Comprehensive Vulnerability Analysis of at Commands Within the Android Ecosystem Dave (Jing) Tian∗1, Grant Hernandez1, Joseph I
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Enabling Musical Applications on a Linux Phone
University of Wollongong Research Online Faculty of Creative Arts - Papers (Archive) Faculty of Arts, Social Sciences & Humanities 2009 Enabling Musical Applications On A Linux Phone Greg Schiemer University of Wollongong, [email protected] E. Chen Royal Melbourne Institute of Technology Follow this and additional works at: https://ro.uow.edu.au/creartspapers Part of the Arts and Humanities Commons, and the Social and Behavioral Sciences Commons Recommended Citation Schiemer, Greg and Chen, E.: Enabling Musical Applications On A Linux Phone 2009. https://ro.uow.edu.au/creartspapers/36 Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] ENABLING MUSICAL APPLICATIONS ON A LINUX PHONE Greg Schiemer Eva Cheng Sonic Arts Research Network School of Electrical and Computer Faculty of Creative Arts Engineering University of Wollongong RMIT Melbourne 2522 3000 The prospect of using compiled Arm9 native code of- fers a way to synthesise music using generic music soft- ABSTRACT ware such as Pure data and Csound rather than interpre- tive languages like java and python which have been Over the past decade the mobile phone has evolved to used in mobile devices [1, 2]. A similar approach to mo- become a hardware platform for musical interaction and bile synthesis has been adopted using the Symbian oper- is increasingly being taken seriously by composers and ating system [3]. instrument designers alike. Its gradual evolution has seen The Linux environment is more suited to the devel- improvements in hardware architecture that require al- opment of new applications in embedded hardware than ternative methods of programming. -

Polycom® Realpresence® Mobile for Android® Release Notes
RELEASE NOTES Version 3.9 | Feburary 2018 | 3725-82877-021A1 Polycom® RealPresence® Mobile for Android® Contents What’s New in Release 3.9 . 1 Release History . 3 Security Updates . 4 Hardware and Software Requirements . 4 Products Tested with This Release . 5 Install and Uninstall RealPresence Mobile . 7 System Constraints and Limitations . 7 Resolved Issues . 10 Known Issues . 10 Interoperability Issues . 12 Enterprise Scalable Video Coding (SVC) Solution . 13 Access Media Statistics . 15 Prepare Your Device for Mutual Transport Layer Security . 17 Get Help . 19 Copyright and Trademark Information . 19 What’s New in Release 3.9 Polycom® RealPresence® Mobile version 3.9 includes the features and functionality of previous releases and includes the following new features. Dropped Support for Automatic Detection of Polycom® SmartPairing™ From this version on, the RealPresence Mobile video collaboration software drops support for the automatic detection feature of Polycom SmartPairing. Instead of listing the IP address of nearby Polycom HDX or RealPresence Group Series systems automatically, you will have to enter their IP addresses manually to pair to them. Polycom, Inc. 1 Release Notes Polycom RealPresence Mobile application - Version 3.9 New Device and OS Support Refer to Hardware and Software Requirements for more information. Polycom, Inc. 2 Release Notes Polycom RealPresence Mobile application - Version 3.9 Release History This following table lists the release history of Polycom RealPresence Mobile application. Release History Release -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Openmoko Is Dead. Long Live Openphoenux!
Openmoko is dead. Long live OpenPhoenux! Nikolaus Schaller, Lukas Märdian LinuxTag, Berlin, May 26th, 2012 Agenda Part one: some history Part two: a long way home Part three: rising from the ashes Part four: flying higher Part five: use it as daily phone – software Q&A Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 2 Some history – Past iterations • FIC GTA01 – Neo 1973 – Roughly 3.000 units sold – Production discontinued • Openmoko GTA02 – Neo Freerunner – Roughly 15.000 units sold – Hardware revision v7 – Production discontinued Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 3 Some history – The End (of part I) • FIC and Openmoko got out • Strong community continues development • Golden Delicious taking the lead – Excellent support for existing devices – Shipping spare parts and add-ons – Tuned GTA02v7++ • Deep sleep fix (aka bug #1024) -> Improved standby time • Bass rework -> Improved sound quality Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 4 Agenda Part one: some history Part two: a long way home Part three: rising from the ashes Part four: flying higher Part five: use it as daily phone – software Q&A Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 5 A long way home How do we get to a new open mobile phone? – open kernel for big ${BRAND} – reverse eng. – order from some ${MANUFACTURER} – hope for openness – DIY, “Use the source, Luke!” Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 6 Using the source: Beagleboard Beagleboard – Full Linux support – Open schematics – Open layout – Expansion connectors – Lots of documentation – Components available Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 7 In theory it could fit (Aug. -

An Analysis of Power Consumption in a Smartphone
An Analysis of Power Consumption in a Smartphone Josh Hildebrand Introduction l Mobile devices derive the energy required to operate from batteries that are limited by the size of the device. l The ability to manage energy usage requires a good understanding of where and how the energy is being used. l The advancing functionality of modern smartphones is increasing the pressure on battery lifetime, and increases the need for effective energy management. l Goal is to break down a modern smartphone and measure the power consumption of the devices major subsystems, under a range of usage scenarios. l Results from the breakdown of energy consumption will be validated against two additional mobile devices. l Finally, an analysis of the energy consumption will be performed, and an energy model will be created to allow us to model usage patterns. Methodology / Device Under Test l The approach is to take physical power measurements at the component level on a piece of real hardware. l Three elements to the experimental setup, the device under test, a hardware data acquisition (DAQ) system, and a host computer. l Device under test is the Openmoko Neo Freerunner 2.5G smartphone. Experimental Setup l To measure power to each component, supply voltage and current must be measured. l Current is measured by placing sense resistors on the power supply rails of each component. Resistors were selected such that the voltage drop did not exceed 10mV, less than 1% of the supply voltage. l Voltages were measured using a National Instruments PCI-6229 DAQ. Software l The device was running the Freerunner port of Android 1.5, using the Linux v2.6.29 kernel. -

A Survey Onmobile Operating System and Mobile Networks
A SURVEY ONMOBILE OPERATING SYSTEM AND MOBILE NETWORKS Vignesh Kumar K1, Nagarajan R2 (1Departmen of Computer Science, PhD Research Scholar, Sri Ramakrishna College of Arts And Science, India) (2Department of Computer Science, Assistant Professor, Sri Ramakrishna College Of Arts And Science, India) ABSTRACT The use of smartphones is growing at an unprecedented rate and is projected to soon passlaptops as consumers’ mobile platform of choice. The proliferation of these devices hascreated new opportunities for mobile researchers; however, when faced with hundreds ofdevices across nearly a dozen development platforms, selecting the ideal platform is often met with unanswered questions. This paper considers desirable characteristics of mobileplatforms necessary for mobile networks research. Key words:smart phones,platforms, mobile networks,mobileplatforms. I.INTRODUCTION In a mobile network, position of MNs has been changing due todynamic nature. The dynamic movements of MNs are tracked regularlyby MM. To meet the QoS in mobile networks, the various issuesconsidered such as MM, handoff methods, call dropping, call blockingmethods, network throughput, routing overhead and PDR are discussed. In this paper I analyse the five most popular smartphone platforms: Android (Linux), BlackBerry, IPhone, Symbian, and Windows Mobile. Each has its own set of strengths and weaknesses; some platforms trade off security for openness, code portability for stability, and limit APIs for robustness. This analysis focuses on the APIs that platforms expose to applications; however in practice, smartphones are manufactured with different physical functionality. Therefore certain platform APIs may not be available on all smartphones. II.MOBILITY MANAGEMENT IP mobility management protocols proposed by Alnasouri et al (2007), Dell'Uomo and Scarrone (2002) and He and Cheng (2011) are compared in terms of handoff latency and packet loss during HM. -

HTC One® (M8) Ufocus™ Content to Create Something New
Get creative with Duo Effects Zoe brings your memories to life Pictures taken with HTC One’s Duo Camera can be HTC One automatically creates story clips from your more than just ordinary photos. Choose Camera mode photos and videos with added background music and if you want to apply Duo Effects in Gallery.1 special effects. The depth sensor in HTC One makes it possible to Make the experience more social. Using HTC’s Zoe™ apply different Duo Effects: app and service, you can invite friends to upload photos and videos taken during the same event and co-create a Zoe collection. You can also remix the Make another object or person stand HTC One® (M8) UFocus™ content to create something new. out. Just tap to refocus. Get started guide Apply beautifully rendered seasonal Seasons effects such as Snow that can be shared as videos or photos. Apply a 3D-like effect that allows Dimension you to view your photos from slightly Plus™ different angles. Highlight foregrounds by applying Foregrounder artistic backgrounds to your photos. Before with UFocus © 2014 HTC Corporation. All rights reserved. HTC, the HTC logo, HTC One, the HTC One logo, HTC BlinkFeed, Dimension Plus, Motion Launch, UFocus, and Zoe are trademarks of HTC Corporation. All other company, product and service names mentioned herein For the complete user guide and other helpful resources, go to are trademarks, registered trademarks or service marks of their www.htc.com/support. respective owners. Please also read the Safety and regulatory guide that’s included in the box. 1 For more details, see Things to remember when using the Duo htc.com Camera in the user guide. -

SECOND AMENDED COMPLAINT 3:14-Cv-582-JD
Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 1 of 19 1 EDUARDO G. ROY (Bar No. 146316) DANIEL C. QUINTERO (Bar No. 196492) 2 JOHN R. HURLEY (Bar No. 203641) PROMETHEUS PARTNERS L.L.P. 3 220 Montgomery Street Suite 1094 San Francisco, CA 94104 4 Telephone: 415.527.0255 5 Attorneys for Plaintiff 6 DANIEL NORCIA 7 UNITED STATES DISTIRCT COURT 8 NORTHERN DISTRICT OF CALIFORNIA 9 DANIEL NORCIA, on his own behalf and on Case No.: 3:14-cv-582-JD 10 behalf of all others similarly situated, SECOND AMENDED CLASS ACTION 11 Plaintiffs, COMPLAINT FOR: 12 v. 1. VIOLATION OF CALIFORNIA CONSUMERS LEGAL REMEDIES 13 SAMSUNG TELECOMMUNICATIONS ACT, CIVIL CODE §1750, et seq. AMERICA, LLC, a New York Corporation, and 2. UNLAWFUL AND UNFAIR 14 SAMSUNG ELECTRONICS AMERICA, INC., BUSINESS PRACTICES, a New Jersey Corporation, CALIFORNIA BUS. & PROF. CODE 15 §17200, et seq. Defendants. 3. FALSE ADVERTISING, 16 CALIFORNIA BUS. & PROF. CODE §17500, et seq. 17 4. FRAUD 18 JURY TRIAL DEMANDED 19 20 21 22 23 24 25 26 27 28 1 SECOND AMENDED COMPLAINT 3:14-cv-582-JD Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 2 of 19 1 Plaintiff DANIEL NORCIA, having not previously amended as a matter of course pursuant to 2 Fed.R.Civ.P. 15(a)(1)(B), hereby exercises that right by amending within 21 days of service of 3 Defendants’ Motion to Dismiss filed October 20, 2014 (ECF 45). 4 Individually and on behalf of all others similarly situated, Daniel Norcia complains and alleges, 5 by and through his attorneys, upon personal knowledge and information and belief, as follows: 6 NATURE OF THE ACTION 7 1. -
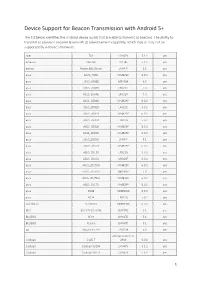
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Compatibility Sheet
COMPATIBILITY SHEET SanDisk Ultra Dual USB Drive Transfer Files Easily from Your Smartphone or Tablet Using the SanDisk Ultra Dual USB Drive, you can easily move files from your Android™ smartphone or tablet1 to your computer, freeing up space for music, photos, or HD videos2 Please check for your phone/tablet or mobile device compatiblity below. If your device is not listed, please check with your device manufacturer for OTG compatibility. Acer Acer A3-A10 Acer EE6 Acer W510 tab Alcatel Alcatel_7049D Flash 2 Pop4S(5095K) Archos Diamond S ASUS ASUS FonePad Note 6 ASUS FonePad 7 LTE ASUS Infinity 2 ASUS MeMo Pad (ME172V) * ASUS MeMo Pad 8 ASUS MeMo Pad 10 ASUS ZenFone 2 ASUS ZenFone 3 Laser ASUS ZenFone 5 (LTE/A500KL) ASUS ZenFone 6 BlackBerry Passport Prevro Z30 Blu Vivo 5R Celkon Celkon Q455 Celkon Q500 Celkon Millenia Epic Q550 CoolPad (酷派) CoolPad 8730 * CoolPad 9190L * CoolPad Note 5 CoolPad X7 大神 * Datawind Ubislate 7Ci Dell Venue 8 Venue 10 Pro Gionee (金立) Gionee E7 * Gionee Elife S5.5 Gionee Elife S7 Gionee Elife E8 Gionee Marathon M3 Gionee S5.5 * Gionee P7 Max HTC HTC Butterfly HTC Butterfly 3 HTC Butterfly S HTC Droid DNA (6435LVW) HTC Droid (htc 6435luw) HTC Desire 10 Pro HTC Desire 500 Dual HTC Desire 601 HTC Desire 620h HTC Desire 700 Dual HTC Desire 816 HTC Desire 816W HTC Desire 828 Dual HTC Desire X * HTC J Butterfly (HTL23) HTC J Butterfly (HTV31) HTC Nexus 9 Tab HTC One (6500LVW) HTC One A9 HTC One E8 HTC One M8 HTC One M9 HTC One M9 Plus HTC One M9 (0PJA1) -

BPOD-I2498 HTC One M7 Lollipop SU-V8.Indd
Android 5.0 operating system update for your HTC ONE®. Software Version: SU6A - Build Number: 5.28.605.12; Baseband: 1.13.41.1209 SU6B - Build Number: 6.21.605.3; Baseband: 1.13.41.1209 Verizon Wireless is pleased to announce an operating system update to Android 5.0 Lollipop. This version brings Android beyond smartphones and tablets, allowing access to apps and Android services on other connected screens like TV’s, cars and wearables. The new material design offers complex animations and 3-D views, 64-bit ABI support and improved runtime. NOTIFICATION PANEL • Lollipop Notification Panel behavior has been adopted • Swipe down once for Notifications • Swipe down a second time for Quick Settings • Toggle Button from KitKat has been replaced by Settings LOCK SCREEN • Lollipop Notification style has been adopted The following Sense settings have been removed • Security > Enable lock screen widgets • Security > Notification Settings • Security > Bypass lock screen on wake HTC One® | For step-by-step instructions on how to perform the download, please visit www.verizonwireless.com/htconeupdate | Data Usage Applies. © 2015 Verizon Wireless. 0315-I2498 1 2 3 HTC ONE LOLLIPOP SETTINGS • “Sound” has been changed to “Sound & notification” in Settings • Notification light settings have been moved to “Sound & notification” • Calendar Picker View offers dropdown capabilities • Search function has been added to settings • Date & Time settings have been reordered • Syncing with new Google Settings and adding in Accessibility • Switch Access • Color Inversion • Color Correction • High Contrast Text • “Sidetone” will be added as a Call Setting, which provides audible feedback to the caller CLOCK • World Clock Globe has been removed for memory considerations | For step-by-step instructions on how to perform the download, please visit www.verizonwireless.com/htconeupdate | Data Usage Applies. -

Call Your Netbsd
Call your NetBSD BSDCan 2013 Ottawa, Canada Pierre Pronchery ([email protected]) May 17th 2013 Let's get this over with ● Pierre Pronchery ● French, based in Berlin, Germany ● Freelance IT-Security Consultant ● OSDev hobbyist ● NetBSD developer since May 2012 (khorben@) Agenda 1.Why am I doing this? 2.Target hardware: Nokia N900 3.A bit of ARM architecture 4.NetBSD on ARM 5.Challenges of the port 6.Current status 7.DeforaOS embedded desktop 8.Future plans 1. A long chain of events ● $friend0 gives me Linux CD ● Computer not happy with Linux ● Get FreeBSD CD shipped ● Stick with Linux for a while ● Play with OpenBSD on Soekris hardware ● $friend1 gets Zaurus PDA ● Switch desktop and laptop to NetBSD ● I buy a Zaurus PDA ● I try OpenBSD on Zaurus PDA 1. Chain of events, continued ● $gf gets invited to $barcamp ● I play with my Zaurus during her presentation ● $barcamp_attender sees me doing this ● Begin to work on the DeforaOS desktop ● Get some of it to run on the Zaurus ● Attend CCC Camp near Berlin during my bday ● $gf offers me an Openmoko Neo1973 ● Adapt the DeforaOS desktop to Openmoko 1. Chain of events, unchained ● $barcamp_attender was at the CCC Camp, too ● We begin to sell the Openmoko Freerunner ● Create a Linux distribution to support it ● Openmoko is EOL'd and we split ways ● $friend2 gives me sparc64 boxes ● Get more involved with NetBSD ● Nokia gives me a N900 during a developer event ● $barcamp_attender points me to a contest ● Contest is about creating an OSS tablet 1. Chain of events (out of breath) ● Run DeforaOS on NetBSD on the WeTab tablet ● Co-win the contest this way ● $friend3 boots NetBSD on Nokia N900 ● Give a talk about the WeTab tablet ● Promise to work on the Nokia N900 next thing ● Apply to BSDCan 2013 ● Taste maple syrup for the first time in Canada ● Here I am in front of you Pictures: Sharp Zaurus Pictures: Openmoko Freerunner Pictures: WeTab Pictures: DeforaOS 2.