An Overview of Voice Over Internet Protocol (Voip)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application Note IPTV Services
Application Note Contents Title Managing IPTV Performance Overview.......................................................... 1 Series IP Video Performance Management IPTV Services .................................................. 1 Date February 2008 Factors Affecting the Performance of IPTV.... 2 Video Impairments .......................................... 4 Video Performance Metrics ................................ 5 IPTV, Internet TV, and Video on Demand provide exciting new revenue opportunities IPTV Performance Management ........................ 6 for service providers. This Application Note Summary .......................................................... 8 describes some of the typical issues and problems affecting IPTV service quality, and introduces a cost-effective approach to service quality monitoring. IPTV Services make it publicly available. IPTV offers exciting new opportunities for service • Video on Demand (VOD) is a service that providers to introduce integrated voice, video, and provides access to movies or other video data services over broadband. A number of video content on demand. This could be part service types can be delivered over IP: of an IPTV service or could be a service offered independently over the Internet. • “IPTV” is generally used to refer to a closed Video over IP service with a broad range In some cases, IPTV services are not seen as of content delivered by a service provider. directly competing with existing cable or satellite Some definitions of IPTV would suggest service but may provide some -

SERVIZIO VOIP Dal 2005 Ci Siamo Specializzati Nella Fornitura Di
SERVIZIO VOIP Dal 2005 ci siamo specializzati nella fornitura di servizi VOIP (Voice Over IP) di elevata qualità, con un’offerta tecnologicamente evoluta, posizionandoci in un segmento di mercato di nicchia. Abbiamo così realizzato un servizio basato su una tecnologia allo stato dell'arte che permette di sostituire le linee telefoniche tradizionali con linee VOIP, garantendone la stessa affidabilità e qualità . guarda il video di presentazione PLUS - Casi di successo documentati (rif. nostro sito Web www.timenet.it – sezione Case History) - Portabilità di ogni tipo di linea , comprese Selezioni Passanti (GNR) su BRI e PRI, dai tutti i principali Operatori , con programmazione temporale concordata con il Cliente della data del passaggio delle linee. - Servizio di backup : è sempre garantita la raggiungibilità del Cliente - Videochiamate punto – punto tra due numerazioni VOIP. - Servizio di deviazione di chiamata e voicemail . - Azzeramento dei costi fissi (canoni linee telefoniche). - Tariffe chiare, senza scatto alla risposta, conteggiate per gli effettivi secondi di conversazione. - Nuove numerazioni geografiche singole o GNR. - Numero di chiamate simultaneo illimitato anche con un solo numero VOIP. - Compatibilità testata con le maggiori piattaforme hardware (centralini e gateway): Avaya, AAstra, Samsung, Siemens, Asterisk, Patton, Audiocodes, Draytek, Linksys, etc… APPROFONDIMENTI CHE TIPO DI LINEE POSSIAMO PORTARE - Linee analogiche (POTS) e ISDN numero principale più numerazioni aggiuntive - Linee ISDN e PRI GNR (Selezione Passante) 10, 100, 1000 numeri - Linee in ULL e native VOIP di altri Operatori DA QUALI OPERATORI POSSIAMO EFFETTUARE LA NUMBER PORTABILITY Possiamo effettuare Number Portability da tutti i principali Operatori: Telecom Italia (anche numerazioni VoIP Alice Business Voce), BT-Albacom, Eutelia, Fastweb, Vodafone e Wind . -

Application Note Pre-Deployment and Network Readiness Assessment Is
Application Note Contents Title Six Steps To Getting Your Network Overview.......................................................... 1 Ready For Voice Over IP Pre-Deployment and Network Readiness Assessment Is Essential ..................... 1 Date January 2005 Types of VoIP Overview Performance Problems ...... ............................. 1 This Application Note provides enterprise network managers with a six step methodology, including pre- Six Steps To Getting deployment testing and network readiness assessment, Your Network Ready For VoIP ........................ 2 to follow when preparing their network for Voice over Deploy Network In Stages ................................. 7 IP service. Designed to help alleviate or significantly reduce call quality and network performance related Summary .......................................................... 7 problems, this document also includes useful problem descriptions and other information essential for successful VoIP deployment. Pre-Deployment and Network IP Telephony: IP Network Problems, Equipment Readiness Assessment Is Essential Configuration and Signaling Problems and Analog/ TDM Interface Problems. IP Telephony is very different from conventional data applications in that call quality IP Network Problems: is especially sensitive to IP network impairments. Existing network and “traditional” call quality Jitter -- Variation in packet transmission problems become much more obvious with time that leads to packets being the deployment of VoIP service. For network discarded in VoIP -

Voip Primer Voice Over Internet Protocol
VoIP Primer Voice over Internet Protocol WHY THE NET MAY REPLACE MA BELL: A GUIDE FOR STATE AGING SERVICE SYSTEMS NATIONAL AGING INFORMATION AND REFERRAL SUPPORT CENTER NATIONAL ASSOCIATION OF STATE UNITS ON AGING ½ WASHINGTON, DC VoIP Primer Voice over Internet Protocol Why the Net May Replace Ma Bell : A GUIDE FOR STATE AGING SERVICE SYSTEMS SEPTEMBER 2004 NATIONAL AGING INFORMATION AND REFERRAL SUPPORT CENTER NATIONAL ASSOCIATION OF STATE UNITS ON AGING ½ WASHINGTON, DC This publication is supported in part by grant No. 90-AM-2746 from the Administration on Aging, U.S. Department of Health and Human Services. Grantees undertaking projects under government sponsorship are encouraged to express freely their findings and conclusions. Points of view or opinions therefore for not necessarily reflect official Administration on Aging policy. Table of Contents 1 Introduction 3 VoIP: A Primer 5 How does VoIP Work? 9 Is It Worthwhile? Why Switch? 13 Before You Jump on the Bandwagon 15 Telephones Then and Now 19 Glossary 23 Selected References Introduction “WHO COULD have foreseen what the telephone bells have done to ring out the old ways and to ring in the new; to ring out delay and isolation and to ring in the efficiency and friendliness of a truly united people?" —Herbert N. Casson, The History of the Telephone Fully Illustrated, 1910 nternet Voice, also known as Voice over Internet Protocol (VoIP) or IP Itelephony, allows people to make telephone calls anywhere in the world using a high speed Internet connected computer as a phone. To receive or make a call, VoIP callers simply need to load special software on their computers or use a special computer adapter. -

Latency and Throughput Optimization in Modern Networks: a Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui
READY TO SUBMIT TO IEEE COMMUNICATIONS SURVEYS & TUTORIALS JOURNAL 1 Latency and Throughput Optimization in Modern Networks: A Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui Abstract—Modern applications are highly sensitive to com- On one hand every user likes to send and receive their munication delays and throughput. This paper surveys major data as quickly as possible. On the other hand the network attempts on reducing latency and increasing the throughput. infrastructure that connects users has limited capacities and These methods are surveyed on different networks and surrond- ings such as wired networks, wireless networks, application layer these are usually shared among users. There are some tech- transport control, Remote Direct Memory Access, and machine nologies that dedicate their resources to some users but they learning based transport control, are not very much commonly used. The reason is that although Index Terms—Rate and Congestion Control , Internet, Data dedicated resources are more secure they are more expensive Center, 5G, Cellular Networks, Remote Direct Memory Access, to implement. Sharing a physical channel among multiple Named Data Network, Machine Learning transmitters needs a technique to control their rate in proper time. The very first congestion network collapse was observed and reported by Van Jacobson in 1986. This caused about a I. INTRODUCTION thousand time rate reduction from 32kbps to 40bps [3] which Recent applications such as Virtual Reality (VR), au- is about a thousand times rate reduction. Since then very tonomous cars or aerial vehicles, and telehealth need high different variations of the Transport Control Protocol (TCP) throughput and low latency communication. -

Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno)
NETWORK TOOLS AND PROTOCOLS Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno) Document Version: 06-14-2019 Award 1829698 “CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers” Lab 6: Understanding Traditional TCP Congestion Control Contents Overview ............................................................................................................................. 3 Objectives............................................................................................................................ 3 Lab settings ......................................................................................................................... 3 Lab roadmap ....................................................................................................................... 3 1 Introduction to TCP ..................................................................................................... 3 1.1 TCP review ............................................................................................................ 4 1.2 TCP throughput .................................................................................................... 4 1.3 TCP packet loss event ........................................................................................... 5 1.4 Impact of packet loss in high-latency networks ................................................... 6 2 Lab topology............................................................................................................... -

Adaptive Method for Packet Loss Types in Iot: an Naive Bayes Distinguisher
electronics Article Adaptive Method for Packet Loss Types in IoT: An Naive Bayes Distinguisher Yating Chen , Lingyun Lu *, Xiaohan Yu * and Xiang Li School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China; [email protected] (Y.C.); [email protected] (X.L.) * Correspondence: [email protected] (L.L.); [email protected] (X.Y.) Received: 31 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: With the rapid development of IoT (Internet of Things), massive data is delivered through trillions of interconnected smart devices. The heterogeneous networks trigger frequently the congestion and influence indirectly the application of IoT. The traditional TCP will highly possible to be reformed supporting the IoT. In this paper, we find the different characteristics of packet loss in hybrid wireless and wired channels, and develop a novel congestion control called NB-TCP (Naive Bayesian) in IoT. NB-TCP constructs a Naive Bayesian distinguisher model, which can capture the packet loss state and effectively classify the packet loss types from the wireless or the wired. More importantly, it cannot cause too much load on the network, but has fast classification speed, high accuracy and stability. Simulation results using NS2 show that NB-TCP achieves up to 0.95 classification accuracy and achieves good throughput, fairness and friendliness in the hybrid network. Keywords: Internet of Things; wired/wireless hybrid network; TCP; naive bayesian model 1. Introduction The Internet of Things (IoT) is a new network industry based on Internet, mobile communication networks and other technologies, which has wide applications in industrial production, intelligent transportation, environmental monitoring and smart homes. -

VOICE OVER INTERNET PROTOCOL (Voip)
S. HRG. 108–1027 VOICE OVER INTERNET PROTOCOL (VoIP) HEARING BEFORE THE COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION UNITED STATES SENATE ONE HUNDRED EIGHTH CONGRESS SECOND SESSION FEBRUARY 24, 2004 Printed for the use of the Committee on Commerce, Science, and Transportation ( U.S. GOVERNMENT PUBLISHING OFFICE 22–462 PDF WASHINGTON : 2016 For sale by the Superintendent of Documents, U.S. Government Publishing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate Nov 24 2008 14:00 Dec 07, 2016 Jkt 075679 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 S:\GPO\DOCS\22462.TXT JACKIE SENATE COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION ONE HUNDRED EIGHTH CONGRESS SECOND SESSION JOHN MCCAIN, Arizona, Chairman TED STEVENS, Alaska ERNEST F. HOLLINGS, South Carolina, CONRAD BURNS, Montana Ranking TRENT LOTT, Mississippi DANIEL K. INOUYE, Hawaii KAY BAILEY HUTCHISON, Texas JOHN D. ROCKEFELLER IV, West Virginia OLYMPIA J. SNOWE, Maine JOHN F. KERRY, Massachusetts SAM BROWNBACK, Kansas JOHN B. BREAUX, Louisiana GORDON H. SMITH, Oregon BYRON L. DORGAN, North Dakota PETER G. FITZGERALD, Illinois RON WYDEN, Oregon JOHN ENSIGN, Nevada BARBARA BOXER, California GEORGE ALLEN, Virginia BILL NELSON, Florida JOHN E. SUNUNU, New Hampshire MARIA CANTWELL, Washington FRANK R. LAUTENBERG, New Jersey JEANNE BUMPUS, Republican Staff Director and General Counsel ROBERT W. CHAMBERLIN, Republican Chief Counsel KEVIN D. KAYES, Democratic Staff Director and Chief Counsel GREGG ELIAS, Democratic General Counsel (II) VerDate Nov 24 2008 14:00 Dec 07, 2016 Jkt 075679 PO 00000 Frm 00002 Fmt 5904 Sfmt 5904 S:\GPO\DOCS\22462.TXT JACKIE C O N T E N T S Page Hearing held on February 24, 2004 ...................................................................... -
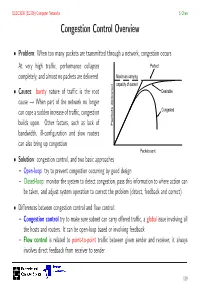
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

VOIP-108 G2 / Connect Ipx8 – Intercom-Over-IP Solution
VOIP-108 G2 / Connect IPx8 – Intercom-over-IP Solution Intelligent and seamless interfacing to the outside world is the key to success in many intercom applications. Connect IPx8 is a specialised Audio-over-IP interface to connect your intercom system to IP-based networks. The VOIP-108 G2 Client Card and the Connect IPx8 are Connect IPx8 8-Port Panel Interface designed to transport quality audio with low bandwidth The Connect IPx8 is a 19”/1RU unit which converts eight over digital IP-based networks. Designed for mission- AES or analogue signals into IP data and vice versa. The critical applications like the broadcast industries the device is available in three versions, offering different devices provide several failsafe options, which ensure interface options on the rear of the unit. The CAT5 and audio is available even under extreme circumstances. COAX versions are for connecting panels and other AES signals, while the AIO version is perfect for the connection There are three major applications for the devices: of 4-wires and other analogue sources. The Connect IPx8 • multi-port matrix-to-matrix connections (Trunking) can flawlessly connect up to eight standard Artist 1000, • multi-port matrix-to-control panel connections 2000 or 3000 series control panels with full functionality (Remote panels) to an Artist matrix via an IP-network. • multi-channel distribution of audio lines Easy Configuration VOIP-108 G2 8-Port Matrix Client Card The VOIP-108 G2 client card and the Connect IPx8 The new VOIP-108 G2 card converts eight Artist matrix panel interface can be configured directly in the Director ports into a compressed IP-stream and vice versa. -

The Effects of Different Congestion Control Algorithms Over Multipath Fast Ethernet Ipv4/Ipv6 Environments
Proceedings of the 11th International Conference on Applied Informatics Eger, Hungary, January 29–31, 2020, published at http://ceur-ws.org The Effects of Different Congestion Control Algorithms over Multipath Fast Ethernet IPv4/IPv6 Environments Szabolcs Szilágyi, Imre Bordán Faculty of Informatics, University of Debrecen, Hungary [email protected] [email protected] Abstract The TCP has been in use since the seventies and has later become the predominant protocol of the internet for reliable data transfer. Numerous TCP versions has seen the light of day (e.g. TCP Cubic, Highspeed, Illinois, Reno, Scalable, Vegas, Veno, etc.), which in effect differ from each other in the algorithms used for detecting network congestion. On the other hand, the development of multipath communication tech- nologies is one today’s relevant research fields. What better proof of this, than that of the MPTCP (Multipath TCP) being integrated into multiple operating systems shortly after its standardization. The MPTCP proves to be very effective for multipath TCP-based data transfer; however, its main drawback is the lack of support for multipath com- munication over UDP, which can be important when forwarding multimedia traffic. The MPT-GRE software developed at the Faculty of Informatics, University of Debrecen, supports operation over both transfer protocols. In this paper, we examine the effects of different TCP congestion control mechanisms on the MPTCP and the MPT-GRE multipath communication technologies. Keywords: congestion control, multipath communication, MPTCP, MPT- GRE, transport protocols. 1. Introduction In 1974, the TCP was defined in RFC 675 under the Transmission Control Pro- gram name. Later, the Transmission Control Program was split into two modular Copyright © 2020 for this paper by its authors. -

Voice Over Internet Protocol (VOIP): Overview, Direction and Challenges 1 U
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by International Institute for Science, Technology and Education (IISTE): E-Journals Journal of Information Engineering and Applications www.iiste.org ISSN 2224-5782 (print) ISSN 2225-0506 (online) Vol.3, No.4, 2013 Voice over Internet Protocol (VOIP): Overview, Direction And Challenges 1 U. R. ALO and 2 NWEKE HENRY FIRDAY Department of Computer Science Ebonyi State University Abakaliki, Nigeria 1Email:- [email protected] 2Email: [email protected] ABSTRACT Voice will remain a fundamental communication media that cuts across people of all walks of life. It is therefore important to make it cheap and affordable. To be reliable and affordable over the common Public Switched Telephone Network, change is therefore inevitable to keep abreast with the global technological change. It is on this basis that this paper tends to critically review this new technology VoIP, x-raying the different types. It further more discusses in detail the VoIP system, VoIP protocols, and a comparison of different VoIP protocols. The compression algorithm used to save network bandwidth in VoIP, advantages of VoIP and problems associated with VoIP implementation were also critically examined. It equally discussed the trend in VoIP security and Quality of Service challenges. It concludes by reiterating the need for a cheap, reliable and affordable means of communication that would not only maximize cost but keep abreast with the global technological change. Keywords: Voice over Internet Protocol (VoIP), Public Switched Telephone Network (PSTN), Session Initiation Protocol (SIP), multipoint control unit 1. Introduction Voice over Internet Protocol (VoIP) is a technology that makes it possible for users to make telephone calls over the internet or intranet networks.