ISG Provider Lens™ Quadrant Report | August 2021 Section Name About This Report
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

LANDESK ANTIVIRUS Powered by Kaspersky Protect Your Endpoints from One Console
LANDESK ANTIVIRUS Powered by Kaspersky Protect Your Endpoints from One Console Every moment you are connected to the LANDESK Antivirus helps you: Internet (and sometimes even when n Deliver the fastest response times to you’re not), you are under attack. minimize your risk of security breaches Today’s cyber attacks have become n Reduce cost and complexity with a extremely dynamic and exponentially centralized solution more complex. LANDESK Antivirus n Detect significant numbers of virus software delivers comprehensive anti- and malware instances missed by malware solutions that are powerful, other solutions through advanced efficient and easy to manage. LANDESK heuristics n Enable IT staff and executives to Antivirus uses the award-winning quickly see which systems are Kaspersky Anti-Virus Engine to to deliver protected and which are vulnerable comprehensive protection from a wide n Provide vulnerability assessments for range of malware including viruses, multiple platforms including Trojans, worms, rootkits, spyware, and Windows, Mac, Linux and HP-UX adware. Security Capabilities: n Kaspersky Lab Awards Real-time protection against multi- vector threats – Protect against Kaspersky Anti-Virus has received viruses, trojans, worms, spyware, multiple highest accolades from leading adware, rootkits, bootkits, independent testing labs: keyloggers, screencapture malware, botnets, zero-day attacks, drive-by download infections and other malicious vectors n System watcher – Monitors and analyzes system operations proactively for suspicious activity -

Ivanti Device and Application Control Version History Since V 2.6
Ivanti Device and Application Control Version History Since v 2.6 Details NEW IN VERSION 5.1 Update 2 [29-May-2018] • More granular control over device attached/detached notifications Additional controls have been added such that the IDAC Control system tray icon remains visible but notifications relating to 'device attached/detached' are now suppressed. For more information refer to https://community.ivanti.com/docs/DOC-67782. • Authorization Wizard now scans inside MSP files Most Windows 10 and Office 2016 updates are delivered as MSP files rather than MSIs. In previous IDAC versions, the Authorization Wizard could only scan inside MSIs making it very difficult to whitelist updates that were delivered as MSPs. We've changed this in 5.1U2 so that the Auth Wizard now scans inside MSPs in addition to MSIs. • Windows 10 version Support We've added support for Windows 10 version 1803 (OS build 17134) which was released by Microsoft on April 30th. Refer to the following community article for details of Windows version support with Ivanti Device and Application Control https://community.ivanti.com/docs/DOC-62154. • Citrix XenApp and XenDesktop Support We've added support for versions 7.15 and 7.17 of Citrix XenApp and XenDesktop. • 7zip library updated We've updated the 7zip library to version 18.01 to address vulnerability CVE-2018-5996. 7zip versions prior to 18.00 contain insufficient exception handling which can lead to multiple memory corruptions and allow remote attackers to cause a denial of service attack or execute arbitrary code. • SQL 2017 Support We've added support for Microsoft SQL 2017. -

Supported Products for ESAP 3.7.8
Firefox https://172.21.158.254/dana-admin/auth/listEsapProducts.cgi?versionid=... Windows ANTI-VIRUS Products PRODUCTS: Marketing Name Display Name 2345安全卫士 (3.x) 2345安全卫士 (3.x) 360 Internet Security (4.x) 360 Internet Security (4.x) 360 Internet Security (5.x) 360 Internet Security (5.x) 360 Internet Security (6.x) 360 Internet Security (6.x) 360 Total Security (4.x) 360 Total Security (4.x) 360 Total Security (5.x) 360 Total Security (5.x) 360 Total Security (6.x) 360 Total Security (6.x) 360 Total Security (8.x) 360 Total Security (8.x) 360 Total Security (9.x) 360 Total Security (9.x) 360天擎 (6.x) 360天擎 (6.x) 360安全卫士 (11.x) 360安全卫士 (11.x) 360杀毒 (1.x) 360杀毒 (1.x) 360杀毒 (3.x) 360杀毒 (3.x) 360杀毒 (5.x) 360杀毒 (5.x) ALYac Enterprise (2.x) ALYac Enterprise (2.x) ALYac Enterprise (3.x) ALYac Enterprise (3.x) AVANSI Antivirus (4.x) AVANSI Antivirus (4.x) AVG Anti-Spyware (7.x) AVG Anti-Spyware (7.x) AVG AntiVirus (10.x) AVG AntiVirus (10.x) AVG AntiVirus (15.x) AVG AntiVirus (15.x) AVG AntiVirus (16.x) AVG AntiVirus (16.x) AVG AntiVirus (2013.x) AVG AntiVirus (2013.x) AVG AntiVirus (2014.x) AVG AntiVirus (2014.x) AVG AntiVirus (2016.x) AVG AntiVirus (2016.x) AVG AntiVirus (7.x) AVG AntiVirus (7.x) AVG AntiVirus (8.x) AVG AntiVirus (8.x) AVG AntiVirus (9.x) AVG AntiVirus (9.x) AVG AntiVirus Business Edition (16.x) AVG AntiVirus Business Edition (16.x) AVG AntiVirus Free (17.x) AVG AntiVirus Free (17.x) AVG AntiVirus Free (18.x) AVG AntiVirus Free (18.x) AVG AntiVirus Free (19.x) AVG AntiVirus Free (19.x) AVG AntiVirus Free (20.x) AVG AntiVirus -

The Forrester Wave™: Endpoint Security Suites, Q2 2018
NOT LICENSED FOR DISTRIBUTION The Forrester Wave™: Endpoint Security Suites, Q2 2018 The 15 Providers That Matter Most To Enterprises And How They Stack Up by Chris Sherman and Salvatore Schiano June 21, 2018 Why Read This Report Key Takeaways In our 21-criteria evaluation of endpoint security Trend Micro, CrowdStrike, And Symantec Lead suite providers, we identified the 15 most The Pack significant ones — Bitdefender, Carbon Black, Forrester’s research uncovered a market in Check Point, Cisco, CrowdStrike, Cylance, ESET, which Trend Micro, CrowdStrike, Symantec, Ivanti, Kaspersky Lab, Malwarebytes, McAfee, Check Point, ESET, Sophos, and Bitdefender are Microsoft, Sophos, Symantec, and Trend Micro — Leaders; Carbon Black, McAfee, Kaspersky Lab, and researched, analyzed, and scored them. This Cisco, Cylance, Microsoft, and Malwarebytes are report shows how each provider measures up to Strong Performers; and Ivanti is a Challenger. help security professionals make the right choice. Security Pros Want An Effective Endpoint Security Suite From Vendors They Trust Buyers want an endpoint security suite that is effective at stopping modern threats without adding to their security team’s complexity. They also want to trust the vendor, both as a strategic partner and as a steward of their data. Behavioral Analysis, Automation, And Real- World Performance Are Key Differentiators As traditional approaches to endpoint security prove less effective, behavioral protection and suite automation have become key differentiators in today’s market. Buyers -
City of Mesa, AZ Contract # 2018011-02 for Information Technology Solutions and Services With
ATTACHMENT 5 City of Mesa, AZ Contract # 2018011-02 for Information Technology Solutions and Services with SHI International Corp. Effective: March 1, 2018 The following documents comprise the executed contract between the City of Meza, AZ and SHI International Corp, effective March 1, 2018: I. Executed Contract II. Mayor and Council Approval III. Supplier Response IV. Original RFP ~ mesa-az AGREEMENT PURSUANT TO SOLICITATION CITY OF MESA AGREEMENT NUMBER 2018011 INFORMATION TECHNOLOGY SOLUTIONS & SERVICES CITY OF MESA, Arizona ("City") Department Name City of Mesa - Purchasing Division Mailing Address P.O. Box 1466 Mesa, AZ 85211-1466 Delivery Address 20 East Main St, Suite 400 Mesa, AZ 85201 Attention Sharon Brause, CPPO, CPPB, CPCP Senior Procurement Officer E-Mail [email protected] Phone (480) 644-2815 Fax (480) 644-2655 AND SHI INTERNATIONAL CORP., ("Contractor") Mailing Address 290 Davidson Ave Somerset, NJ 08873 Remit Address PO Box 952121 Dallas, TX 75395-2121 Attention Meghan Flisakowski, Public Program Manager E-Mail [email protected] Phone 512-517-4088 Fax 732-652-6599 Website www.publicsector.shidirect.com/ Page 1 of 33 CITY OF MESA AGREEMENT PURSUANT TO SOLICITATION This Agreement pursuant to solicitation ("Agreement") is entered into this 27th day of February, 2018, by and between the City of Mesa, Arizona, an Arizona municipal corporation ("City"), and SHI INTERNATIONAL CORP, a New Jersey corporation ("Contractor"). The City and Contractor are each a "Party" to the Agreement or together are "Parties" to the Agreement. RECITALS A. The City issued solicitation number 2018011 ("Solicitation") for INFORMATION TECHNOLOGY SOLUTIONS & SERVICES, to which Contractor provided a response ("Response"); and B. -

Cybersecurity
Cybersecurity Sector Update – April 2021 SPECIALIST INDEPENDENT M&A AND FUNDRAISING ADVISER TO FAST-GROWING TECHNOLOGY BUSINESSES APRIL 2021 1 CYBERSECURITY FAST FACTS CYBERSECURITY FUNDRAISING AND M&A ACTIVITY REMAINS STRONG DESPITE THE CHALLENGES OF A GLOBAL PANDEMIC $8.3bn $21.9bn Invested by VCs +22% -15% Total M&A deal value -36% -6% globally in 2020 transacted in 2020 Value Volume Value Volume $3.7bn $5.5bn Invested by VCs +35% -12% Total M&A deal value -14% -21% globally in Q1 2021 transacted in Q1 2021 Value Volume Value Volume PUBLIC CYBERSECURITY STOCKS ARE TRADING AT ALL-TIME HIGHS, HELPING TO LIFT VALUATIONS IN THE PRIVATE MARKETS +118% 11x LTM rev 3x 24x LTM rev Cybersecurity index Cybersecurity index CrowdStrike stock Paid by CrowdStrike appreciation since valuation appreciation since its IPO in for acquiring Expanse 16th March 2020 June 2019 (+$28.4bn in MC) in Nov 2020 Source(s): Pitchbook (Geography: North America & Europe), Capital IQ APRIL 2021 2 CYBERSECURITY SECTOR SNAPSHOT – APRIL 2021 1 The cybersecurity sector enjoyed another year of strong deal activity ▪ $8.3bn of VC money was invested in the sector in North America and Europe across 632 deals in 2020 (+22% in value but deal count was down by -15%). The strong momentum is set to continue – in the US, cybersecurity businesses already raised $3.6bn in Q1 2021 alone ▪ 2020 was also a new record year for cybersecurity investment in the UK, infosecurity businesses raised over £821m across 73 deals ▪ M&A deal activity remained at high levels compared to a record 2019, amounting to $21.9bn (-36% in value, deal count was down by -6%) ▪ Whilst VC investors were hedging their bets in later stage deals and proven business models, corporate and PE acquirers are not afraid to pay record valuations in highly competitive auctions, e.g. -

Security Software
Infrastructure Software Taxonomy SOFTWARE DEVELOPMENT / DEVOPS IT OPERATIONS MANAGEMENT SECURITY Solutions that enable the Solutions that help to manage Solutions that protect software software development lifecycle, the provisioning, capacity, and systems against malicious including planning, creating, performance, and availability of attacks, unauthorized access and testing, and deploying software an organization’s IT resource use, and other external applications and systems infrastructure and internal risks Infrastructure / Application IT GRC and Service and Identity and Continuous Integration Version Test App / Database Operations Network / App / Advanced Threat SIEM / Security Lifecycle Asset Support Access / Continuous Delivery Management Management Performance Analytics Data Security Protection Analysis Management Management Management Management Monitoring Select Market Participants Select Market Participants Select Market Participants DATA MANAGEMENT CLOUD MANAGED SERVICES COLLABORATION / COMMUNICATION Solutions that manage cloud Solutions that enable groups and Solutions that integrate, cleanse, security, computing, storage, teams to communicate, share, migrate, and manage data across network operations, and coordinate, cooperate, and solve platforms to produce accurate application stacks to automate problems for the purpose of and consistent information and enhance business operations completing a task Project Business Data Quality and Database Data PaaS / aPaaS / Managed Hosting Managed Backup and Communications Agile Project -

Ivanti Device and Application Control Version History Since V2.6
Ivanti Device and Application Control Version History Since v2.6 Details NEW IN VERSION 5.1 Update 3 [18-Dec-2018] • File-Type Filtering for the Portable Device Class The Portable Device class now supports file-type filtering. File filters can be used to limit access to specific file types (e.g. pdf, doc, xls). Up to now, file-type filtering was only available for use with the Removable Storage Devices, Floppy Disk Drives, and DVD/CD Drives device classes. With 5.1 Update 3, file filters can also be used with the Portable Device class. This would enable customers to restrict file transfers to and from mobile phones but allow pictures to be transferred, for example. • Device Control event generated when encrypted media is unlocked Additional logging has been added in 5.1 Update 3 so that an event is generated when encrypted media (e.g. USB key) is unlocked. This log event could then be used to trigger additional actions on the endpoint, for example. • Windows Support Updates We’ve added support for Windows 10 version 1809 (OS build 17763) which was released by Microsoft on Nov 13th. Refer to the following community article for details of Windows 10 version support with Ivanti Device and Application Control https://community.ivanti.com/docs/DOC-62154. We’ve also added support for Windows Server 2019 which was released by Microsoft on Oct 2nd. • Citrix XenApp and XenDesktop Support We’ve added support for version 7.18 of Citrix XenApp and XenDesktop. Components in this Release Component Version SK version 5.1.494 SCOMC version 5.1.500 SXS version 5.1.500 DB version 5.1.500 SMC version 5.1.500 1 ISSUES RESOLVED IN VERSION 5.1 Update 3 [18-Dec-2018] Problem ID Title 51197 Endpoint UI (RTNotify) on crashes randomly with unhandled exception "phase 2 file" 53658 HES 5.0: select user filter and schedule report causes reporting to fail 64411 Card reader unusable after installing agent (Windows 10 1709). -
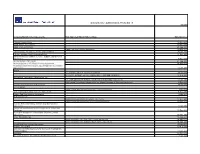
Approved Agreements
General Services Administration, IT Schedule 70 9/4/2018 Company/Manufacturer Agreements GSA Approved EULA/CSAs Listings Date Approved 45Press Privacy Policy 12-Dec-2016 45AIR Terms & Conditions 12-Dec-2016 2SMS Limited Warranty 29-Aug-2013 2SMS End User License Agreement 29-Aug-2013 A10 Networks, Inc. License Terms and Conditions 25-Jan-2018 A Better Solution (ABS) Consulting EULA 15-Dec-2014 Abbott Informatics Software License, Support, and Services Agreement 4-Dec-2015 Abeyon Service Agreement 21-Aug-2018 Ab Initio Software LLC Master License Agreement 24-Aug-2017 Acadis Envisage Technologies, LLC Readiness Suite Master Agreement 12-Oct-2017 Accela Accela Subscription Terms and Conditions 30-Jul-2014 Accela, Inc. Software License, Maintenance Terms and Conditions 16-Sep-2014 Accelerated Technology Laboratories, Inc. ATL LIMS OnDemand Software and Services Subscription Agreement 17-Jun-2016 Accelerated Technology Laboratories, Inc. Master Software & Services Agreement 2-Dec-2013 Accellion Solutions License Agreement 27-Jul-2015 Access Smart Power LogOn Administrator End User License Agreement 7-Apr-2014 ACF Technologies Master License Agreement 8-Nov-2017 Acronis End User License Agreement 4-Mar-2015 ACS Internet LLC Alaska Communications Acceptable Use Policy 17-Dec-2016 Alaska Communications End User License Agreement 17-Dec-2016 Acunetix Web Vulnerability Scanner End User License Agreement 6-Apr-2017 Alaska Communications Services Agreement Terms and Conditions 13-Dec-2016 Actionable Intelligence Technologies Software License Agreement 30-Mar-2015 Active Navigation, Inc. 14-Aug-2012 Active Navigation, Inc. End User License Agreement 14-Aug-2012 Active Navigation, Inc. Software Maintenance Agreement 14-Aug-2012 Actsoft End User License Agreement 23-Oct-2014 Adaptive Computing 22-Sep-2013 Addendum for GSA Customers for licenses to Contrast On- Premises Edition 14-Jan-2015 AdmitMac 31-Dec-2012 ADL Data Systems, Inc. -

Software Sector Summary Report
SOFTWARE SECTOR REPORT Q3 2020 EXECUTIVE SUMMARY Software Q3 2020 » In Q3 2020, the software sector continued to show its resiliency. M&A deal activity and overall M&A deal value witnessed a sharp rebound, and private financing activity continued at a healthy pace. Investors have shown a strong desire for software business models amidst greater cloud adoption and remote work environments, evidenced by favorable performances in public markets and heavy IPO activity with subsequent pops in share price value – Software sector performed well in Q3 with the IGV tech-software index outperforming the S&P 500 by 34.1% LTM as of Q3 2020 – Infrastructure software index grew 148.8% LTM as of Q3 2020, outperforming all other software subsegments » Q3 ’20 saw ~$18Bn in financing deal value and ~$56Bn in M&A deal value - 215 financings, 3.2% lower than Q3 ‘19 - 469 M&A transactions, 22.1% higher than Q3 ’19 » Significant M&A activity in Q3 includes acquisitions in the Security sector: Ivanti’s $930MM acquisition of MobileIron and Fastly’s $775MM acquisition of Signal Sciences » Financial software had some of the largest financing deals in Q3 ‘20 led by the $660MM financing of Robinhood and $650MM financing of Klarna; the Security sector also saw high financing volume » Overall outlook in software growth remains healthy, with most sectors seeing notable growth Select Q3 Active Investors Select Q3 Active Acquirers Notes: Sources: PitchBook, 451 Research, Capital IQ. 2 GCA OVERVIEW The GCA Software Team Sector Coverage US Team VERTICAL SOFTWARE Josh Wepman