Bill Karwin — «SQL Antipatterns
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Source Code Patterns of Cross Site Scripting in PHP Open Source Projects
Source Code Patterns of Cross Site Scripting in PHP Open Source Projects Felix Schuckert12, Max Hildner1, Basel Katt2 ,∗ and Hanno Langweg12 1 HTWG Konstanz, Department of Computer Science, Konstanz, Baden-W¨urttemberg, Germany [email protected] [email protected] [email protected] 2 Department of Information Security and Communication Technology, Faculty of Information Technology and Electrical Engineering, NTNU, Norwegian University of Science and Technology, Gjøvik, Norway [email protected] Abstract To get a better understanding of Cross Site Scripting vulnerabilities, we investigated 50 randomly selected CVE reports which are related to open source projects. The vulnerable and patched source code was manually reviewed to find out what kind of source code patterns were used. Source code pattern categories were found for sources, concatenations, sinks, HTML context and fixes. Our resulting categories are compared to categories from CWE. A source code sample which might have led developers to believe that the data was already sanitized is described in detail. For the different HTML context categories, the necessary Cross Site Scripting prevention mechanisms are described. 1 Introduction Cross Site Scripting (XSS) is on the fourth place in Common Weakness Enumeration (CWE) top 25 2011 [3] and on the seventh place in Open Wep Application Security Project (OWASP) top 10 2017 [4]. Accordingly, Cross Site Scripting is still a common issue in web security. To discover the reason why the same vulnerabilities are still occurring, we investigated the vulnerable and patched source code from open source projects. Similar methods, functions and operations are grouped together and are called source code patterns. -

Postgresql Flyer
PostgreSQL - English Usage Examples Further Information Development system PostgreSQL (2nd Edition), Korry Douglas, Sams Publishing, ISBN: 0672327562 A small system just for developing, running on any supported platform (Unix, Linux, Mac OS, Windows). Beginning Databases with PostgreSQL:From Novice to This system does not need much system resources. Professional, Second Edition, Neil Matthew, Apress, The result can be exported and used in the production ISBN: 1590594789 PostgreSQL system. PostgreSQL Developer's Handbook, Ewald Geschwinde, Sams Publishing, ISBN 0672322609 Beginning PHP and PostgreSQL 8, W. Jason Gilmore, Small to mid-level database server Apress, ISBN 1590595475 A small to mid-level database server has just small PHP and PostgreSQL Advanced Web Programming, hardware requirements. PostgreSQL is not running ex- Ewald Geschwinde and Robert Treat, Sams Publishing, clusive on this system but shares the resources with ISBN 0672323826 other services. A webserver (Blog, CMS) with a data- base backend is a good example. PostgreSQL homepage: www.postgresql.org pgAdmin III: http://www.pgadmin.org Large database server PgFoundry: http://pgfoundry.org phpPgAdmin: http://phppgadmin.sourceforge.net A large database server has extensive hardware re- PostGIS: postgis.refractions.net quirements and is usually dedicated to a single appli- cation or project. PostgreSQL can use the full power Slony: slony.info of the hardware without the need to share resources. PostgreSQL 8.3 What is PostgreSQL? PostgreSQL 8.3, released in early 2008, includes a record PostgreSQL is an object-relational database management number of new and improved features which will greatly system (ORDBMS). It is freely available and usable with- enhance PostgreSQL for application designers, database out licensing fee. -

The Convergence of Modeling and Programming
The Convergence of Modeling and Programming: Facilitating the Representation of Attributes and Associations in the Umple Model-Oriented Programming Language by Andrew Forward PhD Thesis Presented to the Faculty of Graduate and Postdoctoral Studies in partial fulfillment of the requirements for the degree Doctor of Philosophy (Computer Science1) Ottawa-Carleton Institute for Computer Science School of Information Technology and Engineering University of Ottawa Ottawa, Ontario, K1N 6N5 Canada © Andrew Forward, 2010 1 The Ph.D. program in Computer Science is a joint program with Carleton University, administered by the Ottawa Carleton Institute for Computer Science Acknowledgements A very special, and well-deserved, thank you to the following: a) Dr. Timothy C. Lethbridge. Tim has been a mentor of mine for several years, first as one of my undergraduate professors, later as my Master’s supervisor. Tim has again helped to shape my approach to software engineering, research and academics during my journey as a PhD candidate. b) The Complexity Reduction in Software Engineering (CRUISE) group and in particular Omar Badreddin and Julie Filion. Our weekly meetings, work with IBM, and the collaboration with the development of Umple were of great help. c) My family and friends. Thank you and much love Ayana; your support during this endeavor was much appreciated despite the occasional teasing about me still being in school. To my mom (and editor) Jayne, my dad Bill, my sister Allison and her husband Dennis. And, to my friends Neil, Roy, Van, Rob, Pat, and Ernesto – your help will be forever recorded in my work. Finally a special note to Ryan Lowe, a fellow Software Engineer that helped to keep my work grounded during our lengthy discussion about software development – I will miss you greatly. -

A Framework for Working with Cross-Application Social Tagging Data
TECHNISCHE UNIVERSITÄT MÜNCHEN FAKULTÜT FÜR INFORMATIK Forschungs- und Lehreinheit XI Angewandte Informatik / Kooperative Systeme A Framework for Working with Cross-Application Social Tagging Data Walter Christian Kammergruber Vollständiger Abdruck der von der Fakultät für Informatik der Technischen Universität München zur Erlangung des akademischen Grades eines Doktors der Naturwissenschaften (Dr. rer. nat.) genehmigten Dissertation. Vorsitzender: Univ.-Prof. Dr. Helmut Krcmar Prüfer der Dissertation: 1. Univ.-Prof. Dr. Johann Schlichter 2. Univ.-Prof. Dr. Florian Matthes Die Dissertation wurde am 26.06.2014 bei der Technischen Universität München eingere- icht und durch die Fakultät für Informatik am 26.11.2014 angenommen. Zusammenfassung Mit dem zunehmenden Erfolg des Web 2.0 wurde und wird Social-Tagging immer beliebter, und es wurde zu einem wichtigen Puzzle-Stück dieses Phänomens. Im Unterschied zu ausgefeilteren Methoden um Ressourcen zu organisieren, wie beispielsweise Taxonomien und Ontologien, ist Social-Tagging einfach einzusetzen und zu verstehen. Bedingt durch die Einfachheit finden sich keine expliziten und formalen Strukturen vor. Das Fehlen von Struktur führt zu Problemen beim Wiederaufinden von Informationen, da beispielsweise Mehrdeutigkeiten in Suchanfragen nicht aufgelöst werden können. Zum Beispiel kann ein Tag „dog“ (im Englischen) für des Menschen bester Freund stehen, aber auch für das Lieblingsessen mancher Personen, einem Hot Dog. Ein Bild einer Katze kann mit„angora cat“, „cat“, „mammal“, „animal“oder „creature“getagged sein. Die Art der Tags hängt sehr stark vom individuellen Nutzer ab. Weiterhin sind Social-Tagging-Daten auf verschiedene Applikationen verteilt. Ein gemeinsamer Mediator ist nicht vorhanden. Beispielsweise kann ein Nutzer auf vielen verschiedenen Applikationen Entitäten taggen. Für das Internet kann das Flickr, Delicious, Twitter, Facebook and viele mehr sein. -

Designpatternsphp Documentation Release 1.0
DesignPatternsPHP Documentation Release 1.0 Dominik Liebler and contributors Jul 18, 2021 Contents 1 Patterns 3 1.1 Creational................................................3 1.1.1 Abstract Factory........................................3 1.1.2 Builder.............................................8 1.1.3 Factory Method......................................... 13 1.1.4 Pool............................................... 18 1.1.5 Prototype............................................ 21 1.1.6 Simple Factory......................................... 24 1.1.7 Singleton............................................ 26 1.1.8 Static Factory.......................................... 28 1.2 Structural................................................. 30 1.2.1 Adapter / Wrapper....................................... 31 1.2.2 Bridge.............................................. 35 1.2.3 Composite............................................ 39 1.2.4 Data Mapper.......................................... 42 1.2.5 Decorator............................................ 46 1.2.6 Dependency Injection...................................... 50 1.2.7 Facade.............................................. 53 1.2.8 Fluent Interface......................................... 56 1.2.9 Flyweight............................................ 59 1.2.10 Proxy.............................................. 62 1.2.11 Registry............................................. 66 1.3 Behavioral................................................ 69 1.3.1 Chain Of Responsibilities................................... -

Folksonomies - Cooperative Classification and Communication Through Shared Metadata
Folksonomies - Cooperative Classification and Communication Through Shared Metadata Adam Mathes Computer Mediated Communication - LIS590CMC Graduate School of Library and Information Science University of Illinois Urbana-Champaign December 2004 Abstract This paper examines user-generated metadata as implemented and applied in two web services designed to share and organize digital me- dia to better understand grassroots classification. Metadata - data about data - allows systems to collocate related information, and helps users find relevant information. The creation of metadata has generally been approached in two ways: professional creation and author creation. In li- braries and other organizations, creating metadata, primarily in the form of catalog records, has traditionally been the domain of dedicated profes- sionals working with complex, detailed rule sets and vocabularies. The primary problem with this approach is scalability and its impracticality for the vast amounts of content being produced and used, especially on the World Wide Web. The apparatus and tools built around professional cataloging systems are generally too complicated for anyone without spe- cialized training and knowledge. A second approach is for metadata to be created by authors. The movement towards creator described docu- ments was heralded by SGML, the WWW, and the Dublin Core Metadata Initiative. There are problems with this approach as well - often due to inadequate or inaccurate description, or outright deception. This paper examines a third approach: user-created metadata, where users of the documents and media create metadata for their own individual use that is also shared throughout a community. 1 The Creation of Metadata: Professionals, Con- tent Creators, Users Metadata is often characterized as “data about data.” Metadata is information, often highly structured, about documents, books, articles, photographs, or other items that is designed to support specific functions. -

Serendipity in Recommender Systems JYVÄSKYLÄ STUDIES in COMPUTING 281
JYVÄSKYLÄ STUDIES IN COMPUTING 281 Denis Kotkov Serendipity in Recommender Systems JYVÄSKYLÄ STUDIES IN COMPUTING 281 Denis Kotkov Serendipity in Recommender Systems Esitetään Jyväskylän yliopiston informaatioteknologian tiedekunnan suostumuksella julkisesti tarkastettavaksi yliopiston Agora-rakennuksen Alfa-salissa kesäkuun 7. päivänä 2018 kello 12. Academic dissertation to be publicly discussed, by permission of the Faculty of Information Technology of the University of Jyväskylä, in building Agora, Alfa hall, on June 7, 2018 at 12 o’clock noon. UNIVERSITY OF JYVÄSKYLÄ JYVÄSKYLÄ 2018 Serendipity in Recommender Systems JYVÄSKYLÄ STUDIES IN COMPUTING 281 Denis Kotkov Serendipity in Recommender Systems UNIVERSITY OF JYVÄSKYLÄ JYVÄSKYLÄ 2018 Editors Marja-Leena Rantalainen Faculty of Information Technology, University of Jyväskylä Pekka Olsbo, Ville Korkiakangas Publishing Unit, University Library of Jyväskylä Permanent link to this publication: http://urn.fi/URN:ISBN:978-951-39-7438-1 URN:ISBN:978-951-39-7438-1 ISBN 978-951-39-7438-1 (PDF) ISBN 978-951-39-7437-4 (nid.) ISSN 1456-5390 Copyright © 2018, by University of Jyväskylä Jyväskylä University Printing House, Jyväskylä 2018 ABSTRACT Kotkov, Denis Serendipity in Recommender Systems Jyväskylä: University of Jyväskylä, 2018, 72 p. (+included articles) (Jyväskylä Studies in Computing ISSN 1456-5390; 281) ISBN 978-951-39-7437-4 (nid.) ISBN 978-951-39-7438-1 (PDF) Finnish summary Diss. The number of goods and services (such as accommodation or music streaming) offered by e-commerce websites does not allow users to examine all the avail- able options in a reasonable amount of time. Recommender systems are auxiliary systems designed to help users find interesting goods or services (items) on a website when the number of available items is overwhelming. -

Projects on the Move
LINUXCOVERCOMMUNITY USERSTORY SchlagwortSchlagwortFree Software sollte sollte Projectshier hier stehen stehen Schlagwort sollte hier stehen COVER STORY An up-to-date look at free software and its makers PROJECTS ON THE MOVE Free software covers such a diverse range of utilities, applications, and assorted projects that it is sometimes difficult to find the perfect tool. We pick the best of the bunch. This month we cover blogging – the latest buzz, the latest on the DPL elections, and more trouble at Debian. BY MARTIN LOSCHWITZ he EU is entering the second use, install, and configure. For example, extensible. B2 Evolution also has themes round of the battle over software administrators do not need to create a to allow users to design their own blogs. Tpatents. While supporters have database or waste time trying to set one Like the other solutions, Serendipity successfully had the directive passed by up, as Blosxom uses simple text files. [3] aims for ease of use. Themes and the EU Council of Ministers, opponents Entries can be created in the web inter- skins allow users to modify the blog soft- of patents are increasing the pressure face and uploaded via FTP or WebDAV. ware’s appearance. Version 0.8, which is prior to the second reading. The number Plugins add all kinds of functionality to still under development, even supports of pages warning about the danger of Blosxom. The default package supports Smarty framework [4] templates. software patents continues to grow. And RSS feeding of blog entries, and themes Serendipity can also manage multiple it appears unlikely – although by no give the Blosxom blog a pleasing appear- user accounts. -

Laravel - My First Framework Companion for Developers Discovering Laravel PHP Framework
Laravel - my first framework Companion for developers discovering Laravel PHP framework Maksim Surguy This book is for sale at http://leanpub.com/laravel-first-framework This version was published on 2014-09-05 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. ©2014 Maksim Surguy Tweet This Book! Please help Maksim Surguy by spreading the word about this book on Twitter! The suggested hashtag for this book is #laravelfirst. Find out what other people are saying about the book by clicking on this link to search for this hashtag on Twitter: https://twitter.com/search?q=#laravelfirst Also By Maksim Surguy Integrating Front end Components with Web Applications Contents Introduction ................................................. i About the author ............................................. i Prerequisites ................................................ ii Source Code ................................................ ii 1. Meeting Laravel ............................................. 1 1.1 Introducing Laravel 4 PHP framework .............................. 1 1.1.1 Laravel’s Expressive code .................................. 2 1.1.2 Laravel applications use Model-View-Controller pattern ................. 3 1.1.3 Laravel was built by a great community .......................... 3 1.2 History of Laravel framework ................................... 4 1.2.1 State of PHP frameworks world before Laravel 4 ..................... 4 1.2.2 Evolution of Laravel framework .............................. 4 1.3 Advantages of Using Laravel ................................... 5 1.3.1 Convention over configuration ............................... 5 1.3.2 Ready out of the box .................................... 6 1.3.3 Clear organization of all parts of the application .................... -

An Experimental Study of the Performance, Energy, and Programming Effort Trade-Offs of Android Persistence Frameworks
An Experimental Study of the Performance, Energy, and Programming Effort Trade-offs of Android Persistence Frameworks Jing Pu Thesis submitted to the Faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements for the degree of Master of Science in Computer Science and Applications Eli Tilevich, Chair Barbara G. Ryder Francisco Servant July 1, 2016 Blacksburg, Virginia Keywords: Energy Efficiency; Performance; Programming Effort; Orthogonal Persistence; Android; Copyright 2016, Jing Pu An Experimental Study of the Performance, Energy, and Programming Effort Trade-offs of Android Persistence Frameworks Jing Pu (ABSTRACT) One of the fundamental building blocks of a mobile application is the ability to persist program data between different invocations. Referred to as persistence, this functionality is commonly implemented by means of persistence frameworks. When choosing a particular framework, Android|the most popular mobile platform—offers a wide variety of options to developers. Unfortunately, the energy, performance, and programming effort trade-offs of these frameworks are poorly understood, leaving the Android developer in the dark trying to select the most appropriate option for their applications. To address this problem, this thesis reports on the results of the first systematic study of six Android persistence frameworks (i.e., ActiveAndroid, greenDAO, Orm- Lite, Sugar ORM, Android SQLite, and Realm Java) in their application to and performance with popular benchmarks, such as DaCapo. Having measured and ana- lyzed the energy, performance, and programming effort trade-offs for each framework, we present a set of practical guidelines for the developer to choose between Android persistence frameworks. Our findings can also help the framework developers to optimize their products to meet the desired design objectives. -

Privacy by Design in Big Data an Overview of Privacy Enhancing Technologies in the Era of Big Data Analytics
Privacy by design in big data An overview of privacy enhancing technologies in the era of big data analytics FINAL 1.0 PUBLIC DECEMBER 2015 www.enisa.europa.eu European Union Agency For Network And Information Security Privacy by design in big data FINAL | 1.0 | Public | December 2015 About ENISA The European Union Agency for Network and Information Security (ENISA) is a centre of network and information security expertise for the EU, its member states, the private sector and Europe’s citizens. ENISA works with these groups to develop advice and recommendations on good practice in information security. It assists EU member states in implementing relevant EU legislation and works to improve the resilience of Europe’s critical information infrastructure and networks. ENISA seeks to enhance existing expertise in EU member states by supporting the development of cross-border communities committed to improving network and information security throughout the EU. More information about ENISA and its work can be found at www.enisa.europa.eu. Authors Giuseppe D' Acquisto (Garante per la protezione dei dati personali), Josep Domingo-Ferrer (Universitat Rovira i Virgili), Panayiotis Kikiras (AGT), Vicenç Torra (University of Skövde), Yves-Alexandre de Montjoye (MIT), Athena Bourka (ENISA) Editors European Union Agency for Network and Information Security ENISA responsible officers: Athena Bourka, Prokopios Drogkaris For contacting the authors please use [email protected]. For media enquiries about this paper, please use [email protected]. Acknowledgements We would like to thank Gwendal Le Grand (CNIL) for his support and advice during the project. Acknowledgements should also be given to Stefan Schiffner (ENISA) for his help and support in producing this document. -
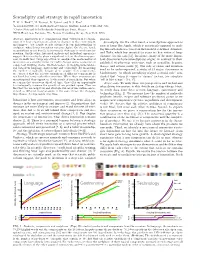
Serendipity and Strategy in Rapid Innovation T
Serendipity and strategy in rapid innovation T. M. A. Fink∗†, M. Reevesz, R. Palmaz and R. S. Farry yLondon Institute for Mathematical Sciences, Mayfair, London W1K 2XF, UK ∗Centre National de la Recherche Scientifique, Paris, France zBCG Henderson Institute, The Boston Consulting Group, New York, USA Abstract. Innovation is to organizations what evolution is to organ- process. isms: it is how organisations adapt to changes in the environment Serendipity. On the other hand, a serendipitous approach is and improve. Yet despite steady advances in our understanding of seen in firms like Apple, which is notoriously opposed to mak- evolution, what drives innovation remains elusive. On the one hand, ing innovation choices based on incremental consumer demands, organizations invest heavily in systematic strategies to accelerate in- novation. On the other, historical analysis and individual experience and Tesla, which has invested for years in their vision of long- suggest that serendipity plays a significant role in the discovery pro- distance electric cars [13]. In science, many of the most impor- cess. To unify these two perspectives, we analyzed the mathematics of tant discoveries have serendipitous origins, in contrast to their innovation as a search process for viable designs across a universe of published step-by-step write-ups, such as penicillin, heparin, component building blocks. We then tested our insights using histor- X-rays and nitrous oxide [9]. The role of vision and intuition ical data from language, gastronomy and technology. By measuring the number of makeable designs as we acquire more components, tend to be under-reported: a study of 33 major discoveries in we observed that the relative usefulness of different components is biochemistry \in which serendipity played a crucial role" con- not fixed, but cross each other over time.