Practicing a Science of Security a Philosophy of Science Perspective
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is That Thing Called Philosophy of Technology? - R
HISTORY AND PHILOSOPHY OF SCIENCE AND TECHNOLOGY – Vol. IV - What Is That Thing Called Philosophy of Technology? - R. J. Gómez WHAT IS THAT THING CALLED PHILOSOPHY OF TECHNOLOGY? R. J. Gómez Department of Philosophy. California State University (LA). USA Keywords: Adorno, Aristotle, Bunge, Ellul, Feenberg, Habermas, Heidegger, Horkheimer, Jonas, Latour, Marcuse, Mumford, Naess, Shrader-Frechette, artifact, assessment, determinism, ecosophy, ends, enlightenment, efficiency, epistemology, enframing, ideology, life-form, megamachine, metaphysics, method, naturalistic, fallacy, new, ethics, progress, rationality, rule, science, techno-philosophy Contents 1. Introduction 2. Locating technology with respect to science 2.1. Structure and Content 2.2. Method 2.3. Aim 2.4. Pattern of Change 3. Locating philosophy of technology 4. Early philosophies of technology 4.1. Aristotelianism 4.2. Technological Pessimism 4.3. Technological Optimism 4.4. Heidegger’s Existentialism and the Essence of Technology 4.5. Mumford’s Megamachinism 4.6. Neomarxism 4.6.1. Adorno-Horkheimer 4.6.2. Marcuse 4.6.3. Habermas 5. Recent philosophies of technology 5.1. L. Winner 5.2. A. Feenberg 5.3. EcosophyUNESCO – EOLSS 6. Technology and values 6.1. Shrader-Frechette Claims 6.2. H Jonas 7. Conclusions SAMPLE CHAPTERS Glossary Bibliography Biographical Sketch Summary A philosophy of technology is mainly a critical reflection on technology from the point of view of the main chapters of philosophy, e.g., metaphysics, epistemology and ethics. Technology has had a fast development since the middle of the 20th century , especially ©Encyclopedia of Life Support Systems (EOLSS) HISTORY AND PHILOSOPHY OF SCIENCE AND TECHNOLOGY – Vol. IV - What Is That Thing Called Philosophy of Technology? - R. -

Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems
NIST Special Publication 800-160 VOLUME 1 Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems RON ROSS MICHAEL McEVILLEY JANET CARRIER OREN This publication contains systems security engineering considerations for ISO/IEC/IEEE 15288:2015, Systems and software engineering — System life cycle processes. It provides security-related implementation guidance for the standard and should be used in conjunction with and as a complement to the standard. This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-160v1 NIST Special Publication 800-160 VOLUME 1 Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems RON ROSS Computer Security Division National Institute of Standards and Technology MICHAEL McEVILLEY The MITRE Corporation JANET CARRIER OREN Legg Mason This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-160v1 November 2016 INCLUDES UPDATES AS OF 03-21-2018: PAGE XIII U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Willie May, Under Secretary of Commerce for Standards and Technology and Director SPECIAL PUBLICATION 800-160, VOLUME 1 SYSTEMS SECURITY ENGINEERING A Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems ________________________________________________________________________________________________ Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. -

Practicing a Science of Security a Philosophy of Science Perspective
Practicing a Science of Security A Philosophy of Science Perspective Jonathan M. Spring Tyler Moore David Pym University College London The University of Tulsa University College London Gower Street 800 South Tucker Drive London WC1E 6BT London WC1E 6BT Tulsa, OK 74104-9700 Alan Turing Institute [email protected] [email protected] [email protected] ABSTRACT Experiments Structured observations of the empirical are untenable world Our goal is to refocus the question about cybersecurity re- Reproducibility Evaluate by repetition, replication, varia- search from ‘is this process scientific’ to ‘why is this scientific is impossible tion, reproduction, and/or corroboration process producing unsatisfactory results’. We focus on five No laws of common complaints that claim cybersecurity is not or can- Mechanistic explanation of phenomena nature not be scientific. Many of these complaints presume views to make nature intelligible No single associated with the philosophical school known as Logical Em- Specialization necessitates translation ontology piricism that more recent scholarship has largely modified or rejected. Modern philosophy of science, supported by mathe- ‘Just’ Both science and engineering are neces- matical modeling methods, provides constructive resources engineering sary to mitigate all purported challenges to a science of security. Table 1: Five common complaints raised by the science of cy- Therefore, we argue the community currently practices a bersecurity community and positive reframing from the phi- science of cybersecurity. A philosophy of science perspective losophy of science literature. suggests the following form of practice: structured observa- tion to seek intelligible explanations of phenomena, evaluating explanations in many ways, with specialized fields (including engineering and forensics) constraining explanations within Its proponents claim a science of security is needed for ongo- their own expertise, inter-translating where necessary. -

A Cybersecurity Testbed for Industrial Control Systems
A Cybersecurity Testbed for Industrial Control Systems R. Candell, D.M. Anand, and K. Stouffer National Institute of Standards and Technology, Gaithersburg MD, U.S.A [rick.candell, dhananjay.anand, keith.stouffer]@nist.gov Abstract — The National Institute of Standards and Technology (NIST) is developing a cybersecurity testbed for industrial control systems (ICS). The goal of this testbed is to measure the performance of an ICS when instrumented with cybersecurity protections in accordance with practices prescribed by prevailing standards and guidelines. This paper outlines the testbed design and lists research goals, use cases, and performance metrics currently being considered. The paper is also intended to initiate discussion between control and security practitioners – two groups that have had little interaction in the past. Research outcomes from the testbed will highlight specific cases where security technologies impact control performance, as well as motivate methods by which control engineers can leverage security engineering to design control algorithms that extend safety and fault tolerance to include advanced persistent threats. Keywords — industrial control systems, robotics, chemical process control, cybersecurity, industrial security, process resilience, penetration testing, process performance, measurement science, testbed, robotics, robot control, safety, supervisory control and data acquisition (SCADA) I. Introduction Given the increasing interest in security of industrial control systems (ICS) and the evolving nature of advanced persistent threats against critical industrial infrastructure [1], the National Institute of Standards and Technology (NIST) has been actively involved in developing standards for cyber and control systems security via several standards bodies. Examples of such standards and guidelines include [2] and [3]. A research testbed, currently in development at NIST, will provide a platform on which to apply cybersecurity strategies to use cases that are practically relevant to industry. -

Neil Postman
Five Things We Need to Know About Technological Change by Neil Postman Talk delivered in Denver Colorado March 28, 1998 … I doubt that the 21st century will pose for us problems that are more stunning, disorienting or complex than those we faced in this century, or the 19th, 18th, 17th, or for that matter, many of the centuries before that. But for those who are excessively nervous about the new millennium, I can provide, right at the start, some good advice about how to confront it. …. Here is what Henry David Thoreau told us: “All our inventions are but improved means to an unimproved end.” Here is what Goethe told us: “One should, each day, try to hear a little song, read a good poem, see a fine picture, and, if possible, speak a few reasonable words.” Socrates told us: “The unexamined life is not worth living.” Rabbi Hillel told us: “What is hateful to thee, do not do to another.” And here is the prophet Micah: “What does the Lord require of thee but to do justly, to love mercy and to walk humbly with thy God.” And I could say, if we had the time, (although you know it well enough) what Jesus, Isaiah, Mohammad, Spinoza, and Shakespeare told us. It is all the same: There is no escaping from ourselves. The human dilemma is as it has always been, and it is a delusion to believe that the technological changes of our era have rendered irrelevant the wisdom of the ages and the sages. Nonetheless, having said this, I know perfectly well that because we do live in a technological age, we have some special problems that Jesus, Hillel, Socrates, and Micah did not and could not speak of. -

Cyber Security Engineering, Bs
2016-2017 Volgenau School of Engineering CYBER SECURITY ENGINEERING, B.S. 2016 - 2017 Cyber Security Engineering is concerned with the development of cyber resilient systems which include the protection of the physical as well as computer and network systems. It requires a proactive approach in engineering design of physical systems with cyber security incorporated from the beginning of system development. Cyber security engineering is an important quantitative methodology to be used in all industries to include, but not limited to, transportation, energy, healthcare, infrastructure, finance, government (federal, state, and local), and defense. The program is focused on the cyber security engineering of integrated cyber-physical systems. This degree provides a foundation in cyber security engineering, and is most appropriate for students with a strong mathematics and science background. The program is administered by the Dean's Office, Volgenau School of Engineering. Cyber security engineers are part of integrated design and development teams for physical systems that require embedded cyber security design, working with engineers from other disciplines (e.g. civil, mechanical, electrical, systems engineers as well as computer scientists and software engineers). Cyber security engineers are engineers who know technology, but who also have in-depth exposure to the application/domain area. Not only do they provide technological solutions to cyber security problems of engineering systems posed by others, but by having an understanding of the application/domain, they can formulate potential security threats, propose appropriate solutions, and then provide leadership in the design of a system to resist and survive these threats. Because of their interdisciplinary training, cyber security engineers are expected to play an increasing role in attacking some of the most pressing current cyber security issues in the country. -

The Fourth Industrial Revolution: How the EU Can Lead It
EUV0010.1177/1781685818762890European ViewSchäfer 762890research-article2018 Article European View 2018, Vol. 17(1) 5 –12 The fourth industrial © The Author(s) 2018 https://doi.org/10.1177/1781685818762890DOI: 10.1177/1781685818762890 revolution: How the EU journals.sagepub.com/home/euv can lead it Matthias Schäfer Abstract The fourth industrial revolution is different from the previous three. This is because machines and artificial intelligence play a significant role in enhancing productivity and wealth creation, which directly changes and challenges the role of human beings. The fourth industrial revolution will also intensify globalisation. Therefore, technology will become much more significant, because regions and societies that cope positively with the technological impact of the fourth industrial revolution will have a better economic and social future. This article argues that the EU can play an important role in developing an environment appropriate for the fourth industrial revolution, an environment that is vibrant and open to new technologies. Member states would profit from an EU-wide coordinated framework for this area. The EU has to establish new common policies for the market-oriented diffusion and widespread use of new technologies. Keywords Fourth industrial revolution, Technology policy, Industrial policy, Leadership Introduction Historically there have been four industrial revolutions (see Schwab 2016). The first began in the early nineteenth century, when the power of steam and water dramatically increased the productivity of human (physical) labour. The second revolution started almost a hundred years later with electricity as its key driver. Mass industrial production Corresponding author: M. Schäfer, Department Politics and Consulting, Head of the Team for Economic Policy, Konrad-Adenauer- Stiftung, Berlin, Germany. -

Technology, Development and Economic Crisis: the Schumpeterian Legacy
CIMR Research Working Paper Series Working Paper No. 23 Technology, development and economic crisis: the Schumpeterian legacy by Rinaldo Evangelista University of Camerino Piazza Cavour, 19/F, 62032 Camerino (IT) +39-0737-403074 [email protected] June 2015 ISSN 2052-062X Abstract This contribution aims at highlighting the complex, non-linear and potentially contradictory nature of the relationships between technological progress, economic growth and social development, in particular within the context of market based economies. The main (provocative) argument put forward in the paper is that the recent neo-Schumpeterian literature, while providing fundamental contributions to our understanding of innovation, has contributed to the rising of a positivistic reading of the relationship between technology, economy and society, with technology being able to guaranty strong economic growth and (implicitly) social welfare. This is confirmed by the fact that, contrary to other influential heterodox economic schools and Schumpeter himself, in the recent neo- Schumpeterian literature technology is only rarely associated to macroeconomic market failures such as systemic crises, structural unemployment, and the growth of social and economic inequalities. It is also argued that the emergence of a “positivistic bias” in the neo-Schumpeterian literature has been associated to the dominance of a supply-side and micro-based view of the technology-economy relationships. Key words: Technology, Innovation, Schumpeter, Development, Crisis JEL codes: B52, O00, O30. 2 1. Introduction There is no doubt that the last economic crisis, with its depth, extension and length, could have, at least in principle, the potentiality of shaking at the fundamentals the dominant neo-liberal economic thinking and policy framework. -

Systems Security Engineering Fact Sheet
The MITRE Corporation Systems Security Engineering The MITRE Corporation is using Systems Security Engineering (SSE) to ensure the U.S. Air Force fields and sustains resilient capabilities that provide mission assurance against evolving threats. SSE uses scientific and engineering principles to deliver assured system-level protection via a single, full-system/full life cycle view of system security. The Challenge Requirements DMS* Cyber attacks, and our ability to effectively deal with them, impact Cryptography Program our nation’s infrastructure, military Software Protection Assurance capabilities, and commercial and military industry partners. Cyber Anti- HW Supply Chain Risk Tamper technology is thoroughly embed- Assurance Management ded into everything we engineer, including both business and weap- Sustainment Other Information ons systems. The historical ways Assurance in which we acquire, operate, and *Diminishing Manufacturing Sources sustain our systems must change Typical security engineering approach: “As Is” because, given time, sophisticated and persistent attackers will get in. Holistic, integrated, program protection The Solution Systems Security Engineering (SSE) New thinking in the applica- tions of systems engineering is Systems Security Engineering Engineering (SSE) Instructions for required in the face of evolving CPI Identification Engineering threats. MITRE is working with Instructions for SSE Integrated our sponsors to address these Technical Process challenges in a holistic manner (SITP) Anti-Tamper that allows the -

Taking Technology Seriously: Introduction to the Special Issue on New Technologies and Global Environmental Politics • Simon Nicholson and Jesse L
Taking Technology Seriously: Introduction to the Special Issue on New Technologies and Global Environmental Politics • Simon Nicholson and Jesse L. Reynolds* Human beings are at once makers of and made by technology. The ability to wield tools was an essential ingredient in propelling an otherwise unremarkable ape to a position of dominance over ecological and even planetary affairs. This dominance has been attained through a remaking of the physical world and has produced a planet fundamentally altered. Technology, this is to say, has been central to history and human-induced environmental change. Our earliest significant environ- mental impacts appear to have been mass extinctions of megafauna, especially in North and South America, Australia, and the Pacific Islands, enabled by hunting and trapping tools and techniques. These were followed by large-scale land use changes from the rise of agriculture, another early set of technologies that were key to Homo sapiens’ success (Boivin et al. 2016). Technology presents a paradox. Existing, emerging, and anticipated technol- ogies offer remarkable possibilities for human well-being and the environmental condition. Since 1900, global average life expectancy has more than doubled and continues to rise (Roser et al. 2013). Most people can access information and educational opportunities that in the not-too-distant past were restricted to a tiny elite. The growth of farmland—which may be the leading direct driver of change in nature (Intergovernmental Science-Policy Platform on Biodiversity and Ecosystem Services 2019)—has recently been reversed through agricultural intensification (World Bank, n.d.). Ozone-depleting substances have been largely replaced by synthetic substitutes. -
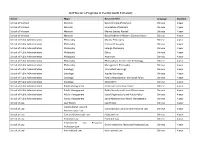
2019 Doctor's Programs in Central South University
2019 Doctor’s Programs in Central South University School Major Research Field Language Duration School of Marxism Marxism Basic Principle of Marxism Chinese 4 year School of Marxism Marxism Sinicization of Marxism Chinese 4 year School of Marxism Marxism Marxist Studies Abroad Chinese 4 year School of Marxism Marxism Basic Problem of Modern Chinese history Chinese 4 year School of Public Administration Philosophy Marxist Philosophy Chinese 4 year School of Public Administration Philosophy Chinese Philosophy Chinese 4 year School of Public Administration Philosophy Foreign Philosophy Chinese 4 year School of Public Administration Philosophy Ethics Chinese 4 year School of Public Administration Philosophy Aesthetics Chinese 4 year School of Public Administration Philosophy Philosophy of Science and Technology Chinese 4 year School of Public Administration Philosophy Management Philosophy Chinese 4 year School of Public Administration Sociology Theoretical Sociology Chinese 4 year School of Public Administration Sociology Applied Sociology Chinese 4 year School of Public Administration Sociology Public Administration and Social Policy Chinese 4 year School of Public Administration Sociology Social Work Chinese 4 year School of Public Administration Public Management Urban and Local Governance Chinese 4 year School of Public Administration Public Management Public Security and Hazard Governance Chinese 4 year School of Public Administration Public Management Social Organizations and Public Policy Chinese 4 year School of Public Administration -

A Systematic Review of Methods for Health Care Technology Horizon Scanning
AHRQ Health Care Horizon Scanning System A Systematic Review of Methods for Health Care Technology Horizon Scanning Prepared for: Agency for Healthcare Research and Quality U.S. Department of Health and Human Services 540 Gaither Road Rockville, MD 20850 Contract No. 290-2010-00006-C Prepared by: Fang Sun, M.D., Ph.D. Karen Schoelles, M.D., S.M., F.A.C.P ECRI Institute 5200 Butler Pike Plymouth Meeting, PA 19462 AHRQ Publication No. 13-EHC104-EF August 2013 This report incorporates data collected during implementation of the U.S. Agency for Healthcare Research and Quality (AHRQ) Health Care Horizon Scanning System by ECRI Institute under contract to AHRQ, Rockville, MD (Contract No. 290-2010-00006-C). The findings and conclusions in this document are those of the authors, who are responsible for its content, and do not necessarily represent the views of AHRQ. No statement in this report should be construed as an official position of AHRQ or of the U.S. Department of Health and Human Services. The information in this report is intended to identify resources and methods for improving the AHRQ Health Care Horizon Scanning System in the future. The purpose of the AHRQ Health Care Horizon Scanning System is to assist funders of research in making well-informed decisions in designing and funding comparative-effectiveness research. This report may periodically be assessed for the urgency to update. If an assessment is done, the resulting surveillance report describing the methodology and findings will be found on the Effective Health Care Program website at: www.effectivehealthcare.ahrq.gov.