Coupling of Design Patterns: Common Practices and Their Benefits
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examining the Relationships Between Software Coupling and Software Performance: a Cross-Platform Experiment
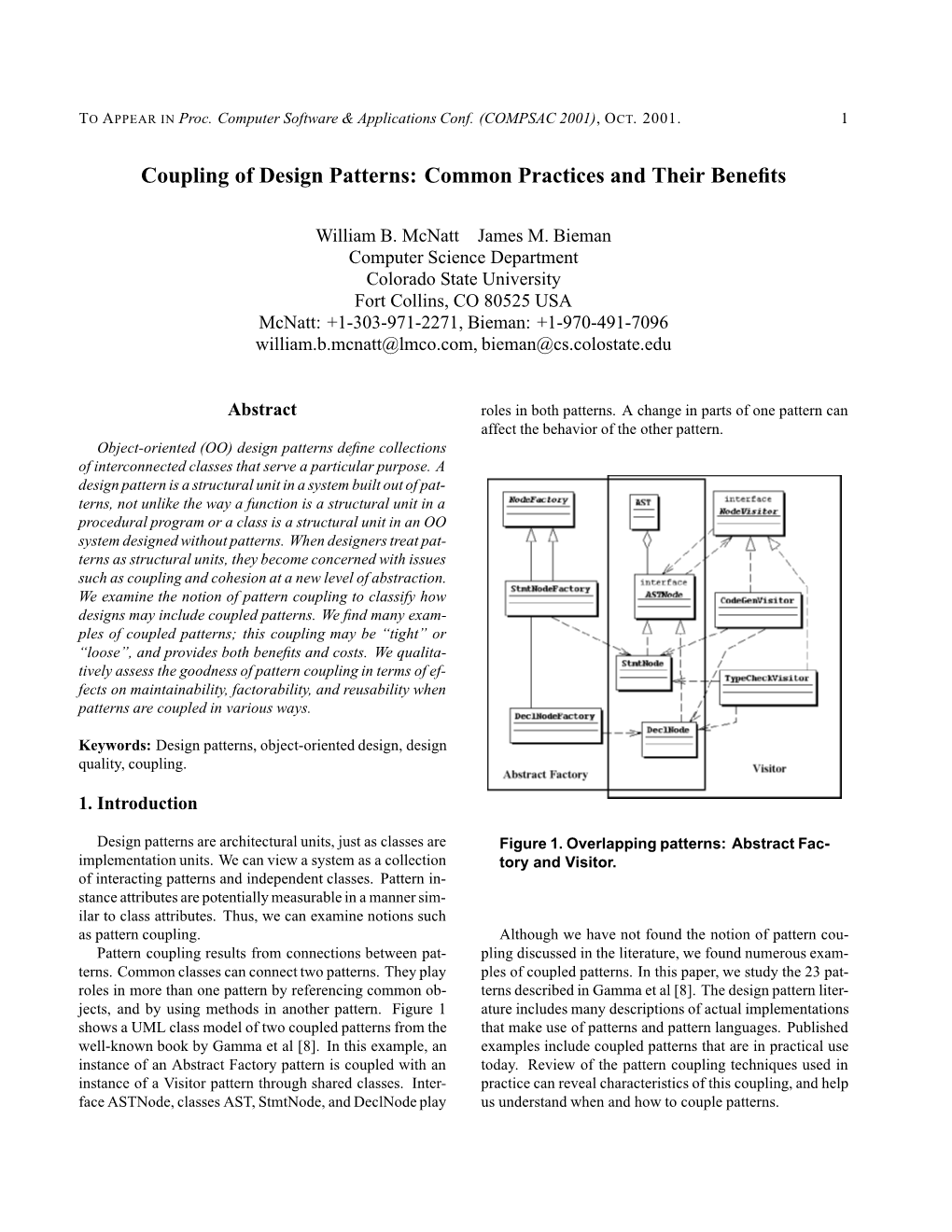
Journal of Computing and Information Technology - CIT 19, 2011, 1, 1–10 1 doi:10.2498/cit.1001353 Examining the Relationships between Software Coupling and Software Performance: A Cross-platform Experiment Liguo Yu1 and Srini Ramaswamy2 1 Computer and Information Sciences Department, Indiana University, South Bend, USA 2 Industrial Software Systems, ABB Corporate Research Center, Bangalore, India Coupling measures the degree of dependencies between Alexander et al., 2010). Table 1 lists the def- software modules. Considerable research has been initions of several major types of coupling in performed to relate software coupling with software understandability, maintainability, and reusability, which structured software systems, in which the de- are the key properties of software maintenance and gree of dependency is considered in increasing evolution. However, only a few research works have order from the bottom (data coupling) to the been reported that study the relationships between soft- ( ) ware coupling and software performance. This study top content coupling . Strong coupling means implemented two benchmarks that measure and compare a high degree of dependency between software the performance of software programs implemented with modules, while loose coupling means a low de- different kinds of coupling, common coupling, data coupling, and stamp coupling. The experiment is run gree of dependency between software modules. on three different platforms, Windows, Linux, and Mac. The results show that (1) the relative performance of systems implemented using different software coupling is platform dependent; (2) while loose coupling is more favorable than strong coupling with respect to software Name Definition maintenance and evolution, it has the drawback of re- duced performance of a software program. -

Lesson 02: Distributed System Patterns
Lesson 02: Distributed System Patterns Phillip J. Windley, Ph.D. CS462 – Large-Scale Distributed Systems Lesson 02: Distributed System Patterns Contents 00 Coupling 03 Distributed Architectures 01 Distributed System Design Axes 04 Conclusion 02 Rethinking Distributed One of the most important Coupling properties of a distributed system is how tightly or loosely coupled the processing is. Lesson 02: Distributed System Patterns Coupling Coupling refers to the degree to which two or more processes are interdependent. We say two things are tightly coupled when they are interdependent and loosely coupled when they are independent. Tight and loose coupling are not binary positions, but rather relative terms. Any given architectural choice might make two processes more or less coupled. CS462 – Large-Scale Distributed Systems 4 Lesson 02: Distributed System Patterns Distributed Systems and Loose Coupling Generally when designing If two processes are completely independent they can successfully operate without any kind of coordination with the other process. distributed systems Whenever we introduce dependencies, the processes must anything that makes the coordinate their activities. This requires some kind of system more loosely communication between the two processes. This can result in coupled is desirable. wasted computation, delays due to latency, and computational errors. But, no useful software Of course, we can’t accomplish most interesting computations without some coupling. Good distributed architectures accomplish system can be built where their tasks with a minimum of coupling. Good distributed system all the components are architects choose architectures that minimize the coupling necessary to get the job done. completely decoupled. CS462 – Large-Scale Distributed Systems 5 Lesson 02: Distributed System Patterns System Level Coupling Coupling can occur on multiple levels within a system. -

LNCS 5103, Pp
An Event-Based Approach to Reducing Coupling in Large-Scale Applications Bartosz Kowalewski1, Marian Bubak1,2, and Bartosz Bali´s1 1 Institute of Computer Science, AGH, Krakow, Poland 2 Academic Computer Centre CYFRONET AGH, Krakow, Poland [email protected], {bubak,balis}@agh.edu.pl Abstract. Large-scale distributed applications tend to become more and more complex and hard to develop, and execute. Approaches used when building such systems have to be revised, in order to decrease coupling within the code and increase productivity during the devel- opment process. Especially event-based programming applied to Web services should gain much attention. In this paper, we present an experi- mental publish/subscribe infrastructure, which introduces robust event- based mechanisms to be used with Web services-enabled applications. The concept of this solution is built upon the extensibility and config- urability principles. We show that performance gap between traditional distributed event-based technologies and the Web also services-based ap- proach is not necessarily as significant as most people tend to think. Keywords: Large-scale computing, distributed computing, decoupling, Web services, event infrastructure, publish/subscribe, WS-Notification. 1 Introduction The main characteristic of an event-based design is its striving to decrease cou- pling in a system [5]. Coupling, usually contrasted with cohesion, is the degree of association between modules, components, subsystems, etc. [6] Over the past three decades a lot of attention has been paid to this concept, both in scientific and commercial computing. Besides many other measures, the level of coupling started to be treated as quality metrics for software design. -

Software Maintainability and Reusability Using Cohesion Metrics
International Journal of Computer Trends and Technology (IJCTT) – Volume 54 Issue 2-December2017 Software Maintainability and Reusability using Cohesion Metrics Adekola, O.D#1, Idowu, S.A*2, Okolie, S.O#3, Joshua, J.V#4, Akinsanya, A.O*5, Eze, M.O#6, EbiesuwaSeun#7 #1Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria *2Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria #3Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria #4Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria *5Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria #6Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria #7Faculty, Computer Science Department, Babcock University,Ilishan-Remo, Ogun State, Nigeria Abstract - Among others, remarkable external software’s lifetime. Ahn et al., (2003) estimated that quality attributes of interest to software practitioners/ maintenance takes up to 80% of the total costof engineers include testability, maintainability and producing software applications. Expectation of reusability.Software engineers still combat achieving more reliable, quicker time-to-market and softwarecrisis and even chronic software affliction maintainable systems. A lot of research has gone into not because there is no standardized software the areas of software reuse and maintenance due to development process but because enough attention is the fact that these among other issues concern not given to seemingly insignificant but crucial intimately system developers/architects/engineers details of internal design attributes such as cohesion rather than end-users. Therehas been enormous and coupling especially in object-oriented systems. growth in software reuse research from the days of Consequently, the aftermath is increased structured programming concepts to object-oriented maintenance cost, effort and time which negatively methods and beyond (e.g. -

Zapthink White Paper
zapthink white paper GOVERNANCE, QUALITY, & MANAGEMENT THE FOUNDATIONS OF SOA ZapThink, LLC y 108 Woodlawn Road y Baltimore, MD 21210 y [email protected] y www.zapthink.com Governance, Quality, & Management July 2008 GOVERNANCE, QUALITY, & MANAGEMENT THE FOUNDATIONS OF SOA July 2008 Analyst: Jason Bloomberg Abstract Service-Oriented Architecture (SOA) is an approach to organizing IT resources to better meet the changing needs of the business. While many organizations are somewhere on their SOA roadmaps, many such organizations face challenges when planning the underlying infrastructure that will support their SOA implementation. One reason for this challenge is that there are three core infrastructure areas that are jointly essential to the success of separate, but overlapping SOA effort: governance, quality, and management. Governance means creating, communicating, and enforcing the policies that apply to the behavior of IT and its users. Quality is a measure of how well working systems meet the needs of the business. Management focuses on how well those systems meet performance, security, and other non-functional requirements for working software. In the context of SOA, however, these three sets of capabilities begin to merge. To provide the business agility benefit that is the core business motivation for many SOA initiatives, governance, quality, and management need not only apply to the design time and run time phases that traditional software projects exhibit. In addition, SOA requires these capabilities apply to the change time phase as well, where organizations reconfigure and recompose Services to meet changing business needs. As a result, the governance, quality, and management challenges that SOA presents go beyond traditional IT concerns. -

Two Cases in High Reliability Organizing
Two Cases in High Reliability Organizing: a Hermeneutic Reconceptualization GERD VAN DEN EEDE ii Two Cases in High Reliability Organizing: a Hermeneutic Reconceptualization iii Two Cases in High Reliability Organizing: a Hermeneutic Reconceptualization Twee Gevalsstudies over Organiseren voor Hoge Betrouwbaarheid: Een Hermeneutische Reconceptualisatie PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit van Tilburg, op gezag van de rector magnificus, prof. dr. Ph. Eijlander, in het openbaar te verdedigen ten overstaan van een door het college voor promoties aangewezen commissie in de aula van de Universiteit op vrijdag 18 december 2009 om 14.15 uur door Gerd Geeraard Paula Van Den Eede geboren op 7 juni 1970 te Dendermonde, België iv Two Cases in High Reliability Organizing: a Hermeneutic Reconceptualization Promotor: Prof. dr. P.M.A. Ribbers Copromotor: dr. B.A. Van de Walle Overige leden: Univ.-Prof. dr.-Ing. F. Fiedrich Prof. dr. T.J. Grant Dr. F. Hardeman Dr. A-F. Rutkowski Prof. dr. M. Turoff Prof. dr. D. Van Lindt . Table of Contents v Table of Contents TABLE OF CONTENTS ................................................................................................................................ V LIST OF FIGURES ......................................................................................................................................XII LIST OF TABLES .......................................................................................................................................XIII GLOSSARY -

Tight and Loose Coupling in Organizations
BE J. Theor. Econ. 2016; aop Romans Pancs* Tight and Loose Coupling in Organizations DOI 10.1515/bejte-2015-0081 Abstract: Some industries have consumers who seek novelty and firms that innovate vigorously and whose organizational structure is loosely coupled, or easily adaptable. Other industries have consumers who take comfort in the traditional and firms that innovate little and whose organizational structure is tightly coupled, or not easily adaptable. This paper proposes a model that explains why the described features tend to covary across industries. The model highlights the pervasiveness of equilibrium inefficiency (innovation can be insufficient or excessive) and the nonmonotonicity of welfare in the equili- brium amount of innovation. Keywords: loose coupling, tight coupling, demand for novelty 1 Introduction Some industries have consumers who seek novelty and have firms that innovate vigorously and whose organizational structure is loosely coupled in the sense that it easily adjusts to the changes in the economic environment. The tech industry in the Silicon Valley is like this. Consumers expect regular upgrades to gadgets; the startup culture and high employee mobility breed firms ready to take advantage of the latest changes in the economic environment. Other indus- tries have consumers who take comfort in the traditional and have firms that innovate little and whose organizational structure is tightly coupled in the sense of being slow to adjust to the changes in the economic environment. The manufacturing industry was like this in Japan in the second-half of the twentieth century, during the industrialization stage. De-facto lifetime employment was common, and the firm’s organizational structure was rigid. -

Security Model for Service-Oriented Architecture
Advanced Computing: An International Journal ( ACIJ ), Vol.2, No.4, July 2011 Security Model For Service-Oriented Architecture Oldooz Karimi, MSc Department of Computer Engineering, sofiyan Azad University, sofiyan, Iran , [email protected] Abstract . In this article, we examine how security applies to Service Oriented Architecture (SOA). Before we discuss security for SOA, lets take a step back and examine what SOA is. SOA is an architectural approach which involves applications being exposed as "services". Originally, services in SOA were associated with a stack of technologies which included SOAP, WSDL, and UDDI. This article addresses the defects of traditional enterprise application integration by combining service oriented-architecture and web service technology. Application integration is then simplified to development and integration of services to tackle connectivity of isomerous enterprise application integration, security, loose coupling between systems and process refactoring and optimization. Key words : service-oriented architecture, enterprise application integration, security 1 Introduction It is tempting to launch into a description of SOA Security without first asking "Why?" Why apply security to SOA? One obvious answer is to protect the SOA infrastructure against attack. This is a valid reason, but there are also enabling, positive reasons for applying security to SOA, such as the ability to monitor usage of services in a SOA. We begin by examining the attacks against SOA technologies, both EAI and ESA. Abstract: Interoperable software architecture requires interoperable security mechanisms. Security is frequently looked at as a black art, but in reality the core concepts of security - knowing your assets and designing for failure - are just good engineering practices. -

Master's Thesis
MASTER’S THESIS Loosely-coupled user-friendly interface: a Window toward a better application of knowledge-based system in Architecture, Engineering and Construction Faridaddin Vahdatikhaki Master’s thesis in Construction Management and Engineering Loosely-coupled user-friendly interface: a Window toward a better application of knowledge-based system in Architecture, Engineering and Construction The Netherlands, January, 2011 Faridaddin Vahdatikhaki Delft University of Technology Van Hattum en Blankfort Supervisors: Prof. Dr. ir. Hennes De Ridder Ir. Marcel Ludema Ir. Sipke Huitema Ir. Martinus van de Ruitenbeek Dedicated to my father for being the embodiment of perfection in my life Acknowledgement: I shall express my most heartfelt gratitude to my parents without whose indelible support and inspiring words, this dissertation would not be. Their kindness has been my last and only recourse in years fraught with disquietude and tension. Their being out there for me never ceased to palliate my distress in every circumstances. I feel obliged to give my deepest thanks to my wife who has never refrained from infusing me with passion and inspiration throughout these years. Words may not convey my appreciation for her being such a supportive person despite all difficulties I put her through with not being next to her. This is my responsibility to thank Martinus van de Ruitenbeek whose brilliance has been my only torch in journeying through the dim realms of research. His enlightening ideas have kept my work progressing and coming to fruition. I am indebted to Dr. Reza Beheshti for being a marvelous friend and guide whenever I was desperate for help. -

Design Principles for the Future Internet Architecture
Design Principles for the Future Internet Architecture Dimitri Papadimitriou1, Theodore Zahariadis2, Pedro Martinez-Julia3, Ioanna Papafili4, Vito Morreale5, Francesco Torelli5, Bernard Sales1, and Piet Demeester6 1 Alcatel-Lucent Bell Labs, Belgium {dimitri.papadimitriou,bernard.sales}@alcatel-lucent.com 2 Synelixis Solutions, Greece [email protected] 3 Univ. of Murcia, Spain [email protected] 4 Athens University of Economics and Business (AUEB) [email protected] 5 Engineering, Italy {vito.morreale,francesco.torelli}@eng.it 6 Ghent University (UGent), Belgium [email protected] Abstract. Design principles play a central role in the architecture of the Internet as driving most engineering decisions at conception level and operational level. This paper is based on the EC Future Internet Architecture (FIArch) Group results and identifies some of the design principles that we expect to govern the future architecture of the Internet. We believe that it may serve as a starting point and comparison for most research and development projects that target the so-called Future Internet Architecture. 1 Introduction Design principles play a central role in the architecture of the Internet as driving most engineering decisions not only at conception level but also at operational level. Many ICT systems do not consider design principles and derive their model directly from requirements. However, when it comes to the design of the Internet, the formulation of design principles is a fundamental characteristic of the process that guides the design of its protocols. On the other hand, in searching for Internet architectural principles, we must remember that technical change is continuous in the information and communication technology industry. -

Transitioning from File-Based HPC Workflows to Streaming Data Pipelines with Openpmd and ADIOS2
Transitioning from file-based HPC workflows to streaming data pipelines with openPMD and ADIOS2 Franz Poeschel1;4, Juncheng E5, William F. Godoy3, Norbert Podhorszki3, Scott Klasky3, Greg Eisenhauer6, Philip E. Davis7, Lipeng Wan3, Ana Gainaru3, Junmin Gu2, Fabian Koller4, René Widera4, Michael Bussmann1;4, and Axel Huebl2;4 1 Center for Advanced Systems Understanding (CASUS), D-02826 Görlitz, Germany 2 Lawrence Berkeley National Laboratory (LBNL), Berkeley 94720, California, USA 3 Oak Ridge National Laboratory (ORNL), Oak Ridge 37830, Tennessee, USA 4 Helmholtz-Zentrum Dresden-Rossendorf (HZDR), D-01328 Dresden, Germany 5 European XFEL GmbH (EU XFEL), D-22869 Schenefeld, Germany 6 Georgia Institute of Technology (Georgia Tech), Atlanta 30332, Georgia, USA 7 Rutgers University (Rutgers), New Brunswick 08901, New Jersey, USA Abstract. This paper aims to create a transition path from file-based IO to streaming-based workflows for scientific applications in anHPC environment. By using the openPMP-api, traditional workflows limited by filesystem bottlenecks can be overcome and flexibly extended for insitu analysis. The openPMD-api is a library for the description of scientific data according to the Open Standard for Particle-Mesh Data (openPMD). Its approach towards recent challenges posed by hardware heterogeneity lies in the decoupling of data description in domain sciences, such as plasma physics simulations, from concrete implementations in hardware and IO. The streaming backend is provided by the ADIOS2 framework, developed at Oak Ridge National Laboratory. This paper surveys two openPMD-based loosely coupled setups to demonstrate flexible appli- cability and to evaluate performance. In loose coupling, as opposed to tight coupling, two (or more) applications are executed separately, e.g. -

Loosely-Coupled Processes
Loosely-Coupled Processes Jayadev Misra∗ Department of Computer Sciences The University of Texas at Austin Austin, Texas 78712 (512) 471-9547 [email protected] 1 Introduction 1.1 Message Communicating and Shared-Variable Systems A system of processes in which the interactions are solely through messages is often called loosely-coupled. Such systems are attractive from a programming viewpoint. They are designed by decomposing a specifica- tion into its separable concerns, each of which could then be implemented by a process; the operation of the system can be understood by asserting properties of the message sequences transmitted among the compo- nent processes. A key attribute of loosely-coupled systems is a guarantee that a message that has been sent cannot be unsent. As a consequence, a process can commence its computation upon receiving a message, with the guarantee that no future message it receives will require it to undo its previous computations. Processes that communicate through shared variables, where a shared variable may be read from/written to by an arbitrary number of processes, are often called tightly-coupled. In contrast to loosely-coupled systems, designs of tightly-coupled systems typically require deeper analysis. Since speeds of the component processes are assumed to be nonzero and finite, but otherwise arbitrary, it is necessary to analyze all possible execution sequences, however unlikely some of them may be, to guarantee the absence of “race conditions.” Special protocols for mutual exclusion are often required for a process to access shared-variables in an exclusive manner. Yet, shared-variables often provide succinct, and even elegant, solutions; for instance, broadcasting a message can often be implemented by storing the message in a variable that can be read by every process.