Conventional Defenses + Unconventional Adversaries == ??? Joshua Corman Director, Security Intelligence @Joshcorman
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“Hacktivists” Strike Back
SECUrITY AGENCE FRANCE-PRESSE Supporters of Wikileaks founder Julian Assange “Hacktivists” Strike Back wear Guy Fawkes masks Cyber attacks on financial institutions serve as they demonstrate against his arrest in as a warning sign Amsterdam in December 2010. The “Hacktivist” in december 2010, the websites of international financial services gi- group “Anonymous” has ants Visa, Mastercard and PayPal were temporarily shut down, victims adopted the Guy Fawkes of a coordinated cyber attack dubbed Operation Payback by its per- image as its public face. petrators. “Hacktivists” who support wikileaks and its founder Julian assange attacked after the companies terminated service and disabled donations to the website. The economic impact of the attack remains unclear and the tar- geted companies denied suffering consequential losses. but the attackers, using the names “anon” and “anonymous,” demonstrated the ability of cyber attacks to infiltrate and damage businesses and government agencies. A modern form of protest Amazon, the online retailer that hosted Anonymous didn’t protest by chanting slogans Wikileaks on its servers, was the first to pull out. or waving signs — it struck against Wikileaks’ Visa, MasterCard and PayPal soon followed, perceived enemies in the spirit of the virtual essentially crippling Wikileaks’ ability to accept world they share. Wikileaks, whose raison d'être is donations that support publishing efforts. The exposing classified or confidential government cyber attacks started soon after. or corporate information, is under pressure When Anonymous staged its attack in the vir- from the United States and other governments tual world, it used a favorite weapon of the cyber after leaking more than 250,000 U.S. -

List of Targets of Arrested Computer Hackers 6 March 2012
List of targets of arrested computer hackers 6 March 2012 The five computer hackers charged in New York Tribune and Los Angeles Times, using on Tuesday and a sixth who pleaded guilty are misappropriated login credentials. accused of involvement in some of the most notorious hacking incidents of the past 18 months. -- February 2011: A cyberattack on private computer security firm HBGary that involved the The following are some of the cyberattacks in theft of 60,000 emails from HBGary employees and which the two Britons, two Irishmen and two the HBGary chief executive, as well as defacing his Americans allegedly played a role as members of Twitter account. Anonymous, Lulz Security or associated groups: -- April-May 2011: A cyberattack on a Fox -- December 2010: Operation Payback. Distributed Broadcasting Company website that involved the denial of service (DDoS) attacks by members of theft of names, dates of birth, telephone numbers, Anonymous on the websites of MasterCard, email and residential addresses for more than PayPal and Visa in retaliation for their refusal to 70,000 potential contestants on the Fox television accept donations for WikiLeaks. In a DDoS attack, show the "X-Factor." a website is bombarded with traffic, slowing it down or knocking it offline completely. -- May 2011: A cyberattack on Sony Pictures Entertainment that revealed the passwords, email -- January 2011: Defacing a website of the Irish addresses, home addresses and dates of birth of political party Fine Gael after accessing computer 100,000 users of the www.sonypictures.com servers in Arizona used to maintain the website, website and a subsequent online attack against www.finegael2011.com. -

Darpa Starts Sleuthing out Disloyal Troops
UNCLASSIFIED (U) FBI Tampa Division CI Strategic Partnership Newsletter JANUARY 2012 (U) Administrative Note: This product reflects the views of the FBI- Tampa Division and has not been vetted by FBI Headquarters. (U) Handling notice: Although UNCLASSIFIED, this information is property of the FBI and may be distributed only to members of organizations receiving this bulletin, or to cleared defense contractors. Precautions should be taken to ensure this information is stored and/or destroyed in a manner that precludes unauthorized access. 10 JAN 2012 (U) The FBI Tampa Division Counterintelligence Strategic Partnership Newsletter provides a summary of previously reported US government press releases, publications, and news articles from wire services and news organizations relating to counterintelligence, cyber and terrorism threats. The information in this bulletin represents the views and opinions of the cited sources for each article, and the analyst comment is intended only to highlight items of interest to organizations in Florida. This bulletin is provided solely to inform our Domain partners of news items of interest, and does not represent FBI information. In the JANUARY 2012 Issue: Article Title Page NATIONAL SECURITY THREAT NEWS FROM GOVERNMENT AGENCIES: American Jihadist Terrorism: Combating a Complex Threat p. 2 Authorities Uncover Increasing Number of United States-Based Terror Plots p. 3 Chinese Counterfeit COTS Create Chaos For The DoD p. 4 DHS Releases Cyber Strategy Framework p. 6 COUNTERINTELLIGENCE/ECONOMIC ESPIONAGE THREAT ITEMS FROM THE PRESS: United States Homes In on China Spying p. 6 Opinion: China‟s Spies Are Catching Up p. 8 Canadian Politician‟s Chinese Crush Likely „Sexpionage,‟ Former Spies Say p. -

Ethical Hacking
Ethical Hacking Alana Maurushat University of Ottawa Press ETHICAL HACKING ETHICAL HACKING Alana Maurushat University of Ottawa Press 2019 The University of Ottawa Press (UOP) is proud to be the oldest of the francophone university presses in Canada and the only bilingual university publisher in North America. Since 1936, UOP has been “enriching intellectual and cultural discourse” by producing peer-reviewed and award-winning books in the humanities and social sciences, in French or in English. Library and Archives Canada Cataloguing in Publication Title: Ethical hacking / Alana Maurushat. Names: Maurushat, Alana, author. Description: Includes bibliographical references. Identifiers: Canadiana (print) 20190087447 | Canadiana (ebook) 2019008748X | ISBN 9780776627915 (softcover) | ISBN 9780776627922 (PDF) | ISBN 9780776627939 (EPUB) | ISBN 9780776627946 (Kindle) Subjects: LCSH: Hacking—Moral and ethical aspects—Case studies. | LCGFT: Case studies. Classification: LCC HV6773 .M38 2019 | DDC 364.16/8—dc23 Legal Deposit: First Quarter 2019 Library and Archives Canada © Alana Maurushat, 2019, under Creative Commons License Attribution— NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) https://creativecommons.org/licenses/by-nc-sa/4.0/ Printed and bound in Canada by Gauvin Press Copy editing Robbie McCaw Proofreading Robert Ferguson Typesetting CS Cover design Édiscript enr. and Elizabeth Schwaiger Cover image Fragmented Memory by Phillip David Stearns, n.d., Personal Data, Software, Jacquard Woven Cotton. Image © Phillip David Stearns, reproduced with kind permission from the artist. The University of Ottawa Press gratefully acknowledges the support extended to its publishing list by Canadian Heritage through the Canada Book Fund, by the Canada Council for the Arts, by the Ontario Arts Council, by the Federation for the Humanities and Social Sciences through the Awards to Scholarly Publications Program, and by the University of Ottawa. -

Hacktivism Cyberspace Has Become the New Medium for Political Voices
White Paper Hacktivism Cyberspace has become the new medium for political voices By François Paget, McAfee Labs™ Table of Contents The Anonymous Movement 4 Origins 4 Defining the movement 6 WikiLeaks meets Anonymous 7 Fifteen Months of Activity 10 Arab Spring 10 HBGary 11 The Sony ordeal 11 Lulz security and denouncements 12 Groups surrounding LulzSec 13 Green rights 14 Other operations 15 AntiSec, doxing, and copwatching 16 Police responses 17 Anonymous in the streets 18 Manipulation and pluralism 20 Operation Megaupload 21 Communications 21 Social networks and websites 21 IRC 22 Anonymity 23 DDoS Tools 24 Cyberdissidents 25 Telecomix 26 Other achievements 27 Patriots and Cyberwarriors 28 Backlash against Anonymous 29 TeaMp0isoN 30 Other achievements 30 Conclusion 32 2 Hacktivism What is hacktivism? It combines politics, the Internet, and other elements. Let’s start with the political. Activism, a political movement emphasising direct action, is the inspiration for hacktivism. Think of Greenpeace activists who go to sea to disrupt whaling campaigns. Think of the many demonstrators who protested against human rights violations in China by trying to put out the Olympic flame during its world tour in 2008. Think of the thousands of activists who responded to the Adbusters call in July 2011 to peacefully occupy a New York City park as part of Occupy Wall Street. Adding the online activity of hacking (with both good and bad connotations) to political activism gives us hacktivism. One source claims this term was first used in an article on the filmmaker Shu Lea Cheang; the article was written by Jason Sack and published in InfoNation in 1995. -

The Masked Avengers: How Anonymous Incited Online
A REPORTER AT LARGE | SEPTEMBER 8, 2014 ISSUE The Masked Avengers How Anonymous incited online vigilantism from Tunisia to Ferguson. BY DAVID KUSHNER Anyone can join Anonymous simply by claiming affiliation. An anthropologist says that participants “remain subordinate to a focus on the epic win—and, especially, the lulz.” n the mid-nineteen-seventies, when Christopher Doyon was a child in rural Maine, he spent Ihours chatting with strangers on CB radio. His handle was Big Red, for his hair. Transmitters lined the walls of his bedroom, and he persuaded his father to attach two directional antennas to the roof of their house. CB radio was associated primarily with truck drivers, but Doyon and others used it to form the sort of virtual community that later appeared on the Internet, with self- selected nicknames, inside jokes, and an earnest desire to effect change. Doyon’s mother died when he was a child, and he and his younger sister were reared by their father, who they both say was physically abusive. Doyon found solace, and a sense of purpose, in the CB-radio community. He and his friends took turns monitoring the local emergency channel. One friend’s father bought a bubble light and affixed it to the roof of his car; when the boys heard a distress call from a stranded motorist, he’d drive them to the side of the highway. There wasn’t much they could do beyond offering to call 911, but the adventure made them feel heroic. Small and wiry, with a thick New England accent, Doyon was fascinated by “Star Trek” and Isaac Asimov novels. -

Data Thieves: the Motivations of Cyber Threat Actors and Their Use
Testimony Data Thieves The Motivations of Cyber Threat Actors and Their Use and Monetization of Stolen Data Lillian Ablon CT-490 Testimony presented before the House Financial Services Committee, Subcommittee on Terrorism and Illicit Finance, on March 15, 2018. For more information on this publication, visit www.rand.org/pubs/testimonies/CT490.html Testimonies RAND testimonies record testimony presented or submitted by RAND associates to federal, state, or local legislative committees; government-appointed commissions and panels; and private review and oversight bodies. Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2018 RAND Corporation is a registered trademark. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions.html. www.rand.org Data Thieves: The Motivations of Cyber Threat Actors and Their Use and Monetization of Stolen Data Testimony of Lillian Ablon1 The RAND Corporation2 Before the Committee on Financial Services Subcommittee on Terrorism and Illicit Finance United States House of Representatives March 15, 2018 ood afternoon, Chairman Pearce, Ranking Member Perlmutter, and distinguished members of the subcommittee. Thank you for the invitation to testify at this important G hearing, “After the Breach: the Monetization and Illicit Use of Stolen Data.” Cybersecurity is a constant and growing challenge. -

2011 Global Application & Network Security Report
& Network Security Report 2011 Global Application 20 11 Global Application & Network Security Report Radware 2012 Annual Security Report Smart Network. Smart Business. Table of Contents 01 02 03 Executive Summary Introduction Hacktivism and the » Most important findings » Scope of the Report Rise of Anonymous » Anonymous Projects » Radware Security Survey » Anonymous Power » The ERT Survey » Anonymous Opens Fire » Case Study: Attack on Turkish Government » Anonymous Modify Attack Vectors » A Post-LOIC Attack – Case Study 04 05 06 Attack Sizes DoS Attack Nature The Internet Server Varies Dramatically Becomes More is not Necessarily the APT Oriented First to Fall » General Description » What Happens When a Firewall is Not Protected - Case Study 07 08 09 More Organizations are Attack Tool Trends Mitigation Now Under DoS Threat » LOIC Techniques » Overview » Mobile LOIC » Mitigation Technologies » R.U.D.Y. (R-U-Dead Yet) » Rate Limit and » THC-SSL-DoS Bandwidth Management » Behavioral-Based Protection » Challenges » Stateful Inspection » Geographical-Based Protection » ACL and RTBH » Signatures (Including Flowspec) » The Most Common DoS Mitigation Technologies 10 11 » Technology Efficiency Counter Attacks Summary » Recommendations for the Network and Security Community Smart Network. Smart Business. 01 Executive Summary 2011 was the year in which DoS / DDoS attacks turned from its niche corner and became a mainstream security threat. The single most important reason for this is the Anonymous phenomena. This loosely organized group brought virtual social protests to the forefront with attacks on large and well-known organizations. Their major campaign, Operation Payback, during the WikiLeaks saga in December 2010 against those supporting the US government was the turning point that shaped the security scene in 2011. -

The Anatomy of an Anonymous Attack the Anatomy of an Anonymous Attack
White Paper Imperva’s Hacker Intelligence Summary Report The Anatomy of an Anonymous Attack The Anatomy of an Anonymous Attack Executive Summary During 2011, Imperva witnessed an assault by the hacktivist group ‘Anonymous’ that lasted 25 days. Our observations give insightful information on Anonymous, including a detailed analysis of hacking methods, as well as an examination of how social media provides a communications platform for recruitment and attack coordination. Hacktivism has grown dramatically in the past year and has become a priority for security organizations worldwide. Understanding Anonymous’ attack methods will help organizations prepare if they are ever a target. Our observation of an Anonymous campaign reveals: › The process used by Anonymous to pick victims as well as recruit and use needed hacking talent. › How Anonymous leverages social networks to recruit members and promotes hack campaigns. › The specific cyber reconnaissance and attack methods used by Anonymous’ hackers. We detail and sequence the steps Anonymous hackers deploy that cause data breaches and bring down websites. Finally, we recommend key mitigation steps that organizations need to help protect against attacks. Methodology This report is based on an Anonymous attack observed by the Imperva Application Defense Center. The target organization of the attack had a Web application firewall deployed which recorded and repelled the attacks. By analyzing traffic logs, we analyzed the attacks on these applications and categorized them according to the attack method, as well as identified patterns and trends within these attacks. We also analyzed Anonymous social media communications in the days leading up to and after the attack. We believe this is the first end-to-end record of a full Anonymous attack. -

Hacktivism, Anonymous & a New Breed of Protest in a Networked World
HACKTIVISM, ANONYMOUS & A NEW BREED OF PROTEST IN A NETWORKED WORLD Noah C.N. Hampson Introduction Early on the morning of November 30, 2010, WikiLeaks.org came under assault by a hacker known as ‚th3j35t3r‛ (The Jester).1 By launching what is known as a denial of service (DoS) attack with soft- ware of his own invention, The Jester overwhelmed WikiLeaks’ serv- ers with requests for information.2 WikiLeaks.org soon crashed, and remained down for over a day.3 Days before, WikiLeaks made interna- tional headlines by posting on its website roughly 250,000 classified documents stolen from the U.S. government.4 On his Twitter feed, The Jester claimed credit: ‚www.wikileaks.org — TANGO DOWN — for attempting to endanger the lives of our troops, ‘other assets’ & foreign relations #wikileaks #fail‛.5 To get its web site back online, WikiLeaks promptly switched hosting providers and began renting bandwidth from Amazon.com.6 DoS and other attacks against WikiLeaks continued, but were unsuc- cessful.7 Shortly thereafter, however, Amazon ousted WikiLeaks from 1 Sean-Paul Correll, ‘Tis the Season of DDoS – WikiLeaks Edition, PandaLabs Blog (Dec. 4, 2010), http://pandalabs.pandasecurity.com/tis-the-season-of-ddos-wikileaks-editio/. 2 See Neil J. Rubenkind, WikiLeaks Attack: Not the First by th3j35t3r, PC (Nov. 29, 2010), http://www.pcmag.com/article2/0,2817,2373559,00.asp 3 See Correll, supra note 1. 4 See Scott Shane & Andrew W. Lehren, Leaked Cables Offer Raw Look at U.S. Diplomacy, N.Y. Times, Nov. 29, 2010, at A1, available at http://www.nytimes.com/2010/11/29/world/29cables.html. -
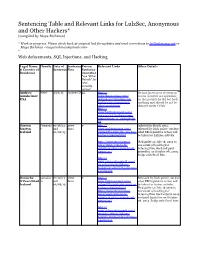
Sentencing Table and Relevant Links for Lulzsec, Anonymous and Other Hackers* (Compiled by Maya Richman)
Sentencing Table and Relevant Links for LulzSec, Anonymous and Other Hackers* (compiled by Maya Richman) * Work in progress. Please check back at original link for updates and send corrections to [email protected] or Maya Richman <[email protected]> * Web defacements, SQL Injections, and Hacking Legal Name Handle Date of Sentence Prison Relevant Links Other Details & Country of Sentence Fine Sentence Residence (months) *see “Other Details” for time actually served Andrew Weev 3/18/13 73,000 US42 http:// He had faced up to 10 years in Aumheimer www.theguardian.com/ prison. Lawyers are appealing USA technology/2013/jan/24/ on the grounds he did not hack hacking-us-government- anything and should be not be cyber-crackdown charged under CFAA. http:// www.huffingtonpost.com/ 2013/03/18/andrew-weev- auernheimer_n_2900387.ht ml Darren Pwnsaus 07/16/13 5000 0 http:// Indicted in March 2012, Martyn e and Euro www.irishexaminer.com/ released by Irish police, unclear Ireland 10/08/13 ireland/fbi-irish-duo-are-top- what FBI legislative action will hackers-186280.html be taken for LulzSec activity. http://www.rte.ie/news/ Pled guilty on July 16, 2013 to 2013/1008/479105-fg- one count of hacking for website-hackers-spared-jail- defacing Fine Gael and paid sentences/ 5000 fine on October 08, 2013. Judge only fined him. http:// www.informationweek.com/ security/attacks/lulzsec- hackers-evade-irish-jail-time/ 240162429 Donncha palladiu 07/16/13 5000 0 http:// Released by Irish police, unclear O'Cearrbhail m and Euro www.irishexaminer.com/ what FBI legislative action will Ireland 10/08/13 ireland/fbi-irish-duo-are-top- be taken for luzlsec activity. -

Hacker, Hoaxer, Whistleblower, Spy the Many Faces of Anonymous
hacker, hoaxer, whistleblower, spy the many faces of anonymous Gabriella Coleman London • New York Hacker Hoaxer Whistleblower 2015 PB 13-08-15.indd 3 8/13/2015 3:44:42 PM Epilogue: The State of Anonymous “I have grown to love secrecy. It seems to be the one thing that can make modern life mysterious or marvelous to us. The commonest thing is delightful if only one hides it.” Oscar Wilde “The political education of apolitical technical people is extra ordinary.” Julian Assange he period described in this book may seem to many to represent the pinnacle of Anonymous activity: their Tsupport role in the various movements that constituted the Arab Spring; the high-profile media attention garnered by the gutsy LulzSec and AntiSec hacks; the ever growing com- mitment to domestic social justice issues seen in engagements against rape culture and police brutality. Unsurprisingly, this impressive flurry of protest activity was met with similarly impressive law enforcement crackdowns. Throughout Europe, Asia, Australia, and the Americas, law enforcement officials detained over one hundred Anonymous activists—including many of the figures profiled in this book: Jeremy Hammond and John Borell in the United States, and Ryan Ackroyd and Mustafa Al-Bassam in the United Hacker Hoaxer Whistleblower 2015 PB 13-08-15.indd 401 8/13/2015 3:44:54 PM 402 hacker, hoaxer, whistleblower, spy Kingdom. Others arrested were geeky activists whose “crime” had been to simply channel a small portion of their computer resources toward DDoS campaigns organized by Anonymous in an effort to collectively shame financial organizations, such as PayPal when they caved to government pressure and terminated all services to the embattled whistleblowing organ- ization WikiLeaks.