Vulnerabilities of Computer Systems: a Test of the VERDICT Computer Security Taxonomy and Its Application to Mobile Ad Hoc Networks
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

File://# Ftp:// Ftps:// Ftpes://# Sftp://# Smb://# Http
CrushFTP supports many different protocols for the VFS that a user can access. FILE://# This is your standard type of folders on your local drives. This could also reference a UNC location on windows if the service is running as a domain user that can access the UNC locations. FTP:// FTPS:// FTPES://# This allows you to use a remote FTP server as the VFS for a user. Some people use an already established IIS FTP server as the back end, but put CrushFTP as the front end giving more controls and protocols. SFTP://# This allows you to use a SFTP server as the back end. OpenSSH on a Linux server is often used as the back end. SMB://# This allows you to connect to a Samba or Windows file server as the backend and provide the credentials. Usually in the format of "smb://user\domain:pass@servername/share/". HTTP:// HTTPS://# This allows you to point to another CrushFTP server and use that as the back end. The HTTP methods used are only valid to another CrushFTP server. It uses specific calls a CrushFTP server expects for file management. WEBDAV:// WEBDAVS://# This allows you to use a standard webdav server as the back end. It makes all the queries about files and dir listings using the webdav XML calls. GDRIVE://# (Disabled due to changes made by google. May come back at a later date after re-evaluating.) RFILE://# Special VFS method that launches new "shells" impersonating the user logging in. Its not super fast, and has a lot of overhead, but some unique scenarios need this method of impersonation if the SMB:// method doesn't work for them. -

Curs 7 Servicii De file Sharing
Curs 7 Servicii de file sharing Gestiunea Serviciilor de Ret, ea 17 noiembrie 2011 GSR Curs 7, Servicii de file sharing 1/45 Moto Jesus saves! The rest of us better make backups. GSR Curs 7, Servicii de file sharing 2/45 Partajarea fis, ierelor SSH. rsync NFS Samba FTP ^Incheiere ^Intreb˘ari GSR Curs 7, Servicii de file sharing 3/45 Suport I \Unix and Linux System Administration" I Chapter 8 { Storage (Section \Storage area networking") I Chapter 18 { The Network File System I Chapter 30 { Cooperating with Windows (Section \Sharing files with Samba and CIFS") I \Professional Linux System Administration" I Chapter 12 { File and Print Sharing GSR Curs 7, Servicii de file sharing 4/45 Outline Partajarea fis, ierelor SSH. rsync NFS Samba FTP ^Incheiere ^Intreb˘ari GSR Curs 7, Servicii de file sharing 5/45 Partajarea fis, ierelor I file sharing I distribut, ie de cont, inut/date/informat, ie I probleme I drepturi de acces I autentificare I consum de resurse (l˘at, ime de band˘a) I interfat, ˘ade utilizare I scalabilitate { num˘arde utilizatori, num˘arde accese I HTTP/FTP, Peer-to-Peer, SSH, rsync, NFS, Samba GSR Curs 7, Servicii de file sharing 6/45 HTTP/FTP I HTTP I universal disponibil, num˘armare client, i (browsere) I suport de securitate (HTTPS) I num˘armare de aplicat, ii I nu are implicit suport pentru transferuri part, iale I wget --continue I folosit, ^ıngeneral pentru download; pentru upload se foloses, te SSH/FTP I necesit˘aacces s, i configur˘arila nivel de server I FTP I din ce ^ınce mai put, in utilizat I suport redus comparativ cu HTTP I -

File Transfer Ipv6 Readiness Includes FTP, FTP/S, SFTP and HTTP Interoperability Testing with Select Applications
File Transfer IPv6 Readiness Includes FTP, FTP/S, SFTP and HTTP Interoperability Testing with Select Applications Andy White, CTO File Transfer Consulting, LLC www.filetransferconsulting.com – ftexperts on Twitter 608-208-1800 (US) June 8, 2011 (ISOC's “World IPv6 Day”) Abstract The world is out of IPv4 addresses and the time of IPv6 is at hand. This paper explores existing file transfer technology used for bulk data exchange under the lens of IPv6 and highlights issues to consider during strategic or tactical planning. Summary results from a series of IPv6 interoperability tests illuminate the findings and recommendations. File Transfer IPv6 Readiness - White Paper and Interoperability Testing - Page 1 of 11 Copyright 2011 File Transfer Consulting, LLC - www.filetransferconsulting.com - ftexperts on Twitter Table of Contents Abstract ......................................................................................................................................................... 1 Table of Contents .......................................................................................................................................... 2 Background ................................................................................................................................................... 3 File Transfer Application Concerns ........................................................................................................... 3 IPv6 Interoperability of File Transfer Software ............................................................................................ -

Creating a Patch and Vulnerability Management Program
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-40 Version 2.0 Title: Creating a Patch and Vulnerability Management Program Publication Date(s): November 2005 Withdrawal Date: July 2013 Withdrawal Note: SP 800-40 is superseded by the publication of SP 800-40 Revision 3 (July 2013). Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: NIST Special Publication 800-40 Revision 3 Title: Guide to Enterprise Patch Management Technologies Author(s): Murugiah Souppaya, Karen Scarfone Publication Date(s): July 2013 URL/DOI: http://dx.doi.org/10.6028/NIST.SP.800-40r3 Additional Information (if applicable) Contact: Computer Security Division (Information Technology Lab) Latest revision of the SP 800-40 Revision 3 (as of June 19, 2015) attached publication: Related information: http://csrc.nist.gov/ Withdrawal SP 800-40 Version 2 provides basic guidance on establishing patch announcement (link): management programs, and guidance to organizations with legacy needs. Date updated: June Ϯϯ, 2015 Special Publication 800-40 Version 2.0 Creating a Patch and Vulnerability Management Program Recommendations of the National Institute of Standards and Technology (NIST) Peter Mell Tiffany Bergeron David Henning NIST Special Publication 800-40 Creating a Patch and Vulnerability Version 2.0 Management Program Recommendations of the National Institute of Standards and Technology Peter Mell Tiffany Bergeron David Henning C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 November 2005 U.S. -
Crushclient Documentation # Commands
CrushClient Documentation # A leading "L" character instructs the client to apply the command to the local client versus to the remote client. lls would sit your current local folder, lcd changes the local folder. Only the file transfer commands do not have an "L" version. (put, get, diffput, diffget) If a path being referenced has a space in it, the path must be quoted. Example: put "some file.txt" "/some folder/my file.txt". Backslash quote escaping is permitted as well. The "local" client doesn't need to be local at all though, both clients can be remote and files can be streamed through the CrushClient. Commands can be sent into he background with a "&" at the end of them. Example: put file.txt remote.txt& There are different ways to start CrushClient. If started with a script, no input will be taken, all input will be read line by line from the script as if you were physically typing it. Don't forget the quit command at the end or the client will wait indefinitely for more input... A script is typically ended with two lines. wait, then quit. java -jar CrushTunnel.jar java -jar CrushTunnel.jar https://demo:[email protected]/demo/ java -jar CrushTunnel.jar https://demo:[email protected]/demo/ file://c:/temp/ java -jar CrushTunnel.jar script my_commands.txt java -jar CrushTunnel.jar inline_script "connect https://demo:[email protected]/demo/;put file.txt;wait;quit;" Example: http://user:[email protected]:port/path/ or https://crushftp.com/ or https://crushftp.com/ demo/ The url must end with a slash. -

How to Log Admin in As Regular User Webdev
How To Log Admin In As Regular User [webdev] 1 / 3 How To Log Admin In As Regular User [webdev] 2 / 3 Alternately, regular SQL can be used for setting the DAV flag on. The DAV ... It is impossible to log on as "nobody" so it's impossible to use owner permissions of the resource. ... The WebDAV admin user "dav" can be deleted.. Password policy is set via G Suite administration. Used to access site admin functions like RSS feeds, REST API access, and WebDAV uploads.. Remote WEBDEV administrator: Configuration to use the statistics - A specific account ... Enter the requested information: login, password, .. Many applications that implement this kind of feature calls them masquerade or impersonate as another user feature. Check with the web .... Create a normal user (not an admin); Try to access their files through webdav using ... The output of your Nextcloud log in Admin > Logging:. If the user did not login, then request.user will be an instance of AnonymousUser . This is a special object used by Django to indicate an .... My admin account can log into the web portal, but new users cannot. ... like you want the "Browse" feature in the admin UI exposed to regular users. ... share's HTTP network access settings), but this requires a WebDAV client.. If you sign in with the credentials of a user with administrator privileges, you can ... unique password for your admin account, and consider changing it regularly. ... WebDAV, FTP, CMIS, and more, all use public services, and therefore include .... by Real Python 16 Comments flask web-dev ... Helpfully, though, I only needed to support a single, “admin” user who was authorized to view reports. -

Release Notes Product: IBM Clinical Development Document Version: 0.1 2020.4.0.0 Area: Development Document Type: Record
Document Title: Technical Release Notes Product: IBM Clinical Development Document Version: 0.1 2020.4.0.0 Area: Development Document Type: Record Technical Notes IBM Clinical Development 2020.4.0.0 Release Date: 28 June 2020 OVERVIEW Purpose: This document provides an overview of IBM Clinical Development 2020.4.0.0 released by IBM Corporation. Background: IBM Clinical Development (formerly Merge eClinicalOS) is a Software as a Service (SaaS) application available for clients to design, deploy, and manage their clinical trials. It provides design tools for each aspect of the design and management process and provides an EDC interface for end-user data collection. It also provides additional tools such as ePRO access, Randomization, Dispense/Shipping Management, Endpoint Adjudication, Medical Coding, and Laboratory Normal collection to help manage different aspects of the trial. Documentation: User manuals for all features in the system are available online within IBM Clinical Development by clicking Online Help from the landing page or User Manuals from the help links in the header. IMPORTANT ALERTS There are two upcoming changes that users need to be aware of and prepare for. 1. CHANGES TO THE IBM CLINICAL DEVELOPMENT WEB ADDRESS Traditionally, users have accessed IBM Clinical Development (ICD) through the secure.eclinicalos.com web address (URL). However, the eClinicalOS name was changed when we transitioned to IBM in 2017. During Q3 2020, we will be updating the web addressDRAFT to secure.clinicaldevelopment.com. More details about the schedule for the transition, redirects, and updating bookmarks will be provided before the change-over. Template #: QA-1356-T6 Licensed Materials – Property of IBM Page 1 of 11 Revision #: Version 06 © Copyright IBM Corp. -
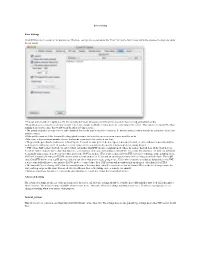
Server Setup Basic Settings Crushftp Has Two Locations for Its Preferences. the Basic Settings Are Located Under the "Prefs
Server Setup Basic Settings CrushFTP has two locations for its preferences. The basic settings are located under the "Prefs" tab on the main screen while the advanced settings are under the file menu. • You can turn on and off logging to a file. If you really don’t care what goes on in the server, you don’t have to keep permanent log files. • Beep when users connect is useful if you want some form of audio feedback of when users are connecting to the server. This option is not available when running it as a service since that would break the rules of being a service. • The speech enabled is another form of audio feedback that can be used to read most anything. Its default setting is where it reads the username of each user as they connect. • Hide splash screen will hide the initial loading splash screen if you want the server to run in a more invisible mode. • Max users is the maximum number of users that can be connected to the server at one time. • The port is the port that the main server is listening on. If you do not use port 21, do not expect your router/firewall, or other end users routers/firewalls to work properly with your server. If you have several virtual servers you will need to use the advanced prefs for editing the port. • "FTP aware NAT router / firewall." is on by default and makes CrushFTP run in a compliant mode where the router / firewall does all the work for you. -

Crushftpdrive Is an Enterprise Only Feature. If Your License on the Server Is Not an Enterprise License, Crushftpdrive Will Not Function
CrushFTPDrive is an enterprise only feature. If your license on the server is not an Enterprise license, CrushFTPDrive will not function. It requires Win7 and above, or OS X. (Linux and Unix could utilize it in command line daemon mode.) CrushFTPDrive Comparison with some other similar products. It lets you connect to the CrushFTP server as a normal server drive on your machine. So on OS X this will be a network drive on your desktop, and for Windows this will be a M: drive, or other letter of your choosing. From there on, it acts like a network volume. You can copy files to and from it, edit and work on files directly on it, etc. Its not using WebDAV, and its built in caching system makes many common network operations very fast as it doesn't need to keep asking the server for information again and again. Behind the scenes, it looks like a SMB/CIFS server item to the OS, but its actually talking to the CrushFTP server entirely over HTTP(s). The client is deployed through a single click download link on the WebInterface, and it can be branded for its logo, and application name. Its localizable too with all strings being editable. Windows users need to install the included 'helper' service to work around OS limitations, but its a one time operation. The client is self updating every time its launched. You can reach Gigabit speeds through it on a LAN. Identical features on OS X or Windows. On OS X you need to have OS X Fuse installed first for the CrushFTPDrive to work: https:// osxfuse.github.io/ Add the button in the user manager to allow downloading of the CrushFTPDrive program. -
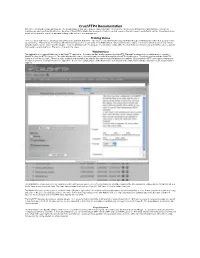
Crushftp4 Documentation Welcome to the Crushftp4 Documentation! the Documentation Is Laid out So That It Is Easily Searchable
CrushFTP4 Documentation Welcome to the CrushFTP4 documentation! The documentation is laid out so that it is easily searchable. It follows the order as such: WebInterface, Main Window, Preferences, UserManager, and User Data File Structure. Each tab of CrushFTP is listed in this document so that you can just search on the tab's name to easily find its section. Every field is listed as well so you may also search on individual settings of the server or user manager too. Training Videos There is a quick start video to get you up and running very easily with CrushFTP. The video is only a few minutes long, but it runs through everything you need to do to get your server up and running. There are also more advanced videos showing you how to use some of the WebInterface, remote administration, setting of a domain name that point to your server, using the built in reports, and a few of the plugins. They are definitely worth checking out. You will just need Quicktime 7 to view them since they are using the H.264 codec to allow for high quality in a very small size. There is no charge for the videos. WebInterface The webInterface is a special folder next to the CrushFTP application. It contains the files used to generate the CrushFTP WebinterFace when using a web browser to connect to CrushFTP using the HTTP:// protocol. The entire WebInterface can be customized and personalized through the CrushFTP UserManager. This allows you to brand the CrushFTP interface to look like you want. -

ICT in Educational Design Processes, Materials, Resources
ICT in Educational Design Processes, Materials, Resources SCIENTIFIC EDITOR Eunika Baron-Polańczyk ICT in Educational Design Processes, Materials, Resources Vol. 12 REVIEW Stanisław Juszczyk Ján Stebila Zielona Góra 2018 THE COUNCIL OF THE PUBLISHING HOUSE Andrzej Pieczyński (przewodniczący), Katarzyna Baldy-Chudzik, Van Cao Long, Rafał Ciesielski, Roman Gielerak, Bohdan Halczak, Małgorzata Konopnicka, Krzysztof Kula, Ewa Majcherek, Marian Nowak, Janina Stankiewicz, Anna Walicka, Zdzisław Wołk, Agnieszka Ziółkowska, Franciszek Runiec (sekretarz) REVIEWERS Stanisław Juszczyk Ján Stebila PROOFREADING Justyna Witczak COVER DESIGN Katarzyna Lotka, Ewa Popiłka TYPESETTING Jolanta Karska © Copyright by Uniwersytet Zielonogórski Zielona Góra 2018 ISSN 2450-3967 ISBN 978-83-842-364-5 OFICYNA WYDAWNICZA UNIWERSYTETU ZIELONOGÓRSKIEGO 65-246 Zielona Góra; ul. Podgórna 50; tel./faks (068) 328 78 64 www.ow.uz.zgora.pl; e-mail: [email protected] TABLE OF CONTENT THE CENTRE OF MEDIA EDUCATION IN ZIELONA GÓRA. INTRODUCTION..........................7 Magdalena Andrzejewska DIFFICULTIES IN LEARNING INTRODUCTORY PROGRAMMING – STUDENTS’ PERSPECTIVE ..........................................................................................15 Eunika Baron-Polańczyk THE SCOPE OF IMPLEMENTATION OF NEW ICT TRENDS IN THE OPINION OF CHILDREN AND ADOLESCENTS .............................................................................27 Erik Bratland TECHNOLOGY AND EDUCATION: WHY DO STUDENTS STILL NEED ACCESS TO SPECIALIZED KNOWLEDGE? .................................................................................37