Keeping the Software Documentation up to Date in Small Companies 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PTC Integrity™ Lifecycle Manager™
PTC Integrity ™ Lifecycle Manager™ The PTC Integrity product family helps organizations accelerate product innovation by reducing complexity, improving collaboration, and automating best practices for software and systems engi- neering. PTC Integrity Lifecycle Manager, a member of the Integrity family, is a flexible, process-based ALM (Application Lifecycle Management) platform that helps teams deliver higher quality, more innovative software with less risk. In today’s world, the demand for smarter, more With seamless, collaborative management of all activi- connected products is increasingly fulfilled through ties and assets, the PTC Integrity Lifecycle Manager software. Software – whether embedded in a product platform helps software engineering teams achieve or providing supporting functionality – is key to driving greater transparency, better productivity and shorter product differentiation and profitability. PTC Integrity cycle times across the entire development lifecycle. Lifecycle Manager provides a global software devel- opment platform that supports all activities and What Makes Integrity Different? assets associated with the engineering and delivery of applications and embedded software. Business All too often, organizations struggle to gain an end- analysts, architects, engineers, developers, quality to-end view of software assets that span multiple managers, testers, partners/suppliers and other tools, with meta-data stored in multiple, disjointed stakeholders all use PTC Integrity Lifecycle Manager repositories. The result is a lack of visibility and as the means for collaboration and control over the traceability across the lifecycle, higher defects and end-to-end development lifecycle. longer development cycles. Our solution provides a unified, global software development platform that supports all activities and assets associated with the engineering and delivery of applications and products. -

Command Line Interface
Command Line Interface Squore 21.0.2 Last updated 2021-08-19 Table of Contents Preface. 1 Foreword. 1 Licence. 1 Warranty . 1 Responsabilities . 2 Contacting Vector Informatik GmbH Product Support. 2 Getting the Latest Version of this Manual . 2 1. Introduction . 3 2. Installing Squore Agent . 4 Prerequisites . 4 Download . 4 Upgrade . 4 Uninstall . 5 3. Using Squore Agent . 6 Command Line Structure . 6 Command Line Reference . 6 Squore Agent Options. 6 Project Build Parameters . 7 Exit Codes. 13 4. Managing Credentials . 14 Saving Credentials . 14 Encrypting Credentials . 15 Migrating Old Credentials Format . 16 5. Advanced Configuration . 17 Defining Server Dependencies . 17 Adding config.xml File . 17 Using Java System Properties. 18 Setting up HTTPS . 18 Appendix A: Repository Connectors . 19 ClearCase . 19 CVS . 19 Folder Path . 20 Folder (use GNATHub). 21 Git. 21 Perforce . 23 PTC Integrity . 25 SVN . 26 Synergy. 28 TFS . 30 Zip Upload . 32 Using Multiple Nodes . 32 Appendix B: Data Providers . 34 AntiC . 34 Automotive Coverage Import . 34 Automotive Tag Import. 35 Axivion. 35 BullseyeCoverage Code Coverage Analyzer. 36 CANoe. 36 Cantata . 38 CheckStyle. .. -

Altova Umodel 2012 User & Reference Manual
User and Reference Manual Altova UModel 2012 User & Reference Manual All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Published: 2012 © 2012 Altova GmbH UML®, OMG™, Object Management Group™, and Unified Modeling Language™ are either registered trademarks or trademarks of Object Management Group, Inc. in the United States and/or other countries. Table of Contents 1 UModel 3 2 Introducing UModel 6 3 What's new in UModel 8 4 UModel tutorial 14 4.1 Starting UModel................................................................................................................. 16 4.2 Use cases ................................................................................................................ -

Ansys SCADE Lifecycle®
EMBEDDED SOFTWARE Ansys SCADE LifeCycle® SCADE LifeCycle is part of the Ansys Embedded Software family of products and solutions that includes modules providing unique support for application lifecycle management. This product line features requirements traceability via Application Lifecycle Management (ALM) tools, traceability from models, configuration and change management, and automatic documentation generation. SCADE LifeCycle enhances the functionalities of Ansys SCADE® tools with add-on modules that bridge SCADE solutions and Requirement Management tools or PLM/ALM (Product Lifecycle Management/ Application Lifecycle Management) tools. With SCADE LifeCycle, all systems and software teams involved in critical applications development can manage and control their design and verification activities across the full life cycle of their SCADE applications. / Requirements Traceability SCADE LifeCycle Application Lifecycle Management (ALM) Gateway provides an integrated traceability analysis solution for safety-critical design processes with SCADE Architect, SCADE Suite, SCADE Display, SCADE Solutions for ARINC 661 and SCADE Test: • Connection to ALM tools: linkage to DOORS NG, DOORS (9.6 and up) Jama Connect, Siemens Polarion, Dassault Systèmes Reqtify 2016. • Graphical creation of traceability links between requirements or other structured documents and SCADE models. • Traceability of test cases from SCADE Test Environment projects. • Bidirectional navigation across requirements and tests. • Customizable Export of SCADE artifacts to DOORS or Jama Connect. • Compliant with DO-178B, DO-178C, EN 50128, IEC 61508, ISO 26262, and IEC 60880 standards. EMBEDDED SOFTWARE / SCADE LifeCycle® // 1 / Project Documentation Generation SCADE LifeCycle Reporter automates the time-consuming creation of detailed and complete reports from SCADE Suite, SCADE Display, SCADE Architect and SCADE UA Page Creator for ARINC 661 designs through: • Generation of reports in RTF or HTML formats. -

Configuration Management for Distributed Development
Software Configuration Management Configuration Management for Distributed Development By Nina Rajkumar. © Think Business Networks Pvt. Ltd., July 2001 All rights reserved. You may make one attributed copy of this material for your own personal use. For additional information or assistance please contact Nina at (+91)422-320-606. www.thinkbn.com • 697A, Trichy Road, Coimbatore, TN 641045. Table of Contents Configuration Management for Distributed Development.............................. 4 Configuration Management ................................................................................ 5 Distributed Development.................................................................................... 5 Cases of Distributed Development ..................................................................... 6 Distance Working ........................................................................................... 6 Outsourcing..................................................................................................... 6 Co-located Groups .......................................................................................... 7 Distributed Groups.......................................................................................... 7 Architecture ........................................................................................................ 8 Remote Login.................................................................................................. 8 Several sites by Master-Slave connections .................................................... -

Opinnäytetyö Ohjeet
Lappeenrannan–Lahden teknillinen yliopisto LUT School of Engineering Science Tietotekniikan koulutusohjelma Kandidaatintyö Mikko Mustonen PARHAITEN OPETUSKÄYTTÖÖN SOVELTUVAN VERSIONHALLINTAJÄRJESTELMÄN LÖYTÄMINEN Työn tarkastaja: Tutkijaopettaja Uolevi Nikula Työn ohjaaja: Tutkijaopettaja Uolevi Nikula TIIVISTELMÄ LUT-yliopisto School of Engineering Science Tietotekniikan koulutusohjelma Mikko Mustonen Parhaiten opetuskäyttöön soveltuvan versionhallintajärjestelmän löytäminen Kandidaatintyö 2019 31 sivua, 8 kuvaa, 2 taulukkoa Työn tarkastajat: Tutkijaopettaja Uolevi Nikula Hakusanat: versionhallinta, versionhallintajärjestelmä, Git, GitLab, SVN, Subversion, oppimateriaali Keywords: version control, version control system, Git, GitLab, SVN, Subversion, learning material LUT-yliopistossa on tietotekniikan opetuksessa käytetty Apache Subversionia versionhallintaan. Subversionin käyttö kuitenkin johtaa ylimääräisiin ylläpitotoimiin LUTin tietohallinnolle. Lisäksi Subversionin julkaisun jälkeen on tullut uusia versionhallintajärjestelmiä ja tässä työssä tutkitaankin, olisiko Subversion syytä vaihtaa johonkin toiseen versionhallintajärjestelmään opetuskäytössä. Työn tavoitteena on löytää opetuskäyttöön parhaiten soveltuva versionhallintajärjestelmä ja tuottaa sille opetusmateriaalia. Työssä havaittiin, että Git on suosituin versionhallintajärjestelmä ja se on myös suhteellisen helppo käyttää. Lisäksi GitLab on tutkimuksen mukaan Suomen yliopistoissa käytetyin ja ominaisuuksiltaan ja hinnaltaan sopivin Gitin web-käyttöliittymä. Näille tehtiin -

Versie Beheer Systemen (VCS) 1
Versie beheer systemen (VCS) 1 Computerclub Volwassenen, Jeugd en Informatica vzw www.vji.be Versie beheer systemen (VCS) Inleiding ..................................................................................................................................... 2 Beheer repository en client programma’s .............................................................................. 2 In- en uitchecken, merging, labeling, branching.................................................................... 2 Software ..................................................................................................................................... 3 Microsoft Visual SourceSafe (VSS) ...................................................................................... 3 SourceOffSite..................................................................................................................... 3 VSSConnexion................................................................................................................... 3 Borland StarTeam .................................................................................................................. 3 CVS (Concurrent Versions System) ...................................................................................... 4 CvsGui................................................................................................................................4 TortoiseCVS...................................................................................................................... -
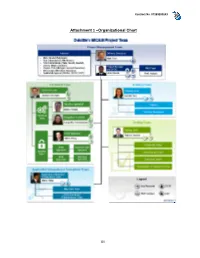
85 Attachment 1 –Organizational Chart
Contract No. 071B3200143 Attachment 1 –Organizational Chart 85 Contract No. 071B3200143 Appendix A - Breakdown of Hardware and Related Software Table 1: Hardware Cost ($): State Brand, Model # Item Specifications will provide from Comments and Description existing Contracts Total # of Virtual The hardware is Machines: 48 sized for Production, QA/Staging, Secure-24 VMware Total # of Virtual Development, and Cluster Access for CPUs: 96 Sandbox Server deploying ISIM, environments in the ISAM and ISFIM Total Virtual RAM: primary data center components 416 GB and for Production, and QA environments in the OS: RedHat Linux secondary data 6.x center The total storage is estimated for Total Storage: 35.7 Production, , TB QA/Staging, Development and Enterprise Class Sandbox Storage (3.8TB of Bronze SAN Storage Tier, 15.8TB of environments in the Silver Tier, 5.1TB of primary data center Logs Tier, 11TB of and for Production, Gold Tier) QA environments in the secondary data center CD/DVD Backup Device None None Rack w/ Power Supply Rack mountable Redundant Power Screen None None A total of 10 Web Gateway appliances are estimated for Production, QA/Staging, Web Gateway Development and Any other Hardware (list) v7.0 Hardware Appliance Sandbox environments in the primary data center and for Production, QA environments in the secondary data center. TOTAL $ 86 Contract No. 071B3200143 Table 2: Related Software Software Component Product Name Cost ($): State # of Licenses Comments License and Version will provide from existing Contracts Contractor user laptops already include this software. We will reuse the Report writers MS Office 2010 State owned software State of Michigan user licenses laptops will need this software for up to 4 users. -

Using Visual COBOL in Modern Application Development Micro Focus the Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK
Using Visual COBOL in Modern Application Development Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com © Copyright 2018-2020 Micro Focus or one of its affiliates. MICRO FOCUS, the Micro Focus logo and Visual COBOL are trademarks or registered trademarks of Micro Focus or one of its affiliates. All other marks are the property of their respective owners. 2020-08-25 ii Contents Using Visual COBOL in Modern Application Development ........................... 4 Introduction to Modern Application Development ................................................................4 What is Modern Application Development? ..............................................................4 Key Concepts in Modern Application Development ..................................................5 Steps Involved in Modern Application Development ................................................ 6 Agile Methods ..................................................................................................................... 7 Introduction to Agile Methods ...................................................................................7 Agile Development Workflow ....................................................................................7 Agile Development and Micro Focus Development Tools .........................................9 Continuous Integration ...................................................................................................... 11 Introduction to Continuous Integration .................................................................. -

Revision Control Solutions to Protect Your Documents and Track Workflow
Revision Control Solutions to Protect Your Documents and Track Workflow WHITE PAPER Contents Overview 3 Common Revision Control Systems 4 Revision Control Systems 4 Using BarTender with Revision Control Systems 4 Limitations of Windows Security 5 Librarian 6 Librarian Features 6 Benefits of Using Librarian with BarTender 7 File States, Publishing and Workflow in Librarian 8 Don’t Forget About Security! 9 Related Documentation 10 Overview A revision control system is based around the concept of tracking changes that happen within directories or files, and preventing one user from overwriting the work of another. Some revision control systems are also used to establish and track workflow for the progression of a file through a series of states. The collection of files or directories in a revision control system are usually called a repository. These systems allow you to specify a directory, file or group of files that will have their changes tracked. This frequently entails users "checking out" and "checking in" files from a repository. Changes are tracked as the user edits the folder or file; these changes will be visible to all users once the item is checked back in. Each revision is annotated with a timestamp and the person making the change. Some of the benefits of revision control include: l Automatic revision numbering for easy tracking. l Enhanced security. Not only does a "check in" and "check out" system keep one user's work from overwriting another, it can prevent unauthorized or even malicious users from accessing a document. l Some revision control systems include publishing "states," which allow you to track the publishing progress of a document and establish a logical, traceable workflow. -

Main Brochure2.Indd
Automate your Build Process . Powerful and fl exible user interface . Automate version control, compilers, install builders, deployment, testing, notifi cations, and lots more... Dynamic build process using fl ow control, iterators, loops, and exceptions . Full debugger built in - breakpoints, variable watches, live logging . Script events for every action to customise your build process Hierarchical Logging Error Handling FinalBuilder ActionStudio . The log is presented in the same . Easily detect and handle errors during . Allows development of native FinalBuilder hierarchy as your build process your build process actions . Optionally view live log output . Exception handling actions . Includes property page designer and as the build runs include: TRY, CATCH, FINALLY code editor with syntax highlighting . Builds logs are automatically . Control the fl ow of your build process . Develop actions in VBScript, JScript, COM, archived and recover from errors or any .Net language such as C#, VB.Net or Delphi for .Net . Export the log as XML, HTML, or . Unhandled errors trigger the OnFailure Text action list . Included in all editions of FinalBuilder VSoft Technologies Pty Ltd http://www.fi nalbuilder.com ABN: 82 078 466 092 P.O. Box 126, Erindale Centre, ACT 2903, Australia salesinfo@fi nalbuilder.com Phone: +61 2 6282 7488, Fax +61 2 6282 7588 news://news.fi nalbuilder.com FinalBuilder Integrates with your version control system . Microsoft TeamSystem Use a GUI instead of XML fi les . Microsoft Visual SourceSafe . Perforce Although FinalBuilder uses an XML based fi le format, you . IBM Rational ClearCase don’t need to understand it or even look at it. The FinalBuilder . QSC Team Coherence GUI allows you to quickly and easily create a build process . -

Market Definition/Description Magic Quadrant
Magic Quadrant for Application Development Life Cycle Management http://www.gartner.com/technology/reprints.do?id=1-1OR69EF&ct=131231&st=sb# 19 November 2013 ID:G00249074 Analyst(s): Thomas E. Murphy, Jim Duggan, Nathan Wilson Market Definition/Description The application development life cycle management (ADLM) tool market is focused on the planning and governance activities of the software development life cycle (SDLC). ADLM products are focused on the "development" portion of an application's life, with the term ADLM evolving from the term application life cycle management (ALM). Key elements of an ADLM solution include: Software requirements definition and management Software change and configuration management Software project planning, with a current focus on agile planning Work item management Quality management, including defect management In addition, other key capabilities include: Reporting Workflow Integration to version management Support for wikis and collaboration Strong facilities for integration to other ADLM tools This Magic Quadrant represents a snapshot of the ADLM market at a particular point in time. Gartner advises readers not to compare the placement of vendors from prior years. The market is changing — vendor acquisitions, partnerships, solution development and alternative delivery are evidence of these changes — and the criteria for selecting and ranking vendors continue to evolve. Our assessments take into account the vendors' current product offerings and overall strategies, as well as their future initiatives and product road maps. We also factor in how well vendors are driving market changes or adapting to changing market requirements. This Magic Quadrant will help CIOs and business and IT leaders who are developing their ADLM strategies to assess whether they have the right products and enterprise platforms to support them.