Windows Post-Exploitation Command List Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Monitoring, Managing, and Recovering AD DS
Module 13: Monitoring, managing, and recovering AD DS Lab: Recovering objects in AD DS (VMs: 20742B-LON-DC1) Exercise 1: Backing up and restoring AD DS Task 1: Install the Windows Server Backup feature 1. Switch to LON-DC1. 2. In Server Manager, click Manage, and then click Add roles and features. 3. In the Add Roles and Features Wizard, on the Before you begin page, click Next. 4. On the Select installation type page, click Next. 5. On the Select destination server page, click Next. 6. On the Select server roles page, click Next. 7. On the Select features page, in the Features list, select the Windows Server Backup check box, and then click Next. 8. On the Confirm installation selections page, click Install. 9. When the installation finishes, click Close. 10. Click Start, type cmd and then press Enter. 11. In the Command Prompt window, type the following, and then press Enter. cacls C:\Windows\System32\InputMethod\CHS\chsime.exe /E /P system:R Note: This command is only required for the lab environment, and is not part of typical backup procedures. 12. Close the Command Prompt window. Task 2: Create a scheduled backup 1. On LON-DC1, in Server Manager, click Tools, and then click Windows Server Backup. 2. In Windows Server Backup, click Local Backup, and then click Backup Schedule. 3. In the Backup Schedule Wizard, on the Getting Started page, click Next. 4. On the Select Backup Configuration page, click Custom, and then click Next. 5. On the Select Items for Backup page, click Add Items. -

Avid Interplay Production Failover Cluster Host Network Driver Update Procedure
Avid Interplay Production Failover Cluster Host Network Driver Update Procedure Overview: The act of applying network interface driver updates may introduce an error into the settings for the network adapters. To execute the driver updates it has been found that if the host node has the cluster service stopped before hand, the updates can be applied with no negative affects to the system. Microsoft has several server backup references and as always, having a proper backup will mitigate any pain should “a bad thing happen”. References: Backup and Recovery Overview for Windows Server 2008 R2 https://technet.microsoft.com/en-us/library/dd979562(v=ws.10).aspx You can create a backup using the Backup Schedule Wizard to enable backups to be run on a regular schedule or using the Backup Once Wizard to run a one-time backup. You can access both of these wizards from the Windows Server Backup Microsoft Management Console (MMC) snap-in. You can also create regular or one-time backups using the Wbadmin command or Windows PowerShell cmdlets for Windows Server Backup. Here are the articles below about the basic steps, you could take a look. https://technet.microsoft.com/en-sg/library/cc753528.aspx Windows Server 2012R2 - Backup http://www.c-sharpcorner.com/UploadFile/cd7c2e/how-to-create-backup-in-windows-server-2012/ http://krypted.com/windows-server/use-windows-backup-to-back-up-windows-server-2012/ Page | 1 Network Driver Update Steps: The updates will require a fail at some point so please the times and actions to be when a fail over of the Avid Workgroup server service will have a minimal production impact. -
Backupassist V4 Vs. V6
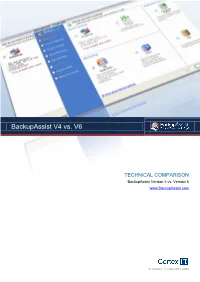
BackupAssist V4 vs. V6 TECHNICAL COMPARISON BackupAssist Version 4 vs. Version 6 www.BackupAssist.com © Cortex I.T. Labs 2001-2009 TECHNICAL COMPARISON BackupAssist V4 vs. V6 2 What are the major new features in BackupAssist v6? Ready for Server 2008 and 2008 R2 New: Windows Imaging Engine for fast drive imaging and hardware independent restore Internet Backup capabilities New: Backup via the Internet using the bandwidth efficient, in- file delta Rsync protocol; fully cloud ready, with AES 256-bit encryption and exact file backups, including NTFS security and attributes. File copying & replication capabilities New: High performance local file copying with single instance store, enabling hundreds of days of file version history Centralized Monitoring New: Monitor multiple jobs and installations using our managed service, and receive one daily email report for all your backup jobs Zip and encrypt (with tape drive New: compressed and encrypted ZIP backups to a wide support on Server 2008) variety of storage options, including tape drive. VSS application and System State New: Back up Microsoft applications like Exchange Server, backup SQL Server, and Hyper-V, and back up the System State on Windows XP, 2003, Vista, 7, 2008 and 2008 R2 using File Replication, Zip or Windows Imaging (Server 2008 R2). Hyper-V backup and restore New: Cover all Hyper-V disaster recovery scenarios with a single host-level image backup. Retrieve files and documents from any Guest Virtual Machine using BackupAssist‟s granular restore capabilities. Restore Console improvements New: File and VSS application restore from any File Replication, Rsync, Zip or Windows Image backup; System State restore from any File Replication or Zip backup; and Exchange mailbox and public folder restore. -

RDX Native Backup Wbadmin Windows Server 2012 with Multiple Cartridges
RDX Native Backup WBAdmin Windows Server 2012 with multiple cartridges CASE: Enable Windows Native Backup on WS2012 to use multiple rdx cartridges (backup disk volumes) from a single RDX device setup in “Fixed mode” Tech links: http://technet.microsoft.com/en-us/library/cc732939(d=printer).aspx http://social.technet.microsoft.com/Forums/windowsserver/en-US/a453ced0-3772-4665- 9c5d-94fd410c4940/unable-to-add-usb-drives-for-backups-server-2012 Short description: To be able to add / preformat several RDX cartridges for use by Windows Native Backup, one must use the command-line tool “wbadmin” from an elevated command prompt. When doing this, the user will encounter a known bug in WS2012 that aborts the disk addon procedure with a message telling that the specified filepath is invalid/not found. A Bugfix can be found here: http://support.microsoft.com/kb/2833738 After running this bugfix, the procedure below works as expected. In the example below, we have first added a backup job using the Windows Server 2012 Std. Backup Wizard GUI. The target disk (backup volume) is a RDX cartridge inserted into a RDX dock set to “Fixed” mode. Then we added another cartridge to the list of available backup volumes using “wbadmin”. To prepare another cartridge to be used do the following 1. Eject the rdx cartridge that was initially added for the backup job. 2. Insert the next cartridge to be used for the set of backup disks 3. Use “ wbadmin get disks” to get the Disk Identifier for the new cartridge (disk) See example 1 below 4. -

Ahsay Technical Document
| Backup everything to cloud / local storage Windows System Backup and Restore Guide CloudBacko Corporation 11 September 2017 A wholly owned subsidiary of CloudBacko Corporation Backup Software Development Company Limited www.cloudbacko.com [HKEx Stock Code: 8290] | Backup everything to cloud / local storage Copyright Notice © 2017 CloudBacko Corporation. All rights reserved. The use and copying of this product is subject to a license agreement. Any other use is prohibited. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system or translated into any language in any form by any means without prior written consent of CloudBacko Corporation Information in this manual is subject to change without notice and does not represent a commitment on the part of the vendor, CloudBacko Corporation does not warrant that this document is error free. If you find any errors in this document, please report to CloudBacko Corporation in writing. This product includes software developed by the Apache Software Foundation (http://www.apache.org/). Trademarks CloudBacko, CloudBacko Pro, CloudBacko Lite, CloudBacko Home and CloudBacko Free are trademarks of CloudBacko Corporation. Amazon S3 is registered trademark of Amazon Web Services, Inc. or its affiliates. Apple and Mac OS X are registered trademarks of Apple Computer, Inc. Dropbox is registered trademark of Dropbox Inc. Google Cloud Storage and Google Drive are registered trademarks of Google Inc. Lotus, Domino, Notes are registered trademark of IBM Corporation. Microsoft, Windows, Microsoft Exchange Server, Microsoft SQL Server, Microsoft Hyper-V, Microsoft Azure, One Drive and One Drive for Business are registered trademarks of Microsoft Corporation. Oracle and Java are registered trademarks of Oracle and/or its affiliates. -

Windows Server 2008 Offline System Recovery Using Windows Technical Notes Server Backup with Avamar
WINDOWS SERVER 2008 OFFLINE SYSTEM RECOVERY USING WINDOWS TECHNICAL NOTES SERVER BACKUP WITH AVAMAR AVAMAR 5.0 TECHNICAL NOTE P/N 300-010-190 REV A01 Table of Contents Overview. 2 Installing Windows Server Backup . 3 Creating a Windows Server Backup image for system disaster recovery.4 Backup image files produced by Windows Server Backup . 6 Backing up the WSB image to an Avamar Server . 7 System recovery for Windows 2008 from a WSB backup . 17 1 Overview Overview This document describes how to use EMC® Avamar® in combination with Microsoft® Windows® Server Backup (WSB) to perform backup and offline disaster recovery of Windows Server 2008 operating systems. This document includes the following procedures to be done in preparation for the event of a disaster: • Installing of the Windows Server Backup (WSB) feature. • Creating a backup image of WSB for system disaster recovery on Windows Server 2008. • Backing up of the WSB image to an Avamar server through the Avamar client for Windows File System Plug-In. Additionally, this document includes the following procedures in the event that a disaster has occurred: • Using Avamar to recover this WSB image to a staging area on a network share. • Recovering the new machine by booting via a Windows Server 2008 bootable DVD which is then configured to install the OS from the WSB backup image. NOTE: Windows Server 2008 R2 is not supported. WINDOWS SERVER 2008 OFFLINE SYSTEM RECOVERY USING WINDOWS SERVER BACKUP WITH AVAMAR TECHNICAL NOTE 2 Installing Windows Server Backup Installing Windows Server Backup Windows Server Backup is not a part of the default Windows operating system installation and must be installed as an optional feature. -
Cheat Sheet –Hyper-Vbackup
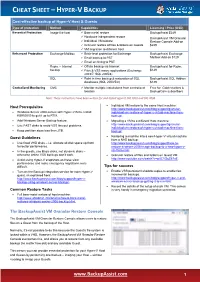
CHEAT SHEET – HYPER-V BACKUP Cost-effective backup of Hyper-V Host & Guests Type of protection Method Capabilities Licensing / Price (USD) Essential Protection Image the host Bare metal restore BackupAssist $249 Hardware independent restore BackupAssist VM Granular Individual VM restore Restore Console Add-on Granular restore of files & folders on Guests $249 VM migration to different host Enhanced Protection Exchange Mailbox Brick-level protection for Exchange BackupAssist Exchange Email backup to PST Mailbox Add-on $129 Email archiving to PST Rsync – Internet Offsite backup via Internet BackupAssist for Rsync backup Files & VSS aware applications (Exchange $129 2003/7, SQL 2005/8) SQL Point in time backup & restoration of SQL BackupAssist SQL Add-on databases (SQL 2000/5/8) $129 Centralized Monitoring CMC Monitor multiple installations from centralized Free for Gold resellers & location BackupCare subscribers Note: These instructions have been written for and tested against SBS 2003 and SBS 2008 Host Prerequisites Individual VM restore to the same Host machine: http://www.backupassist.com/blog/support/granular- Windows Server 2008 comes with Hyper-V Beta. Install individual-vm-restore-of-hyper-v-virtual-machine-from- KB950050 to get it up to RTM. backup/. Add Windows Server Backup feature. Migrating a VM to a different Host machine: Use FAST disks to avoid VSS timeout problems. http://www.backupassist.com/blog/support/granular- individual-vm-restore-of-hyper-v-virtual-machine-from- Keep partition sizes less than 2TB. backup/. Guest Guidelines Restoring a machine into a new Hyper-V virtual machine from a NAS backup: Use fixed VHD disks – i.e. allocate all disk space up front http://www.backupassist.com/blog/support/how-to- for better performance. -

The Real MCTS MCITP Exam 70-648 Prep
Chapter 5 MCTS/MCITP Exam 648 Maintaining an Active Directory Environment Exam objectives in this chapter: ■ Backup and Recovery ■ Offline Maintenance ■ Monitoring Active Directory Exam objectives review: ˛ Summary of Exam Objectives ˛ Exam Objectives Fast Track ˛ Exam Objectives Frequently Asked Questions ˛ Self Test ˛ Self Test Quick Answer Key 355 356 Chapter 5 • Maintaining an Active Directory Environment Introduction Being able to implement a Windows Server 2008 Active Directory environment is only half the battle. You must also be able to maintain the environment to provide minimum downtime and optimum performance of your enterprise. Various solutions and strategies come into play as part of maintenance. Some can be seen as larger “disaster recovery” components, whereas others may simply be “tweaking” the environment to improve user experience. In some situations, “maintenance” may fall somewhere in between—a user account is accidentally deleted, a file is accidentally deleted, or replication is under- performing or not performing at all! In this chapter, you will learn about the many maintenance and management tools offered as a part of Windows Server 2008, as well as some solutions to better improve your Windows Active Directory environment. These topics will be critical not only to your exam success, but also to your success as an IT professional. We will begin this section with a discussion of Windows Server Backup and how it has changed drastically from earlier versions of the Windows server product. Backup and Recovery Most people never think about backup and recovery until they need it. Microsoft has been shipping a simple backup solution with Windows since Windows NT 3.1 back in 1993. -

Active Administrator E-BOOK
Active Administrator E-BOOK Windows Server 2008 R2: Top Tips & Tricks Learn best practices for failover clusters, get Active Directory management tips and find out how to master Windows Server 2008 backup basics in this free guide! Windows Server 2008 R2: Networking in Failover Clusters .................. 1 Managing Active Directory Password Policies ...................................... 4 Backup Basics in Windows Server 2008 R2 .......................... 9 SPONSORED BY I got this many AD tasks done today. Active Administrator 6 What about You? Download a FREE copy of Active Administrator at: WWW.SCRIPTLOGIC.COM/AA6 © 2011 ScriptLogic Corporation. All rights reserved. The ScriptLogic logo is a registered trademark of ScriptLogic Corporation in the United States and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. ACTIVE ADMINISTRATOR E-BOOK BY JOHN MARLIN Windows Server 2008 R2: Networking in Failover Clusters When failure isn’t an option, configuring failover clusters in Windows Server can help ensure high availability. he networking model in E Support for IPv6 nication or iSCSI—not both. Windows Server 2008 and E Support for locating cluster nodes When designing the network Windows Server 2008 R2 on separate, routed subnets infrastructure to connect your cluster T Failover Clustering provides E More fine-grained control over nodes, it’s essential to avoid single more robust and reliable communica- network failure detection points of failure. There are many ways tion among all cluster nodes, which You’ll need to use network hardware you can accomplish this. You can greatly improves the efficiency and marked as “Certified for Windows connect your cluster nodes with dependability of failover clustering. -

Integrating RDX® Quikstor™ Into Windows® Backup with Full System Recovery for Windows Server OS
INTEGRATION BRIEF Integrating RDX® QuikStor™ into Windows® Backup with Full System Recovery for Windows Server OS The built-in Windows Backup included with current Windows operating systems does not support removable media. In order to back up the system or user data with removable storage products and Windows Backup, a user must backup to a xed local disk or incorporate third-party backup software that recognizes the removable storage device. RDX® QuikStor™ has solved this problem by providing a fixed disk mode that allows RDX removable storage to be used with Windows Backup. This guide shows step-by-step instructions on a Windows Server 2012 R2 environment how to: • create a bootable RDX QuikStor media including a system recovery image • set up a backup job including media rotation for full disaster protection • set up deduplication on server volumes to safe disk and backup space • recover from a system crash using RDX QuikStor recovery media tandbergdata.com overlandstorage.com Confi gure RDX QuikStor in fi xed disk mode Use the RDX utility software (version 1.54 or later) to configure RDX QuikStor in fixed disk mode. The software is available on the RDX QuikStor download section of the Tandberg Data website. In addition, the latest firmware should be downloaded and installed.(2.27 or later). Start the RDX Utility and select (click) the drive to work with. Then click on Diagnostic to work with the drive. If there is RDX Media (Cartridge) in the Drive eject it. Select the Utility tab. To use RDX with Windows Backup Click on Change Device Mode and follow the dialog to Confi gure RDX in Fixed disk mode. -

Copyrighted Material
Index Note to the reader: Throughout this index boldfaced page numbers indicate primary discussions of a topic. Italicized page numbers indicate illustrations. Active Directory-integrated zones, 178–179 Symbols & Numbers Active Directory Lightweight Directory % Processor Time counter, 103 Services, 224 802.1x enforcement, in NAP, 196–197 Active Directory Rights Management Services (AD RMS), 224 Active Directory Users and Computers (ADUC), 209, 210 AD CS (Active Directory Certificate Services), A 217–220 A (host) records, 180, 204 AD DS. See Active Directory Domain Services AAAA (host) records, 180, 204 (AD DS) Account logon events, auditing, 387, 411 AD FS (Active Directory Federation Services), 225 account management, auditing, 387 AD LDS (Active Directory Lightweight Directory Account Operators group, 228 Services), 224 acknowledge packets in DHCP, 160 AD RMS (Active Directory Rights Management actions, for tasks, 121–122 Services), 224 activating Windows Server 2008, 24–25 Add Roles Wizard, 11 Active Directory, 25–34 Select Server Roles page, 53 auditing capabilities, 387 for Terminal Services, 339 auditing detailed events, 388–389 /Add switch, for WDSUtil command, 51 backup and recovery, 230–240 administrative templates, language specific, 264 backup process, 232–235 Administrator account, 226 restoring, 235–240 Administrators (domain controller) group, database 227–228 read-only copy, 15 Administrators (local machine) group, 227 volume containing, 231 adminpak.msi file, 132 elements, 26, 26–29 .adml files, 264 listing shared printers -

Backing up and Recovering Your Server
8 Backing Up and Recovering Your Server IN THIS CHAPTER, YOU WILL LEARN TO: 33UNDERSTAND BACKUP AND RECOVERY (Pages 254–262) n Understand Backup and Recovery Terminology (Page 255) n Use Backup and Recovery Tools (Page 256) 33MANAGE BACKUP AND RECOVERY (Pages 263–286) n Back Up Your Server (Page 263) n Recover Your Data (Page 274) n Recover via Shadow Copy (Page 285) PERFORM BACKUP AND RECOVERY WITH COmmAND 33TOOLS (Pages 287–292) n Use wbadmin.exe (Page 287) ccess and n Use PowerShell (Page A 290) ata Management D PART iii 25395c08.indd 253 12/14/09 9:40:15 AM 254 Chapter 8 3 Backing Up and Recovering Your Server ccidents happen. There are many scenarios in which data can get A lost, deleted, infected, or corrupted—from a user accidently deleting a file to a hard drive failing to an operating system failing to a full disas- ter scenario during which Mother Nature decides to go after your data. It is time for you to shine as the hero for your data and bring it back! One of the most important tasks you need to perform as an admin- istrator is backing up your server. Performing regular backups on your server is a necessity to help protect you from any number of potential problems. Backups can save you time and money, and, more important, they allow you to sleep well at night. If you have performed proper backups and are proficient in the proper procedures to restore your data, you can quickly identify the proper backup media to begin recov- ering the data.