Online File W9.1 Wireless Advertising in Action
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FCC-06-11A1.Pdf
Federal Communications Commission FCC 06-11 Before the FEDERAL COMMUNICATIONS COMMISSION WASHINGTON, D.C. 20554 In the Matter of ) ) Annual Assessment of the Status of Competition ) MB Docket No. 05-255 in the Market for the Delivery of Video ) Programming ) TWELFTH ANNUAL REPORT Adopted: February 10, 2006 Released: March 3, 2006 Comment Date: April 3, 2006 Reply Comment Date: April 18, 2006 By the Commission: Chairman Martin, Commissioners Copps, Adelstein, and Tate issuing separate statements. TABLE OF CONTENTS Heading Paragraph # I. INTRODUCTION.................................................................................................................................. 1 A. Scope of this Report......................................................................................................................... 2 B. Summary.......................................................................................................................................... 4 1. The Current State of Competition: 2005 ................................................................................... 4 2. General Findings ....................................................................................................................... 6 3. Specific Findings....................................................................................................................... 8 II. COMPETITORS IN THE MARKET FOR THE DELIVERY OF VIDEO PROGRAMMING ......... 27 A. Cable Television Service .............................................................................................................. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Member Directory
D DIRECTORY Member Directory ABOUT THE MOBILE MARKETING ASSOCIATION (MMA) Mobile Marketing Association Member Directory, Spring 2008 The Mobile Marketing Association (MMA) is the premier global non- profit association established to lead the development of mobile Mobile Marketing Association marketing and its associated technologies. The MMA is an action- 1670 Broadway, Suite 850 Denver, CO 80202 oriented organization designed to clear obstacles to market USA development, establish guidelines and best practices for sustainable growth, and evangelize the mobile channel for use by brands and Telephone: +1.303.415.2550 content providers. With more than 600 member companies, Fax: +1.303.499.0952 representing over forty-two countries, our members include agencies, [email protected] advertisers, handheld device manufacturers, carriers and operators, retailers, software providers and service providers, as well as any company focused on the potential of marketing via mobile devices. *Updated as of 31 May, 2008 The MMA is a global organization with regional branches in Asia Pacific (APAC); Europe, Middle East & Africa (EMEA); Latin America (LATAM); and North America (NA). About the MMA Member Directory The MMA Member Directory is the mobile marketing industry’s foremost resource for information on leading companies in the mobile space. It includes MMA members at the global, regional, and national levels. An online version of the Directory is available at http://www.mmaglobal.com/memberdirectory.pdf. The Directory is published twice each year. The materials found in this document are owned, held, or licensed by the Mobile Marketing Association and are available for personal, non-commercial, and educational use, provided that ownership of the materials is properly cited. -

Android 101 Class 1 of 6
Android vs iOS Throwdown Cheryl Sedota Peter Schnabel Charleston Digital Corridor 1.17.2014 What is Android? Android is a free, open source mobile operating system based on Linux It is ready-made, lightweight & customizable Android can run on any mobile device: mobile phones, phablets, tablets & others! Android was unveiled in November 2007 Android is developed/maintained by Google Who Is Android? Open Handset Alliance = consortium of 84 companies whose govern Android's development of open standards for mobile devices Technology Companies: Google, eBay, PacketVideo... Device Manufacturers: Samsung, HTC, LG, Moto, Sony... Wireless Carriers: Sprint, T-Mobile, NTT DoCoMo... Wireless Chip Manufacturers: Qualcomm, Intel, TI... Standard Disclaimer There is no black-and-white better mobile operating system, Android or iOS Each platorm has its strengths and diferent people prefer diferent features/designs What Users Prefer Android over iOS? Android is more attractive to power users who need to do more Android Prioritizes Can Do over Hairdo Droid Commercial https://www.youtube.com/watch?v=w83UQkiuNZQ Android Does More Android is about being more powerful and DOING MORE. Android is not hyper-focused on a super shiny, polished user experience Faster Innovation All the major tech companies in the Open Handset Alliance are not only backing the Android, they are rapidly pushing it forward, driving broader faster innovation NFC Near Field Communication (NFC) enables short range communication between two devices, or between a device and a passive tag / transmitter without a power source Apply NFC Technology Tap Two Devices Together to Share Files/Photos Apply NFC Technology Google Wallet is an NFC based wireless payment system that allows its users to store debit and credit card information to make payments at PayPass-enabled terminal at checkouts Put It To A Vote Android is the MOST POPULAR mobile operating system 70% of the mobile phones being sold today run Android Faster Innovation Android pushes the envelope, innovating earlier.. -

M-Learning Tools and Applications
2342-2 Scientific m-Learning 4 - 7 June 2012 m-Learning Tools and Applications TRIVEDI Kirankumar Rajnikant Shantilal Shah Engineering College New Sidsar Campu, PO Vartej Bhavnagar 364001 Gujarat INDIA m-Learning Tools and Applications Scientific m-learning @ ICTP , Italy Kiran Trivedi Associate Professor Dept of Electronics & Communication Engineering. S.S.Engineering College, Bhavnagar, Gujarat Technological University Gujarat, India [email protected] Mobile & Wireless Learning • Mobile = Wireless • Wireless ≠ Mobile (not always) • M-learning is always mobile and wireless. • E-learning can be wireless but not mobile Scientific m-learning @ ICTP Italy Smart Phones • Combines PDA and Mobile Connectivity. • Supports Office Applications • WLAN, UMTS, High Resolution Camera • GPS, Accelerometer, Compass • Large Display, High End Processor, Memory and long lasting battery. Scientific m-learning @ ICTP Italy The Revolution .. • Psion Organizer II • 8 bit processor • 9V Battery • OPL – Language • Memory Extensions, plug-ins • Birth of Symbian 1984 2012 Scientific m-learning @ ICTP Italy History of Smartphone • 1994 : IBM Simon • First “Smartphone” • PIM, Data Communication Scientific m-learning @ ICTP Italy Scientific m-learning @ ICTP Italy The First Nokia Smartphones • 2001 : Nokia 7650 • GPRS : HSCSD • Light – Proximity Sensor • Symbian OS ! • Nokia N95 (March 07) • Having almost all features Scientific m-learning @ ICTP Italy S60 and UIQ Scientific m-learning @ ICTP Italy Scientific m-learning @ ICTP Italy Know your target-know your device -

Annual Report 2014 (Year Ended March 31, 2014)
NTT DOCOMO,INC.Annual Report 2014 Annual Report 2014 Year Ended March 31, 2014 NTT DOCOMO, INC. Year Ended March 31,2014 EndedMarch Year Well- Grounded Strategy Printed in Japan Contents Corporate Data Corporate Information As of March 31, 2014 01 Fiscal 2013 Highlights Company Name Fiscal Year-End 02 DOCOMO’s Businesses NTT DOCOMO, INC. March 31 Address Number of Employees (Consolidated) 03 Key Concepts for Understanding DOCOMO Head Offi ce: 24,860 11-1, Nagata-cho 2-chome, Chiyoda-ku, 04 DOCOMO’s Growth Strategy Corporate Website Tokyo 100-6150, Japan https://www.nttdocomo.co.jp/english/ 12 To Our Stakeholders Tel: +81-3-5156-1111 Date of Establishment IR Information DOCOMO will make wide-ranging August 1991 https://www.nttdocomo.co.jp/english/corporate/ir/ use of its latent power and strive Capital Independent Registered Public Accounting Firm to achieve growth and higher ¥949,679,500,000 KPMG AZSA LLC (the Japan member fi rm of KPMG International) corporate value. 18 DOCOMO’s Growth Strategy Initiatives Stock Information Well-Grounded Strategy As of March 31, 2014 20 Number of Subscriptions Stock Listings Number of Shares 25 ARPU Tokyo Stock Exchange, First Section listed October 1998 Total Number of Authorized Shares: 17,460,000,000 30 New Business Areas (Securities code: 9437) Total Number of Issued Shares: 4,365,000,000 36 Management Capital New York Stock Exchange listed March 2002 Number of Shareholders (Ticker symbol: DCM) 42 Management System 327,818 Transfer Agent Distribution of Ownership among Shareholders 52 Review of Financial and Operational Results Mitsubishi UFJ Trust and Banking Corporation, 52 11-Year Summary of Selected Financial Data Corporate Agency Department 4-5, Marunouchi 1-chome, Chiyoda-ku, Tokyo 100-8212, Japan 54 Financial Highlights Tel: +81-3-3212-1211 NTT 63.32% Inquiries about procedures of stock: +81-120-232-711 Foreign Corporations, etc. -

View PDF of Past Speakers
SPEAKERS | 2008-2011 2011 NOV Amsterdam, Netherlands 2008 AUG Berlin, Germany Gianluca Ferremi, VP Sales & Marketing, Motive Television KEYNOTE SPEAKER Antonio Gioia, Project Manager, DTT Content Factory, MediaSet Stefan Jenzowsky, Head of Business Unit Multimedia, Siemens Communications, Media and Technology Tim Hadley, Director, Corporate Communications, Omniphone Telmo Perez Luaces, VP Strategy, Orange - France Telecom Benoit Joly, Senior VP - Operational Marketing, Technicolor Colin Lawrence, Commercial Director, BBC World News SESSION SPEAKERS Cees Links, CEO, GreenPeak Technologies David Noguer Bau, Head of SP Marketing, EMEA, Juniper Networks Simon McGrath, General Manager, Europe, thePlatform, a Comcast Pilgrim Beart, Director and Co-founder, AlertMe subsidiary Jan Van Bogaert, Chief Engineer, Alcatel-Lucent Fernando Coloma Miró, Head of Connected Home Services, Telefónica Klaus Böhm, Director, Technology, Media & Telecommunications, Deloitte Thomas Nogues, Director of Technology, Cable Europe Consulting GmbH R. Uwe Placzek, CEO, Acetrax Paul Bristow, VP Strategy, Middleware & Consumer Experience, Advanced Antti Reijönen, VP Solution Management, F-Secure Digital Broadcast (ADB) Jerome Rota, Sr. VP of Consumer Products and Services, PacketVideo Richard Bullwinkle, Chief Evangelist, Rovi Corporation Toby Russell, Chief Executive Officer, 3Vision Philippe Calvet, Director of Home & Broadband Network Standards, Orange Christopher Schouten, Senior Marketing Director - Online, Irdeto Olivier Carmona, Board of Directors Member, Digital -
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

Attachment Docomo Smart Home Initiative
Attachment docomo Smart Home Initiative dtab™ 10.1-inch tablet running on Android™ 4.1, dedicated to usage with Wi-Fi® at home. Optimized to enjoy videos, animation, shopping and other rich content from dmarket™, simply by entering one’s DOCOMO ID and password with no additional subscription requirement. Accommodates web browsing, and features home screen specially designed to enjoy dmarket portal. Direct access to all dmarket services and daily updates of recommended contents. Compatible with many “docomo cloud™” services, such as the Shabette-Concier™ voice-based personal agent and Photo Collection™ photo sharing. Compatible DOCOMO services: dmarket dmenu™ Shabette-Concier Photo Collection docomo chizu navi™ Smartphone Anshin Enkaku Support™ (Smartphone remote support) Sale: Late March 2013 SmartTV dstick™ Flash drive-like HDMI device enabling movies, animation and music downloaded from dmarket or other online sources such as YouTube™ to be viewed on TVs at no extra cost. Operated by using a DOCOMO smartphone as a remote controller, via a Bluetooth® connection. Compatible services: d video™ (video store with over 7,000 titles and 57,000 items, including Japanese and international movies, dramas, animation, music, karaoke and BeeTV®) d anime store™ (anime store with over 4,000 episodes of 200 popular titles) d hits™ (music store specializing in J-Pop presented via 50 programs) Smart Play by Twonky™ (videos and music saved on PCs and smartphones via home networks can be played back on television screens) Requirements include a television with HDMI and USB ports, broadband network with Wi-Fi connection and DOCOMO smartphone or tablet compatible with the device’s remote control application. -
Technology, Software and Information & Business Services
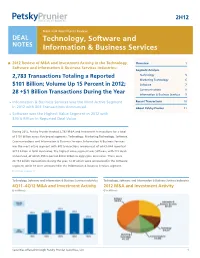
2H12 M&A and Investments Review DEAL Technology, Software and NotES Information & Business Services 2012 Review of M&A and Investment Activity in the Technology, Overview 1 Software and Information & Business Services Industries: Segment Analysis 2,783 Transactions Totaling a Reported Technology 5 Marketing Technology 6 $101 Billion; Volume Up 15 Percent in 2012; Software 7 Communications 8 28 +$1 Billion Transactions During the Year Information & Business Services 9 Information & Business Services was the Most Active Segment Recent Transactions 10 in 2012 with 803 Transactions Announced About Petsky Prunier 11 Software was the Highest Value Segment in 2012 with $40.6 Billion in Reported Deal Value During 2012, Petsky Prunier tracked 2,783 M&A and investment transactions for a total of $101 billion across five broad segments: Technology, Marketing Technology, Software, Communications and Information & Business Services. Information & Business Services was the most active segment with 803 transactions announced, of which 644 reported $27.8 billion in total deal value. The highest value segment was Software with 772 deals announced, of which 494 reported $40.6 billion in aggregate deal value. There were 28 +$1 billion transactions during the year, 12 of which were announced in the Software segment, while 10 were announced in the Information & Business Services segment. [continued on page 2] Technology, Software and Information & Business Services Industries Technology, Software and Information & Business Services Industries 4Q11–4Q12 M&A and Investment Activity 2012 M&A and Investment Activity ($ in Billions) ($ in Millions) Securities offered through Petsky Prunier Securities, LLC 1 Deal Notes Second Half 2012 M&A Activity There were 1,650 mergers and acquisitions announced in 2012, of which One Equity Partners’ $1.1 billion acquisition of M*Modal, a clinical 1,008 reported $86.7 billion in aggregate deal value. -

3GPP/OP#9 Meeting Ottawa, Canada 2 May 2003 3GPP/OP#9(03)
3GPP/OP#9 Meeting 3GPP/OP#9(03)08 Ottawa, Canada 4 April 2003 page 1 of 13 2 May 2003 Source: FFG Chairman Title: Year 2003 Budget and Partner Contributions Agenda item: 6.3 Document for: Decision X Discussion Information 1 Year 2003 Budget 1.1 Support Budget The 2003 MCC support budget was discussed and agreed in principle during OP#8 in St Paul de Vence (see report of OP#8 given in OP#8(02)09). The basis for the 2003 was recorded as below: Budget Line 2003 proposed allocation at OP#8 (kEUR) MCC Staff 1000 Additional support staff 150 MCC Contractors 1963 Travel and subsistence 700 Overheads 1784 Contingency 200 Sub Total 5 797 However, it was agreed to reduce the budget given above by a further 250 kEUR. The precise budget lines where further reductions should be made was left for the discretion of the MCC in consultation with FFG, but the aim was to retain the same service level within 3GPP wherever possible. The precise budget line allocations were derived as given in the following tables by FFG and should now be approved by this OP meeting. page 2 of 13 Budget Line 2003 proposed allocation at FFG#10(kEUR) MCC Staff 970 Additional support staff 150 MCC Contractors 1832 Travel and subsistence 680 Overheads 1706 Contingency 200 Sub Total 5 538 The revised support budget proposal given above is derived at Annex A: 1.2 Specific tasks budget The Partners agreed to the following allocation for the continuation of Task 160 (TTCN).