Analysis of Public Opinion During Anthrax Scares, The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Amerithrax Investigative Summary
The United States Department of Justice AMERITHRAX INVESTIGATIVE SUMMARY Released Pursuant to the Freedom of Information Act Friday, February 19, 2010 TABLE OF CONTENTS I. THE ANTHRAX LETTER ATTACKS . .1 II. EXECUTIVE SUMMARY . 4 A. Overview of the Amerithrax Investigation . .4 B. The Elimination of Dr. Steven J. Hatfill as a Suspect . .6 C. Summary of the Investigation of Dr. Bruce E. Ivins . 6 D. Summary of Evidence from the Investigation Implicating Dr. Ivins . .8 III. THE AMERITHRAX INVESTIGATION . 11 A. Introduction . .11 B. The Investigation Prior to the Scientific Conclusions in 2007 . 12 1. Early investigation of the letters and envelopes . .12 2. Preliminary scientific testing of the Bacillus anthracis spore powder . .13 3. Early scientific findings and conclusions . .14 4. Continuing investigative efforts . 16 5. Assessing individual suspects . .17 6. Dr. Steven J. Hatfill . .19 7. Simultaneous investigative initiatives . .21 C. The Genetic Analysis . .23 IV. THE EVIDENCE AGAINST DR. BRUCE E. IVINS . 25 A. Introduction . .25 B. Background of Dr. Ivins . .25 C. Opportunity, Access and Ability . 26 1. The creation of RMR-1029 – Dr. Ivins’s flask . .26 2. RMR-1029 is the source of the murder weapon . 28 3. Dr. Ivins’s suspicious lab hours just before each mailing . .29 4. Others with access to RMR-1029 have been ruled out . .33 5. Dr. Ivins’s considerable skill and familiarity with the necessary equipment . 36 D. Motive . .38 1. Dr. Ivins’s life’s work appeared destined for failure, absent an unexpected event . .39 2. Dr. Ivins was being subjected to increasing public criticism for his work . -

Doj Inspector General Michael Horowitz Was Handpicked by the “Espionage Machine Part…
12/20/2017 Americans for Innovation: DOJ INSPECTOR GENERAL MICHAEL HOROWITZ WAS HANDPICKED BY THE “ESPIONAGE MACHINE PART… More Next Blog» Create Blog Sign In SEARCH by topic, keyword or phrase. Type in Custom Search box e.g. "IBM Eclipse Foundation" or "racketeering" Custom Search Saturday, December 16, 2017 DEEP STATE Member SHADOW DOJ INSPECTOR GENERAL MICHAEL HOROWITZ GOVERNMENT WAS HANDPICKED BY THE “ESPIONAGE MACHINE POSTER Harvard | Yale | Stanford Sycophants PARTY” RUN BY SOROS & ROGUE SPIES FOR AN Updated Dec. 12, 2017. UNELECTED CORPORATE COMBINE CLICK HERE TO SEE COMBINED TIMELINE OF THE INCREDIBLE BACKSTORY: HIJACKING OF THE INTERNET HOROWITZ HAS BEEN GROOMED BY GEORGE SOROS VIA DNC BARNEY PAY-to-PLA Y NEW W ORLD ORDER FRANK, THE CLINTONS AND JAMES CHANDLER SINCE HARVARD LAW SCHOOL This timeline shows how insiders sell access & manipulate politicians, police, intelligence, HOROWITZ & CLINTON ROAMED THE PLANET USING SPEECHES TO ORGANIZE judges and media to keep their secrets Clintons, Obamas, Summers were paid in cash for THE “ESPIONAGE MACHINE PARTY” TAKEOVER OF THE USA outlandish speaking fees and Foundation donations. Sycophant judges, politicians, academics, bureaucrats and media were fed tips to mutual funds tied to insider HE COACHED LEGAL & CORPORATE CRONIES HOW TO SKIRT U.S. stocks like Facebook. Risk of public exposure, SENTENCING & ETHICS LAWS blackmail, pedophilia, “snuff parties” (ritual child sexual abuse and murder) and Satanism have ensured silence among pay-to-play beneficiaries. The U.S. Patent Office CONTRIBUTING WRITERS | OPINION | AMERICANS FOR INNOVATION | DEC. 17, 2017 UPDATED DEC. 20, 2017 | is their toy box from which to steal new ideas. -

2001 Anthrax Letters
Chapter Five: 2001 Anthrax Letters Author’s Note: The analysis and comments regarding the communication efforts described in this case study are solely those of the authors; this analysis does not represent the official position of the FDA. This case was selected because it is one of the few major federal efforts to distribute medical countermeasures in response to an acute biological incident. These events occurred more than a decade ago and represent the early stages of US biosecurity preparedness and response; however, this incident serves as an excellent illustration of the types of communication challenges expected in these scenarios. Due in part to the extended time since these events and the limited accessibility of individual communications and messages, this case study does not provide a comprehensive assessment of all communication efforts. In contrast to the previous case studies in this casebook, the FDA’s role in the 2001 anthrax response was relatively small, and as such, this analysis focuses principally on the communication efforts of the CDC and state and local public health agencies. The 2001 anthrax attacks have been studied extensively, and the myriad of internal and external assessments led to numerous changes to response and communications policies and protocols. The authors intend to use this case study as a means of highlighting communication challenges strictly within the context of this incident, not to evaluate the success or merit of changes made as a result of these events. Abstract The dissemination of Bacillus anthracis via the US Postal Service (USPS) in 2001 represented a new public health threat, the first intentional exposure to anthrax in the United States. -

Like It Or Not, Trump Has a Point: FISA Reform and the Appearance of Partisanship in Intelligence Investigations by Stewart Baker1
Like It or Not, Trump Has a Point: FISA Reform and the Appearance of Partisanship in Intelligence Investigations by Stewart Baker1 To protect the country from existential threats, its intelligence capabilities need to be extraordinary -- and extraordinarily intrusive. The more intrusive they are, the greater the risk they will be abused. So, since the attacks of 9/11, debate over civil liberties has focused almost exclusively on the threat that intelligence abuses pose to the individuals and disfavored minorities. That made sense when our intelligence agencies were focused on terrorism carried out by small groups of individuals. But a look around the world shows that intelligence agencies can be abused in ways that are even more dangerous, not just to individuals but to democracy. Using security agencies to surveil and suppress political opponents is always a temptation for those in power. It is a temptation from which the United States has not escaped. The FBI’s director for life, J. Edgar Hoover, famously maintained his power by building files on numerous Washington politicians and putting his wiretapping and investigative capabilities at the service of Presidents pursuing political vendettas. That risk is making a comeback. The United States used the full force of its intelligence agencies to hold terrorism at bay for twenty years, but we paid too little attention to geopolitical adversaries who are now using chipping away at our strengths in ways we did not expect. As American intelligence reshapes itself to deal with new challenges from Russia and China, it is no longer hunting small groups of terrorists in distant deserts. -

CPC Outreach Journal #191
#191 14 Aug 2002 USAF COUNTERPROLIFERATION CENTER CPC OUTREACH JOURNAL Air University Air War College Maxwell AFB, Alabama Welcome to the CPC Outreach Journal. As part of USAF Counterproliferation Center’s mission to counter weapons of mass destruction through education and research, we’re providing our government and civilian community a source for timely counterproliferation information. This information includes articles, papers and other documents addressing issues pertinent to US military response options for dealing with nuclear, biological and chemical threats and attacks. It’s our hope this information resource will help enhance your counterproliferation issue awareness. Established here at the Air War College in 1998, the USAF/CPC provides education and research to present and future leaders of the Air Force, as well as to members of other branches of the armed services and Department of Defense. Our purpose is to help those agencies better prepare to counter the threat from weapons of mass destruction. Please feel free to visit our web site at www.au.af.mil/au/awc/awcgate/awc-cps.htm for in-depth information and specific points of contact. Please direct any questions or comments on CPC Outreach Journal to Lt Col Michael W. Ritz, ANG Special Assistant to Director of CPC or Jo Ann Eddy, CPC Outreach Editor, at (334) 953- 7538 or DSN 493-7538. To subscribe, change e-mail address, or unsubscribe to this journal or to request inclusion on the mailing list for CPC publications, please contact Mrs. Eddy. The following articles, papers or documents do not necessarily reflect official endorsement of the United States Air Force, Department of Defense, or other US government agencies. -

Chapman Law Review
Chapman Law Review Volume 21 Board of Editors 2017–2018 Executive Board Editor-in-Chief LAUREN K. FITZPATRICK Managing Editor RYAN W. COOPER Senior Articles Editors Production Editor SUNEETA H. ISRANI MARISSA N. HAMILTON TAYLOR A. KENDZIERSKI CLARE M. WERNET Senior Notes & Comments Editor TAYLOR B. BROWN Senior Symposium Editor CINDY PARK Senior Submissions & Online Editor ALBERTO WILCHES –––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––– Articles Editors ASHLEY C. ANDERSON KRISTEN N. KOVACICH ARLENE GALARZA STEVEN L. RIMMER NATALIE M. GAONA AMANDA M. SHAUGHNESSY-FORD ANAM A. JAVED DAMION M. YOUNG __________________________________________________________________ Staff Editors RAYMOND AUBELE AMY N. HUDACK JAMIE L. RICE CARLOS BACIO MEGAN A. LEE JAMIE L. TRAXLER HOPE C. BLAIN DANTE P. LOGIE BRANDON R. SALVATIERRA GEORGE E. BRIETIGAM DRAKE A. MIRSCH HANNAH B. STETSON KATHERINE A. BURGESS MARLENA MLYNARSKA SYDNEY L. WEST KYLEY S. CHELWICK NICHOLE N. MOVASSAGHI Faculty Advisor CELESTINE MCCONVILLE, Professor of Law CHAPMAN UNIVERSITY HAZEM H. CHEHABI ADMINISTRATION JEROME W. CWIERTNIA DALE E. FOWLER ’58 DANIELE C. STRUPPA BARRY GOLDFARB President STAN HARRELSON GAVIN S. HERBERT,JR. GLENN M. PFEIFFER WILLIAM K. HOOD Provost and Executive Vice ANDY HOROWITZ President for Academic Affairs MARK CHAPIN JOHNSON ’05 JENNIFER L. KELLER HAROLD W. HEWITT,JR. THOMAS E. MALLOY Executive Vice President and Chief SEBASTIAN PAUL MUSCO Operating Officer RICHARD MUTH (MBA ’05) JAMES J. PETERSON SHERYL A. BOURGEOIS HARRY S. RINKER Executive Vice President for JAMES B. ROSZAK University Advancement THE HONORABLE LORETTA SANCHEZ ’82 HELEN NORRIS MOHINDAR S. SANDHU Vice President and Chief RONALD M. SIMON Information Officer RONALD E. SODERLING KAREN R. WILKINSON ’69 THOMAS C. PIECHOTA DAVID W. -

Lessons from the Anthrax Attacks Implications for US
Lessons from the Anthrax Attacks Implications for US. Bioterrorism Preparedness A Report on a National Forum on Biodefense Author David Heymart Research Assistants Srusha Ac h terb erg, L Joelle Laszld Organized by the Center for Strategic and International Studies and the Defense Threat Reduction Agency --CFr”V? --.....a DlSTRf BUTION This report ISfor official use only; distribution authorized to U S. government agencies, designated contractors, and those with an official need Contains information that may be exempt from public release under the Freedom of Information Act. exemption number 2 (5 USC 552); exemption number 3 (’lo USC 130).Approvalof the Defense Threat Reduction Agency prior to public release is requrred Contract Number OTRAM-02-C-0013 For Official Use Only About CSIS For four decades, the Center for Stravgic and Internahonal Studies (CSIS)has been dedicated 10 providing world leaders with strategic insights on-and pohcy solubons tcurrentand emergtng global lssues CSIS IS led by John J Hamre, former L S deputy secretary of defense It is guided by a board of trustees chaired by former U S senator Sam Nunn and consistlng of prominent individuals horn both the public and private sectors The CSIS staff of 190 researchers and support staff focus pnrnardy on three subjecr areas First, CSIS addresses the fuU spectrum of new challenges to national and mternabonal security Second, it maintains resident experts on all of the world's myor geographical regions Third, it IS committed to helping to develop new methods of governance for the global age, to this end, CSIS has programs on technology and pubhc policy, International trade and finance, and energy Headquartered in Washington, D-C ,CSIS IS pnvate, bipartlsan, and tax-exempt CSIS docs not take specific policy positions, accordygly, all views expressed herein should be understood to be solely those ofthe author Spousor. -

Confidentiality Complications
Confidentiality Complications: How new rules, technologies and corporate practices affect the reporter’s privilege and further demonstrate the need for a federal shield law The Reporters Committee for Freedom of the Press June 2007 Lucy A. Dalglish, Esq. Gregg P. Leslie, Esq. Elizabeth J. Soja, Esq. 1101 Wilson Blvd., Suite 1100 Arlington, Virginia 22209 (703) 807-2100 Executive Summary The corporate structure of the news media has created new obstacles, both financial and practical, for journalists who must keep promises of confidentiality. Information that once existed only in a reporter’s notebook can now be accessed by companies that have obligations not only to their reporters, but to their shareholders, their other employees, and the public. Additionally, in the wake of an unprecedented settlement in the Wen Ho Lee Privacy Act case, parties can target news media corporations not just for their access to a reporter’s information, but also for their deep pockets. The potential for conflicts of interest is staggering, but the primary concerns of The Reporters Committee for Freedom of the Press are that: • because of the 21st-century newsroom’s reliance on technology, corporations now have access to notes, correspondence and work-product information that before only existed in a reporter’s notebook; • the new federal “e-discovery” court rules allow litigants to discover vastly more information than a printed page – or even a saved e-mail – would provide during litigation; • while reporters generally only have responsibilities to themselves, -

Forensic Intelligence International, LLC the Kauth House, 318 Cooper Avenue, Hancock, Michigan 49930 2 151 Moore Street SE, Crawfordville, Georgia 30631 Tel
Forensic Intelligence International, LLC the Kauth house, 318 Cooper Avenue, Hancock, Michigan 49930 2 151 Moore Street SE, Crawfordville, Georgia 30631 Tel. 906-370-9993 (MI), 706-456-2696 (GA), 706-294-9993 (cellular) FI Fax & Voice Mail 603-452-8208 | E-mail: [email protected] Saturday, July 6, 2002 [22:44:15] Stephen P. Dresch, Ph.D. STEVEN JAY HATFILL Questionable (Quite Possibly Unsavory) Past – Ideal Fall-Guy for the Anthrax Incidents Hatfill in his own words, as posted (Spring or Summer 2001?) on the Southwestern College (Kansas) web site:1 Steven Hatfill [Southwestern College, Winfield, Kansas] '75 is a specialist in biological warfare and its defense, and has completed training to become a United Nations weapons inspector in Iraq. The training involved five weeks of intensive study in France with 52 other scientists from U.N. member nations. When inspectors are given permission to re-enter Iraq, Hatfill will be on the first team of in- spectors. The U.N. training continues a peripatetic career that began while Hatfill was studying for his biology degree at Southwestern: He took a year off to work with a Methodist doctor in Africa. After gradu- ating from SC Hatfill received a medical degree from the Godfrey Huggins School of Medicine in Rhodesia, with board certification in hematological pathology from South Africa. The South African government recruited him to be medical officer on a one-year tour of duty in Ant- arctica, and he completed a post-doctoral fellowship at Oxford University in England. He has three separate master's degrees in microbial genetics, medical biochemistry, and experimental pathology, as well as a Ph.D. -

VIPS' William Binney Advarer: Russiagate
Hvad er geopolitik? Første del: Historie. LaRouche PAC’s Undervisningsserie 2018, »Hvad er det Nye Paradigme?«, Lektion 2, 17. feb. 2018 Der var de fortsatte provokationer i Mellemøsten, provokationer i Asien, Koreakrigen, Vietnamkrigen – dette var geopolitik med det formål at bevare Det britiske Imperium. Og desværre, med mordet på Kennedy, blev USA en partner i det, man kunne kalde et »anglo-amerikansk geopolitisk imperium«. Og hvad gik politikkerne ud på? Frihandel, neoliberal økonomi, nedskæringspolitik. Svækkelse af regeringer, svækkelse af ideen om national suverænitet og etablering af institutioner som den Europæiske Union, der ønsker ikkevalgte bureaukrater til at bestemme politikker for det, der plejede at være nationalstater. Det så ud, som om alt dette kunne ændre sig i 1989, med den kommunistiske verdens fald, med det østtyske regimes kollaps og Berlinmurens fald. På dette tidspunkt intervenerede LaRouche-organisationen meget direkte, for et alternativ til geopolitik. Lyndon LaRouche var blevet fængslet af George Bush, med assistance fra den daværende vicestatsanklager i Boston, Robert Mueller. Men Helga Zepp-LaRouche anførte kampen for det, vi dengang kaldte den Produktive Trekant Paris- Berlin-Wien, og dernæst, så tidligt som i slutningen af 1990, det, der blev kaldt den »Nye Silkevej« eller den Eurasiske Landbro, som et middel til at bringe nationer sammen og overvinde disse kunstige opdelinger, skabt af Det britiske Imperium. Download (PDF, Unknown) EIR: Man det britiske kup i jorden: Muellers anklageskrifter mod russiske sociale medietrolde platter det amerikanske folk Som vi gentagne gange har vist, så er den strategiske sammenhæng for kuppet mod Trump en fuldt optrappet bestræbelse på at bevare den anglo-amerikanske orden imod det, der opfattes som Kinas fremvoksende magt, som nu er allieret med Rusland. -
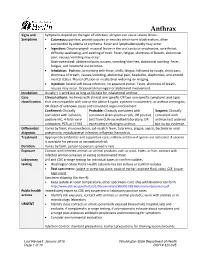
Anthrax Reporting and Investigation Guideline
Anthrax Signs and Symptoms depend on the type of infection; all types can cause severe illness: Symptoms • Cutaneous: painless, pruritic papules or vesicles which form black eschars, often surrounded by edema or erythema. Fever and lymphadenopathy may occur. • Ingestion: Oropharyngeal: mucosal lesion in the oral cavity or oropharynx, sore throat, difficulty swallowing, and swelling of neck. Fever, fatigue, shortness of breath, abdominal pain, nausea/vomiting may occur. Gastrointestinal: abdominal pain, nausea, vomiting/diarrhea, abdominal swelling. Fever, fatigue, and headache are common. • Inhalation: Biphasic, presenting with fever, chills, fatigue, followed by cough, chest pain, shortness of breath, nausea/vomiting, abdominal pain, headache, diaphoresis, and altered mental status. Pleural effusion or mediastinal widening on imaging. • Injection: Severe soft tissue infection; no apparent eschar. Fever, shortness of breath, nausea may occur. Occasional meningeal or abdominal involvement. Incubation Usually < 1 week but as long as 60 days for inhalational anthrax Case Clinical criteria: An illness with at least one specific OR two non-specific symptoms and signs classification that are compatible with one of the above 4 types, systemic involvement, or anthrax meningitis; OR death of unknown cause and consistent organ involvement Confirmed: Clinically Probable: Clinically consistent with Suspect: Clinically consistent with isolation, consistent Gram-positive rods, OR positive consistent with positive IHC, 4-fold rise in test from CLIA-accredited laboratory, OR anthrax test ordered antibodies, PCR, or LF MS epi evidence relating to anthrax but no epi evidence Differential Varies by form; mononucleosis, cat-scratch fever, tularemia, plague, sepsis, bacterial or viral diagnosis pneumonia, mycobacterial infection, influenza, hantavirus Treatment Appropriate antibiotics and supportive care; anthrax antitoxin if spores are activated. -

The Case Study of Crossfire Hurricane
TIMELINE: Congressional Oversight in the Face of Executive Branch and Media Suppression: The Case Study of Crossfire Hurricane 2009 FBI opens a counterintelligence investigation of the individual who would become Christopher Steele’s primary sub-source because of his ties to Russian intelligence officers.1 June 2009: FBI New York Field Office (NYFO) interviews Carter Page, who “immediately advised [them] that due to his work and overseas experiences, he has been questioned by and provides information to representatives of [another U.S. government agency] on an ongoing basis.”2 2011 February 2011: CBS News investigative journalist Sharyl Attkisson begins reporting on “Operation Fast and Furious.” Later in the year, Attkisson notices “anomalies” with several of her work and personal electronic devices that persist into 2012.3 2012 September 11, 2012: Attack on U.S. installations in Benghazi, Libya.4 2013 March 2013: The existence of former Secretary of State Hillary Clinton’s private email server becomes publicly known.5 May 2013: o News reports reveal Obama’s Justice Department investigating leaks of classified information and targeting reporters, including secretly seizing “two months of phone records for reporters and editors of The Associated Press,”6 labeling Fox News reporter James Rosen as a “co-conspirator,” and obtaining a search warrant for Rosen’s personal emails.7 May 10, 2013: Reports reveal that the Internal Revenue Service (IRS) targeted and unfairly scrutinized conservative organizations seeking tax-exempt status.8