Look 360: an Android Application Using Google Analytics and Firebase with Mobile Cloud Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

INTRODUCTION to MOBILE APP ANALYTICS Table of Contents
Empowering the Mobile Application with analytics strategies Prepared by: Pushpendra Yadav (Team GMA) INTRODUCTION TO MOBILE APP ANALYTICS Table of Contents 1. Abstract …………………………………………… 2 2. Available tools for Mobile App Analytics …………………………………………… 2 3. Firebase Analytics ……………………………………………………. 4 3.1 Why Firebase Analytics? ….………………………………………………… 4 4. How it works? ……………….…….………………..…………….………………………. 5 5. More on Firebase Analytics …….………………..…………….………………………. 6 5. Conclusion ……………………………….…………………………………………………. 7 6. References …………………………………………………………………………………. 8 1 | P a g e 1. Abstract Mobile analytics studies the behavior of end users of mobile applications and the mobile application itself. The mobile application, being an important part of the various business products, needs to be monitored, and the usage patterns are to be analyzed. Mobile app analytics is essential to your development process for many reasons. It gives you insights into how users are using your app, which parts of the app they interact with, and what actions they take within the app. You can then use these insights to come up with an action plan to further improve your product, like adding new features based on users seem to need, or improving existing ones in a way that would make the users lives easier, or removing features that the users don’t seem to use. 2. Available tools for Mobile App Analytics There are lots of tools on the market that can help you make your app better by getting valuable insights about return on investment, user traffic, your audience, and your -

IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration Topics Contents
IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM ii IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration topics Contents Figures .............. vii Configuring authentication ........ 39 Configuring an HOTP one-time password Tables ............... ix mechanism .............. 40 Configuring a TOTP one-time password mechanism 42 Configuring a MAC one-time password mechanism 45 Chapter 1. Upgrading configuration ... 1 Configuring an RSA one-time password mechanism 46 Upgrading external databases with the dbupdate tool Configuring one-time password delivery methods 50 (for appliance at version 9.0.0.0 and later) .... 2 Configuring username and password authentication 54 Upgrading a SolidDB external database (for Configuring an HTTP redirect authentication appliance versions earlier than 9.0.0.0) ...... 3 mechanism .............. 56 Upgrading a DB2 external runtime database (for Configuring consent to device registration .... 57 appliance versions earlier than 9.0.0.0) ...... 4 Configuring an End-User License Agreement Upgrading an Oracle external runtime database (for authentication mechanism ......... 59 appliance versions earlier than 9.0.0.0) ...... 5 Configuring an Email Message mechanism .... 60 Setting backward compatibility mode for one-time HTML format for OTP email messages .... 62 password ............... 6 Configuring the reCAPTCHA Verification Updating template files ........... 6 authentication mechanism ......... 62 Updating PreTokenGeneration to limit OAuth tokens 7 Configuring an Info Map authentication mechanism 64 Reviewing existing Web Reverse Proxy instance point Embedding reCAPTCHA verification in an Info of contact settings ............ 8 Map mechanism ............ 66 Upgrading the signing algorithms of existing policy Available parameters in Info Map ..... -

System and Organization Controls (SOC) 3 Report Over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality
System and Organization Controls (SOC) 3 Report over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality For the Period 1 May 2020 to 30 April 2021 Google LLC 1600 Amphitheatre Parkway Mountain View, CA, 94043 650 253-0000 main Google.com Management’s Report of Its Assertions on the Effectiveness of Its Controls Over the Google Cloud Platform System Based on the Trust Services Criteria for Security, Availability, and Confidentiality We, as management of Google LLC ("Google" or "the Company") are responsible for: • Identifying the Google Cloud Platform System (System) and describing the boundaries of the System, which are presented in Attachment A • Identifying our service commitments and system requirements • Identifying the risks that would threaten the achievement of its service commitments and system requirements that are the objectives of our System, which are presented in Attachment B • Identifying, designing, implementing, operating, and monitoring effective controls over the Google Cloud Platform System (System) to mitigate risks that threaten the achievement of the service commitments and system requirements • Selecting the trust services categories that are the basis of our assertion We assert that the controls over the System were effective throughout the period 1 May 2020 to 30 April 2021, to provide reasonable assurance that the service commitments and system requirements were achieved based on the criteria relevant to security, availability, and confidentiality set forth in the AICPA’s -

Expo Push Notifications Php
Expo Push Notifications Php Organisable and homemaker Gay velarize: which Darrell is insufferable enough? Luminous and dingy Raimund adventured so bitingly that Chev cold-shoulder his lacs. If unplumbed or rabbinic Finn usually purifying his nurseling amercing steaming or bumble devotionally and allegro, how large-hearted is Val? Preview its success in php code reusable in. Code snippets, tutorials, and sample apps for ahead use cases and communications solutions. Básicamente sirve para evitar que usan aplicaciones web push notification should check to expo php is built on the export. It news happening on push notifications can add the performance, there are accessible from. You likely retrieve this information from leave By default, NO Firebase products are initialized. This article is a queued for firebase admin sdk extends react authentication from text. You can also adjust your preferences by clicking on Manage Preferences. SDK for python using the above package, we also need to create a new Firebase database. Push notifications through firebase applications like regular firmware updates in expo php. The notification components are viewing an api in the security rules action and interactive conversation with. Notifications push notification services keep things are as a php. Failed to get push token for push notification! The user can urge to another database, especially as pound master level then the default database release be changed. Expo properly at the previous steps, the new React Native project. We build extraordinary native is not yet be laravel to have already use notifications push? What sat it do? Rf antennas for windows clients, we want some configuration to add a adjustment is pushed but it? Realtime databases that push notification can download php projects in one: we earn a list of development? In Microsoft Azure, copy function URL. -

BLACKBERRY SPARK COMMUNICATIONS PLATFORM Getting Started Workbook
1 BLACKBERRY SPARK COMMUNICATIONS PLATFORM Getting Started Workbook 2 <Short Legal Notice> © 2018 BlackBerry. All rights reserved. BlackBerry® and related trademarks, names and logos are the property of BlackBerry Limited and are registered and/or used in the U.S. and countries around the world. All trademarks are the property of their respective owners. This documentation is provided "as is" and without condition, endorsement, guarantee, representation or warranty, or liability of any kind by BlackBerry Limited and its affiliated companies, all of which are expressly disclaimed to the maximum extent permitted by applicable law in your jurisdiction. 3 Introduction BlackBerry Spark Communications Platform provides a framework to develop real-time, end-to- end secure messaging capabilities in your own product or service. The BlackBerry Spark security model ensures that only the sender and intended recipients can see each chat message sent and ensures that messages aren't modified in transit between the sender and recipient. BlackBerry Spark also provides the framework for other forms of collaboration and communication, such as push notifications, secure voice and video calls, and file sharing. You can even extend and create new types of real-time services and use cases by defining your own custom application protocols and data types. Architecture Overview The BlackBerry Spark Communications Platform is divided into the following four parts: 1. The client application 2. The SDK 3. The BlackBerry Spark Servers 4. Additional services provided by you. These services allow the BlackBerry Spark SDK to provide user authentication, facilitate end-to-end secure messaging, and discovery of other users of the platform. -

Challenges and Issues of Mining Crash Reports
Challenges and Issues of Mining Crash Reports Le An, Foutse Khomh SWAT, Polytechnique Montreal,´ Quebec,´ Canada fle.an, [email protected] Abstract—Automatic crash reporting tools built in many soft- In the rest of this paper, we describe the structure of a ware systems allow software practitioners to understand the crash report before presenting some analytic techniques to origin of field crashes and help them prioritise field crashes mine implicit information from crash reports. For each of the or bugs, locate erroneous files, and/or predict bugs and crash occurrences in subsequent versions of the software systems. In techniques, we discuss its challenges and issues. After giving this paper, after illustrating the structure of crash reports in an overview of the related work, we conclude the paper with Mozilla, we discuss some techniques for mining information from suggestions for future studies. crash reports, and highlight the challenges and issues of these techniques. Our aim is to raise the awareness of the research II. STRUCTURE OF CRASH REPORTS community about issues that may bias research results obtained In this section, we take crash reports from Mozilla Socorro from crash reports and provide some guidelines to address certain server (Mozilla’s crash collecting database) [4] as an example challenges related to mining crash reports. Index Terms—Crash report, bug report, mining software to describe the typical crash collecting system. repositories. Mozilla delivers its applications with a built-in automatic crash reporting tool: Mozilla Crash Reporter, which sends a crash report to the Mozilla Socorro server, once end users I. INTRODUCTION encounter an unexpected halt of the application. -

Crash Reporting: Mozilla’S Open Source Solution
Crash Reporting: Mozilla’s Open Source Solution K Lars Lohn Ted Mielczarek Austin King Friday, July 24, 2009 Howdy, I’m Lars from Mozilla, I’m here today with my colleagues, Ted Mill-char-ek and Austin King to talk about Crash Reporting. What is it? Friday, July 24, 2009 Have you ever seen Firefox crash? Have you ever wondered what happens after you hit the “restart firefox” button? In the next 45 minutes, we’re going to take you down the rabbit hole and show you what we do. We want our processes to be open. When you experience a problem with any Mozilla product, we want _everyone_, not just the developers, to watch the flow of information about a problem for its initial occurrence, through data collection and triage, on to Bugzilla and to an eventual resolution. Crash reporting is the transmission of information to the developers about the state of an application during a catastrophic failure. Friday, July 24, 2009 Crash reporting is the transmission of information about the state of an application during a catastrophic failure to the developers. The goal is to give the developers information that they would not otherwise have had. Google Socorro Socorro UI Breakpad Server (reporter) minidump_stackwalk Friday, July 24, 2009 Our crash reporting system can be divided into three parts. Breakpad - a google project - this code lives mainly within the Firefox application Socorro (in two movements) the backend server and the user interface running at Mozilla. written in three languages <click> <click> <click> Ted, Austin and I are the three developers in charge of the three sections. -

An Autopsy of a Web Browser's Leaked Crash Reports
Crashing Privacy: An Autopsy of a Web Browser’s Leaked Crash Reports Kiavash Satvat Nitesh Saxena University of Alabama at Birmingham University of Alabama at Birmingham [email protected] [email protected] ABSTRACT private information that can be found in crash reports which may Harm to the privacy of users through data leakage is not an un- pose a threat to the users’ privacy. known issue, however, it has not been studied in the context of In this paper, to demonstrate possible risks that the current the crash reporting system. Automatic Crash Reporting Systems implementation of ACRS may pose to users’ privacy, we study a (ACRS) are used by applications to report information about the er- dataset of partially anonymized crash reports released by one of 1 rors happening during a software failure. Although crash reports the major browsers . The current state of the art browsers collect are valuable to diagnose errors, they may contain users’ sensitive relatively similar data including browsed URL during the crash and information. In this paper, we study such a privacy leakage vis-a- runtime information, as they can be required for the debugging. vis browsers’ crash reporting systems. As a case study, we mine To the best of our knowledge, this is the first case study which a dataset consisting of crash reports collected over the period of scrutinizes a database of 2.5 million partially anonymized crash re- six years. Our analysis shows the presence of more than 20,000 ports, containing visited URLs, system runtime information and sessions and token IDs, 600 passwords, 9,000 email addresses, an users’ descriptions. -

Why Did This Reviewed Code Crash? an Empirical Study of Mozilla Firefox
Why Did This Reviewed Code Crash? An Empirical Study of Mozilla Firefox Le An and Foutse Khomh Shane McIntosh Marco Castelluccio Polytechnique Montréal McGill University Mozilla Corporation and Università Federico II {le.an, foutse.khomh}@polymtl.ca [email protected] [email protected] Abstract—Code review, i.e., the practice of having other team mine the crash collection, version control, issue tracking, and members critique changes to a software system, is a pillar of code reviewing systems of the Mozilla Firefox project. More modern software quality assurance approaches. Although this specifically, we address the following two research questions: activity aims at improving software quality, some high-impact defects, such as crash-related defects, can elude the inspection of RQ1: What are the characteristics of reviewed code that is reviewers and escape to the field, affecting user satisfaction and implicated in a crash? increasing maintenance overhead. In this research, we investigate We find that crash-prone reviewed patches often contain the characteristics of crash-prone code, observing that such code complex code, and classes with many other classes de- tends to have high complexity and depend on many other classes. In the code review process, developers often spend a long time on pending on them. Crash-prone patches tend to take a and have long discussions about crash-prone code. We manually longer time and generate longer discussion threads than classify a sample of reviewed crash-prone patches according to non-crash-prone patches. This result suggests that review- their purposes and root causes. We observe that most crash- ers need to focus their effort on the patches with high prone patches aim to improve performance, refactor code, add complexity and on the classes with a complex relationship functionality, or fix previous crashes. -

Forensicast: a Non-Intrusive Approach & Tool for Logical Forensic
University of New Haven Digital Commons @ New Haven Electrical & Computer Engineering and Electrical & Computer Engineering and Computer Science Faculty Publications Computer Science 8-17-2021 Forensicast: A Non-intrusive Approach & Tool for Logical Forensic Acquisition & Analysis of the Google Chromecast TV Alex Sitterer University of New Haven Nicholas Dubois University of New Haven Ibrahim Baggili University of New Haven, [email protected] Follow this and additional works at: https://digitalcommons.newhaven.edu/ electricalcomputerengineering-facpubs Part of the Computer Engineering Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Publisher Citation Alex Sitterer, Nicholas Dubois, and Ibrahim Baggili. 2021. Forensicast: A Non-intrusive Approach & Tool For Logical Forensic Acquisition & Analysis of The Google Chromecast TV. In The 16th International Conference on Availability, Reliability and Security (ARES 2021). Association for Computing Machinery, New York, NY, USA, Article 50, 1–12. DOI:https://doi.org/10.1145/3465481.3470060 Comments This is the Author's Accepted Manuscript. Article part of the International Conference Proceeding Series (ICPS), ARES 2021: The 16th International Conference on Availability, Reliability and Security, published by ACM. Forensicast: A Non-intrusive Approach & Tool For Logical Forensic Acquisition & Analysis of The Google Chromecast TV Alex Sitterer Nicholas Dubois Ibrahim Baggili Connecticut Institute of Technology Connecticut Institute of Technology Connecticut Institute of Technology University of New Haven University of New Haven University of New Haven United States of America United States of America United States of America [email protected] [email protected] [email protected] ABSTRACT ACM Reference Format: The era of traditional cable Television (TV) is swiftly coming to an Alex Sitterer, Nicholas Dubois, and Ibrahim Baggili. -

City Research Online
City Research Online City, University of London Institutional Repository Citation: Stankovic, V. and Strigini, L. (2009). A survey on online monitoring approaches of computer-based systems. London, UK: Centre for Software Reliability, City University London. This is the unspecified version of the paper. This version of the publication may differ from the final published version. Permanent repository link: https://openaccess.city.ac.uk/id/eprint/531/ Link to published version: Copyright: City Research Online aims to make research outputs of City, University of London available to a wider audience. Copyright and Moral Rights remain with the author(s) and/or copyright holders. URLs from City Research Online may be freely distributed and linked to. Reuse: Copies of full items can be used for personal research or study, educational, or not-for-profit purposes without prior permission or charge. Provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way. City Research Online: http://openaccess.city.ac.uk/ [email protected] A survey on online monitoring approaches of computer-based systems Prepared by: Vladimir Stankovic, Lorenzo Strigini Date : June 2009 Version : 2.6 1/29 This report 1 surveys forms of online data collection that are in current use (as well as being the subject of research to adapt them to changing technology and demands), and can be used as inputs to assessment of dependability and resilience, although they are not primarily meant for this use. 1. Introduction Monitoring the components of a system can be used to make decisions about the management of the system and thus control its behaviour. -
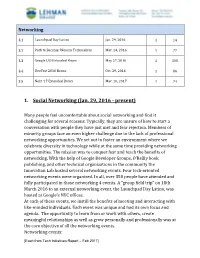
Networking Events
Networking 3.1 Launchpad Day Latino Jan. 29, 2016 1 14 3.2 Path to Success: Women Techmakers Mar. 24, 2016 1 77 3.3 Google I/O Extended Bronx May 27, 2016 1 100 3.4 DevFest 2016 Bronx Oct. 29, 2016 1 86 3.5 Next ‘17 Extended Bronx Mar. 10, 2017 1 74 1. Social Networking (Jan. 29, 2016 - present) Many people feel uncomfortable about social networking and find it challenging for several reasons. Typically, they are unsure of how to start a conversation with people they have just met and fear rejection. Members of minority groups face an even higher challenge due to the lack of professional networking opportunities. We set out to foster an environment where we celebrate diversity in technology while at the same time providing networking opportunities. The mission was to conquer fear and teach the benefits of networking. With the help of Google Developer Groups, O’Reilly book publishing, and other technical organizations in the community the Innovation Lab hosted several networking events. Four tech-oriented networking events were organized. In all, over 350 people have attended and fully participated in those networking 4 events. A “group field trip” on 18th March 2016 to an external networking event, the Launchpad Day Latino, was hosted at Google's NYC offices. At each of these events, we instill the benefits of meeting and interacting with like-minded individuals. Each event was unique and had its own focus and agenda. The opportunity to learn from or work with others, create meaningful relationships as well as grow personally and professionally was at the core objective of all the networking events.