Design and Implementation of Random Number Generator System Based on Android Smartphone Sensor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
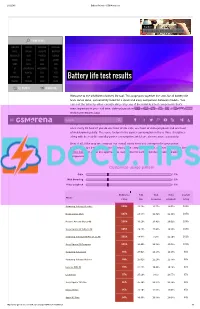
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Response Data 910 14
Count of Type Desc. Total [40 (DUMMY) DISPLAY PHONES] 1 [BLACKBERRY] 2 [CHARGER] 1 [COVERS] 1 [FLIPTOP PHONE] 1 [HC1] 1 [HDCI M8 MOBILE PHONE] 1 [HUAWEI] 1 [I PHONE 4] 2 [I PHONE 5] 2 [I PHONE 5C] 1 [I PHONE 5S] 1 [I PHONE] 1 [IPHONE 5 WHITE IN COLOUR] 1 [IPHONE 5S] 1 [IPHONE 6] 1 [IPHONE CHARGER] 2 [IPHONE CHARGERS] 1 [IPHONE PHONE CHARGER] 1 [IPHONE] 2 [MOBILE PHONE AND CHARGED] 1 [MOBILE PHONE BATTERY] 1 [MOBILE PHONE CASE] 1 [MOBILE PHONE FOR SENIOR] 1 [MOBILE PHONE] 16 [MOBILE TELEPHONE - UNKNOWN DETAILS] 1 [MOBILE TELEPHONE] 4 [MOTOROLA] 1 [NOKIA LUMINA 530 MOBILE PHONE] 1 [NOKIA MOBILE] 1 [PHONE CHARGER] 1 [PHONE SIM CARD] 1 [SAMSUNG GALAXY S3 MINI] 1 [SAMSUNG] 1 [SIM CARD] 2 [SMART PHONE] 1 [SONY XPERIA Z1] 1 [SONY XPERIA Z2] 1 [TABLET] 1 [TELEPHONE CABLE] 1 [TESCO MOBILE PHONE] 1 [TESCO] 1 [UNKNOWN MAKE OF MOBILE PHONE] 1 [WORKS AND PERSONAL] 1 1PHONE 4S 1 3 [3 SIM CARD] 1 3G 1 4 [I PHONE] 1 4S 1 ACCESSORIES [CHARGER AND PHONE COVER] 1 ACER 2 ACER LIQUID 1 ACER LIQUID 3 1 ACER LIQUID 4Z [MOBILE TELEPHONE] 1 ACER LIQUID E 1 ACER LIQUID E2 1 ACER LIQUID E3 1 ACTEL [MOBILE PHONE] 1 ALCATEL 6 ALCATEL [MOBILE PHONE] 3 ALCATEL ITOUCH [ALCATEL ITOUCH] 1 ALCATEL ONE 232 1 ALCATEL ONE TOUCH 6 ALCATEL ONE TOUCH [TRIBE 30GB] 1 ALCATEL ONE TOUCH TRIBE 3040 1 ALCATELL 1 ANDROID [TABLET] 1 APHONE 5 1 APLE IPHONE 5C 1 APLLE I PHONE 5S 2 APLLE IPHONE 4 1 APPL I PHONE 4 1 APPLE 11 APPLE [I PHONE] 1 APPLE [IPHONE] 1 APPLE [MOBILE PHONE CHARGER] 1 APPLE 1 PHONE 4 1 APPLE 1 PHONE 5 1 APPLE 1 PHONE 5 [I PHONE] 1 APPLE 3GS [3GS] 1 APPLE 4 3 APPLE 4 -

Samsung Galaxy FAME (Pearl White) Dein Smartphone, Dein Auftritt
Endgeräte-Produktinformation I Produkte für unterwegs Samsung Galaxy FAME (Pearl White) Dein Smartphone, Dein Auftritt. Basisinformation Artikelnummer| EAN-Code 99920469 |8806085614956 Voraussichtlicher Verkaufsstart 04-2013 Abmessungen und Gewicht 113,0 x 62,0 x 11,6 mm | ca. 121g Farbe Pearl White Stand-by-Zeit | Sprechzeit bis ca. 580 Std. | bis ca. 858 Minuten Akku Li-Ionen, 1300 mAh SAR-Wert Kopf: 0,831 W/kg; Körper: 0,350 W/kg Frequenzbänder GSM Quadband (850, 900, 1800, 1900, MHz) Betriebssystem Android 4.1 Kamera 5.0 Megapixel Display TFT-Displaytechnologie (Fulltouch), 262.144 Farben, 320 x 480 Pixel Prozessor 1 GHz, Typ Broadcom BCM21654 (Daten-) Speicher 4 GB interner Gerätespeicher (ca. 1,67 GB verfügbar); 512 MB SRAM Speichererweiterung (optional) MicroSD, max. 32 GB Navigation: Empfänger und A-GPS, GPS-Empfänger, Glonass, Navigations-Software Navigon Select Telekom Edition Schnittstellen Bluetooth, Micro-USB, USB (Erk. Dtr. am USB-Port), W-LAN, 3,5er Klinke Endgeräte-Display-Abbildung ist symbolisch, der Inhalt Sondereigenschaften Android™ 4.1, WLAN 802.11 b/g/n, kann je nach Software-Version abweichen WiFi Direct, WLAN-/USB-& BT- Tethering, GPS, A-GPS, Glonass, Navigon Select, NFC, S Beam via NFC Tarifempfehlung: und Wi-Fi Direct, Bluetooth® 4.0 & Ideal geeignet für die Vermarktung/Nutzung in den A2DP, 3,5 Klinke, SND & IM, E-Mail, Tarifen Call & Surf Mobil Exchange ActiveSync®, MP3-Player, 5 MP Kamera, Video-Player, Game Hub Highlights Brillanter 8,89 cm Touchscreen mit TouchWiz-Benutzeroberfläche Neueste Android™ 4.1-Plattform Änderungen bzgl. Lieferumfang und Leistungsmerkmalen vorbehalten. Die Angaben zu Betriebszeiten sind als Nennwerte zu verstehen und gelten für neue, nach Herstellervorschriften in Betrieb genommene Akkus bei optimaler Netzversorgung. -

Presentación De Powerpoint
Modelos compatibles de Imóvil No. Marca Modelo Teléfono Versión del sistema operativo 1 360 1501_M02 1501_M02 Android 5.1 2 100+ 100B 100B Android 4.1.2 3 Acer Iconia Tab A500 Android 4.0.3 4 ALPS (Golden Master) MR6012H1C2W1 MR6012H1C2W1 Android 4.2.2 5 ALPS (Golden Master) PMID705GTV PMID705GTV Android 4.2.2 6 Amazon Fire HD 6 Fire HD 6 Fire OS 4.5.2 / Android 4.4.3 7 Amazon Fire Phone 32GB Fire Phone 32GB Fire OS 3.6.8 / Android 4.2.2 8 Amoi A862W A862W Android 4.1.2 9 amzn KFFOWI KFFOWI Android 5.1.1 10 Apple iPad 2 (2nd generation) MC979ZP iOS 7.1 11 Apple iPad 4 MD513ZP/A iOS 7.1 12 Apple iPad 4 MD513ZP/A iOS 8.0 13 Apple iPad Air MD785ZP/A iOS 7.1 14 Apple iPad Air 2 MGLW2J/A iOS 8.1 15 Apple iPad Mini MD531ZP iOS 7.1 16 Apple iPad Mini 2 FE276ZP/A iOS 8.1 17 Apple iPad Mini 3 MGNV2J/A iOS 8.1 18 Apple iPhone 3Gs MC132ZP iOS 6.1.3 19 Apple iPhone 4 MC676LL iOS 7.1.2 20 Apple iPhone 4 MC603ZP iOS 7.1.2 21 Apple iPhone 4 MC604ZP iOS 5.1.1 22 Apple iPhone 4s MD245ZP iOS 8.1 23 Apple iPhone 4s MD245ZP iOS 8.4.1 24 Apple iPhone 4s MD245ZP iOS 6.1.2 25 Apple iPhone 5 MD297ZP iOS 6.0 26 Apple iPhone 5 MD298ZP/A iOS 8.1 27 Apple iPhone 5 MD298ZP/A iOS 7.1.1 28 Apple iPhone 5c MF321ZP/A iOS 7.1.2 29 Apple iPhone 5c MF321ZP/A iOS 8.1 30 Apple iPhone 5s MF353ZP/A iOS 8.0 31 Apple iPhone 5s MF353ZP/A iOS 8.4.1 32 Apple iPhone 5s MF352ZP/A iOS 7.1.1 33 Apple iPhone 6 MG492ZP/A iOS 8.1 34 Apple iPhone 6 MG492ZP/A iOS 9.1 35 Apple iPhone 6 Plus MGA92ZP/A iOS 9.0 36 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.0.2 37 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.1 -

"220 ვოლტს"-ის (206344945) კუთვნილი მოძრავი ქონება (ტექნიკა, აქსესუარები)
შპს "220 ვოლტს"-ის (206344945) კუთვნილი მოძრავი ქონება (ტექნიკა, აქსესუარები) დანართი #1 დასახელება რაოდენობა მზომი ერთეული შენიშვნა მუშა მდგომარეობა Micromax Q 50 20 ც დაუდგენელია 1 მუშა მდგომარეობა Micromax M 2 Carbon Graphite 9 ც დაუდგენელია 2 EA-CC9U21B Camera Case 100 ც 3 კვების ელემენტი li-an goletiani მუშა მდგომარეობა 179 ც energ i8910 დაუდგენელია 4 მუშა მდგომარეობა samsung ch@tt s357 duos silver 120 ც დაუდგენელია 5 for optimua G pro ქეისი LG 73 ც mobile(voia) 6 samsung galaxy s4 ქეისი EF- 17 ც PI950BCEGWW 7 samsung galaxy s4 flip done etui aver 12 ც rabat EF-FI950BYEGWW 8 samsung grand protect cover+ EF- 8 ც PI908BWEGRU 9 Galaxy S5 Protective Cover Gray EF- 3 ც PG900BSEGRU 10 samsung galaxy s5 pink metalic EF- 4 ც CG900BFEGRU 11 samsung galaxy s4 protective cover+ ef- 6 ც pi95bnegww 12 samsung EF-FI950BBEGRU S4 Flip 2 ც cover 13 samsung galaxy s4EF-FI950BBEGWW 11 ც 14 samsung galaxy grand ek-fi908blegru 4 ც 15 samsung galaxy s3 pouch efc- 3 ც 1g6ldecsdt 16 samsung galaxy note 2 flip cover efc- 4 ც 1j9wegstd 17 samsung galaxy note 2 flip cover EFC- 6 ც 1J9FWEGSTD 18 samsung galaxy note 3 s view cover EF- 4 ც CN900BBEGRU 19 მუშა მდგომარეობა samsung galaxy note gt-n8000 white 2 ც დაუდგენელია 20 მუშა მდგომარეობა samsung galaxy tab3 255.8 მმ gt-p5200 2 ც დაუდგენელია 21 მუშა მდგომარეობა samsung galaxy tab4 203.1 მმ sm-t331 2 ც დაუდგენელია 22 მუშა მდგომარეობა micromax mx 360 35 ც დაუდგენელია 23 მუშა მდგომარეობა samsung galaxy tab 3 sm-311 3 ც დაუდგენელია 24 მუშა მდგომარეობა samsung საათები smart watch v-7000 18 ც დაუდგენელია 25 მუშა -

Note to Editors: Samsung GALAXY Young Product Specifications
Note to Editors: Samsung GALAXY Young Product Specifications HSPA 7.2/5.76 900/2100 Network EDGE/GPRS 850/900/1800/1900 Processor 1 GHz processor Display 3.27” HVGA TFT OS Android 4.1 (Jelly Bean) Camera Main(Rear): 3-megapixel camera Codec: MPEG4, H.263, H.264 Video Playback: WVGA@30fps Record: VGA@24fps Codec: MP3, Vorbis(OGG), AAC, AAC+,eAAC+, AMR(NB,WB), I-Melody, MIDI, Audio WMA Music Player with SoundAlive 3.5mm Ear Jack Samsung Apps Samsung Kies Samsung TouchWiz Motion UI: Smart Alert, Shake to update, Turn over to mute Samsung Hub Content Features * - Game Hub Lite & Services Samsung ChatON mobile communication service Samsung S Cloud / Dropbox Google Search, Google Maps, Gmail, Google Latitude Google Play Store, Google Play Books, Google Play Movies Google Plus, YouTube, Google Talk, Google Places, Google Navigation, Google Downloads GPS A-GPS Bluetooth® v 3.0 USB 2.0 Connectivity Wi-Fi 802.11 b/g/n, Wi-Fi Direct NFC(optional) Sensor Accelerometer, Digital Compass, Proximity 4GB Storage + 768MB (RAM) Memory microSD (up to 64GB) Dimension 58.6 x 109.4 x 12.5 mm, 112 g Battery Standard battery, Li-ion 1,300mAh * The availability of each Samsung Hub and Google service may differ by country. * All functionality, features, specifications and other product information provided in this document including, but not limited to, the benefits, design, pricing, components, performance, availability, and capabilities of the product are subject to change without notice or obligation. * Android, Google, Android Beam, Google Search, Google Maps, Gmail, Google Latitude, Google Play Store, Google Play Books, Google Play Movies, Google Plus, YouTube, Google Talk, Google Places, Google Navigation, and Google Downloads are trademarks of Google Inc. -

Manual Samsung Galaxy Ace Duos Gt S6802b Price in India 2012
Manual Samsung Galaxy Ace Duos Gt S6802b Price In India 2012 Samsung S6802 (5 Jul 2015) - Samsung S6802 price in India now at Rs 8197. Phone comes with Charger + Headphones. its a 2012 Model. Samsung Galaxy Ace Duos S6802 Vs Samsung Galaxy S Duos S7562 · Samsung S6802 Vs. Junglee.com: Buy Samsung Galaxy Ace Duos S6802 Battery at Lowest Price from online sellers within India. Read Samsung If you have a Samsung Galaxy Ace Duos S6802, we have good news for you. The good news is Follow us. Conditions of Use & Sale · Privacy Notice, © 2012-2015 Junglee.com or its affiliates. ». Always On with GALAXY Ace DUOS You always go 100% - whether you're at work or at play. That's why you'll settle for nothing less than Samsung's GALAXY. Minimum Order is 3 Phones To Qualify For These Trade Prices G808, G810, Galaxy Ace 3 Duos - GT-S7272C, Galaxy Ace 3 LTE - GT-S7275B, Galaxy Ace 3. Compare Samsung Galaxy Ace S5830I Prices in India and Buy online across Box Contents, Handset, Battery, Charger, Earphone, USB Cable, User Manual, Warranty Card. Also Known As, Samsung Galaxy Ace GT-S5830i Samsung Galaxy Ace Duos S6802 Price: Rs. 6,999. 47 Like · Reply · Oct 31, 2012 12:44am. View Delivery Options & Pricing. Ask us something. Questions about this item? Email us. Why Mobile Fun? Unbeatable Range & Choice, Order By 6pm For. Manual Samsung Galaxy Ace Duos Gt S6802b Price In India 2012 >>>CLICK HERE<<< We now have 374 ads from 15 sites for samsung galaxy s duos price black, Released 2012, September BODY Dimensions 121.5 x. -

Konig Size S Konig Size M Konig Size M-Large Konig Size L
Konig Size S Konig Size M Konig Size M-Large Konig Size L Konig Size XL Konig Size XXL Konig Size XXXL HTC Desire C Apple iPhone 4S Apple iPhone 5S Samsung I9195 Galaxy S4 mini Samsung Galaxy S5 mini (SM-G800F) Apple iPhone 6 Samsung Galaxy S5 (SM-900F) HTC Explorer Apple iPhone 4 Apple iPhone 5C Samsung I8190 Galaxy SIII mini Samsung Galaxy Ace 4 (SM-G357) Samsung I9500/I9505 Galaxy S4 Samsung Galaxy S5 Plus (SM-G901F) HTC Wildfire Apple iPhone Touch 3G Apple iPhone 5 Samsung S7580 Galaxy Trend Plus Samsung I9105 Galaxy SII Plus Samsung I9300I Galaxy SIII Neo Samsung Galaxy S4 Active I9295 HTC Wildfire S Apple iPhone 3GS Nokia Asha 300 Samsung S7562 Galaxy S Duos Samsung I9100 Galaxy SII Samsung I9300 Galaxy SIII Samsung Galaxy S4 Zoom (SM-C101) LG Optimus L3 E400 Apple iPhone 3GS Samsung S7560 Galaxy Trend Samsung I8260 Galaxy Core Samsung I9250 Galaxy Nexus Samsung Galaxy Xcover 2 S7710 Nokia 3110 Classic Apple iPod Touc h3G Samsung S7500 Galaxy Ace Plus Samsung S7390 Galaxy Trend Lite Samsung Galaxy Core II (SM-G355H) Sony Xperia M2 Nokia 3109 Classic BlackBerry 9320 Curve Samsung S7270 Galaxy Ace 3 Sony Xperia Z3 Compact Sony Xperia ZR Sony Xperia Z Nokia 6230(i) BlackBerry 9360 Curve Samsung I9070 Galaxy S Advance Sony Xperia Z1 Compact Sony Xperia T Nokia Lumia 920 Nokia C2-02 BlackBerry 9790 Bold Samsung I9023 Nexus S Sony Xperia SP Sony Xperia S Nokia Lumia 625 Nokia C2-03 Google Nexus One Samsung I9003 Galaxy SL Sony Xperia E Nokia Lumia 900 Motorola Moto G2nd Gen. -

A Maneira Mais Prática E Simples De Você Receber Pagamentos Com Cartões De Débito E Crédito Usando Seu Smartphone Ou Tablet
A maneira mais prática e simples de você receber pagamentos com cartões de débito e crédito usando seu smartphone ou tablet. Confira os equipamentos compatíveis. Página | 1 Atenção: A compatibilidade de um equipamento com o Vero Mobile não garante que sua versão Dual Chip do celular seja igualmente compatível. Havendo compatibilidade, o aparelho estará listado com essa informação. Marca Modelo Versão Status Apple iPad iOS 7.1 COMPATÍVEL Apple iPhone 4 iOS 7.1 COMPATÍVEL Apple iPhone 4s iOS 7.1 COMPATÍVEL Apple iPhone 5 iOS 7.1 COMPATÍVEL Apple iPhone 5c iOS 7.1 COMPATÍVEL Apple iPhone 5s iOS 7.1 COMPATÍVEL Apple iPhone 6 iOS 7.1 COMPATÍVEL Apple iPhone 6 iOS 7.1 COMPATÍVEL Apple iPod Touch iOS COMPATÍVEL LG LG E465F Android NÃO COMPATÍVEL LG LG E977 Android 4.4 COMPATÍVEL LG LG G PRO LITE D685 Android 4.2.2 NÃO COMPATÍVEL LG LG G2 Android COMPATÍVEL LG LG G2 Mini D618 Android 4.4.2 NÃO COMPATÍVEL LG LG G3 LG D855P Android 4.4.2 COMPATÍVEL LG LG G3 Stylus D690 Android NÃO COMPATÍVEL LG LG G3 Stylus D690 Dual Chip Android 4.4.2 NÃO COMPATÍVEL LG LG L1 E410F Android 4.2 COMPATÍVEL LG LG L40 Dual Android 4.4.2 COMPATÍVEL LG LG L40 DualTV Android NÃO COMPATÍVEL LG LG L7 P716 Android COMPATÍVEL LG LG L70 Android 4.4 COMPATÍVEL LG LG L70 dual chip Android COMPATÍVEL LG LG L80 Android COMPATÍVEL LG LG L90 Dual Android NÃO COMPATÍVEL LG LG LEON Dual H342f Android NÃO COMPATÍVEL LG LG MyTouch Q Android 2.3.6 COMPATÍVEL LG LG Nexus 4 E960 Android 4.4 NÃO COMPATÍVEL LG LG Nexus 5 Android 4.4 NÃO COMPATÍVEL LG LG Optimus G Android 4.0.4 COMPATÍVEL -

Manual De Usuario
GT-S6810P Manual de usuario www.samsung.com Acerca de este manual El dispositivo ofrece funciones de comunicación y entretenimiento de alta calidad sobre los altos estándares y la experiencia tecnológica de Samsung. Este manual del usuario está diseñado específicamente para describir en detalle las funciones del dispositivo. • Lea este manual antes de usar el dispositivo a fin de garantizar el uso correcto y seguro. • Las descripciones se basa en los ajustes predeterminados del dispositivo. • Es posible que las imágenes y las capturas de pantalla no sean exactamente iguales al producto real. • El contenido puede diferir del producto final o del software proporcionado por los proveedores de servicios o transmisores, y se encuentra sujeto a cambio sin previo aviso. Para acceder a la última versión del manual, consulte el sitio Web de Samsung, www.samsung.com. • El contenido (contenido de alta calidad) que exija un alto uso del CPU y la memoria RAM afectará el rendimiento general del dispositivo. Las aplicaciones relacionadas con el contenido podrían no funcionar correctamente, según las especificaciones del dispositivo y el entorno en el cual lo use. • Las funciones disponibles y los servicios adicionales pueden variar según el dispositivo, el software o el proveedor de servicios. • Las aplicaciones y sus funciones pueden variar según el país, la región o las especificaciones de hardware. Samsung no se hace responsable por los problemas de rendimiento provocados por aplicaciones de cualquier proveedor aparte de Samsung. • Samsung no se hace responsable por los problemas de rendimiento o las incompatibilidades provocados por la edición de los ajustes de registro o la alteración del software del sistema operativo. -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -

ETUI W Kolorze Czarnym ALCATEL A3
ETUI w kolorze czarnym ALCATEL A3 5.0'' CZARNY ALCATEL PIXI 4 4.0'' 4034A CZARNY ALCATEL PIXI 4 5.0'' 5045X CZARNY ALCATEL POP C3 4033A CZARNY ALCATEL POP C5 5036A CZARNY ALCATEL POP C7 7041X CZARNY ALCATEL POP C9 7047D CZARNY ALCATEL U5 5044D 5044Y CZARNY HTC 10 CZARNY HTC DESIRE 310 CZARNY HTC DESIRE 500 CZARNY HTC DESIRE 516 CZARNY HTC DESIRE 610 CZARNY HTC DESIRE 616 CZARNY HTC DESIRE 626 CZARNY HTC DESIRE 650 CZARNY HTC DESIRE 816 CZARNY HTC ONE A9 CZARNY HTC ONE A9s CZARNY HTC ONE M9 CZARNY HTC U11 CZARNY HUAWEI ASCEND G510 CZARNY HUAWEI ASCEND Y530 CZARNY HUAWEI ASCEND Y600 CZARNY HUAWEI G8 GX8 CZARNY HUAWEI HONOR 4C CZARNY HUAWEI HONOR 6X CZARNY HUAWEI HONOR 7 LITE 5C CZARNY HUAWEI HONOR 8 CZARNY HUAWEI HONOR 9 CZARNY HUAWEI MATE 10 CZARNY HUAWEI MATE 10 LITE CZARNY HUAWEI MATE 10 PRO CZARNY HUAWEI MATE S CZARNY HUAWEI P10 CZARNY HUAWEI P10 LITE CZARNY HUAWEI P10 PLUS CZARNY HUAWEI P8 CZARNY HUAWEI P8 LITE 2017 CZARNY HUAWEI P8 LITE CZARNY HUAWEI P9 CZARNY HUAWEI P9 LITE CZARNY HUAWEI P9 LITE MINI CZARNY HUAWEI Y3 2017 CZARNY HUAWEI Y3 II CZARNY HUAWEI Y5 2017 Y6 2017 CZARNY HUAWEI Y5 Y560 CZARNY HUAWEI Y520 Y540 CZARNY HUAWEI Y541 CZARNY HUAWEI Y6 II CZARNY HUAWEI Y625 CZARNY HUAWEI Y7 CZARNY iPHONE 5C CZARNY iPHONE 5G CZARNY iPHONE 6 4.7'' CZARNY iPHONE 7 4.7'' 8 4.7'' CZARNY iPHONE 7 PLUS 5.5'' 8 PLUS CZARNY iPHONE X A1865 A1901 CZARNY LENOVO K6 NOTE CZARNY LENOVO MOTO C CZARNY LENOVO MOTO C PLUS CZARNY LENOVO MOTO E4 CZARNY LENOVO MOTO E4 PLUS CZARNY LENOVO MOTO G4 XT1622 CZARNY LENOVO VIBE C2 CZARNY LENOVO VIBE K5 CZARNY