Semantics of Parametric Polymorphism in Imperative Programming Languages
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

At—At, Batch—Execute Commands at a Later Time
at—at, batch—execute commands at a later time at [–csm] [–f script] [–qqueue] time [date] [+ increment] at –l [ job...] at –r job... batch at and batch read commands from standard input to be executed at a later time. at allows you to specify when the commands should be executed, while jobs queued with batch will execute when system load level permits. Executes commands read from stdin or a file at some later time. Unless redirected, the output is mailed to the user. Example A.1 1 at 6:30am Dec 12 < program 2 at noon tomorrow < program 3 at 1945 pm August 9 < program 4 at now + 3 hours < program 5 at 8:30am Jan 4 < program 6 at -r 83883555320.a EXPLANATION 1. At 6:30 in the morning on December 12th, start the job. 2. At noon tomorrow start the job. 3. At 7:45 in the evening on August 9th, start the job. 4. In three hours start the job. 5. At 8:30 in the morning of January 4th, start the job. 6. Removes previously scheduled job 83883555320.a. awk—pattern scanning and processing language awk [ –fprogram–file ] [ –Fc ] [ prog ] [ parameters ] [ filename...] awk scans each input filename for lines that match any of a set of patterns specified in prog. Example A.2 1 awk '{print $1, $2}' file 2 awk '/John/{print $3, $4}' file 3 awk -F: '{print $3}' /etc/passwd 4 date | awk '{print $6}' EXPLANATION 1. Prints the first two fields of file where fields are separated by whitespace. 2. Prints fields 3 and 4 if the pattern John is found. -

TDS) EDEN PG MV® Pigment Ink for Textile
Technical Data Sheet (TDS) EDEN PG MV® Pigment Ink for Textile Product Description: Applications: EDEN PG MV water based pigment Ink is ideal for high-speed direct digital printing on all standard fabrics available on the market. The ink prints on all types of fabrics with equal quality and coverage without color shifts or patches. EDEN PG MV Pigment Ink may be used on cotton, cotton blends, polyester, polyamide (nylon) and treated & untreated fabrics. EDEN PG MV is ideal for a wide range of applications including sportswear, footwear, fashion, home décor and home textile and is designed for indoor and outdoor applications. This ink is manufactured using cutting edge technology and • Home textile • Bags • Indoor furnishing high-performance pigments, for optimal ink fluidity and • Décor • Sport apparel • Fashion & apparel printability through piezo printheads without bleeding or • Footwear migration. Compatible Print Head Technology: Ricoh Gen 4 & Gen 5 Industrial print heads based printers. Pre-treatment: The use of Bordeaux EDEN PG™ OS® (pretreatment liquid) is Product Line: recommended in order to achieve higher chemical attributes (see table below for comparison). The pretreatment process for fabrics is done offline using a standard textile padder. Red Cleaning Print procedure: Cyan Magenta Yellow Black Magenta Liquid The printing process can be done either inline or in individual segments. Inline printing allows the printed fabric to be fed Material Compatibility: through a standard textile dryer directly. Alternatively, if the printing stage is separated from the drying stage, drying is • Cotton required before rolling the fabric. • Viscose • Polyester • Lycra Drying Working Parameters: • Silk Recommended drying time: 3 minutes • Polyamide Recommended temperature: 150°C (302°F) • Leather • Synthetic leather Post-treatment: No chemical post treatment is needed. -

Design and Implementation of Generics for the .NET Common Language Runtime
Design and Implementation of Generics for the .NET Common Language Runtime Andrew Kennedy Don Syme Microsoft Research, Cambridge, U.K. fakeÒÒ¸d×ÝÑeg@ÑicÖÓ×ÓfغcÓÑ Abstract cally through an interface definition language, or IDL) that is nec- essary for language interoperation. The Microsoft .NET Common Language Runtime provides a This paper describes the design and implementation of support shared type system, intermediate language and dynamic execution for parametric polymorphism in the CLR. In its initial release, the environment for the implementation and inter-operation of multiple CLR has no support for polymorphism, an omission shared by the source languages. In this paper we extend it with direct support for JVM. Of course, it is always possible to “compile away” polymor- parametric polymorphism (also known as generics), describing the phism by translation, as has been demonstrated in a number of ex- design through examples written in an extended version of the C# tensions to Java [14, 4, 6, 13, 2, 16] that require no change to the programming language, and explaining aspects of implementation JVM, and in compilers for polymorphic languages that target the by reference to a prototype extension to the runtime. JVM or CLR (MLj [3], Haskell, Eiffel, Mercury). However, such Our design is very expressive, supporting parameterized types, systems inevitably suffer drawbacks of some kind, whether through polymorphic static, instance and virtual methods, “F-bounded” source language restrictions (disallowing primitive type instanti- type parameters, instantiation at pointer and value types, polymor- ations to enable a simple erasure-based translation, as in GJ and phic recursion, and exact run-time types. -

Relational Constraint Driven Test Case Synthesis for Web Applications
Relational Constraint Driven Test Case Synthesis for Web Applications Xiang Fu Hofstra University Hempstead, NY 11549 [email protected] This paper proposes a relational constraint driven technique that synthesizes test cases automatically for web applications. Using a static analysis, servlets can be modeled as relational transducers, which manipulate backend databases. We present a synthesis algorithm that generates a sequence of HTTP requests for simulating a user session. The algorithm relies on backward symbolic image computation for reaching a certain database state, given a code coverage objective. With a slight adaptation, the technique can be used for discovering workflow attacks on web applications. 1 Introduction Modern web applications usually rely on backend database systems for storing important system infor- mation or supporting business decisions. The complexity of database queries, however, often complicates the task of thoroughly testing a web application. To manually design test cases involves labor intensive initialization of database systems, even with the help of unit testing tools such as SQLUnit [25] and DBUnit [8]. It is desirable to automatically synthesize test cases for web applications. There has been a strong interest recently in testing database driven applications and database man- agement systems (see e.g., [12, 4, 20]). Many of them are query aware, i.e., given a SQL query, an initial database (DB) instance is generated to make that query satisfiable. The DB instance is fed to the target web application as input, so that a certain code coverage goal is achieved. The problem we are trying to tackle is one step further – it is a synthesis problem: given a certain database state (or a relational constraint), a call sequence of web servlets is synthesized to reach the given DB state. -
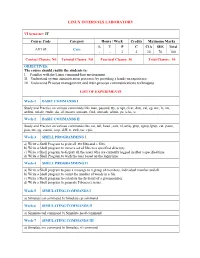
LINUX INTERNALS LABORATORY III. Understand Process
LINUX INTERNALS LABORATORY VI Semester: IT Course Code Category Hours / Week Credits Maximum Marks L T P C CIA SEE Total AIT105 Core - - 3 2 30 70 100 Contact Classes: Nil Tutorial Classes: Nil Practical Classes: 36 Total Classes: 36 OBJECTIVES: The course should enable the students to: I. Familiar with the Linux command-line environment. II. Understand system administration processes by providing a hands-on experience. III. Understand Process management and inter-process communications techniques. LIST OF EXPERIMENTS Week-1 BASIC COMMANDS I Study and Practice on various commands like man, passwd, tty, script, clear, date, cal, cp, mv, ln, rm, unlink, mkdir, rmdir, du, df, mount, umount, find, unmask, ulimit, ps, who, w. Week-2 BASIC COMMANDS II Study and Practice on various commands like cat, tail, head , sort, nl, uniq, grep, egrep,fgrep, cut, paste, join, tee, pg, comm, cmp, diff, tr, awk, tar, cpio. Week-3 SHELL PROGRAMMING I a) Write a Shell Program to print all .txt files and .c files. b) Write a Shell program to move a set of files to a specified directory. c) Write a Shell program to display all the users who are currently logged in after a specified time. d) Write a Shell Program to wish the user based on the login time. Week-4 SHELL PROGRAMMING II a) Write a Shell program to pass a message to a group of members, individual member and all. b) Write a Shell program to count the number of words in a file. c) Write a Shell program to calculate the factorial of a given number. -

Unix Programming
P.G DEPARTMENT OF COMPUTER APPLICATIONS 18PMC532 UNIX PROGRAMMING K1 QUESTIONS WITH ANSWERS UNIT- 1 1) Define unix. Unix was originally written in assembler, but it was rewritten in 1973 in c, which was principally authored by Dennis Ritchie ( c is based on the b language developed by kenThompson. 2) Discuss the Communication. Excellent communication with users, network User can easily exchange mail,dta,pgms in the network 3) Discuss Security Login Names Passwords Access Rights File Level (R W X) File Encryption 4) Define PORTABILITY UNIX run on any type of Hardware and configuration Flexibility credits goes to Dennis Ritchie( c pgms) Ported with IBM PC to GRAY 2 5) Define OPEN SYSTEM Everything in unix is treated as file(source pgm, Floppy disk,printer, terminal etc., Modification of the system is easy because the Source code is always available 6) The file system breaks the disk in to four segements The boot block The super block The Inode table Data block 7) Command used to find out the block size on your file $cmchk BSIZE=1024 8) Define Boot Block Generally the first block number 0 is called the BOOT BLOCK. It consists of Hardware specific boot program that loads the file known as kernal of the system. 9) Define super block It describes the state of the file system ie how large it is and how many maximum Files can it accommodate This is the 2nd block and is number 1 used to control the allocation of disk blocks 10) Define inode table The third segment includes block number 2 to n of the file system is called Inode Table. -

Parametric Polymorphism Parametric Polymorphism
Parametric Polymorphism Parametric Polymorphism • is a way to make a language more expressive, while still maintaining full static type-safety (every Haskell expression has a type, and types are all checked at compile-time; programs with type errors will not even compile) • using parametric polymorphism, a function or a data type can be written generically so that it can handle values identically without depending on their type • such functions and data types are called generic functions and generic datatypes Polymorphism in Haskell • Two kinds of polymorphism in Haskell – parametric and ad hoc (coming later!) • Both kinds involve type variables, standing for arbitrary types. • Easy to spot because they start with lower case letters • Usually we just use one letter on its own, e.g. a, b, c • When we use a polymorphic function we will usually do so at a specific type, called an instance. The process is called instantiation. Identity function Consider the identity function: id x = x Prelude> :t id id :: a -> a It does not do anything with the input other than returning it, therefore it places no constraints on the input's type. Prelude> :t id id :: a -> a Prelude> id 3 3 Prelude> id "hello" "hello" Prelude> id 'c' 'c' Polymorphic datatypes • The identity function is the simplest possible polymorphic function but not very interesting • Most useful polymorphic functions involve polymorphic types • Notation – write the name(s) of the type variable(s) used to the left of the = symbol Maybe data Maybe a = Nothing | Just a • a is the type variable • When we instantiate a to something, e.g. -

Products for Totally Integrated Automation
ST70_2015_en_Kap01.book Seite 1 Mittwoch, 20. Mai 2015 12:16 12 © Siemens AG 2015 Introduction 1 1/2 LOGO! logic module 1/3 SIMATIC basic controller 1/3 SIMATIC S7-1200 1/4 SIMATIC advanced controller 1/4 SIMATIC S7-1500 1/5 SIMATIC S7-300 1/7 SIMATIC S7-400 1/9 SIMATIC distributed controllers 1/11 SIMATIC software controllers 1/12 SIMATIC WinAC RTX (F) 1/12 SIMATIC programming devices 1/12 SIMATIC Field PG M4 1/13 SIMATIC Industrial PCs 1/14 SIMATIC software 1/15 SIMATIC ET 200 1/16 SIMATIC HMI 1/17 SIMATIC PCS 7 1/18 SIMATIC NET Brochures For brochures serving as selection guides for SIMATIC products refer to: www.siemens.com/simatic/ printmaterial Siemens ST 70 · 2015 ST70_2015_en_Kap01.book Seite 2 Mittwoch, 20. Mai 2015 12:16 12 © Siemens AG 2015 Introduction LOGO! LOGO! logic module 1 ■ Overview LOGO!: Easy-to-use technology with a future The compact, easy-to-use and low-cost solution for simple control tasks. Universally applicable in industry, and in functional or residential buildings. Replaces wiring by linking functions. Operates in a similar way to a programmable logic controller. With integrated operating and display unit for direct input on the device and display of message texts/variables, or as a version without display or keys. Simple operation: • Interconnection of functions by mouse click on the PC or at the press of a button on the device Minimum time requirements: • Wiring solely of the inputs and outputs • Parallel creation of circuit diagram and assembly of control cabinet Reduced costs: • Many integral functions of switching technology High level of flexibility: • Simple modification of functionality at the press of a button • Versions for different operating voltages • Modular design, therefore expandable at any time For further information, refer to: LOGO! 8 versions: www.siemens.com/logo • Ethernet interface for programming and communication with SIMATIC Controllers, SIMATIC Panels and PCs • Networking of max. -

CSE 307: Principles of Programming Languages Classes and Inheritance
OOP Introduction Type & Subtype Inheritance Overloading and Overriding CSE 307: Principles of Programming Languages Classes and Inheritance R. Sekar 1 / 52 OOP Introduction Type & Subtype Inheritance Overloading and Overriding Topics 1. OOP Introduction 3. Inheritance 2. Type & Subtype 4. Overloading and Overriding 2 / 52 OOP Introduction Type & Subtype Inheritance Overloading and Overriding Section 1 OOP Introduction 3 / 52 OOP Introduction Type & Subtype Inheritance Overloading and Overriding OOP (Object Oriented Programming) So far the languages that we encountered treat data and computation separately. In OOP, the data and computation are combined into an “object”. 4 / 52 OOP Introduction Type & Subtype Inheritance Overloading and Overriding Benefits of OOP more convenient: collects related information together, rather than distributing it. Example: C++ iostream class collects all I/O related operations together into one central place. Contrast with C I/O library, which consists of many distinct functions such as getchar, printf, scanf, sscanf, etc. centralizes and regulates access to data. If there is an error that corrupts object data, we need to look for the error only within its class Contrast with C programs, where access/modification code is distributed throughout the program 5 / 52 OOP Introduction Type & Subtype Inheritance Overloading and Overriding Benefits of OOP (Continued) Promotes reuse. by separating interface from implementation. We can replace the implementation of an object without changing client code. Contrast with C, where the implementation of a data structure such as a linked list is integrated into the client code by permitting extension of new objects via inheritance. Inheritance allows a new class to reuse the features of an existing class. -

INF 102 CONCEPTS of PROG. LANGS Type Systems
INF 102 CONCEPTS OF PROG. LANGS Type Systems Instructors: James Jones Copyright © Instructors. What is a Data Type? • A type is a collection of computational entities that share some common property • Programming languages are designed to help programmers organize computational constructs and use them correctly. Many programming languages organize data and computations into collections called types. • Some examples of types are: o the type Int of integers o the type (Int→Int) of functions from integers to integers Why do we need them? • Consider “untyped” universes: • Bit string in computer memory • λ-expressions in λ calculus • Sets in set theory • “untyped” = there’s only 1 type • Types arise naturally to categorize objects according to patterns of use • E.g. all integer numbers have same set of applicable operations Use of Types • Identifying and preventing meaningless errors in the program o Compile-time checking o Run-time checking • Program Organization and documentation o Separate types for separate concepts o Indicates intended use declared identifiers • Supports Optimization o Short integers require fewer bits o Access record component by known offset Type Errors • A type error occurs when a computational entity, such as a function or a data value, is used in a manner that is inconsistent with the concept it represents • Languages represent values as sequences of bits. A "type error" occurs when a bit sequence written for one type is used as a bit sequence for another type • A simple example can be assigning a string to an integer -

Parametric Polymorphism (Generics) 30 April 2018 Lecturer: Andrew Myers
CS 4120/5120 Lecture 36 Parametric Polymorphism (Generics) 30 April 2018 Lecturer: Andrew Myers Parametric polymorphism, also known as generics, is a programming language feature with implications for compiler design. The word polymorphism in general means that a value or other entity that can have more than one type. We have already talked about subtype polymorphism, in which a value of one type can act like another (super)type. Subtyping places constraints on how we implemented objects. In parametric polymorphism, the ability for something to have more than one “shape” is by introducing a type parameter. A typical motivation for parametric polymorphism is to support generic collection libraries such as the Java Collection Framework. Prior to the introduction of parametric polymorphism, all that code could know about the contents of a Set or Map was that it contained Objects. This led to code that was clumsy and not type-safe. With parametric polymorphism, we can apply a parameterized type such as Map to particular types: a Map String, Point maps Strings to Points. We can also parameterize procedures (functions, methods) withh respect to types.i Using Xi-like syntax, we might write a is_member method that can look up elements in a map: contains K, V (c: Map K, V , k: K): Value { ... } Map K, V h m i h i ...h i p: Point = contains String, Point (m, "Hello") h i Although Map is sometimes called a parameterized type or a generic type , it isn’t really a type; it is a type-level function that maps a pair of types to a new type. -

Polymorphism
Polymorphism A closer look at types.... Chap 8 polymorphism º comes from Greek meaning ‘many forms’ In programming: Def: A function or operator is polymorphic if it has at least two possible types. Polymorphism i) OverloaDing Def: An overloaDeD function name or operator is one that has at least two Definitions, all of Different types. Example: In Java the ‘+’ operator is overloaDeD. String s = “abc” + “def”; +: String * String ® String int i = 3 + 5; +: int * int ® int Polymorphism Example: Java allows user DefineD polymorphism with overloaDeD function names. bool f (char a, char b) { return a == b; f : char * char ® bool } bool f (int a, int b) { f : int * int ® bool return a == b; } Note: ML Does not allow function overloaDing Polymorphism ii) Parameter Coercion Def: An implicit type conversion is calleD a coercion. Coercions usually exploit the type-subtype relationship because a wiDening type conversion from subtype to supertype is always DeemeD safe ® a compiler can insert these automatically ® type coercions. Example: type coercion in Java Double x; x = 2; the value 2 is coerceD from int to Double by the compiler Polymorphism Parameter coercion is an implicit type conversion on parameters. Parameter coercion makes writing programs easier – one function can be applieD to many subtypes. Example: Java voiD f (Double a) { ... } int Ì double float Ì double short Ì double all legal types that can be passeD to function ‘f’. byte Ì double char Ì double Note: ML Does not perform type coercion (ML has no notion of subtype). Polymorphism iii) Parametric Polymorphism Def: A function exhibits parametric polymorphism if it has a type that contains one or more type variables.