Detection of Malicious Android Applications: Classical Machine Learning Vs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Machine Learning Or Econometrics for Credit Scoring: Let’S Get the Best of Both Worlds Elena Dumitrescu, Sullivan Hué, Christophe Hurlin, Sessi Tokpavi
Machine Learning or Econometrics for Credit Scoring: Let’s Get the Best of Both Worlds Elena Dumitrescu, Sullivan Hué, Christophe Hurlin, Sessi Tokpavi To cite this version: Elena Dumitrescu, Sullivan Hué, Christophe Hurlin, Sessi Tokpavi. Machine Learning or Econometrics for Credit Scoring: Let’s Get the Best of Both Worlds. 2020. hal-02507499v2 HAL Id: hal-02507499 https://hal.archives-ouvertes.fr/hal-02507499v2 Preprint submitted on 2 Nov 2020 (v2), last revised 15 Jan 2021 (v3) HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Machine Learning or Econometrics for Credit Scoring: Let's Get the Best of Both Worlds∗ Elena, Dumitrescu,y Sullivan, Hu´e,z Christophe, Hurlin,x Sessi, Tokpavi{ October 18, 2020 Abstract In the context of credit scoring, ensemble methods based on decision trees, such as the random forest method, provide better classification performance than standard logistic regression models. However, logistic regression remains the benchmark in the credit risk industry mainly because the lack of interpretability of ensemble methods is incompatible with the requirements of financial regulators. In this paper, we pro- pose to obtain the best of both worlds by introducing a high-performance and inter- pretable credit scoring method called penalised logistic tree regression (PLTR), which uses information from decision trees to improve the performance of logistic regression. -

Testing Anti-Virus in Linux: How Effective Are the Solutions Available for Desktop Computers?
Royal Holloway University of London ISG MSc Information Security thesis series 2021 Testing anti-virus in Linux: How effective are the solutions available for desktop computers? Authors Giuseppe Raffa, MSc (Royal Holloway, 2020) Daniele Sgandurra, Huawei, Munich Research Center. (Formerly ISG, Royal Holloway.) Abstract Anti-virus (AV) programs are widely recognized as one of the most important defensive tools available for desktop computers. Regardless of this, several Linux users consider AVs unnec- essary, arguing that this operating system (OS) is “malware-free”. While Windows platforms are undoubtedly more affected by malicious software, there exist documented cases of Linux- specific malware. In addition, even though the estimated market share of Linux desktop sys- tems is currently only at 2%, it is certainly possible that it will increase in the near future. Considering all this, and the lack of up-to-date information about Linux-compatible AV solutions, we evaluated the effectiveness of some anti-virus products by using local installations, a well- known on-line malware scanning service (VirusTotal) and a renowned penetration testing tool (Metasploit). Interestingly, in our tests, the average detection rate of the locally-installed AV programs was always above 80%. However, when we extended our analysis to the wider set of anti-virus solutions available on VirusTotal, we found out that the average detection rate barely reached 60%. Finally, when evaluating malicious files created with Metasploit, we verified that the AVs’ heuristic detection mechanisms performed very poorly, with detection rates as low as 8.3%.a aThis article is published online by Computer Weekly as part of the 2021 Royal Holloway informa- tion security thesis series https://www.computerweekly.com/ehandbook/Royal-Holloway-Testing-antivirus- efficacy-in-Linux. -

13Th International Conference on Cyber Conflict: Going Viral 2021
2021 13th International Conference on Cyber Confict: Going Viral T. Jančárková, L. Lindström, G. Visky, P. Zotz (Eds.) 2021 13TH INTERNATIONAL CONFERENCE ON CYBER CONFLICT: GOING VIRAL Copyright © 2021 by NATO CCDCOE Publications. All rights reserved. IEEE Catalog Number: CFP2126N-PRT ISBN (print): 978-9916-9565-4-0 ISBN (pdf): 978-9916-9565-5-7 COPYRIGHT AND REPRINT PERMISSIONS No part of this publication may be reprinted, reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of the NATO Cooperative Cyber Defence Centre of Excellence ([email protected]). This restriction does not apply to making digital or hard copies of this publication for internal use within NATO, or for personal or educational use when for non-proft or non-commercial purposes, providing that copies bear this notice and a full citation on the frst page as follows: [Article author(s)], [full article title] 2021 13th International Conference on Cyber Confict: Going Viral T. Jančárková, L. Lindström, G. Visky, P. Zotz (Eds.) 2021 © NATO CCDCOE Publications NATO CCDCOE Publications LEGAL NOTICE: This publication contains the opinions of the respective authors only. They do not Filtri tee 12, 10132 Tallinn, Estonia necessarily refect the policy or the opinion of NATO Phone: +372 717 6800 CCDCOE, NATO, or any agency or any government. NATO CCDCOE may not be held responsible for Fax: +372 717 6308 any loss or harm arising from the use of information E-mail: [email protected] contained in this book and is not responsible for the Web: www.ccdcoe.org content of the external sources, including external websites referenced in this publication. -

Reinforcement Learning in Supervised Problem Domains
Technische Universität München Fakultät für Informatik Lehrstuhl VI – Echtzeitsysteme und Robotik reinforcement learning in supervised problem domains Thomas F. Rückstieß Vollständiger Abdruck der von der Fakultät für Informatik der Technischen Universität München zur Erlangung des akademischen Grades eines Doktors der Naturwissenschaften (Dr. rer. nat.) genehmigten Dissertation. Vorsitzender: Univ.-Prof. Dr. Daniel Cremers Prüfer der Dissertation 1. Univ.-Prof. Dr. Patrick van der Smagt 2. Univ.-Prof. Dr. Hans Jürgen Schmidhuber Die Dissertation wurde am 30. 06. 2015 bei der Technischen Universität München eingereicht und durch die Fakultät für Informatik am 18. 09. 2015 angenommen. Thomas Rückstieß: Reinforcement Learning in Supervised Problem Domains © 2015 email: [email protected] ABSTRACT Despite continuous advances in computing technology, today’s brute for- ce data processing approaches may not provide the necessary advantage to win the race against the ever-growing amount of data that can be wit- nessed over the last decades. In this thesis, we discuss novel methods and algorithms that are capable of directing attention to relevant details and analysing it in sequence to overcome the processing bottleneck and to keep up with this data explosion. In the first of three parts, a novel exploration technique for Policy Gradi- ent Reinforcement Learning is presented which replaces traditional ad- ditive random exploration with state-dependent exploration, exploring on a higher, more strategic level. We will show how this new exploration method converges faster and finds better global solutions than random exploration can. The second part of this thesis will introduce the concept of “data con- sumption” and discuss means to minimise it in supervised learning tasks by deriving classification as a sequential decision process and ma- king it accessible to Reinforcement Learning methods. -

Page 1 of 3 Virustotal
VirusTotal - Free Online Virus, Malware and URL Scanner Page 1 of 3 VT Community Sign in ▼ Languages ▼ Virustotal is a service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware detected by antivirus engines. More information... 0 VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is goodware. 0 VT Community VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is malware. File name: wsusoffline71.zip Submission date: 2011-11-01 08:16:44 (UTC) Current status: finished not reviewed Result: 0 /40 (0.0%) Safety score: - Compact Print results Antivirus Version Last Update Result AhnLab-V3 2011.10.31.00 2011.10.31 - AntiVir 7.11.16.225 2011.10.31 - Antiy-AVL 2.0.3.7 2011.11.01 - Avast 6.0.1289.0 2011.11.01 - AVG 10.0.0.1190 2011.11.01 - BitDefender 7.2 2011.11.01 - CAT-QuickHeal 11.00 2011.11.01 - ClamAV 0.97.3.0 2011.11.01 - Commtouch 5.3.2.6 2011.11.01 - Comodo 10625 2011.11.01 - Emsisoft 5.1.0.11 2011.11.01 - eSafe 7.0.17.0 2011.10.30 - eTrust-Vet 36.1.8650 2011.11.01 - F-Prot 4.6.5.141 2011.11.01 - F-Secure 9.0.16440.0 2011.11.01 - Fortinet 4.3.370.0 2011.11.01 - GData 22 2011.11.01 - Ikarus T3.1.1.107.0 2011.11.01 - Jiangmin 13.0.900 2011.10.31 - K7AntiVirus 9.116.5364 2011.10.31 - Kaspersky 9.0.0.837 2011.11.01 - McAfee 5.400.0.1158 2011.11.01 - McAfee-GW-Edition 2010.1D 2011.10.31 - Microsoft 1.7801 2011.11.01 - NOD32 6591 2011.11.01 - Norman 6.07.13 2011.10.31 - nProtect 2011-10-31.01 2011.10.31 - http://www.virustotal.com/file -scan/report.html?id=874d6968eaf6eeade19179712d53 .. -
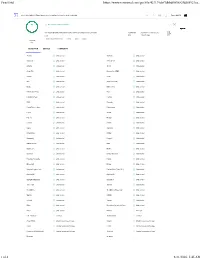
Virustotal Scan on 2020.08.21 for Pbidesktopsetup 2
VirusTotal https://www.virustotal.com/gui/file/423139def3dbbdf0f5682fdd88921ea... 423139def3dbbdf0f5682fdd88921eaface84ff48ef2e2a8d20e4341ca4a4364 Patch My PC No engines detected this file 423139def3dbbdf0f5682fdd88921eaface84ff48ef2e2a8d20e4341ca4a4364 269.49 MB 2020-08-21 11:39:09 UTC setup Size 1 minute ago invalid-rich-pe-linker-version overlay peexe signed Community Score DETECTION DETAILS COMMUNITY Acronis Undetected Ad-Aware Undetected AegisLab Undetected AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antiy-AVL Undetected SecureAge APEX Undetected Arcabit Undetected Avast Undetected AVG Undetected Avira (no cloud) Undetected Baidu Undetected BitDefender Undetected BitDefenderTheta Undetected Bkav Undetected CAT-QuickHeal Undetected ClamAV Undetected CMC Undetected Comodo Undetected CrowdStrike Falcon Undetected Cybereason Undetected Cyren Undetected eScan Undetected F-Secure Undetected FireEye Undetected Fortinet Undetected GData Undetected Ikarus Undetected Jiangmin Undetected K7AntiVirus Undetected K7GW Undetected Kaspersky Undetected Kingsoft Undetected Malwarebytes Undetected MAX Undetected MaxSecure Undetected McAfee Undetected Microsoft Undetected NANO-Antivirus Undetected Palo Alto Networks Undetected Panda Undetected Qihoo-360 Undetected Rising Undetected Sangfor Engine Zero Undetected SentinelOne (Static ML) Undetected Sophos AV Undetected Sophos ML Undetected SUPERAntiSpyware Undetected Symantec Undetected TACHYON Undetected Tencent Undetected TrendMicro Undetected TrendMicro-HouseCall Undetected VBA32 Undetected -

An Analysis of Domain Classification Services
Mis-shapes, Mistakes, Misfits: An Analysis of Domain Classification Services Pelayo Vallina Victor Le Pochat Álvaro Feal IMDEA Networks Institute / imec-DistriNet, KU Leuven IMDEA Networks Institute / Universidad Carlos III de Madrid Universidad Carlos III de Madrid Marius Paraschiv Julien Gamba Tim Burke IMDEA Networks Institute IMDEA Networks Institute / imec-DistriNet, KU Leuven Universidad Carlos III de Madrid Oliver Hohlfeld Juan Tapiador Narseo Vallina-Rodriguez Brandenburg University of Universidad Carlos III de Madrid IMDEA Networks Institute/ICSI Technology ABSTRACT ACM Reference Format: Domain classification services have applications in multiple areas, Pelayo Vallina, Victor Le Pochat, Álvaro Feal, Marius Paraschiv, Julien including cybersecurity, content blocking, and targeted advertising. Gamba, Tim Burke, Oliver Hohlfeld, Juan Tapiador, and Narseo Vallina- Rodriguez. 2020. Mis-shapes, Mistakes, Misfits: An Analysis of Domain Yet, these services are often a black box in terms of their method- Classification Services. In ACM Internet Measurement Conference (IMC ’20), ology to classifying domains, which makes it difficult to assess October 27ś29, 2020, Virtual Event, USA. ACM, New York, NY, USA, 21 pages. their strengths, aptness for specific applications, and limitations. In https://doi.org/10.1145/3419394.3423660 this work, we perform a large-scale analysis of 13 popular domain classification services on more than 4.4M hostnames. Our study empirically explores their methodologies, scalability limitations, 1 INTRODUCTION label constellations, and their suitability to academic research as The need to classify websites became apparent in the early days well as other practical applications such as content filtering. We of the Web. The first generation of domain classification services find that the coverage varies enormously across providers, ranging appeared in the late 1990s in the form of web directories. -

Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10
Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10 January 2020 Document: Consumer Security Products Performance Benchmarks (Edition 2) Authors: J. Han, D. Wren Company: PassMark Software Date: 13 January 2020 Edition: 2 File: Consumer_Security_Products_Performance_Benchmarks_2020_Ed_2.docx Consumer Security Performance Benchmarks 2019 PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 REVISION HISTORY ............................................................................................................................................ 3 REFERENCES ...................................................................................................................................................... 3 EXECUTIVE SUMMARY ...................................................................................................................................... 4 OVERALL SCORE ................................................................................................................................................ 5 PRODUCTS AND VERSIONS ............................................................................................................................... 6 PERFORMANCE METRICS SUMMARY ................................................................................................................ 7 TEST RESULTS ................................................................................................................................................ -

Acer Lanscope Agent 2.2.25.84 Acer Lanscope Agent 2.2.25.84 X64
Acer LANScope Agent 2.2.25.84 Acer LANScope Agent 2.2.25.84 x64 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus 2.8.0.2237 AEC TrustPort Personal Firewall 4.0.0.1305 AhnLab SpyZero 2007 and SmartUpdate AhnLab V3 Internet Security 7.0 Platinum Enterprise AhnLab V3 Internet Security 7.0 Platinum Enterprise x64 ArcaVir Antivir/Internet Security 09.03.3201.9 Ashampoo AntiSpyware 2 v 2.05 Ashampoo AntiVirus AtGuard 3.2 Authentium Command Anti-Malware v 5.0.5 AVG Identity Protection 8.5 BitDefender Antivirus 2008 BitDefender Antivirus Plus 10.247 BitDefender Client Professional Plus 8.0.2 BitDefender Antivirus Plus 10 BitDefender Standard Edition 7.2 (Fr) Bit Defender Professional Edition 7.2 (Fr) BitDefender 8 Professional Plus BitDefender 8 Professional (Fr) BitDefender 8 Standard BitDefender 8 Standard (Fr) BitDefender 9 Professional Plus BitDefender 9 Standard BitDefender for FileServers 2.1.11 BitDefender Free Edition 2009 12.0.12.0 BitDefender Antivirus 2009 12.0.10 BitDefender 2009 12.0.11.5 BitDefender Internet Security 2008 BitDefender Internet Security 2009 12.0.8 BitDefender 2009 Internet Security 12.0.11.5 BitDefender Internet Security v10.108 BitDefender Total Security 2008 BitDefender 2009 Total Security 12.0.11.5 CA AntiVirus 2008 CA Anti-Virus r8.1 / CA eTrustITM Agent r8.1 CA eTrustITM 8.1 CA eTrustITM 8.1.00 CA eTrustITM Agent 8.0.403 CA eTrust Pestpatrol 5.0 CA HIPS Managed Client 1.0 CA eTrust Antivirus 7.1.0194 CA PC Security Suite 6.0 \ Private PC Security Suite 6.0 CA PC Security Suite 6.0.00 Cipafilter Client Tools -

Acer Lanscope Agent 2.2.25.84 Acer Lanscope Agent 2.2.25.84
Acer LANScope Agent 2.2.25.84 Acer LANScope Agent 2.2.25.84 x64 Ad-Aware 9.6.0 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus 2.8.0.2237 AEC TrustPort Personal Firewall 4.0.0.1305 AhnLab V3 Internet Security 8.0 AhnLab V3 Internet Security 8.0 x64 AhnLab SpyZero 2007 and SmartUpdate AhnLab V3 Internet Security 7.0 Platinum Enterprise AhnLab V3 Internet Security 7.0 Platinum Enterprise x64 Aluria Security Center Alyac Antivirus Alyac Antivirus x64 ALYac 2.1 Avira AntiVir PersonalEdition Classic 7 - 8 Avira AntiVir Personal - Free Antivirus 360 Anti Virus ArcaVir Antivir/Internet Security 09.03.3201.9 ArcaVir Antivir/Internet Security 09.03.3201.9 x64 Ashampoo AntiSpyware 2 v 2.05 Ashampoo AntiVirus Ashampoo Anti-Malware 1.11 Ashampoo Firewall 1.20 Ashampoo FireWall PRO 1.14 AtGuard 3.2 Authentium Command Anti-Malware v 5.0.5 Authentium Command Anti-Malware v 5.1.0 Authentium Command Anti-Malware v 5.0.9 Authentium Safe Central 3.0.2.3236.3236 ALWIL Software Avast 4.0 ALWIL Software Avast 4.7 ALWIL Avast 5 avast! Free Antivirus / Pro Antivirus / Internet Security 7 avast! Free Antivirus / Pro Antivirus / Internet Security 8 avast! Free Antivirus 6.0.1 Grisoft AVG 7.x Grisoft AVG 6.x Grisoft AVG 8.x Grisoft AVG 8.5 Grisoft AVG 8.5 Free Grisoft AVG 8.5 Free 64-bit Grisoft AVG 8.5 64-bit Grisoft AVG LinkScanner® 8.5 Grisoft AVG LinkScanner® 8.5 x64 Grisoft AVG 8.x x64 AVG 9.0 AVG 9.0 x64 AVG Free 9.0 AVG Free 9.0 x64 AVG 10.0.1136 Free Edition AVG 2011 AVG 2011 x64 AVG 2012.0.1913 x64 AVG 2012.0.1913 x86 AVG 2012 Free 2012.0.1901 x64 -

Ten Strategies of a World-Class Cybersecurity Operations Center Conveys MITRE’S Expertise on Accumulated Expertise on Enterprise-Grade Computer Network Defense
Bleed rule--remove from file Bleed rule--remove from file MITRE’s accumulated Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITRE’s expertise on accumulated expertise on enterprise-grade computer network defense. It covers ten key qualities enterprise- grade of leading Cybersecurity Operations Centers (CSOCs), ranging from their structure and organization, computer MITRE network to processes that best enable effective and efficient operations, to approaches that extract maximum defense Ten Strategies of a World-Class value from CSOC technology investments. This book offers perspective and context for key decision Cybersecurity Operations Center points in structuring a CSOC and shows how to: • Find the right size and structure for the CSOC team Cybersecurity Operations Center a World-Class of Strategies Ten The MITRE Corporation is • Achieve effective placement within a larger organization that a not-for-profit organization enables CSOC operations that operates federally funded • Attract, retain, and grow the right staff and skills research and development • Prepare the CSOC team, technologies, and processes for agile, centers (FFRDCs). FFRDCs threat-based response are unique organizations that • Architect for large-scale data collection and analysis with a assist the U.S. government with limited budget scientific research and analysis, • Prioritize sensor placement and data feed choices across development and acquisition, enteprise systems, enclaves, networks, and perimeters and systems engineering and integration. We’re proud to have If you manage, work in, or are standing up a CSOC, this book is for you. served the public interest for It is also available on MITRE’s website, www.mitre.org. more than 50 years. -

Measuring and Modeling the Label Dynamics of Online Anti-Malware Engines
Measuring and Modeling the Label Dynamics of Online Anti-Malware Engines Shuofei Zhu1, Jianjun Shi1,2, Limin Yang3 Boqin Qin1,4, Ziyi Zhang1,5, Linhai Song1, Gang Wang3 1The Pennsylvania State University 2Beijing Institute of Technology 3University of Illinois at Urbana-Champaign 4Beijing University of Posts and Telecommunications 5University of Science and Technology of China 1 VirusTotal • The largest online anti-malware scanning service – Applies 70+ anti-malware engines – Provides analysis reports and rich metadata • Widely used by researchers in the security community report API scan API Metadata Submitter Sample Reports 2 Challenges of Using VirusTotal • Q1: When VirusTotal labels are trustworthy? McAfee ✔️ ⚠️ ⚠️ ✔️ ✔️ Day 1 2 3 4 5 6 Time Sample 3 Challenges of Using VirusTotal • Q1: When VirusTotal labels are trustworthy? • Q2: How to aggregate labels from different engines? • Q3: Are different engines equally trustworthy? Engines Results McAfee ⚠️ ⚠️ Microsoft ✔️ ✔️ Kaspersky ✔️ Avast ⚠️ … 3 Challenges of Using VirusTotal • Q1: When VirusTotal labels are trustworthy? • Q2: How to aggregate labels from different engines? • Q3: Are different engines equally trustworthy? Equally trustworthy? 3 Literature Survey on VirusTotal Usages • Surveyed 115 top-tier conference papers that use VirusTotal • Our findings: – Q1: rarely consider label changes – Q2: commonly use threshold-based aggregation methods – Q3: often treat different VirusTotal engines equally Consider Label Changes Threshold-Based Method Reputable Engines Yes Yes No Yes