International Journal of Innovative Technology and Exploring Engineering
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

30Th Annual Meeting “Rapid Evolution in the Healthcare Ecosystem: Become Frontiers”
2020 FINAL PROGRAM North American Skull Base Society 30th Annual Meeting “Rapid Evolution in the Healthcare Ecosystem: Become Frontiers” February 7-9, 2020 La Cantera Resort & Spa, San Antonio, TX Pre-Meeting Dissection Course: February 5-6, 2020 PRESIDENT: Ricardo Carrau, MD, MBA PROGRAM CHAIRS: Adam Zanation, MD & Daniel Prevedello, MD PRE-MEETING COURSE CHAIRS: Paul Gardner, MD & Arturo Solares, MD SCIENTIFIC PROGRAM COMMITTEE: Ricardo Carrau, MD, MBA, President, Adam Zanation, MD, MBA, Program Co-Chair, Daniel Prevedello, MD, Program Co-Chair, Paul Gardner, MD, Arturo Solares, MD, FACS, James Evans, MD, FACS, FAANS, Shaan Raza, MD, Brian Thorp, MD, Deanna Sasaki-Adams, MD, Chris Rassekh, MD, Christine Klatt-Cromwell, MD, Tonya Stefko, MD, Moises Arriaga, MD, Jamie Van Gompel, MD, Kibwei McKinney, MD, Derrick Lin, MD, FACS, Carlos Pinheiro-Neto, MD, PhD Dear friends and colleagues, Welcome to the 30th Annual Meeting of the North American Skull Base Society! This event will be held at La Cantera Resort in San Antonio, Texas; February 7-9, 2020 with a pre-meeting hands-on dissection course February 5-6, 2020. La Cantera is a beautiful resort, full of family- oriented amenities, located just 20 minutes from San Antonio’s downtown, The Alamo historical site and the world renowned Riverwalk. The meeting theme, Rapid Evolution in the Healthcare Ecosystem: Ricardo Carrau, MD, MBA Becoming Frontiers, will present the opportunity to discuss technological, technical, societal and economic changes affecting the way we deliver care to our patients and how our frontier horizon changes faster than our ability to adapt to these changes (“becoming frontiers”). -

Olympian Suresh Babu Memorial 9Th Kerala State Youth Athletics
KERALA STATE ATHLETICS ASSOCIATION OLYMPIAN SURESH BABU MEMORIAL9TH KERALA STATE YOUTH ATHLETICS CHAMPIONSHIP-2019 From : 31-Jan-2019 To : 01-Feb-2019 Meet Result : - FINAL - 31-Jan-2019 - 01-Feb-2019 POS BIB Athlete DOB Father'S Name Team Performance Youth Girls Under 18 Event:13 100m FINAL 31-Jan-2019 03:54 PM NR DUTEE CHAND ORISSA 11.62 Sec 2013 MR APARNA ROY Kozhikode 12.51 Sec 2018 I 104 BHAVIKA V.S 12-Aug-2002 SHAJI V.K Ernakulam 12.77 Sec II 255 ANN ROSE TOMY 25-Feb-2002 TOMY VARKEY Kottayam 12.82 Sec III 256 ALEENA VARGHESE 12-May-2003 VARGHESE Kottayam 12.89 Sec IV 363 ANGEL SILVIA M 12-Aug-2002 Kozhikode 12.96 Sec V 293 GRACE MARIYA WILSON 07-Sep-2002 WILSON CHACKO Thiruvananthapuram 13.38 Sec VI 112 DIYA TERESA ANTONY 27-Aug-2002 ANTONY K G Ernakulam 13.39 Sec VII 187 RESHMI JAYARAJ 17-Mar-2003 JAYARAJAN Idukki 13.54 Sec VIII 367 AISWARYA M 01-Apr-2002 SUDHEER Malappuram 13.65 Sec Youth Girls Under 18 Event:23 200m FINAL 01-Feb-2019 09:13 AM NR DUTEE CHAND JHARKHAND 24.28 Sec 2012 MR ANCY SOJAN Thrissur 24.90 Sec 2018 I 104 BHAVIKA V.S 12-Aug-2002 SHAJI V.K Ernakulam 25.76 Sec II 355 TREESA MATHEW 03-Jul-2002 MATHEW K V Kozhikode 25.96 Sec III 363 ANGEL SILVIA M 12-Aug-2002 Kozhikode 25.98 Sec IV 293 GRACE MARIYA WILSON 07-Sep-2002 WILSON CHACKO Thiruvananthapuram 27.08 Sec V 112 DIYA TERESA ANTONY 27-Aug-2002 ANTONY K G Ernakulam 27.22 Sec VI 367 AISWARYA M 01-Apr-2002 SUDHEER Malappuram 27.97 Sec VII 187 RESHMI JAYARAJ 17-Mar-2003 JAYARAJAN Idukki 28.15 Sec VIII 215 PRIYADHARSINI R 22-Jun-2002 RAJENDRAN C Palakkad 28.58 Sec -

Annexure 1B 18416
Annexure 1 B List of taxpayers allotted to State having turnover of more than or equal to 1.5 Crore Sl.No Taxpayers Name GSTIN 1 BROTHERS OF ST.GABRIEL EDUCATION SOCIETY 36AAAAB0175C1ZE 2 BALAJI BEEDI PRODUCERS PRODUCTIVE INDUSTRIAL COOPERATIVE SOCIETY LIMITED 36AAAAB7475M1ZC 3 CENTRAL POWER RESEARCH INSTITUTE 36AAAAC0268P1ZK 4 CO OPERATIVE ELECTRIC SUPPLY SOCIETY LTD 36AAAAC0346G1Z8 5 CENTRE FOR MATERIALS FOR ELECTRONIC TECHNOLOGY 36AAAAC0801E1ZK 6 CYBER SPAZIO OWNERS WELFARE ASSOCIATION 36AAAAC5706G1Z2 7 DHANALAXMI DHANYA VITHANA RAITHU PARASPARA SAHAKARA PARIMITHA SANGHAM 36AAAAD2220N1ZZ 8 DSRB ASSOCIATES 36AAAAD7272Q1Z7 9 D S R EDUCATIONAL SOCIETY 36AAAAD7497D1ZN 10 DIRECTOR SAINIK WELFARE 36AAAAD9115E1Z2 11 GIRIJAN PRIMARY COOPE MARKETING SOCIETY LIMITED ADILABAD 36AAAAG4299E1ZO 12 GIRIJAN PRIMARY CO OP MARKETING SOCIETY LTD UTNOOR 36AAAAG4426D1Z5 13 GIRIJANA PRIMARY CO-OPERATIVE MARKETING SOCIETY LIMITED VENKATAPURAM 36AAAAG5461E1ZY 14 GANGA HITECH CITY 2 SOCIETY 36AAAAG6290R1Z2 15 GSK - VISHWA (JV) 36AAAAG8669E1ZI 16 HASSAN CO OPERATIVE MILK PRODUCERS SOCIETIES UNION LTD 36AAAAH0229B1ZF 17 HCC SEW MEIL JOINT VENTURE 36AAAAH3286Q1Z5 18 INDIAN FARMERS FERTILISER COOPERATIVE LIMITED 36AAAAI0050M1ZW 19 INDU FORTUNE FIELDS GARDENIA APARTMENT OWNERS ASSOCIATION 36AAAAI4338L1ZJ 20 INDUR INTIDEEPAM MUTUAL AIDED CO-OP THRIFT/CREDIT SOC FEDERATION LIMITED 36AAAAI5080P1ZA 21 INSURANCE INFORMATION BUREAU OF INDIA 36AAAAI6771M1Z8 22 INSTITUTE OF DEFENCE SCIENTISTS AND TECHNOLOGISTS 36AAAAI7233A1Z6 23 KARNATAKA CO-OPERATIVE MILK PRODUCER\S FEDERATION -

International Journal of Recent Technology and Engineering
International Journal of Recent Technology and Engineering ISSN : 2277 - 3878 Website: www.ijrte.org Volume-1 Issue-5, November 2012 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. a n d E n y g i n g e o l e o r i n n h g c e T t n e c Ijrt e e R I n f E t o X e N P l l r L O I n a O T R A a n I V N r O G N t IN i u o o n J a l www.ijrte.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. -
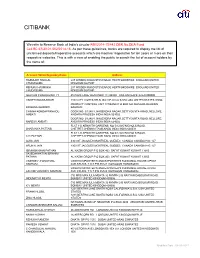
Details of Unclaimed Deposits / Inoperative Accounts
CITIBANK We refer to Reserve Bank of India’s circular RBI/2014-15/442 DBR.No.DEA Fund Cell.BC.67/30.01.002/2014-15. As per these guidelines, banks are required to display the list of unclaimed deposits/inoperative accounts which are inactive/ inoperative for ten years or more on their respective websites. This is with a view of enabling the public to search the list of account holders by the name of: Account Holder/Signatory Name Address HASMUKH HARILAL 207 WISDEN ROAD STEVENAGE HERTFORDSHIRE ENGLAND UNITED CHUDASAMA KINGDOM SG15NP RENUKA HASMUKH 207 WISDEN ROAD STEVENAGE HERTFORDSHIRE ENGLAND UNITED CHUDASAMA KINGDOM SG15NP GAUTAM CHAKRAVARTTY 45 PARK LANE WESTPORT CT.06880 USA UNITED STATES 000000 VAIDEHI MAJMUNDAR 1109 CITY LIGHTS DR ALISO VIEJO CA 92656 USA UNITED STATES 92656 PRODUCT CONTROL UNIT CITIBANK P O BOX 548 MANAMA BAHRAIN KRISHNA GUDDETI BAHRAIN CHINNA KONDAPPANAIDU DOOR NO: 3/1240/1, NAGENDRA NAGAR,SETTYGUNTA ROAD, NELLORE, AMBATI ANDHRA PRADESH INDIA INDIA 524002 DOOR NO: 3/1240/1, NAGENDRA NAGAR,SETTYGUNTA ROAD, NELLORE, NARESH AMBATI ANDHRA PRADESH INDIA INDIA 524002 FLAT 1-D,KENWITH GARDENS, NO 5/12,MC'NICHOLS ROAD, SHARANYA PATTABI CHETPET,CHENNAI TAMILNADU INDIA INDIA 600031 FLAT 1-D,KENWITH GARDENS, NO 5/12,MC'NICHOLS ROAD, C D PATTABI . CHETPET,CHENNAI TAMILNADU INDIA INDIA 600031 ALKA JAIN 4303 ST.JACQUES MONTREAL QUEBEC CANADA CANADA H4C 1J7 ARUN K JAIN 4303 ST.JACQUES MONTREAL QUEBEC CANADA CANADA H4C 1J7 IBRAHIM KHAN PATHAN AL KAZMI GROUP P O BOX 403 SAFAT KUWAIT KUWAIT 13005 SAJEDAKHATUN IBRAHIM PATHAN AL KAZMI -

UNITED STATES GERMANY RUSSIA UKRAINE End 2015 National Lists
end 2015 National Lists Top 10 Decathlon Top 50 8742 1 UNITED STATES EATON Ashton 9045 88 29/08/15 1 Beijing O'BRIEN Dan 8891 66 05/09/92 1 Talence CLAY Bryan 8832 80 30/06/08 1 Eugene HARDEE Trey 8790 84 20/08/09 1 Berlin PAPPAS Tom 8784 76 22/06/03 1 Palo Alto JOHNSON Dave 8705 63 24/04/92 1 Azuza HUFFINS Chris 8694 70 20/06/98 1 Nlle Orleans FRITZ Steve 8644 67 01/08/96 4 Atlanta JENNER Bruce 8634 49 30/07/76 1 Montréal BARKER Ricky 8404 69 15/03/96 2 College Station 87423 10 8678 2 GERMANY HINGSEN Jurgen 8832 58 09/06/84 1 Mannheim FREIMUTH Uwe 8792 61 21/07/84 1 Potsdam WENTZ Siegfried 8762 60 05/06/83 2 Bernhausen BUSEMANN Frank 8706 75 01/08/96 2 Atlanta VOSS Torsten 8680 63 04/09/87 1 Roma SCHRADER Michael 8670 87 11/08/13 2 Moskva KRATSCHMER Guido 8667 53 14/06/80 1 Bernhausen FREIMUTH Rico 8561 88 29/08/15 3 Beijing BEHRENBRUCH Pascal 8558 85 28/06/12 1 Helsinki MEIER Paul 8548 71 20/08/93 3 Stuttgart 86776 10 8513 3 RUSSIA DEGTYARYOV Grigoriy 8698 58 22/06/84 1 Kyiv LOBODIN Lev 8571 69 20/08/98 3 Budapest SHKURENEV Ilya 8538 91 29/08/15 4 Beijing POGORELOV Aleksandr 8528 80 20/08/09 3 Berlin KUTSENKO Yuriy 8519 52 22/06/84 3 Kyiv SYSOEV Aleksey 8497 85 01/06/08 2 Götzis AKHAPKIN Konstantin 8485 56 02/08/82 1 Moskva DROZDOV Aleksey 8475 83 01/09/07 4 Osaka ZHELANOV Sergey 8417 57 22/06/84 4 Kyiv GREBENYUK Aleksandr 8400 51 03/07/77 1 Riga 85128 10 8455 4 UKRAINE APAICHEV Aleksandr 8709 61 03/06/84 1 Neubrandenburg YURKOV Aleksandr 8574 75 04/06/00 4 Götzis SOBOLEVSKIY Igor 8547 62 22/06/84 2 Kyiv NEVSKIY Aleksandr 8491 58 20/05/84 -

Abstarct Book IJEAT V1i2 Dec
IInntteerrnnaattiioonnaall JJoouurrnnaall ooff EEnnggiinneeeerriinngg aanndd AAddvvaanncceedd TTeecchhnnoollooggyy ISSN : 2249 - 8958 Website: www.ijeat.org Volume-1 Issue-2, December 2011 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. Ltd. ced Te van ch d no A l d o n g y a g n i r e e IJEat n i I E n g X N t P e L IO n O E T r R A I V n NG NO f IN a o t l i o a n n r a u l J o www.ijeat.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. -

ASIAN GAMES Year Event Name Performance Rank/ Place MEN 100 M Lavy Pinto 10.8 S Gold 200 M Lavy Pinto 22.0 S Gold 200 M M
ASIAN GAMES Year Event Name Performance Rank/ Place MEN 100 m Lavy Pinto 10.8 s Gold 200 m Lavy Pinto 22.0 s Gold 200 m M. Gabriel 22.5 s Silver 400 m A. S. Bakshi 50.8 s Silver 400 m Govind Singh 51.4 s Bronze 800 m Ranjit Singh 1:59.3 s Gold 800 m Kulwant Singh 1:59.7 s Silver 1500 m Nikka Singh 4:04.1 s Gold 5000 m Pritam Singh 15:57.8 s Silver 10,000 m Gurbachan Singh 34:58.8 s Bronze 400 m hurdles Teja Singh 56.9 s Silver 3000 m steeplechase Ajit Singh 9:37.8 s Bronze Lavy Pinto M. Gabriel 4 × 100 m relay 42.8 s Silver Ram Swaroop Alfred Shamin 1951 A. S. Bakshi Govind Singh 4 × 400 m relay 3:24.2 s Gold Balwant Singh Karnan Singh Marathon Chhota Singh 2:42:58.6 s Gold Marathon Surat Singh Mathur 2:53:49.8 s Bronze 10,000 m walk Mahabir Prasad 52:31.4 s Gold 10,000 m walk Kesar Singh 52:54.0 s Bronze 50 km walk Bakhtawar Singh 5:44:07.4 s Gold 50 km walk B. Das 5:44:14.6 s Silver Long jump Baldev Singh 6.99 m Silver Shot put Madan Lal 13.78 m Gold Discus throw Makhan Singh 39.92 m Gold Hammer throw Somnath Chopra 43.35 m Silver Hammer throw Kishen Singh 42.32 m Bronze Javelin throw Parsa Singh 50.38 m Silver Decathlon Khurshid Ahmed 5099 points Bronze WOMEN 100 m Roshan Mistry 12.8 S Silver 200 m Mary D'Souza 28.0 s Bronze Mary D'Souza Roshan Mistry 4 × 100 m relay 51.9 s Silver Banoo Gulzar 1951 Pat Mendonca High jump Marie Semoes 1.37 m Bronze Long jump Sylvia Gauntlet 4.52 m Bronze Shot put Barbara Webster 9.02 m Bronze Javelin throw Barbara Webster 26.7 m Bronze MEN 100 m M. -

Tiny Kerala in Mega Olympics
COVER STORY Olympic medal for India outside Olympic Hockey. He won the medal in 57 kg. freestyle wrestling. The other two bronze medals were won by Leander Paes in Tennis in Atlanta Olympics in 1996 and Karnam Malleswari in weight lifting in Sydney Olympics in 2000. In no other individual items India could so far achieve medals. But in 1960 and in 1984 the whole nation was expecting individual medals from two athletes viz. “Flying-Sikh” Milkha Singh and “Payyoli Express” P.T. Usha. In Rome, Milkha Singh returned his career-best time of 45.6 seconds for 400 meters race in the finals, breaking the then existing Olympic record. But stunningly he was restricted to the fourth place in the race in which the American athlete Otis Davis clocked 44.9 seconds to win the gold. Karl Kaufman of Germany won Tiny Kerala in the silver medal and Malcolm Spence of South Africa obtained the bronze medal. When the final result was announced, the whole of Indian nation was sobbing! The mega Olympics 8th August 1984 was also a similar black day for India. On that day P.T. Usha was R. Radhakrishnan championship in Hockey till 1956 running in the finals of the 400m. hurdles hile the world is once again continuously and in 1960 Rome Olympics in Los Angeles. About 100 crores of moving on to the cheers and Pakistan defeated India in the finals and people in India were eagerly waiting for a ecstasy of modern Olympics, won the gold. Again in the next Olympics good news – winning the first medal for W at Tokyo, India could regain its gold India in Olympic athletics. -

OLYMPIAN SURESH BABU MEMORIAL 8TH KERALA STATE YOUTH ATHLETICS CHAMPIONSHIP - 2018 from : 12-Jun-2018 to : 13-Jun-2018
KERALA STATE ATHLETICS ASSOCIATION OLYMPIAN SURESH BABU MEMORIAL 8TH KERALA STATE YOUTH ATHLETICS CHAMPIONSHIP - 2018 From : 12-Jun-2018 To : 13-Jun-2018 Meet Result : - FINAL - 12-Jun-2018 - 13-Jun-2018 POS BIB Athlete DOB Father'S Name Team Performance Youth Girls Under 18 Event:17 100m FINAL 12-Jun-2018 03:43 PM NR DUTEE CHAND ORISSA 11.62 Sec 2013 MR ANJU P M PALAKKAD 12.70 Sec 2012 I 213 APARNA ROY 31-May-2001 ROYMON K. OVELIL Kozhikode 12.51 Sec NMR II 174 ANU JOSEPH 21-Apr-2002 BENNY O B Kannur 12.84 Sec III 126 BHAVIKA V.S 12-Aug-2002 SHAJI V.K Ernakulam 12.84 Sec IV 201 ANJALI P D 22-Mar-2001 DILEESH P D Kottayam 13.08 Sec V 312 ANJANA M S 03-May-2002 SELVARAJ.B Thiruvananthapuram 13.22 Sec VI 125 DIYA TERESA ANTONY 27-Aug-2002 ANTONY K G Ernakulam 13.36 Sec VII 197 ANANYA JETO 10-Apr-2001 JETO JOSE Kottayam 13.55 Sec VIII 388 UTHARA P 29-Jan-2002 RAMAKRISHNAN P Malappuram 13.61 Sec Youth Girls Under 18 Event:16 200m FINAL 13-Jun-2018 02:46 PM NR DUTEE CHAND JHARKHAND 24.28 Sec 2012 MR ANCY SOJAN Thrissur 25.92 Sec 2017 I 350 ANCY SOJAN 01-Mar-2001 SOJAN E T Thrissur 24.90 Sec NMR II 124 GOWRINANDANA 26-Mar-2002 RAJESH P T Ernakulam 26.09 Sec III 126 BHAVIKA V.S 12-Aug-2002 SHAJI V.K Ernakulam 26.34 Sec IV 125 DIYA TERESA ANTONY 27-Aug-2002 ANTONY K G Ernakulam 26.79 Sec V 193 ANN ROSE TOMY 25-Feb-2002 TOMY VARKEY Kottayam 27.09 Sec VI 314 GRACE MARIYA WILSON 07-Sep-2002 Thiruvananthapuram 27.26 Sec VII 201 ANJALI P D 22-Mar-2001 DILEESH P D Kottayam 27.38 Sec Youth Girls Under 18 Event:5 400m FINAL 12-Jun-2018 09:41 AM NR PINKI -

Editor in Chief Dr
Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal (M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. Deepak Garg Professor, Department of Computer Science and Engineering, Thapar University, Patiala (Punjab), India, Senior Member of IEEE, Secretary of IEEE Computer Society (Delhi Section), Life Member of Computer Society of India (CSI), Indian Society of Technical Education (ISTE), Indian Science Congress Association Kolkata. Dr. Vijay Anant Athavale Director of SVS Group of Institutions, Mawana, Meerut (U.P.) India/ U.P. Technical University, India Dr. T.C. Manjunath Principal & Professor, HKBK College of Engg, Nagawara, Arabic College Road, Bengaluru-560045, Karnataka, India Dr. Kosta Yogeshwar Prasad Director, Technical Campus, Marwadi Education Foundation‘s Group of Institutions, Rajkot-Morbi Highway, Gauridad, Rajkot, Gujarat, India Dr.