Evaluation and Selection of Case Tools: A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Command Line Interface
Command Line Interface Squore 21.0.2 Last updated 2021-08-19 Table of Contents Preface. 1 Foreword. 1 Licence. 1 Warranty . 1 Responsabilities . 2 Contacting Vector Informatik GmbH Product Support. 2 Getting the Latest Version of this Manual . 2 1. Introduction . 3 2. Installing Squore Agent . 4 Prerequisites . 4 Download . 4 Upgrade . 4 Uninstall . 5 3. Using Squore Agent . 6 Command Line Structure . 6 Command Line Reference . 6 Squore Agent Options. 6 Project Build Parameters . 7 Exit Codes. 13 4. Managing Credentials . 14 Saving Credentials . 14 Encrypting Credentials . 15 Migrating Old Credentials Format . 16 5. Advanced Configuration . 17 Defining Server Dependencies . 17 Adding config.xml File . 17 Using Java System Properties. 18 Setting up HTTPS . 18 Appendix A: Repository Connectors . 19 ClearCase . 19 CVS . 19 Folder Path . 20 Folder (use GNATHub). 21 Git. 21 Perforce . 23 PTC Integrity . 25 SVN . 26 Synergy. 28 TFS . 30 Zip Upload . 32 Using Multiple Nodes . 32 Appendix B: Data Providers . 34 AntiC . 34 Automotive Coverage Import . 34 Automotive Tag Import. 35 Axivion. 35 BullseyeCoverage Code Coverage Analyzer. 36 CANoe. 36 Cantata . 38 CheckStyle. .. -
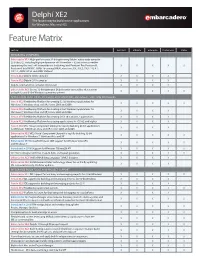
Delphi XE2 Feature Matrix
Delphi® XE2 The fastest way to build native applications for Windows, Mac and iOS Feature Matrix Feature Architect Ultimate Enterprise Professional Starter INTEGRATED COMPILERS Enhanced in XE2! High-performance 32-bit optimizing Delphi® native code compiler 23.0 (dcc32), including High performance x86 Assembler – 32-bit inline assembler supporting the Intel® x86 instruction set (including Intel Pentium® Pro, Pentium III, X X X X X Pentium 4, Intel MMX™, SIMD, Streaming SIMD Extensions, SSE, SSE2, SSE3, SSE 4.1, SSE 4.2, AMD SSE4A and AMD® 3DNow!® New in XE2! Delphi 64-bit compiler X X X X New in XE2! Delphi OS X compiler X X X X Delphi command line compiler (dcc32.exe) X X X X Enhanced in XE2! Create 32-bit optimized Delphi native executables that can run X X X X X on both 32 and 64-bit Windows operating systems APPLICATION PLATFORMS, INTEGRATED FRAMEWORKS, DESIGNERS, SDKS AND INSTALLERS New in XE2! FireMonkey Platform for creating 32-bit Windows applications for X X X X X Windows 7, Windows Vista and XP; Server 2003 and 2008. New in XE2! FireMonkey Platform for creating 64-bit Windows applications for X X X X Windows 7, Windows Vista and XP; Server 2003 and 2008. New in XE2! FireMonkey Platform for creating OS X 10.6 and 10.7 applications X X X X New in XE2! FireMonkey Platform for creating applications for iOS 4.2 and higher X X X X New in XE2! VCL (Visual Component Library) for rapidly building 64-bit applications X X X X for Windows 7,Windows Vista and XP; Server 2003 and 2008. -

Analysis of Devops Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters
International Journal of Computer Applications (0975 – 8887) Volume 181 – No. 33, December 2018 Analysis of DevOps Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters R. Vaasanthi V. Prasanna Kumari, PhD S. Philip Kingston Research Scholar, HOD, MCA Project Manager SCSVMV University Rajalakshmi Engineering Infosys, Mahindra City, Kanchipuram College, Chennai Chennai ABSTRACT cloud. Now-a-days more than ever, DevOps [Development + Operations] has gained a tremendous amount of attention in 2. SCM software industry. Selecting the tools for building the DevOps Source code management (SCM) is a software tool used for pipeline is not a trivial exercise as there are plethora’s of tools development, versioning and enables team working in available in market. It requires thought, planning, and multiple locations to work together more effectively. This preferably enough time to investigate and consult other plays a vital role in increasing team’s productivity. Some of people. Unfortunately, there isn’t enough time in the day to the SCM tools, considered for this study are GIT, SVN, CVS, dig for top-rated DevOps tools and its compatibility with ClearCase, Mercurial, TFS, Monotone, Bitkeeper, Code co- other tools. Each tool has its own pros/cons and compatibility op, Darcs, Endevor, Fossil, Perforce, Rational Synergy, of integrating with other tools. The objective of this paper is Source Safe, and GNU Bazaar. Table1 consists of SCM tools to propose an approach by adding weightage to each with weightage. parameter for the curated list of the DevOps tools. 3. BUILD Keywords Build is a process that enables source code to be automatically DevOps, SCM, dependencies, compatibility and pipeline compiled into binaries including code level unit testing to ensure individual pieces of code behave as expected [4]. -

Seapine ALM Reporting Platform Database Reference Guide V2016.1
Seapine ALM Data Warehouse Database Reference Guide Version 2016.1 Contents Key entities ................................................................................................................................................................... 1 Repository ................................................................................................................................................................. 1 License Server .......................................................................................................................................................... 1 QA Wizard Pro .......................................................................................................................................................... 1 Surround SCM ........................................................................................................................................................... 1 TestTrack ................................................................................................................................................................... 2 Data dictionary ............................................................................................................................................................. 5 Table: LS_AUTHENTICATION_METHOD ................................................................................................................ 5 Table: LS_EMAIL ..................................................................................................................................................... -

Visual Build Help
Visual Build Professional User's Manual Copyright © 1999-2021 Kinook Software, Inc. Contents I Table of Contents Part I Introduction 1 1 Overview ................................................................................................................................... 1 2 Why Visual................................................................................................................................... Build? 1 3 New Features................................................................................................................................... 2 Version 4 .......................................................................................................................................................... 2 Version 5 .......................................................................................................................................................... 3 Version 6 .......................................................................................................................................................... 4 Version 7 .......................................................................................................................................................... 7 Version 8 .......................................................................................................................................................... 9 Version 9 ......................................................................................................................................................... -

Third Party Licenses for Embarcadero RAD Studio XE, Delphi XE, C++Builder XE
Third Party Licenses for Embarcadero RAD Studio XE, Delphi XE, C++Builder XE This Document contains either required notices for third party software or the third party license documents under which the Separately Licensed Code is licensed. (Please note that in some cases, the license listed may differ from the license under which the latest version of the code can be obtained) Table of Contents Separately Licensed Code ............................................................................................. Microsoft® .NET framework redistributable ............................................................... Microsoft® Visual J# redistributable .......................................................................... Office UI License Agreement ...................................................................................... InstallAware Express .................................................................................................. Rave Reports ............................................................................................................. IP*Works .................................................................................................................... CodeSite .................................................................................................................... FinalBuilder ................................................................................................................ Apache Subversion ................................................................................................... -

Helix Authentication Service Administrator Guide 2021.1 May 2021 Copyright © 2020-2021 Perforce Software, Inc
Helix Authentication Service Administrator Guide 2021.1 May 2021 Copyright © 2020-2021 Perforce Software, Inc.. All rights reserved. All software and documentation of Perforce Software, Inc. is available from www.perforce.com. You can download and use Perforce programs, but you can not sell or redistribute them. You can download, print, copy, edit, and redistribute the documentation, but you can not sell it, or sell any documentation derived from it. You can not modify or attempt to reverse engineer the programs. This product is subject to U.S. export control laws and regulations including, but not limited to, the U.S. Export Administration Regulations, the International Traffic in Arms Regulation requirements, and all applicable end-use, end-user and destination restrictions. Licensee shall not permit, directly or indirectly, use of any Perforce technology in or by any U.S. embargoed country or otherwise in violation of any U.S. export control laws and regulations. Perforce programs and documents are available from our Web site as is. No warranty or support is provided. Warranties and support, along with higher capacity servers, are sold by Perforce. Perforce assumes no responsibility or liability for any errors or inaccuracies that might appear in this book. By downloading and using our programs and documents you agree to these terms. Perforce and Inter-File Branching are trademarks of Perforce. All other brands or product names are trademarks or registered trademarks of their respective companies or organizations. Contents How to use -

Analiza in Prenova Sistema Upravljanja Z Dokumentacijo V Podjetju
UNIVERZA V LJUBLJANI FAKULTETA ZA RA ČUNALNIŠTVO IN INFORMATIKO Aleksander Pahor ANALIZA IN PRENOVA SISTEMA UPRAVLJANJA Z DOKUMENTACIJO V PODJETJU Diplomsko delo na visokošolskem strokovnem študiju Mentor: dr. Mojca Ciglari č Ljubljana, 2009 I Z J A V A O A V T O R S T V U diplomskega dela Spodaj podpisani/-a ____________________________________, z vpisno številko ____________________________________, sem avtor/-ica diplomskega dela z naslovom: _________________________________________________________________________ _________________________________________________________________________ S svojim podpisom zagotavljam, da: • sem diplomsko delo izdelal/-a samostojno pod mentorstvom (naziv, ime in priimek) ___________________________________________________________________ in somentorstvom (naziv, ime in priimek) ___________________________________________________________________ • so elektronska oblika diplomskega dela, naslov (slov., angl.), povzetek (slov., angl.) ter klju čne besede (slov., angl.) identi čni s tiskano obliko diplomskega dela • soglašam z javno objavo elektronske oblike diplomskega dela v zbirki »Dela FRI«. V Ljubljani, dne ______________ Podpis avtorja/-ice:______________________ Zahvala V prvi vrsti se zahvaljujem svoji mentorici dr. Mojci Ciglari č za potrpljenje, ki ga je izkazala z menoj. Predvsem cenim to, da je bila pripravljena z nekaterimi izdelki po čakati, kar je bilo pogojeno z mojim delom, ki velikokrat ne dopuš ča, da bi se svojim ostalim obveznostim posvetil toliko, kolikor bi si zaslužile. Zahvaljujem se vsem v podjetju Hermes Softlab d.d., ki so mi vedno stali ob strani in mi pomagali odrasti strokovno, poslovno in osebno. Davorju Hvali, ki me je vzel v službo in vsem mojim nadrejenim: Alešu Pestotniku, Primožu Svetku, Mihi Urbaniji in Alešu Koširju, ki so mi zaupali vedno bolj odgovorne naloge, ki so mi omogo čile videti svet in delati na mnogih projektih in podjetjih. -

Ansys SCADE Lifecycle®
EMBEDDED SOFTWARE Ansys SCADE LifeCycle® SCADE LifeCycle is part of the Ansys Embedded Software family of products and solutions that includes modules providing unique support for application lifecycle management. This product line features requirements traceability via Application Lifecycle Management (ALM) tools, traceability from models, configuration and change management, and automatic documentation generation. SCADE LifeCycle enhances the functionalities of Ansys SCADE® tools with add-on modules that bridge SCADE solutions and Requirement Management tools or PLM/ALM (Product Lifecycle Management/ Application Lifecycle Management) tools. With SCADE LifeCycle, all systems and software teams involved in critical applications development can manage and control their design and verification activities across the full life cycle of their SCADE applications. / Requirements Traceability SCADE LifeCycle Application Lifecycle Management (ALM) Gateway provides an integrated traceability analysis solution for safety-critical design processes with SCADE Architect, SCADE Suite, SCADE Display, SCADE Solutions for ARINC 661 and SCADE Test: • Connection to ALM tools: linkage to DOORS NG, DOORS (9.6 and up) Jama Connect, Siemens Polarion, Dassault Systèmes Reqtify 2016. • Graphical creation of traceability links between requirements or other structured documents and SCADE models. • Traceability of test cases from SCADE Test Environment projects. • Bidirectional navigation across requirements and tests. • Customizable Export of SCADE artifacts to DOORS or Jama Connect. • Compliant with DO-178B, DO-178C, EN 50128, IEC 61508, ISO 26262, and IEC 60880 standards. EMBEDDED SOFTWARE / SCADE LifeCycle® // 1 / Project Documentation Generation SCADE LifeCycle Reporter automates the time-consuming creation of detailed and complete reports from SCADE Suite, SCADE Display, SCADE Architect and SCADE UA Page Creator for ARINC 661 designs through: • Generation of reports in RTF or HTML formats. -

Opinnäytetyö Ohjeet
Lappeenrannan–Lahden teknillinen yliopisto LUT School of Engineering Science Tietotekniikan koulutusohjelma Kandidaatintyö Mikko Mustonen PARHAITEN OPETUSKÄYTTÖÖN SOVELTUVAN VERSIONHALLINTAJÄRJESTELMÄN LÖYTÄMINEN Työn tarkastaja: Tutkijaopettaja Uolevi Nikula Työn ohjaaja: Tutkijaopettaja Uolevi Nikula TIIVISTELMÄ LUT-yliopisto School of Engineering Science Tietotekniikan koulutusohjelma Mikko Mustonen Parhaiten opetuskäyttöön soveltuvan versionhallintajärjestelmän löytäminen Kandidaatintyö 2019 31 sivua, 8 kuvaa, 2 taulukkoa Työn tarkastajat: Tutkijaopettaja Uolevi Nikula Hakusanat: versionhallinta, versionhallintajärjestelmä, Git, GitLab, SVN, Subversion, oppimateriaali Keywords: version control, version control system, Git, GitLab, SVN, Subversion, learning material LUT-yliopistossa on tietotekniikan opetuksessa käytetty Apache Subversionia versionhallintaan. Subversionin käyttö kuitenkin johtaa ylimääräisiin ylläpitotoimiin LUTin tietohallinnolle. Lisäksi Subversionin julkaisun jälkeen on tullut uusia versionhallintajärjestelmiä ja tässä työssä tutkitaankin, olisiko Subversion syytä vaihtaa johonkin toiseen versionhallintajärjestelmään opetuskäytössä. Työn tavoitteena on löytää opetuskäyttöön parhaiten soveltuva versionhallintajärjestelmä ja tuottaa sille opetusmateriaalia. Työssä havaittiin, että Git on suosituin versionhallintajärjestelmä ja se on myös suhteellisen helppo käyttää. Lisäksi GitLab on tutkimuksen mukaan Suomen yliopistoissa käytetyin ja ominaisuuksiltaan ja hinnaltaan sopivin Gitin web-käyttöliittymä. Näille tehtiin -

Main Brochure2.Indd
Automate your Build Process . Powerful and fl exible user interface . Automate version control, compilers, install builders, deployment, testing, notifi cations, and lots more... Dynamic build process using fl ow control, iterators, loops, and exceptions . Full debugger built in - breakpoints, variable watches, live logging . Script events for every action to customise your build process Hierarchical Logging Error Handling FinalBuilder ActionStudio . The log is presented in the same . Easily detect and handle errors during . Allows development of native FinalBuilder hierarchy as your build process your build process actions . Optionally view live log output . Exception handling actions . Includes property page designer and as the build runs include: TRY, CATCH, FINALLY code editor with syntax highlighting . Builds logs are automatically . Control the fl ow of your build process . Develop actions in VBScript, JScript, COM, archived and recover from errors or any .Net language such as C#, VB.Net or Delphi for .Net . Export the log as XML, HTML, or . Unhandled errors trigger the OnFailure Text action list . Included in all editions of FinalBuilder VSoft Technologies Pty Ltd http://www.fi nalbuilder.com ABN: 82 078 466 092 P.O. Box 126, Erindale Centre, ACT 2903, Australia salesinfo@fi nalbuilder.com Phone: +61 2 6282 7488, Fax +61 2 6282 7588 news://news.fi nalbuilder.com FinalBuilder Integrates with your version control system . Microsoft TeamSystem Use a GUI instead of XML fi les . Microsoft Visual SourceSafe . Perforce Although FinalBuilder uses an XML based fi le format, you . IBM Rational ClearCase don’t need to understand it or even look at it. The FinalBuilder . QSC Team Coherence GUI allows you to quickly and easily create a build process . -

Buyers Guide Product Listings
BUYERS GUIDE PRODUCT LISTINGS Visual Studio Magazine Buyers’ Guide Product Listings The 2009 Visual Studio Magazine Buyers’ Guide listings comprise more than 700 individual products and services, ranging from developer tooling and UI components to Web hosting and instructor-led training. Included for each product is contact and pricing information. Keep in mind that many products come in multiple SKUs and with varied license options, so it’s always a good idea to contact vendors directly for specific pricing. The developer tools arena is a vast and growing space. As such, we’re always on the prowl for new tools and vendors. Know of a product our readers might want to learn more about? E-mail us at [email protected]. BUG & FEATURE TRACKING Gemini—CounterSoft Starts at $1189 • countersoft.com • +44 (0)1753 824000 Rational ClearQuest—IBM Rational Software $1,810 • ibm.com/rational • 888-426-3774 IssueNet Intercept—Elsinore Technologies Call for price • elsitech.com • 866-866-0034 FogBugz 7.0—Fog Creek Software $199 • fogcreek.com • 888-364-2849; 212-279-2076 SilkPerformer—Borland Call for price • borland.com • 800-632-2864; 512-340-2200 OnTime 2009 Professional—Axosoft Starts at $795 for five users • axosoft.com • 800-653-0024; SourceOffSite 4.2—SourceGear 480-362-1900 $239 • sourcegear.com • 217-356-0105 Alexsys Team 2.10—Alexsys Surround SCM 2009—Seapine Software Starts at $145 • alexcorp.com • 888-880-2539; 781-279-0170 Call for price • seapine.com • 888-683-6456; 513-754-1655 AppLife DNA—Kinetic Jump Software TeamInspector—Borland