Network Libraries 3. UE20CS56X Elective –I 4 0 0 4 4 EC 4. UE20CS57X Elective –II 4 0 0 4 4 EC 5. -

Scapy Documentation (!)
Scapy documentation (!) Philippe BIONDI phil(at)secdev.org 2 Contents 1 Introduction 5 1.1 About this document ......................... 5 1.2 What is Scapy ............................ 5 1.3 Scapy’s concepts ........................... 5 1.3.1 Fast packet design ...................... 5 1.3.2 Probe once, interpret many ................. 6 1.3.3 Scapy decodes, it does not interpret ............ 6 I Examples 9 2 Quick start 11 3 Packet manipulation 13 4 Network discovery 15 5 Attacks 17 II Reference 19 6 Packet manipulation 21 6.0.4 User’s methods ........................ 21 6.0.5 Developer’s methods ..................... 23 7 Packet list manipulation 25 7.1 User’s methods ............................ 25 8 Commands 29 8.1 Tools .................................. 29 8.2 Communication commands ..................... 34 8.2.1 Sniff family .......................... 34 8.2.2 Send family .......................... 35 8.2.3 Send and receive family ................... 35 8.3 high-level commands ......................... 37 8.4 Answering machines ......................... 38 3 4 CONTENTS III Extending Scapy 39 9 Adding a new protocol 41 9.1 Definition of a layer ......................... 41 9.2 Fields ................................. 42 9.3 Layers’ methods ........................... 43 9.4 Binding layers ............................. 43 9.5 Layers’ design patterns ........................ 43 9.5.1 For a string whose length is given by another field .... 43 10 Adding a new field 45 10.1 The Field API ............................. 45 11 Adding an answering machine 49 12 Making your own tools 51 13 Scripting Scapy 53 14 Adding a new high-level function 55 IV Internals 57 15 Networking code 59 15.1 Supersockets ............................. 59 15.2 Routing packets ............................ 60 16 Object model 63 1 Introduction 1.1 About this document 1.2 What is Scapy Scapy is a Python program that enables you to forge, dissect, emit or sniff network packets, probe, scan or attack networks. -

Scapy Documentation Release 2.1.0
Scapy Documentation Release 2.1.0 Philippe Biondi and the Scapy community December 14, 2009 CONTENTS 1 Introduction 3 1.1 About Scapy........................................3 1.2 What makes Scapy so special...............................3 1.3 Quick demo........................................5 1.4 Learning Python......................................7 2 Download and Installation9 2.1 Overview..........................................9 2.2 Installing Scapy v2.x....................................9 2.3 Installing Scapy v1.2.................................... 10 2.4 Optional software for special features........................... 11 2.5 Platform-specific instructions............................... 12 3 Usage 19 3.1 Starting Scapy....................................... 19 3.2 Interactive tutorial..................................... 19 3.3 Simple one-liners...................................... 42 3.4 Recipes........................................... 46 4 Advanced usage 51 4.1 ASN.1 and SNMP..................................... 51 4.2 Automata.......................................... 60 5 Build your own tools 67 5.1 Using Scapy in your tools................................. 67 5.2 Extending Scapy with add-ons............................... 68 6 Adding new protocols 71 6.1 Simple example...................................... 71 6.2 Layers........................................... 72 6.3 Dissecting......................................... 75 6.4 Building.......................................... 79 6.5 Fields........................................... -

SCADA Intrusion Detection System Test Framework
SCADA Intrusion Detection System Test Framework By: Henrik Waagsnes Supervisor: Nils Ulltveit-Moe, Associate Professor Ph.D IKT 590 - Master’s thesis Spring 2017 Department of Information and Communication Technology Faculty of Engineering and Science University of Agder Grimstad, 21 May 2017 Henrik Waagsnes SCADA Intrusion Detection System Test Framework Abstract Supervisory control and data acquisition (SCADA) systems play an important role in our critical infrastructure (CI). Several of the protocols used in SCADA communication are old and lack of security mechanisms. This master thesis presents a SCADA Intrusion Detection System Test Framework that can be used to simulate SCADA traffic and detect malicious network activity. The framework uses a signature-based approach and utilize two different IDS engines, Suricata and Snort. The IDS engines include rule-sets for the IEC 60870-5-104, DNP3 and Modbus protocols. The IDS engines ships detected events to a distributed cluster and visualize them using a web interface. The experiments carried out in this project show that there generally is little difference between Suricata and Snort's ability to detect malicious traffic. Suricata is compatible with signatures written in snort lightweight rules description language. I did however, discover some compatibility issues. The purposed framework applies additional latency to the analysis of IDS events. The perceived latency was generally higher for Snort events than for Suricata events. The reason for this is probably the additional processing time applied by the implemented log conversion tool. Keywords: SCADA, IDS, SIEM 2 Henrik Waagsnes SCADA Intrusion Detection System Test Framework Preface This report is the result of the master thesis IKT 590 (30 ECTS) which is part of my fourth semester MSc study at the Faculty of Engineering and Science, University of Agder (UiA) in Grimstad, Norway. -

Denial of Service Attack and Defense
Denial of Service Attack and Defense Authors: Katalin Papp - Regina Birò - Kristian Segnana - Enrico Guarato Teacher: Luca Allodi 20 april 2016 Contents Introduction 4 1 What constitutes a DOS attack? 4 2 Environment Setup 5 Internet architectural model 7 3 TCP/IP stack 7 4 Application layer: HTTP 8 4.1 The GET method . 10 4.2 The POST method . 10 5 Transport layer: TCP, UDP 10 5.1 UDP header . 11 5.2 TCP header . 12 5.3 TCP connection setup . 13 5.4 Vulnerability of 3 way handshake . 14 6 Network layer: IP 14 7 Command line traffic monitoring tools 16 8 Munin 17 9 Wireshark 18 DoS/DDoS attacks 19 10 SYN flood 19 10.1 Description . 19 10.2 Issues and possible solutions . 19 10.3 Mitigation . 20 10.4 Tools: Scapy . 21 10.4.1 Brief Introduction . 21 10.5 Scapy . 21 10.5.1 Usage . 21 2 10.5.2 Python Script . 24 10.5.3 Server DoS . 26 10.5.4 Scapy Conclusion . 28 DDoS with LOIC 29 11 TCP, UDP Flood 29 11.1 Involuntary DDoS . 29 11.2 An example of voluntary DDoS: LOIC . 29 11.3 How to use LOIC on Windows and Linux . 30 11.4 A bit of history and consequences . 32 HTTP POST attack with slowhttptest 34 12 HTTP Post Attack 34 12.1 slowhttptest . 35 Bibliography 38 3 Introduction 1 What constitutes a DOS attack? A Denial Of Service (DoS) attack aims at disrupting the availabiliy of a service or a resource. DoS can mean a variety of things: if someone hacks your facebook account and changes your password and your recovery email, that is effectively a DoS attack. -

Packet Sniffing and Spoofing
SEED Labs – Packet Sniffing and Spoofing Lab 1 Packet Sniffing and Spoofing Lab Copyright © 2006 - 2020 Wenliang Du, All rights reserved. Free to use for non-commercial educational purposes. Commercial uses of the materials are prohibited. The SEED project was funded by multiple grants from the US National Science Foundation. 1 Overview Packet sniffing and spoofing are two important concepts in network security; they are two major threats in network communication. Being able to understand these two threats is essential for understanding se- curity measures in networking. There are many packet sniffing and spoofing tools, such as Wireshark, Tcpdump, Netwox, Scapy, etc. Some of these tools are widely used by security experts, as well as by attackers. Being able to use these tools is important for students, but what is more important for students in a network security course is to understand how these tools work, i.e., how packet sniffing and spoofing are implemented in software. The objective of this lab is two-fold: learning to use the tools and understanding the technologies under- lying these tools. For the second object, students will write simple sniffer and spoofing programs, and gain an in-depth understanding of the technical aspects of these programs. This lab covers the following topics: • How the sniffing and spoofing work • Packet sniffing using the pcap library and Scapy • Packet spoofing using raw socket and Scapy • Manipulating packets using Scapy Readings and Videos. Detailed coverage of sniffing and spoofing can be found in the following: • Chapter 15 of the SEED Book, Computer & Internet Security: A Hands-on Approach, 2nd Edition, by Wenliang Du.