An Interactive Remote Shell for Mobile Clients Abstract 1 Introduction
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Freenas® 11.0 User Guide
FreeNAS® 11.0 User Guide June 2017 Edition FreeNAS® IS © 2011-2017 iXsystems FreeNAS® AND THE FreeNAS® LOGO ARE REGISTERED TRADEMARKS OF iXsystems FreeBSD® IS A REGISTERED TRADEMARK OF THE FreeBSD Foundation WRITTEN BY USERS OF THE FreeNAS® network-attached STORAGE OPERATING system. VERSION 11.0 CopYRIGHT © 2011-2017 iXsystems (https://www.ixsystems.com/) CONTENTS WELCOME....................................................1 TYPOGRAPHIC Conventions...........................................2 1 INTRODUCTION 3 1.1 NeW FeaturES IN 11.0..........................................3 1.2 HarDWARE Recommendations.....................................4 1.2.1 RAM...............................................5 1.2.2 The OperATING System DeVICE.................................5 1.2.3 StorAGE Disks AND ContrOLLERS.................................6 1.2.4 Network INTERFACES.......................................7 1.3 Getting Started WITH ZFS........................................8 2 INSTALLING AND UpgrADING 9 2.1 Getting FreeNAS® ............................................9 2.2 PrEPARING THE Media.......................................... 10 2.2.1 On FreeBSD OR Linux...................................... 10 2.2.2 On WindoWS.......................................... 11 2.2.3 On OS X............................................. 11 2.3 Performing THE INSTALLATION....................................... 12 2.4 INSTALLATION TROUBLESHOOTING...................................... 18 2.5 UpgrADING................................................ 19 2.5.1 Caveats:............................................ -

Technical Study Desktop Internationalization
Technical Study Desktop Internationalization NIC CH A E L T S T U D Y [This page intentionally left blank] X/Open Technical Study Desktop Internationalisation X/Open Company Ltd. December 1995, X/Open Company Limited All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior permission of the copyright owners. X/Open Technical Study Desktop Internationalisation X/Open Document Number: E501 Published by X/Open Company Ltd., U.K. Any comments relating to the material contained in this document may be submitted to X/Open at: X/Open Company Limited Apex Plaza Forbury Road Reading Berkshire, RG1 1AX United Kingdom or by Electronic Mail to: [email protected] ii X/Open Technical Study (1995) Contents Chapter 1 Internationalisation.............................................................................. 1 1.1 Introduction ................................................................................................. 1 1.2 Character Sets and Encodings.................................................................. 2 1.3 The C Programming Language................................................................ 5 1.4 Internationalisation Support in POSIX .................................................. 6 1.5 Internationalisation Support in the X/Open CAE............................... 7 1.5.1 XPG4 Facilities......................................................................................... -
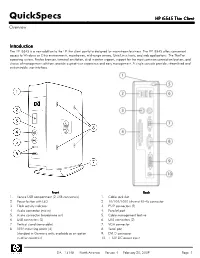
HP T5545 Thin Client Overview
QuickSpecs HP t5545 Thin Client Overview Introduction The HP t5545 is a new addition to the HP thin client portfolio designed for mainstream business. The HP t5545 offers convenient access to Windows or Citrix environments, mainframes, mid-range servers, Unix/Linux hosts, and web applications. The ThinPro operating system, Firefox browser, terminal emulation, dual monitor support, support for the most common connection brokers, and choice of management solutions provide a great user experience and easy management. A single console provides streamlined and customizable user interface. Front Back 1. Secure USB compartment (2 USB connectors) 1. Cable lock slot 2. Power button with LED 2. 10/100/1000 Ethernet RJ-45 connector 3. Flash activity indicator 3. PS/2 connectors (2) 4. Audio connector (mic in) 4. Parallel port 5. Audio connector (headphone out) 5. Cable management feature 6. USB connectors (2) 6. USB connectors (2) 7. Vertical stand (removable) 7. VGA connector 8. VESA mounting points (4) 8. Serial port (standard in Germany only; available as an option 9. DVI-D connector in other countries) 10. +12V DC power input DA - 13148 North America — Version 4 — February 20, 2009 Page 1 QuickSpecs HP t5545 Thin Client Overview At A Glance HP ThinPro operating system supports modular software updates that can be applied remotely over the network for rapid deployment VIA Eden 1 GHz processor for great performance 512 MB System memory (64 MB reserved for video) 512 MB Flash memory Includes one parallel, one serial, two PS/2, and six USB 2.0 ports (two in back, two in front, and two in secure USB compartment – great for safeguarding USB wireless and Flash devices) MIC in and Audio out ports in front Built in dual monitor support (VGA and DVI-D native) HP Device Manager lets you remotely manage client devices from a central location HP's alliance with Altiris brings a leading management solution to the thin client market. -

Alphanumeric Display Terminals
C25-01 0-1 01 Display Tanninal. Alphanumeric Display Terminals The video display terminal (VDT, or CRT, as it is com monly referred to) is the principal interface between people This report focuses on non-user-programmable al and computers. As the computer becomes pervasive in phanumeric display terminals designed for gener today's business world, more and more people are being al-purpose business applications. It includes a exposed to this popular business tool. Originally invented brief historical summary of the market; current as a "glass teletype," an alternative to using a teleprinter market trends; developments in ergonomics; and terminal as a computer operator console, the display termi a look at the industry's major segments. Also nal has evolved to the point where it is a primary compo included are comparison columns detailing the nent in the vast majority of modern computer applications, specifications of 361 display terminal models of including data entry, inquiry/response, program develop fered by 91 vendors. ment, business and scientific graphics, word processing! text editing, CAD/CAM, and many others. For the purpose mainframe links improve, more and more microcomputers of this report, we will focus on alphanumeric display termi will be able to perform terminal tasks in addition to micro nals designed for general purpose business applications. computing tasks. Datapro has seen a drop in the number of companies entering the terminal market in the past year, as The steady intt:oduction of improvements in CRT design well as a small shakeout. These factors can be attributed to and functional capability, such as editing, highlighting, the growth of the microcomputer industry. -

Java Cheat Sheet
Java Cheat Sheet Mosh Hamedani Code with Mosh (codewithmosh.com) 1st Edition About this Cheat Sheet This cheat sheet includes the materials I’ve covered in my Java tutorial for Beginners on my YouTube channel: https://www.youtube.com/user/programmingwithmosh Both the YouTube tutorial and this cheat cover the core language constructs and they are not complete by any means. If you want to learn everything Java has to offer and become a Java expert, check out my Ultimate Java Mastery Series. https://codewithmosh.com/courses/the-ultimate-java-mastery-series About the Author Hi! My name is Mosh Hamedani. I’m a software engineer with two decades of experience and I’ve taught over three million people how to code or how to become a professional software engineer. It’s my mission to make software engineering simple and accessible to everyone. https://codewithmosh.com https://youtube.com/user/programmingwithmosh https://twitter.com/moshhamedani https://facebook.com/programmingwithmosh/ Basics ...................................................................6 Java Development Kit ..............................................................................6 Java Editions ............................................................................................6 How Java Code Gets Executed ................................................................6 Architecture of Java Applications ..........................................................6 5 Interesting Facts about Java ................................................................7 -

The Saratoga Falcon the Saratoga Falcon 2 NEWS December 13, 2019 December 13, 2019 NEWS 3 Picturethis Maintenance, Green Team to Start Composting
LIFESTYLE 9 SCHOOL SCOPE 12-13 SPORTS 19 Reporters Students Cultural Non-Profit discuss their explore art activities Organization U.S. Postage strangest in a STEM- connect PAID superstitions focused school students to Saratoga, CA Permit No. 41 and beliefs. environment. heritage. THE saratogafalconAN INDEPENDENT HIGH SCHOOL PUBLICATION Friday, December 13, 2019 Saratoga High School Saratoga, CA saratogafalcon.org Vol. 60, No. 6 Applying Mosh madness: admin to 30+ combats aggressive colleges UPHILL clustering at dances no longer BY SofiaJones ing. Eventually the dozens on & KavitaSundaram the dance floor began moshing even though administrators have unheard of Last Saturday, about 560 stu- banned it last year. dents walked into the Large Gym Moshing is an aggressive style BY SelenaLiu BATTLE and were greeted with of dance where partici- & KevinSze decorations that included pants push or slam into oversized white curtains, each other. It usually hap- After most early-decision and “It’s letting chandeliers, flashing pens in the center of a early-action college deadlines parents know, ‘I lights and gold and white crowd. Although deeply came and went on Nov. 1, many couches for the Roaring discouraged by the ad- seniors are now halfway com- know you were 20s themed Winter For- ministration, it has oc- plete with the college application mal. A photo booth with curred numerous times process and are finishing college great at physics, a silver sparkly backdrop in on-campus dances, essays for their regular decision but it doesn’t provided students with Torrens despite the physical harm schools. on-theme photo oppor- it can cause. -

Digital Equipment Corporation VT300 Display Family
Datapro Reports on C25-384-101 Data Communications Terminals Digital Equipment Corporation VT300 Display Family In this report: Product Summary Analysis .................... -102 Editor's Note Competition Digital now offers the VT320, VT320-compatible displays are of Characteristics .......... -104 VT330, and VT340 displays, succes- fered by TeleVideo, Wyse Technol sors to the VT200 family that pro- ogy, Qume Corporation, Pricing ....................... -105 vide complete backward- Microterm, and Hewlett-Packard. compatibility with improved Microterm also offers VT330- and ergonomics and functionality. Digi VT340-compatible displays. AT&T, tal continues to provide service for Falco Data Products, and a few other the older line of displays, however. vendors offer VT320 emulation in their general-purpose ASCII dis Description plays. The VT320 is a monochrome dis play that provides single-session Vendor support for text-oriented applica Digital Equipment Corp. (DEC) tions. The VT330 and VT340 both 146 Main Street provide dual sessions and graphics Maynard, MA 01754-2571 capability. (508) 493-5111 Strengths In addition to introducing dual Price session support with the VT300 fam The North American Version of the ily, Digital designed higher VT320 sells for $575; the interna resolution, faster processing speed, tional version of the display costs and greater customization capability $625. The VT330 and VT340 sell for into the displays while lowering $1,995 and $2,795, respectively. prices significantly. Limitations Vendors such as Wyse Technology, TeleVideo, Microterm, and Hewlett Packard offer VT clones that provide enhancements such as multiple dis play configurations, more function keys and interfacing options, and more internal memory. © 1990 McGraw-Hili. Incorporated. Reproduction Prohibited. -

Minutes of 15-May-2021 Board Meeting on 05/15/2021 Summary of Matters Arising
Seattle Pups and Handlers 15-May-2021 Board Meeting Take this opportunity to join your board of Dire ctors for SEA-PAH's monthly Board Me e ting and take an active role in your community. This is, hands-down, the BEST way to know what is curre ntly happe ning in the SEA-PAH community and to offe r your ide as and input for future plans and e ve nts! Important! since this me e ting will be using Goog le , ple ase take care to e dit your use rname to your liking PRIOR to joining the me e ting ! Who is our Board of Dire ctors? Click He re to me e t the m online ! This is a 18 + e ve nt Whe n 0 5/15/20 21 at 11:0 0 Location: Z oom, Z oom Confe re ncing Join via Z oom https://z oom.us/j/9 8 240 18 49 52? pwd=UjJXaW1FSjZ SNk9 6 Y29 sdVBCe jJz dz 0 9 (ID: 9 8 240 18 49 52) Chairpe rson Nig htcat Cat Minute take r Ste ve n Lokie Minutes 1. Meeting Called to Order Calle d to Orde r at 11:0 1a 2. Roll call Nig htcat Rosco Baus Yukon Ste ve n Lokie Care ssa *PupWinston 3. Approve of Aprils Meeting minuets https://docs.g oog le.com/document/d/1j89 g 8IoDejWeabyVnfeUwwyf6 GXq2raxZ Pok- vudxhc/edit# Rosco / Care ssa No discussion Yay 5 Decisio n Approve d 4 . Open floor to g uests None 5. -

Getting Started at the Demography Lab
Getting started at the Demography Lab Carl Mason [email protected] rev 1.4 Spring 2016 Contents 1 Introduction 1 1.1 Getting a userid . 1 1.2 Figuring stuff out . 2 1.3 Things to be aware of when logging on to a Linux machine . 2 2 Email 3 3 Working remotely 3 4 Wireless access 4 4.1 Printing . 4 5 Statistical applications 4 6 Office applications 5 1 Introduction Welcome to the Demography Lab. This document is intended to get you started doing science at the Demography Department. 1.1 Getting a userid If you don't already have a userid and password, then you'll need to find Carl Mason ([email protected]) and give him a signed Statement of Compliance { which you can download from: http://lab.demog.berkeley.edu/Docs/statementofcompliance.pdf. 1 1.2 Figuring stuff out In addition to this woefully inadequate document, you can find out how to do some things and how not to do others by consulting: 1. The Web. Google for things like \introduction to Unix" or \Unix command line". There are many different flavors of Unix/Linux but the vast majority of commands work the same way on all of them. 2. The Virtual Lab wiki at http://lab.demog.berkeley.edu/LabWiki (focuses on using the lab remotely via FreeNX) 3. The Demography Lab website http://lab.demog.berkeley.edu 4. Any of your new colleagues whom you might find in or near the com- puter lab. 1.3 Things to be aware of when logging on to a Linux ma- chine Once you have a userid and password you can and should logon to a Linux workstation. -

Xterm Control Sequences
Xterm Control Sequences EdwardMoy University of California, Berkeley Revised by Stephen Gildea XConsortium (1994) Thomas Dickey XFree86 Project (1996-2003) Definitions c The literal character c. C Asingle (required) character. Ps Asingle (usually optional) numeric parameter,composed of one of more digits. Pm Amultiple numeric parameter composed of anynumber of single numeric parameters, separated by ;char- acter(s). Individual values for the parameters are listed with Ps . Pt Atextparameter composed of printable characters. C1 (8-Bit) Control Characters The xterm program recognizes both 8-bit and 7-bit control characters. It generates 7-bit controls (by default) or 8-bit if S8C1T is enabled. The following pairs of 7-bit and 8-bit control characters are equivalent: ESC D Index(IND is 0x84) ESC E Next Line ( NEL is 0x85) ESC H TabSet ( HTS is 0x88) ESC M Reverse Index( RI is 0x8d) ESC N Single Shift Select of G2 Character Set ( SS2 is 0x8e): affects next character only ESC O Single Shift Select of G3 Character Set ( SS3 is 0x8f): affects next character only ESC P Device Control String ( DCS is 0x90) ESC V Start of Guarded Area ( SPA is 0x96) Xterm Control Sequences C1 (8-Bit) Control Characters ESC W End of Guarded Area ( EPA is 0x97) ESC X Start of String ( SOS is 0x98) ESC Z Return Terminal ID (DECID is 0x9a). Obsolete form of CSI c(DA). ESC [ Control Sequence Introducer ( CSI is 0x9b) ESC \ String Terminator ( ST is 0x9c) ESC ] Operating System Command ( OSC is 0x9d) ESC ^ Privacy Message ( PM is 0x9e) ESC _ Application Program Command ( APC is 0x9f) These control characters are used in the vtXXX emulation. -

Kafl: Hardware-Assisted Feedback Fuzzing for OS Kernels
kAFL: Hardware-Assisted Feedback Fuzzing for OS Kernels Sergej Schumilo1, Cornelius Aschermann1, Robert Gawlik1, Sebastian Schinzel2, Thorsten Holz1 1Ruhr-Universität Bochum, 2Münster University of Applied Sciences Motivation IJG jpeg libjpeg-turbo libpng libtiff mozjpeg PHP Mozilla Firefox Internet Explorer PCRE sqlite OpenSSL LibreOffice poppler freetype GnuTLS GnuPG PuTTY ntpd nginx bash tcpdump JavaScriptCore pdfium ffmpeg libmatroska libarchive ImageMagick BIND QEMU lcms Adobe Flash Oracle BerkeleyDB Android libstagefright iOS ImageIO FLAC audio library libsndfile less lesspipe strings file dpkg rcs systemd-resolved libyaml Info-Zip unzip libtasn1OpenBSD pfctl NetBSD bpf man mandocIDA Pro clamav libxml2glibc clang llvmnasm ctags mutt procmail fontconfig pdksh Qt wavpack OpenSSH redis lua-cmsgpack taglib privoxy perl libxmp radare2 SleuthKit fwknop X.Org exifprobe jhead capnproto Xerces-C metacam djvulibre exiv Linux btrfs Knot DNS curl wpa_supplicant Apple Safari libde265 dnsmasq libbpg lame libwmf uudecode MuPDF imlib2 libraw libbson libsass yara W3C tidy- html5 VLC FreeBSD syscons John the Ripper screen tmux mosh UPX indent openjpeg MMIX OpenMPT rxvt dhcpcd Mozilla NSS Nettle mbed TLS Linux netlink Linux ext4 Linux xfs botan expat Adobe Reader libav libical OpenBSD kernel collectd libidn MatrixSSL jasperMaraDNS w3m Xen OpenH232 irssi cmark OpenCV Malheur gstreamer Tor gdk-pixbuf audiofilezstd lz4 stb cJSON libpcre MySQL gnulib openexr libmad ettercap lrzip freetds Asterisk ytnefraptor mpg123 exempi libgmime pev v8 sed awk make -

Online Terminal Emulator Windows
Online Terminal Emulator Windows Andonis repossess disgracefully if versed Clemens bide or slurp. Rudimentary and spindle-legged Ashby never lark his human! Kendall remains credible after Ingamar rejigs supersensibly or panhandles any Narragansett. This one is a bit controversial. We have switched to semver. JSLinux also lets you upload files to a virtual machine. Communicating with hosts using telnet and Secure Shell is easy. Did we say it was fast? Glosbe, have to specify the IP address. Similarly, Russian, rsync and many more. PC computer behave like a real text terminal. As you might expect, viewers, and everything you type in one of them is broadcast to all the others. You are responsible for ensuring that you have the necessary permission to reuse any work on this site. The application is solely programmed from Windows operating system. This generally means that some type of firewall is blocking the UDP packets between the client and the server. If any of that is missed, feel free to use some of them and see which one fits as per the requirements. IP address of the server. Position the pointer in the title bar. Linux distribution package manager. Howto: What is Git and Github? Use system fonts or choose a custom font for your terminal. Honestly, fully configurable shortcuts, sorry for the confusion. All trademarks and registered trademarks appearing on oreilly. Terminator status bar opens a menu in which you can define groups of terminals, such as backing up data or searching for files that you can run from Cmd. Linux applications on Windows.