International Journal of Innovative Technology and Exploring Engineering
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

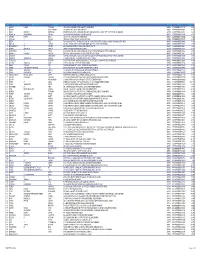
LMRC / Corporate Office Date: 31.08.2016
TSSPDCL - LMRC / Corporate office Date: 31.08.2016 Name of 11 KV Name of the Relay Alternate Supply S.No Circle Name of 33/11KV SS Vol From To Duration Cause of Breakdown Feeder Division Indication Arranged 1 Parsapur Mahabubnagar 11kv Mahabubnagar 6:00 10:30 4:30 11KV Jumper cut at Parsapur (V) - 2 Hasnabad Mahabubnagar 11kv Mahabubnagar 6:15 13:10 6:55 11KV Conductor cut at Hasnabad forest (V) - 3 Perapalla Mahabubnagar 11kv Mahabubnagar 5:20 13:00 7:40 11KV Insuletar failure at Perapalla (vi) 4 Laxmipur Jadcherla 11kv Jadcherla 4:00 9:00 5:00 11KV Conductor cut at Appireddypally (vi) 5 Bandamidipally Jadcherla 11kv Jadcherla 8:00 12:30 4:30 Tree follon the line near Kaverammapet 6 Industrial Jadcherla 11kv Jadcherla 7:45 12:25 4:45 Insulator fail near Polepally 7 MBNR Chukkapur Jadcherla 11kv Jadcherla 9:00 10:30 1:30 11kv wire cut near Cheepnunthala 8 Kishan Nagar Jadcherla 11kv Jadcherla 4:40 9:15 4:35 Insulator fail near Chilukamarry 9 NADIGADDA Nagarkurnool 11kv Nagarkurnool 2:30 12:00 9:30 2POLES CONDUCTOR CUT NADIGADDA AGL LAND - INSULATOR FAILED NEAR MADURANAGAR 10 CHOUTAPALLY Nagarkurnool 11kv Nagarkurnool 3.00 15.20 12:20 - COLNEY 11 RANGAPUR Nagarkurnool 11kv Nagarkurnool 3.00 12.00 9:00 POLESHETYPALLY ROAD T/F PRABULAM - 12 CHANDRAKAL Nagarkurnool 11kv Nagarkurnool 3.00 12.00 9:00 11KV WIRE CUT AT NAKALA PALLY GATE - 13 SATHAPUR Nagarkurnool 11kv Nagarkurnool 6.00 11.40 5:40 INSULATOR FAILED AT JONALBIGUDA (V) - 1 Marriguda Thamadapally 11kv Devarakonda 03.00 07.00 04.00 E/L 11Kv Insulator Failed - 2 Kattangur Powerloom -

River Inundation and Hazard Mapping a Case Study of North Zone –Surat City
Patel Chandresh G, Dr.P.J. Gundaliya . /International Journal of New Technologies in Science and Engineering Vol. 2, Issue 2, Aug 2015, ISSN 2349-0780 River Inundation and Hazard Mapping a Case Study of North Zone –Surat City Patel Chandresh G, Assistant Professor, Ganpat University, Kherva Dr.P.J. Gundaliya, Associate Professor, LDCE, Ahmedabad Abstract: New technologies, such as Geographical Information System (GIS) and Remote Sensing (RS) are helping the researchers to create accurate floodplain maps with improved efficiency. This paper illustrates generation of Digital Elevation Model (DEM) and GIS applications for developing floodplain models of North Zone of Surat City, fastest growing city of Gujarat state, India. Flood event occurred in 2006 and discharge observed near Nehru Bridge is taken as reference to workout probable submergence depth of different area lying in North Zone of Surat city. Based on flood frequency analysis of the study area flood inundation map for flood return period of 30, 32 (Worst flood event-2006) and 35 years (future flood event) are generated in GIS environment. Keywords: DEM, Flood, North Zone, River I. INTRODUCTION Flooding is one of the serious natural hazards in the world [1] ,and it accounts for 40% of all deaths caused by natural disasters, with most flood events occurring in developing, tropical regions [2] .Floods are of many types including flash flooding [3] , flooding due to rising ground water [4] , coastal flooding [5] and flooding due to the opening or breaking of a dam or reservoir [6] .Floods resulting from excessive rainfall within a short period of time and consequent high river discharge damage crops and infrastructure. -

Psyphil Celebrity Blog Covering All Uncovered Things..!! Vijay Tamil Movies List New Films List Latest Tamil Movie List Filmography
Psyphil Celebrity Blog covering all uncovered things..!! Vijay Tamil Movies list new films list latest Tamil movie list filmography Name: Vijay Date of Birth: June 22, 1974 Height: 5’7″ First movie: Naalaya Theerpu, 1992 Vijay all Tamil Movies list Movie Y Movie Name Movie Director Movies Cast e ar Naalaya 1992 S.A.Chandrasekar Vijay, Sridevi, Keerthana Theerpu Vijay, Vijaykanth, 1993 Sendhoorapandi S.A.Chandrasekar Manorama, Yuvarani Vijay, Swathi, Sivakumar, 1994 Deva S. A. Chandrasekhar Manivannan, Manorama Vijay, Vijayakumar, - Rasigan S.A.Chandrasekhar Sanghavi Rajavin 1995 Janaki Soundar Vijay, Ajith, Indraja Parvaiyile - Vishnu S.A.Chandrasekar Vijay, Sanghavi - Chandralekha Nambirajan Vijay, Vanitha Vijaykumar Coimbatore 1996 C.Ranganathan Vijay, Sanghavi Maaple Poove - Vikraman Vijay, Sangeetha Unakkaga - Vasantha Vaasal M.R Vijay, Swathi Maanbumigu - S.A.Chandrasekar Vijay, Keerthana Maanavan - Selva A. Venkatesan Vijay, Swathi Kaalamellam Vijay, Dimple, R. 1997 R. Sundarrajan Kaathiruppen Sundarrajan Vijay, Raghuvaran, - Love Today Balasekaran Suvalakshmi, Manthra Joseph Vijay, Sivaji - Once More S. A. Chandrasekhar Ganesan,Simran Bagga, Manivannan Vijay, Simran, Surya, Kausalya, - Nerrukku Ner Vasanth Raghuvaran, Vivek, Prakash Raj Kadhalukku Vijay, Shalini, Sivakumar, - Fazil Mariyadhai Manivannan, Dhamu Ninaithen Vijay, Devayani, Rambha, 1998 K.Selva Bharathy Vandhai Manivannan, Charlie - Priyamudan - Vijay, Kausalya - Nilaave Vaa A.Venkatesan Vijay, Suvalakshmi Thulladha Vijay 1999 Manamum Ezhil Simran Thullum Endrendrum - Manoj Bhatnagar Vijay, Rambha Kadhal - Nenjinile S.A.Chandrasekaran Vijay, Ishaa Koppikar Vijay, Rambha, Monicka, - Minsara Kanna K.S. Ravikumar Khushboo Vijay, Dhamu, Charlie, Kannukkul 2000 Fazil Raghuvaran, Shalini, Nilavu Srividhya Vijay, Jyothika, Nizhalgal - Khushi SJ Suryah Ravi, Vivek - Priyamaanavale K.Selvabharathy Vijay, Simran Vijay, Devayani, Surya, 2001 Friends Siddique Abhinyashree, Ramesh Khanna Vijay, Bhumika Chawla, - Badri P.A. -

ED Likely to Seize Bank Accounts of Celebrities in Drugs Case
Follow us on: @TheDailyPioneer facebook.com/dailypioneer RNI No. TELENG/2018/76469 Established 1864 ANALYSIS 7 MONEY 8 SPORTS 12 Published From CASTE CENSUS: STERILE INDIA’S PLAYING XI HYDERABAD DELHI LUCKNOW GST MOP UP TOPS RS 1L-CR FOR BHOPAL RAIPUR CHANDIGARH IDEAS OF POLITICIANS SECOND STRAIGHT MONTH IN AUG IN FOCUS BHUBANESWAR RANCHI DEHRADUN VIJAYAWADA *LATE CITY VOL. 3 ISSUE 313 HYDERABAD, THURSDAY, SEPTEMBER 2, 2021; PAGES 12 `3 *Air Surcharge Extra if Applicable VISHAL SIGNS PAN-INDIA FILM { Page 11 } www.dailypioneer.com FISHERMAN NETS ‘FISH WITH HEART OF ACTRESS SAIRA BANU, ADMITTED TO ROAD AHEAD MAY BE BUMPIER THAN POPE FRANCIS SAYS NOT RESIGNING, GOLD', TAKES HOME OVER RS 1 CRORE HINDUJA HOSPITAL, CURRENTLY IN ICU HOPED: SUNDAR PICHAI TO GOOGLE LIVING ‘NORMAL LIFE’ AFTER SURGERY fisherman from Maharashtra's Palghar, near Mumbai, had eteran actress Saira Banu, who was admitted to Mumbai's an Francisco, United States: Google on Tuesday extended ope Francis is not thinking of resigning and is living "a never imagined that he would make a fortune with his Hinduja Hospital a couple of days ago after she the option for its employees to work from home into next totally normal life" following intestinal surgery in July, he Acatch and earn crores overnight. Chandrakant Tare, a Vcomplained of blood pressure-related issues, has been Syear due to the pandemic. Returning to Google campuses Psaid in a radio interview on Wednesday. Francis, 84, fisherman from Murbe village in Palghar district, took his boat moved to the Intensive Care Unit (ICU) ward of the hospital on will remain voluntary globally through January 10, with local dismissed an Italian newspaper report that he might step to the sea for the first time on August 28 after the monsoon Wednesday, reports news agency ANI. -
Section 124- Unpaid and Unclaimed Dividend
Sr No First Name Middle Name Last Name Address Pincode Folio Amount 1 ASHOK KUMAR GOLCHHA 305 ASHOKA CHAMBERS ADARSHNAGAR HYDERABAD 500063 0000000000B9A0011390 36.00 2 ADAMALI ABDULLABHOY 20, SUKEAS LANE, 3RD FLOOR, KOLKATA 700001 0000000000B9A0050954 150.00 3 AMAR MANOHAR MOTIWALA DR MOTIWALA'S CLINIC, SUNDARAM BUILDING VIKRAM SARABHAI MARG, OPP POLYTECHNIC AHMEDABAD 380015 0000000000B9A0102113 12.00 4 AMRATLAL BHAGWANDAS GANDHI 14 GULABPARK NEAR BASANT CINEMA CHEMBUR 400074 0000000000B9A0102806 30.00 5 ARVIND KUMAR DESAI H NO 2-1-563/2 NALLAKUNTA HYDERABAD 500044 0000000000B9A0106500 30.00 6 BIBISHAB S PATHAN 1005 DENA TOWER OPP ADUJAN PATIYA SURAT 395009 0000000000B9B0007570 144.00 7 BEENA DAVE 703 KRISHNA APT NEXT TO POISAR DEPOT OPP OUR LADY REMEDY SCHOOL S V ROAD, KANDIVILI (W) MUMBAI 400067 0000000000B9B0009430 30.00 8 BABULAL S LADHANI 9 ABDUL REHMAN STREET 3RD FLOOR ROOM NO 62 YUSUF BUILDING MUMBAI 400003 0000000000B9B0100587 30.00 9 BHAGWANDAS Z BAPHNA MAIN ROAD DAHANU DIST THANA W RLY MAHARASHTRA 401601 0000000000B9B0102431 48.00 10 BHARAT MOHANLAL VADALIA MAHADEVIA ROAD MANAVADAR GUJARAT 362630 0000000000B9B0103101 60.00 11 BHARATBHAI R PATEL 45 KRISHNA PARK SOC JASODA NAGAR RD NR GAUR NO KUVO PO GIDC VATVA AHMEDABAD 382445 0000000000B9B0103233 48.00 12 BHARATI PRAKASH HINDUJA 505 A NEEL KANTH 98 MARINE DRIVE P O BOX NO 2397 MUMBAI 400002 0000000000B9B0103411 60.00 13 BHASKAR SUBRAMANY FLAT NO 7 3RD FLOOR 41 SEA LAND CO OP HSG SOCIETY OPP HOTEL PRESIDENT CUFFE PARADE MUMBAI 400005 0000000000B9B0103985 96.00 14 BHASKER CHAMPAKLAL -

Probabilidades E Estat´Istica
Probabilidades e Estat´ıstica Segundo exame/segundo teste - 08/07/2006 Sala QA Capacidade: 55 34078 FRANCISCO JORGE CAMPANTE AMARO 35935 LU´IS MIGUEL DA MOTA DORES PONCE DE LEAO˜ 39428 PEDRO MIGUEL DE ALMEIDA LIMA 40587 NUNO PEDRO CARDOSO BARRADAS BOTELHO LOUREN ¸CO 41723 NUNO PEDRO RIBEIRO 42708 NUNO ALEXANDRE OLIVEIRA FELIX´ 42844 SANDRA MARIA PEDRO MARQUES CASTELO 43285 FERNANDO JOSE´ PEREIRA MARQUES 44032 PEDRO MARIA VASCONCELOS DE ALBERGARIA PINHEIRO MOREIRA 44181 MARIA DE FATIMA´ BICHARDO BRAVO 45341 HUGO DANIEL RAMOS FONSECA 45507 LU´IS PEDRO RIBEIRO SANTANA RODRIGUES 45551 PEDRO MIGUEL GOMES MOTA CARVALHO 45570 RICARDO MIGUEL CUSTODIO´ MAUR´ICIO 45599 TIAGO MANUEL FERREIRA VIEIRA 46016 D´ILIA MARIA TAVARES LACERDA DE FIGUEIREDO 46212 SONIA´ ALEXANDRA HELENO FERREIRA 46241 JOAO˜ FILIPE RODRIGUES DRUMOND 46450 FILIPE MIGUEL BORGAS DUARTE 46698 SAMUEL CALVARIO´ PAIS MARTINS 46806 ANDRE´ FILIPE MENAIA CORREIA DELGADO 46836 DIOGO MIGUEL DIAS DUARTE 46841 FILIPE ALEXANDRE LEITAO˜ DOS SANTOS 46849 GON ¸CALOFILIPE RODRIGUES FORTES 46884 JOAO˜ RICARDO TEODOSIO´ GLORIA´ FRAGOSO 46886 JONAS GALHORDAS DUARTE ALVES 46899 LUC´ILIO SABINO GUIMARAES˜ COELHO DE OLIVEIRA 46929 NELSON MANUEL EDUARDO VER´ISSIMO 46940 NUNO MIGUEL VAZ AFONSO 46950 PEDRO MANUEL NATAL 46980 RUI GON ¸CALOMATIAS SAMPAIO 47152 PEDRO JOSE´ LUCAS NEVES PEREIRA 47165 PEDRO NUNO RODRIGUES BENTO 47609 TIAGO MANUEL DOS SANTOS RODRIGUES 47685 HUGO MIGUEL COSTA BRAS´ 48223 ANDRE´ MARTINS MAUR´ICIO 48224 ANTONIO´ PEDRO MARQUES FERREIRO 48249 FERNANDO MIGUEL CORREIA LEANDRO FERREIRA -

Status of Release of Scholarship to Students for the AY 2013-14 Under PMSSS Scheme for J&K Students (Till 30/04/2016) Note: 1
Status of Release of Scholarship to Students for the AY 2013-14 under PMSSS Scheme for J&K students (Till 30/04/2016) Note: 1. For any query sent mail to [email protected] 2. Scholarships shown as released in AY 2015-16 are subject to verification & confirmation of account details of students for DBT Status of Release of Status of Release of Status of Release of 1st Renewal 2nd Renewal S.No. Student'S Name College Name State Course Fresh Scholarship Scholarship Scholarship (AY 2015- 2013-14 (AY 2014 -15) 16) International Institute Of 1 Manik Gupta Information Technology, Andhra Pradesh Engineering Left The Institute Left The Institute Left The Institute Hyderabad Shadan College Of Engineering & 2 Aadil Qayoom Wani Andhra Pradesh Engineering Claim Not Received Claim Not Received Claim Not Received Technology Shadan College Of Engineering & 3 Subyta Hameed Shah Andhra Pradesh Engineering Claim Not Received Claim Not Received Claim Not Received Technology 4 Mohit Kumar Chadha Vemu Institute Of Technology Andhra Pradesh Engineering Claim Not Received Claim Not Received Claim Not Received 5 Diksha Manhas CGC Group Of College Chandigarh Engineering Fee Receipts Pending Claim Not Received Claim Not Received 6 Irfan Wali Dar CGC Group Of College Chandigarh Engineering Released Claim Not Received Claim Not Received 7 Manav Juneja CGC Group Of College Chandigarh Engineering Released Claim Not Received Claim Not Received 8 Mohd Zahoor Sadiq CGC Group Of College Chandigarh Engineering Released Claim Not Received Claim Not Received -

List of the Firms for Rate Contract 2011-12 for Chemicals, Glassware, Plastic Wares, Diagnostic Kits
1 Rate Contract 2015-16 IVRI, Izatnagar ANNEXURE-I LIST OF THE FIRMS FOR RATE CONTRACT 2015-16 FOR CHEMICALS, GLASSWARE, PLASTIC WARES, DIAGNOSTIC KITS ETC. Sl. Name of Firm Discount Item for which applied for Price List Local Dealer No. Offered Rate Contract effective for 1. M/s ARC Biosciences, B-48, 5% Plasticware & Hardcopy Direct Supply by principal firm in all areas. Basement, Karamat Complex, Laboratory items 2015 Nishatganj, Lucknow-226006. Mob: 09307834565, 07084023907 2. M/s Alfa Aesar Johnson 5% Chemicals Softcopy 1. M/s Sambhav Enterprises, UG-13, Commercial Complex Matthey Chemicals India Pvt. 2015-16 Rajendra Nagar Chauraha Bareilly – 243122. Ltd., Survey No.195, 196, Mob.8755720075 (for Bareilly & Mukteswar) Kandlakoya, Medchal Mandal, 2. M/s Shree Chemicals, Shop No. 2, Al-shan Co-op RR District, Hyderabad-501401. Society,381 Bhawani Peth Harka Nagar Near, Vinay High Tel.No.040-67301234 School Pune – 411 002 3. M/s Scientific & Allied Products #306, SaraswathiNiwas, 5th Main Channel Road, Saraswathipuram, Ulsoor Bangalore – 560 008 4. M/s Pattanaik Scientific Supply Syndicate 48, Madhusudan Nagar, Unit – IV, Bhubaneswar – 751 001 3. M/s Avantor Performance 5%on Chemicals & Glassware Softcopy 1. M/s Sterling Scientific, C-276A, Rajendra Nagar, Bareilly- Materials India Limited, 17th brand- 2015-16 243122. Floor, Building No. 5 Tower C IDT, 2. M/s Balaji Scientific & Chemicals, Street No. 2 Opp.- DLF Cyber City Phase –III advansta, Hotel Nanaks, Rampur Road Haldwani – 263139 Gurgaon-122002, Haryana, Bensphera Uttrakhand, (Mob: 09897037381) India Phone: (0124) 4656700, & 4656750 10% on brand- Rankem, J.T. Baker 4. -

YOUR DHAKA ART SUMMIT “Dhaka Art Summit Has Set the Gold Standard for the Visual Arts in South Asia.” -Bunty Chand, Director of Asia Society, India CONTENTS
YOUR DHAKA ART SUMMIT “Dhaka art summit has set the gold standard for the visual arts in South Asia.” -Bunty Chand, Director of Asia Society, India CONTENTS ABOUT DAS ........................................................................ 6 PROGRAMME ..................................................................... 8 SCHEDULE ........................................................................ 25 VENUE MAP ...................................................................... 54 DHAKA ............................................................................... 56 OUR PARTNERS ................................................................ 60 Front Cover: Louis Kahn, National Parliament Building, Dhaka. Image credit: Randhir Singh 2 3 The Missing One installation view. Photo courtesy of the Dhaka Art Summit and Samdani Art Foundation. Photo credit: Jenni Carter DHAKA ART SUMMIT 2018 “I have never experienced something as art focused, open and inclusive as I just did at Dhaka Art Summit. The calibre of the conversations was a rare happening in our region.¨ -Dayanita Singh, DAS 2016 Participating Artist 5 The Dhaka Art Summit (DAS) is an international, non-commercial research and exhibition platform for art and architecture connected to South Asia. With a core focus on Bangladesh, DAS re-examines how we think about these forms of art in both a regional and an international context. Founded in 2012 by the Samdani Art Foundation, DAS is held every two years in a public- private partnership with the Bangladesh Shilpakala Academy, with the support of the Ministry of Cultural Affairs and Ministry of Information of the People’s Republic of Bangladesh, the National Tourism Board, Bangladesh Investment Development Authority (BIDA), and in association with the Bangladesh National Museum. Rejecting the traditional biennale format to create a more generative space for art and exchange, DAS’s interdisciplinary programme concentrates its endeavours towards the advancement and promotion of South Asia’s contemporary and historic creative communities. -

University Aishe Code
University Aishe Code Aishe Srno Code University Name 1 U-0122 Ahmedabad University (Id: U-0122) 2 U-0830 ANANT NATIONAL UNIVERSITY (Id: U-0830) 3 U-0125 Carlox Teachers University, Ahmedabad (Id: U-0125) Centre for Environmental Planning and Technology University, Ahmedabad (Id: U- 4 U-0127 0127) 5 U-0131 Dr. Babasaheb Ambedkar Open University, Ahmedabad (Id: U-0131) 6 U-0775 GLS UNIVERSITY (Id: U-0775) 7 U-0135 Gujarat Technological University, Ahmedbabd (Id: U-0135) 8 U-0136 Gujarat University, Ahmedabad (Id: U-0136) 9 U-0817 GUJARAT UNIVERSITY OF TRANSPLANTATION SCIENCES (Id: U-0817) 10 U-0137 Gujarat Vidyapith, Ahmedabad (Id: U-0137) 11 U-0139 Indian Institute of Technology, Gandhinagar (Id: U-0139) 12 U-0922 Indrashil University (Id: U-0922) INSTITUTE OF INFRASTRUCTURE TECHNOLOGY RESEARCH AND MANAGEMENT 13 U-0765 (IITRAM) (Id: U-0765) 14 U-0734 LAKULISH YOGA UNIVERSITY, AHMEDABAD (Id: U-0734) 15 U-0146 Nirma University, Ahmedabad (Id: U-0146) 16 U-0790 RAI UNIVERSITY (Id: U-0790) 17 U-0595 Rakshashakti University, Gujarat (Id: U-0595) 18 U-0123 Anand Agricultural University, Anand (Id: U-0123) 19 U-0128 Charotar University of Science & Technology, Anand (Id: U-0128) 20 U-0148 Sardar Patel University, Vallabh Vidyanagar (Id: U-0148) 21 U-0150 Sardarkrushinagar Dantiwada Agricultural University, Banaskantha (Id: U-0150) 22 U-0124 Maharaja Krishnakumarsinhji Bhavnagar University (Id: U-0124) 23 U-0126 Central Univeristy of Gujarat, Gandhinagar (Id: U-0126) 24 U-0594 Children University, Gandhinagar (Id: U-0594) Dhirubhai Ambani Institute -

Goons Abduct Female Protagonist Kalyani and Take Her to a Secluded
ACTION BY BCCC ON COMPLAINTS RECEIVED FROM 1 SEPTEMBER 2017 TO 30 JUNE 2019 A : SPECIFIC A-1CONTENT : Specific S.NO Channel Total Nature of Complaints Telecast date of the Action By BCCC Progra Number programme reviewed mme of by BCCC Complain 1 Silsila Colors 1ts Molly and Nandini are childhood friends. Molly is married to Kunal 27-12-2018 BCCC admitted the complaint and viewed the episode. Mishti is shown Badalte and Nandini to Rajdeep. After excessive torture by her husband, switching off the bathroom lights when Pari goes for a bath and locks it from Rishton Nandini leaves Rajdeep and comes to stay with Molly. Molly’s outside. The child is shown screaming for help but Mishti plays loud music to Ka’ husband Kunal falls in love with her and divorces her to marry ensure that nobody else in the house can hear her. The little girl Pari faints Nandini. He is unaware that Molly was six months pregnant when inside the bathroom, feeling uneasy. BCCC decided to caution the channel he left her. Molly has a daughter Mishti and Nandini has a that such depiction could influence impressionable minds. The Council daughter Pari, who are also very good friends. When Mishti cautioned the channel to refrain from such depiction in a prolonged manner comes to know the reality of Kunal being her father, she starts even if it was part of the storyline. The complaint was DISPOSED OF. hating him and ends her friendship with Pari. Pari, in absence of her father Kunal, goes and stays with Mishti for a couple of days. -

Crime Patrol Promo of Ek Duje Ke Waaste Page 1 Of
ACTION BY BCCC ON COMPLAINTS RECEIVED FROM 1 SEPTEMBER 2017 TO 31 JANUARY 2020 A : SPECIFIC CONTENT A-1RELATED : Specific COMPLAINTS Content related Programme Channel Total Summary of complaint Telecast date of Action By BCCC Number the programme of reviewed by BCCC Complaint Beyhadh Sony 3s It shows female antagonist Maya plotting and committing a murder to seek BCCC admitted the complaint and viewed the episode. Female protagonist Maya, revenge. The process and method of the murder is shown in detail. The who is a psychopath, sees her sister getting killed by the male protagonist’s father. programme is meant for adults and the telecast time (9 PM) is unsuitable for Maya gets agitated and decides to kill male protagonist Rudra on his wedding day. family viewing. Showing revenge, in terms of murder and similar ghastly acts However, the process and method of murder have not been shown. The show is during primetime, needs consideration for banning. Being an FTII graduate, I themed on the revenge that Maya wants to seek from Rudra’s family. BCCC can opine what is good for public viewing on TV. If it had restricted view like considered it to be a part of the storyline and decided not to intervene. The channel films, the case would have been different. has taken care not to shown scenes of titillation or gore. The complaint was DISPOSED OF. Crime Patrol Sony 2 Episode 07/12/19: It shows scenes of extreme violence and sexual assault in 07/12/2019 BCCC admitted the complaint and viewed the episode.