Transitioning to Ipv6
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement
University of Central Florida STARS Electronic Theses and Dissertations, 2004-2019 2015 Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement Raya Alsharfa University of Central Florida Part of the Electrical and Electronics Commons Find similar works at: https://stars.library.ucf.edu/etd University of Central Florida Libraries http://library.ucf.edu This Masters Thesis (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Electronic Theses and Dissertations, 2004-2019 by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Alsharfa, Raya, "Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement" (2015). Electronic Theses and Dissertations, 2004-2019. 1350. https://stars.library.ucf.edu/etd/1350 PERFORMANCE EVALUATION OF TCP MULTIHOMING FOR IPV6 ANYCAST NETWORKS AND PROXY PLACEMENT by RAYA MAJID ALSHARFA B.S. NAJAF TECHNICAL COLLEGE, 2010 A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering. in the Department of Electrical Engineering and Computer Science in the College of Engineering and Computer Science at the University of Central Florida Orlando, Florida Fall Term 2015 Major Professor: Mostafa Bassiouni © 2015 Raya Majid Alsharfa ii ABSTRACT In this thesis, the impact of multihomed clients and multihomed proxy servers on the performance of modern networks is investigated. The network model used in our investigation integrates three main components: the new one-to-any Anycast communication paradigm that facilitates server replication, the next generation Internet Protocol Version 6 (IPv6) that offers larger address space for packet switched networks, and the emerging multihoming trend of connecting devices and smart phones to more than one Internet service provider thereby acquiring more than one IP address. -

DNS Anycast for High Availability and Performance DNS Anycast Addressing for High Availability and by Timothy Rooney Performance Product Management Director
White Paper DNS Anycast for High Availability and Performance DNS Anycast Addressing for High Availability and by Timothy Rooney Performance Product management director BT Diamond IP By Tim Rooney Director, Product Management BT Diamond IP www.btdiamondip.com DNS Anycast for High Availability and Performance By Tim Rooney, Director, Product Management Introduction We’ve all heard the mantra, “do more with less,” – for some of us to the point of numbness. But when it comes to mission-critical DNS name resolution services, any suggestion of skimping is likely to evoke defiance from those responsible for maintaining its availability and performance. One strategy, however, that can make the deployment of DNS services more efficient is the use of anycast addressing. This white paper shows how DNS servers can be deployed with anycast to achieve a number of benefits, including higher availability and resilience. Defining Anycast The term anycast refers to an IP address assigned to a set of interfaces (usually belonging to different nodes), any one of which can be the intended recipient. Anycast addresses are assigned from the same address space from which unicast addresses have been allocated. Thus, unlike private address space, one cannot visually differentiate a unicast address from an anycast address. An IP packet destined for an anycast address is routed to the nearest interface (according to routing table metrics) configured with the anycast address. The concept is that the sender doesn’t necessarily care which particular host, or in this case DNS server, receives the packet, just as long as one of those sharing the anycast address receives it. -

Towards Passive Analysis of Anycast in Global Routing: Unintended Impact of Remote Peering
Towards Passive Analysis of Anycast in Global Routing: Unintended Impact of Remote Peering Rui Bian Shuai Hao Haining Wang University of Delaware CAIDA / UC San Diego University of Delaware bianrui@udel:edu haos@caida:org hnw@udel:edu Amogh Dhamdere Alberto Dainotti Chase Cotton CAIDA / UC San Diego CAIDA / UC San Diego University of Delaware amogh@caida:org alberto@caida:org ccotton@udel:edu ABSTRACT adoption [8] or the efficiency in particular services like DNS[18]. Anycast has been widely adopted by today’s Internet services, in- Due to the insufficient distinctions between unicast and anycast cluding DNS, CDN, and DDoS protection, in which the same IP from the perspective of a routing table, the common method to address is announced from distributed locations and clients are di- identify anycast addresses is through active Internet-wide measure- rected to the topologically-nearest service replica. Prior research has ments. Cicalese et al. [8, 9] studied the enumeration and city-level focused on various aspects of anycast, either its usage in particular geolocation of anycast prefixes by using latency measurements services such as DNS or characterizing its adoption by Internet- based on the detection of speed-of-light violations. However, the wide active probing methods. In this paper, we first explore an latency of ping may not always reliably reflect the geographic dis- alternative approach to characterize anycast based on previously tance of two IP addresses [4, 34]. Also, active probing requires the collected global BGP routing information. Leveraging state-of-the- use of many vantage points to achieve the necessary coverage. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
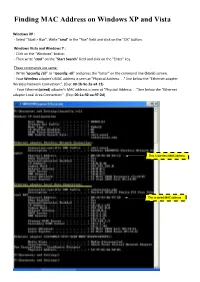
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Crain-Haiti-Anycast-En.Pdf
Anycasting the DNS John Crain Internet Corporation for Assigned Names and Numbers What is Anycast? ‣ “Anycast is a network addressing and routing scheme whereby data is routed to the "nearest" or "best" destination as viewed by the routing topology.” - Wikipedia ‣ unicast - IP address is a unique interface ‣ multicast - Multiple locations at same IP address all receiving packets. ‣ anycast - IP address points to multiple locations but only one visible. Limitations ‣ Because routing information can change! ‣ UDP protocols ‣ Short lived TCP sessions ‣ This sounds a lot like DNS packets :) ‣ Not good for longer TCP sessions ‣ Think of a web session that can last seconds or videostreaming that can last even longer! Why do it? ‣ Adds Capacity ‣ 2 x 100Mb is more than 1 x 100Mb ‣ Localizes trafc ‣ Means closer, hence faster replies ‣ During attacks it also localizes problems ‣ It’s FUN!!!! Is it hard? ‣ Not really but there are some considerations ‣ Managing the anycast instances takes some thought ‣ Need multiple IP address ranges... ‣ More on that..... Implementing Anycast Separate DNS server into it’s own network ‣ Get a dedicated routable /24 of IPv4 space and a range of IPv6 space ‣ Also get a dedicated Autonomous System Number (ASN) ‣ This is necessary for creating a unique routing entity ‣ ICANN L-ROOT (NET6-2001-500-3-1) 2001:0500:0003:0000:0000:0000:0000:0000 - 2001:0500:0003:FFFF:FFFF:FFFF:FFFF:FFFF ‣ ICANN L-ROOT (NET-199-7-83-0-1) 199.7.83.0 - 199.7.83.255 ‣ ASNumber: 20144 A name server ‣ Has an IP address on which it answers DNS queries. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Unicast Forwarding
Unicast Forwarding • Unicast Forwarding, page 1 Unicast Forwarding The Enhanced Forwarding functionality consists of the following: • End Host Registration and Tracking: Leaf switch will intercept the ARP and DHCP packets and learns the IP to MAC binding for the host. In the case of virtualized environments, VDP may be used to track the VM moves. • End Host Route Distribution using BGP: MP-BGP is used within the Vinci fabric to distribute the IP reachability information across the leaf switches in the fabric. Route reflectors will be used for scalability purposes. • ARP and IPv6 ND Proxy: One of the goals of Vinci Enhanced forwarding is to eliminate flooding across the fabric. For this purpose, every leaf switch will act as a ARP/IPv6 ND proxy for all the hosts connected to the leaf switch. • Anycast Default Gateway: Leaf switches act as the default gateway for routing across subnets. All the leafs that handle a given subnet are configured with the same anycast IP address and MAC address. • Forwarding Behavior at Leaf switches: A fabric VLAN is allocated per tenant VRF in the Vinci fabric. BGP advertises the reachability of hosts attached to remote leafs to all the leaf nodes. Ingress leaf switch routes the traffic from the tenant VLAN to the egress leaf switch where the destination host is attached via the fabric VLAN. Egress leaf switch routes the traffic back to the tenant VLAN. This allow the platforms to optimize by scaling the FIB host route table without scaling the MAC address table. • Routing within the subnet: Leaf switch responds with the Anycast Default Gateway MAC to the ARP requests for hosts within the same subnet. -

Attacking the Spanning Tree Protocol
C H A P T E R 3 Attacking the Spanning Tree Protocol Radia Perlman, a distinguished engineer at Sun Microsystems, named as one of the 20 most influential people in the industry in the 25th anniversary issue of Data Communications magazine and the original inventor of the 802.1D spanning-tree specification recently had a few words to say about the protocol: “It’s time to redo (one of the Internet’s most widely used technologies) in a way that is more robust and gives more efficient paths.”1 Introducing Spanning Tree Protocol Chapter 2, “Defeating a Learning Bridge’s Forwarding Process,” explained how Ethernet switches build their forwarding tables by learning source MAC addresses from data traffic. When an Ethernet frame arrives on a switch port in VLAN X with a destination MAC address for which there is no entry in the forwarding table, the switch floods the frame. That is, it sends a copy of the frame to every single port in VLAN X (except the port that originally received the frame). Although this is perfectly fine in a single-switch environment, interesting side effects are observed in multiswitch topologies, as Figure 3-1 shows. The figure represents a simple network composed of two LAN switches interconnected by two Ethernet links. 44 Chapter 3: Attacking the Spanning Tree Protocol Figure 3-1 Basic Network Setup MAC-address 0000.0000.000A 0/1 A B All Interfaces Are Switch 1 in VLAN 5 Link Y Link X Switch 2 0/2 MAC-address 0000.0000.000B In the next steps, MAC addresses are conveniently shortened to a single-letter format for clarity. -

L-Root and Internet in LAC Mauricio Vergara Ereche | Qos Internet CEPAL | Oct 2015 Agenda
L-Root and Internet in LAC Mauricio Vergara Ereche | QoS Internet CEPAL | Oct 2015 Agenda 1 2 3 What is L-Root LAC ICANN? Connectivity 4 5 Our model for Recommend deployment ations | 2 What is ICANN? What is a resilient and secure Internet? Quick Look at ICANN Overview ICANN is a global multi-stakeholder, private sector organization that manages Internet resources for the public benefit. It is best known for its role as technical coordinator of the Internet’s Domain Name System Mission To coordinate, at the overall level, the global Internet’s system of unique identifiers, and in particular to ensure the stable and secure operation of the Internet’s unique identifier system | 4 Supporting A Healthy, Resilient Internet | 5 SSR: Security, Stability and Resiliency Secure 1 Capacity to protect and prevent misuse of Internet Unique identifiers Stable Capacity to ensure that the system operates as expected, 2 and that users of the unique identifiers have confidence that the system operates as expected Resilient Capacity of the unique identifier system to effectively 3 withstand/tolerate/survive malicious attacks and other disruptive events without disruption or cessation of service | 6 L-Root DNS and Anycasting How DNS Works? Root Server 2 www.icann.org ? 1 3 4 8 .ORG Server 5 DNS Resolver (ISP) 6 9 7 www.icann.org ICANN.ORG Server | 8 What is L-Root? “L” is one of 13 independently operated root servers serving the DNS root zone ICANN DNS Engineering team operates L under the Autonomous System Number (ASN) AS20144 using the following -
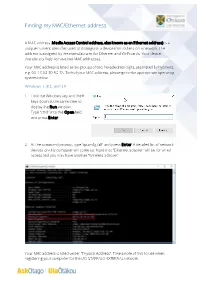
Finding My MAC/Ethernet Address
Finding my MAC/Ethernet address A MAC address (Media Access Control address, also known as an Ethernet address) is a unique numeric identifier used to distinguish a device from others on a network. The address is assigned by the manufacturer for Ethernet and Wi-Fi cards. Your device therefore is likely to have two MAC addresses. Your MAC address is listed as six groups of two hexadecimal digits, separated by hyphens, e.g. 00-13-02-80-92-7A. To find your MAC address, please go to the appropriate operating system below. Windows 7, 8.1, and 10 1. Hold the Windows key and the R keys down at the same time to display the Run window. Type "cmd" into the Open field and press Enter. 2. At the command prompt, type "ipconfig /all" and press Enter. A detailed list of network devices on this computer will come up. Note that "Ethernet adapter" will be for wired access and you may have another "Wireless adapter". Your MAC address is listed under "Physical Address". Take a note of this to use when registering your computer for the UO-STAFF/UO-EXTERNAL network. Mac OS X 1. From the Apple drop-down menu open System Preferences and click on Network. 2. If you want to register for wired access, select Ethernet from the list on the left. 3. Click the Advanced… button and select the Hardware tab to see the MAC address for your Ethernet card. 4. If you need to register for wireless access, click Cancel then select Wi-Fi from the list on the left. -

Introduction to IP Multicast Routing
Introduction to IP Multicast Routing by Chuck Semeria and Tom Maufer Abstract The first part of this paper describes the benefits of multicasting, the Multicast Backbone (MBONE), Class D addressing, and the operation of the Internet Group Management Protocol (IGMP). The second section explores a number of different algorithms that may potentially be employed by multicast routing protocols: - Flooding - Spanning Trees - Reverse Path Broadcasting (RPB) - Truncated Reverse Path Broadcasting (TRPB) - Reverse Path Multicasting (RPM) - Core-Based Trees The third part contains the main body of the paper. It describes how the previous algorithms are implemented in multicast routing protocols available today. - Distance Vector Multicast Routing Protocol (DVMRP) - Multicast OSPF (MOSPF) - Protocol-Independent Multicast (PIM) Introduction There are three fundamental types of IPv4 addresses: unicast, broadcast, and multicast. A unicast address is designed to transmit a packet to a single destination. A broadcast address is used to send a datagram to an entire subnetwork. A multicast address is designed to enable the delivery of datagrams to a set of hosts that have been configured as members of a multicast group in various scattered subnetworks. Multicasting is not connection oriented. A multicast datagram is delivered to destination group members with the same “best-effort” reliability as a standard unicast IP datagram. This means that a multicast datagram is not guaranteed to reach all members of the group, or arrive in the same order relative to the transmission of other packets. The only difference between a multicast IP packet and a unicast IP packet is the presence of a “group address” in the Destination Address field of the IP header.