Playing with IE11 Activex 0Days About Me
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Pentest-Report Mailvelope 12.2012 - 02.2013 Cure53, Dr.-Ing
Pentest-Report Mailvelope 12.2012 - 02.2013 Cure53, Dr.-Ing. Mario Heiderich / Krzysztof Kotowicz Index Introduction Test Chronicle Methodology Vulnerabilities MV -01-001 Insufficient Output Filtering enables Frame Hijacking Attacks ( High ) MV -01-002 Arbitrary JavaScript execution in decrypted mail contents ( High ) MV -01-003 Usage of external CSS loaded via HTTP in privileged context ( Medium ) MV -01-004 UI Spoof via z - indexed positioned DOM Elements ( Medium ) MV -01-005 Predictable GET Parameter Usage for Connection Identifiers ( Medium ) MV -01-006 Rich Text Editor transfers unsanitized HTML content ( High ) MV -01-007 Features in showModalDialog Branch expose M ailer to XSS ( Medium ) MV -01-008 Arbitrary File Download with RTE editor filter bypass ( Low ) MV -01-009 Lack of HTML Sanitization when using Plaintext Editor ( Medium ) Miscellaneous Issues Conclusion Introduction “Mailvelope uses the OpenPGP encryption standard which makes it compatible to existing mail encryption solutions. Installation of Mailvelope from the Chrome Web Store ensures that the installation package is signed and therefore its origin and integrity can be verified. Mailvelope integrates directly into the Webmail user interface, it's elements are unintrusive and easy to use in your normal workflow. It comes preconfigured for major web mail provider. Mailvelope can be customized to work with any Webmail.”1 1 http :// www . mailvelope . com /about Test Chronicle • 2012/12/20 - XSS vectors in common input fields (Mailvelope options etc.) • 2012/12/20 - -

Faster Base64 Encoding and Decoding Using AVX2 Instructions
Faster Base64 Encoding and Decoding using AVX2 Instructions WOJCIECH MUŁA, DANIEL LEMIRE, Universite´ du Quebec´ (TELUQ) Web developers use base64 formats to include images, fonts, sounds and other resources directly inside HTML, JavaScript, JSON and XML files. We estimate that billions of base64 messages are decoded every day. We are motivated to improve the efficiency of base64 encoding and decoding. Compared to state-of-the-art implementations, we multiply the speeds of both the encoding (≈ 10×) and the decoding (≈ 7×). We achieve these good results by using the single-instruction-multiple-data (SIMD) instructions available on recent Intel processors (AVX2). Our accelerated software abides by the specification and reports errors when encountering characters outside of the base64 set. It is available online as free software under a liberal license. CCS Concepts: •Theory of computation ! Vector / streaming algorithms; General Terms: Algorithms, Performance Additional Key Words and Phrases: Binary-to-text encoding, Vectorization, Data URI, Web Performance 1. INTRODUCTION We use base64 formats to represent arbitrary binary data as text. Base64 is part of the MIME email protocol [Linn 1993; Freed and Borenstein 1996], used to encode binary attachments. Base64 is included in the standard libraries of popular programming languages such as Java, C#, Swift, PHP, Python, Rust, JavaScript and Go. Major database systems such as Oracle and MySQL include base64 functions. On the Web, we often combine binary resources (images, videos, sounds) with text- only documents (XML, JavaScript, HTML). Before a Web page can be displayed, it is often necessary to retrieve not only the HTML document but also all of the separate binary resources it needs. -

Bookings of Westin Diplomat Bookings
RESTful Web Applications with Spring 3.0 Arjen Poutsma Senior Software Engineer SpringSource Speaker’s qualifications • Fifteen years of experience in Enterprise Software Development • Six years of Web service experience • Development lead of Spring Web Services • Working on Spring 3.0 • Contributor to various Open Source frameworks: (XFire, Axis2, NEO, ...) SpringSource Confidential. Do not distribute without express permission Overview • RESTful URLs • URI templates • Content negotiation • HTTP method conversion • ETag support SpringSource Confidential. Do not distribute without express permission RESTful URLs Resources • URLs are unique identifiers for Resources • Typically nouns • Customer • Orders • Shopping cart URLs [scheme:][//authority][path][?query][#fragment] http://www.springsource.com https://mybank.com http://www.google.com/search?q=arjen %20poutsma http://java.sun.com/j2se/1.4.2/docs/api/java/lang/ String.html#indexOf(int) SpringSource Confidential. Do not distribute without express permission Paths • Represents hierarchy • Represents value for consumers • Collections on higher levels SpringSource Confidential. Do not distribute without express permission Example Path Description /hotels List of all hotels /hotels/westindiplomat Details of Westin Diplomat /hotels/westindiplomat/ List of bookings of Westin Diplomat bookings /hotels/westindiplomat/ Individual booking bookings/42584 No Hierarchy? Path Description maps/24.9195,17.821 Commas maps/24.9195;17.821 Semicolons Query Variables • Input for algorithms • Get ignored by proxies -
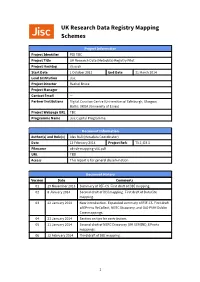
UK Research Data Registry Mapping Schemes
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

Cs297report-PDF
CS297 Report Bookmarklet Builder for Offline Data Retrieval Sheetal Naidu [email protected] Advisor: Dr. Chris Pollett Department of Computer Science San Jose State University Fall 2007 Table of Contents Introduction ………………………………………………………………………………. 3 Deliverable 1 ……………………………………………………………………………... 3 Deliverable 2 ……………………………………………………………………………... 4 Deliverable 3 ……………………………………………………………………………... 6 Deliverable 4 ……………………………………………………………………………... 7 Future work ………………………………………………………………………………. 8 Conclusion ……………………………………………………………………………….. 8 References ………………………………………………………………………………... 8 2 Introduction A bookmarklet is a small computer application that is stored as a URL of a bookmark in the browser. Bookmarlet builders exist for storing single webpages in hand held devices and these webpages are stored as PDF files. The goal of my project is to develop a tool that can save entire web page applications as bookmarklets. This will enable users to use these applications even when they are not connected to the Internet. The main technology beyond Javascript needed to do this is the data: URI scheme. This enables images, Flash, applets, PDFs, etc. to be directly embedded as base64 encoded text within a web page. This URI scheme is supported by all major browsers other than Internet Explorer. Our program will obfuscate the actual resulting JavaScript so these complete applications could potentially be sold without easily being reverse engineered. The application will be made available online, to users who are typically website owners and would like to allow their users to be able to use the applications offline. This report describes the background work that was conducted as preparation for CS298 when the actual implementation of the project will take place. This preparation work was split into four main deliverables. The deliverables were designed at gaining relevant information and knowledge with respect to the main project. -

Gemini and NTS Exit Reform API Usage Guidelines
Gemini and NTS Exit Reform API Usage Guidelines ~ 1 ~ Table of Contents 1. Introduction ............................................................................................................................................6 1.1. API Technology Overview ....................................................................................................................6 2. API Client Development Guidelines .....................................................................................................8 2.1. HTTPS and SSL ...................................................................................................................................9 2.2. Authentication and Authorization ...................................................................................................... 10 2.3. Maintaining the Session .................................................................................................................... 10 2.4. Authentication / Loss of Session / Authorization Failures ................................................................. 10 2.5. Request a Compressed Response to your API Client ...................................................................... 11 3. API Configuration Details ................................................................................................................... 14 3.1. API Technology Overview ................................................................................................................. 14 3.2. Network Requirements ..................................................................................................................... -

Q4 2016 Newsletter
FraudAction™ Anti-Fraud Services Q4 2016 NEWSLETTER TABLE OF CONTENTS Introduction ............................................................................................................................................ 3 The Many Schemes and Techniques of Phishing ............................................................................................... 4 The Tax Refund Ploy - Multi-branded Phishing ............................................................................................... 4 Bulk Phishing Campaigns ........................................................................................................................ 4 Random Folder Generators ...................................................................................................................... 5 Local HTML Scheme .............................................................................................................................. 6 BASE64 encoded Phishing in a URL ........................................................................................................... 7 Phishing with MITM capabilities ................................................................................................................. 7 Phishing Plus Mobile Malware in India ....................................................................................................... 10 Fast-Flux Phishing ............................................................................................................................... 13 Additional Phishing Techniques -

Analysis of Hypertext Markup Isolation Techniques for XSS Prevention
Analysis of Hypertext Isolation Techniques for XSS Prevention Mike Ter Louw Prithvi Bisht V.N. Venkatakrishnan Department of Computer Science University of Illinois at Chicago Abstract that instructs a browser to mark certain, isolated portions of an HTML document as untrusted. If robust isolation Modern websites and web applications commonly inte- facilities were supported by web browsers, policy-based grate third-party and user-generated content to enrich the constraints could be enforced over untrusted content to user’s experience. Developers of these applications are effectively prevent script injection attacks. in need of a simple way to limit the capabilities of this The draft version of HTML 5 [21] does not propose less trusted, outsourced web content and thereby protect any hypertext isolation facility, even though XSS is a long their users from cross-site scripting attacks. We summa- recognized threat and several informal solutions have re- rize several recent proposals that enable developers to iso- cently been suggested by concerned members of the web late untrusted hypertext, and could be used to define ro- development community. The main objective of this pa- bust constraint environments that are enforceable by web per is to categorize these proposals, analyze them further browsers. A comparative analysis of these proposals is and motivate the web standards and research communities presented highlighting security, legacy browser compati- to focus on the issue. bility and several other important qualities. 2 Background 1 Introduction Today’s browsers implement a default-allow policy for One hallmark of the Web 2.0 phenomenon is the rapid JavaScript in the sense they permit execution of any script increase in user-created content for web applications. -

HTTPAPI S. Dalal Internet-Draft Intended Status: Standards Track E
HTTPAPI S. Dalal Internet-Draft Intended status: Standards Track E. Wilde Expires: January 11, 2022 July 10, 2021 The Deprecation HTTP Header Field draft-ietf-httpapi-deprecation-header-02 Abstract The HTTP Deprecation Response Header Field can be used to signal to consumers of a URI-identified resource that the resource has been deprecated. Additionally, the deprecation link relation can be used to link to a resource that provides additional context for the deprecation, and possibly ways in which clients can find a replacement for the deprecated resource. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on January 11, 2022. Copyright Notice Copyright (c) 2021 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust’s Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. -

Describing Data Patterns. a General Deconstruction of Metadata Standards
Describing Data Patterns A general deconstruction of metadata standards Dissertation in support of the degree of Doctor philosophiae (Dr. phil.) by Jakob Voß submitted at January 7th 2013 defended at May 31st 2013 at the Faculty of Philosophy I Humboldt-University Berlin Berlin School of Library and Information Science Reviewer: Prof. Dr. Stefan Gradman Prof. Dr. Felix Sasaki Prof. William Honig, PhD This document is licensed under the terms of the Creative Commons Attribution- ShareAlike license (CC-BY-SA). Feel free to reuse any parts of it as long as attribution is given to Jakob Voß and the result is licensed under CC-BY-SA as well. The full source code of this document, its variants and corrections are available at https://github.com/jakobib/phdthesis2013. Selected parts and additional content are made available at http://aboutdata.org A digital copy of this thesis (with same pagination but larger margins to fit A4 paper format) is archived at http://edoc.hu-berlin.de/. A printed version is published through CreateSpace and available by Amazon and selected distributors. ISBN-13: 978-1-4909-3186-9 ISBN-10: 1-4909-3186-4 Cover: the Arecibo message, sent into empty space in 1974 (image CC-BY-SA Arne Nordmann, http://commons.wikimedia.org/wiki/File:Arecibo_message.svg) CC-BY-SA by Widder (2010) Abstract Many methods, technologies, standards, and languages exist to structure and de- scribe data. The aim of this thesis is to find common features in these methods to determine how data is actually structured and described. Existing studies are limited to notions of data as recorded observations and facts, or they require given structures to build on, such as the concept of a record or the concept of a schema. -

Dynamic Web-Applications with Meteor.Js
Yrkkö Äkkijyrkkä Dynamic Web-Applications with Meteor.js Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Thesis 4 December 2015 Abstract Author(s) Yrkkö Äkkijyrkkä Title Dynamic Web-Applications with Meteor.js Number of Pages 36 pages Date December 4, 2015 Degree Bachelor of Engineering Degree Programme Information Technology Specialisation option Software engineering Instructor(s) Simo Silander, Senior Lecturer This thesis studies the viability of using Meteor.js in implementing a content management system by using the User Centred Design and Generic programming paradigm. The goal of the project was to program generic visual templates and software modules to be used in the aggregation and displaying of user-created data. The need for a content management system came from Aalto University Department of Ar- chitecture, which was in dire need for a more accessible way of interacting with their audi- ence and the academic community. During the development a great deal of care was placed on making the intranet side acces- sible to different user profiles, the common factor being the fact that the user base is stems from the architecture department or similar academic circles. The author’s knowledge and experience gained during studies and working as a freelance web-developer during the past 5 years were well applied in the project, as well as the know- how acquired at Conmio Oy building high concurrency web-applications that once served up to 100 million page hits per day. Within this frame work, the study tries to objectively ascertain how production-ready Meteor actually is, how flexible it is when considering a particular software design and how well it performs when carrying out the design.