Virus Bulletin, February 1994
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tech Industry
EmailWire Tech Media Sector Distribution List Reach your target audience in the Technology industry. See next page for complete media list. Call 281-645-4086, go to www.EmailWire.Com EmailWire and IT-NewsWire are newswire services of GroupWeb Media LLC. The above logos are registered trademarks of respective media outlets. EmailWire Information Technology Media Sector Distribution List. Call 281-6454086 AI (Artificial Intelligence) magazine imageSource magazine Baseline Information Management magazine Business Solutions magazine Information Week magazine Cadalyst magazine Infosecurity magazine ChannelPro magazine InfoWorld magazine CIO magazine Issues in Science and Technology magazine CIO Insight magazine IT Professional magazine Cloud Computing magazine IT Solution Journal magazine CNET Laptop magazine Computer magazine Mac Life magazine Computer Link magazine MacRumors Computer Technology Review magazine Macworld Computer User magazine Make magazine Computerworld magazine Mass High Tech magazine Computor Edge magazine Maximum PC magazine Connected World magazine MIS Quarterly magazine CPU Computer Power User magazine Mission Critical magazine Creo Community Mobile Enterprise magazine CRN magazine NCTechNews Cyber Trend magazine Network Computing magazine D-Lib (Digital Library) magazine Network Products Guide magazine Datamation magazine Network World DevProConnections magazine Nuts & Volts magazine Enterprise Executive magazine Online magazine eWeek magazine PC magazine Federal Computer Week (FCW) magazine PC World magazine Field -

Chapter 18 Magazines and Newsletters
Chapter 18 Magazines and Newsletters 18.1 ... The Beginning Publication of personal computing articles was initially in electronic magazines such as Popular Electronics, QST and Radio-Electronics. Then came the magazines and newsletters devoted to personal computing and microcomputers. Most of these initial publications were not specific to a particular microprocessor or type of microcomputer. The following are some of the more significant publications. The first publication devoted to personal computing was the Amateur Computer Society ACS Newsletter. The editor was Stephen B. Gray who was also the founder of ACS. The first issue was published in August 1966 and the last in December 1976. It was a bi- monthly directed at anyone interested in building and operating a personal computer. The newsletter was a significant source of information on the design and construction of a computer during the time period it was published. The PCC Newsletter was published by Robert L. Albrecht of the People's Computer Company in California. The first issue was published in October 1972. The first issue cover stated it “is a newspaper... about having fun with computers, learning how to use computers, how to buy a minicomputer for yourself your school and books films and tools of the future.” The newspaper name changed to the People’s Computers with a magazine type of format in May-June 1977. Hal Singer started the Micro-8 Newsletter in September 1974. This was a newsletter published by the Micro-8 Computer Users Group, originally the Mark-8 Group for Mark-8 computer users. Another publication started in 1974, was The Computer Hobbyist newsletter. -

Periodicals for Microcomputers: an Annotated Bibliography Second Edition
Periodicals for Microcomputers: An Annotated Bibliography Second Edition by Thomas C. Stilwell Working Paper No. 21 1985 MSU INTERNATIONAL DEVELOPMENT PAPERS Carl K. Eicher, Carl Liedholm, and Michael T. Weber Co-Editors The MSU International Development Paper series is designed to further the comparative analysis of international development activities in Africa, Latin America, Asia, and the Near East. The papers report research findings on historical, as well as contemporary, international development problems. The series includes papers on a wide range of topics, such as alternative rural development strategies; nonfarm employment and small scale industry; housing and construction; farming and marketing systems; food and nutrition policy analysis; economics of rice production in West Africa; technological change, employment, and income distribution; computer techniques for farm and marketing surveys; and farming systems research. The papers are aimed at teachers, researchers, policy makers, donor agencies, and international development practitioners. Selected papers will be translated into French, Spanish, or Arabic. Individuals and institutions in Third World countries may receive single copies free of charge. See inside back cover for a list of available papers and their prices. For more information, write to: MSU International Development Papers Department of Agricultural Economics Agriculture Hall Michigan State University East Lansing, Michigan 48824-1039 U.S.A. PERIODICALS FOR MICROCOMPUTERS: An Annotated Bibliography Second Edition* By Thomas C. Stilwell Visiting Associate Professor Department of Agricultural Economics Michigan State University 1985 *This paper is published by the Department of Agricultural Economics, Michigan State University, under the "Food Security in Africa" Cooperative Agreement DAN-1l90-A-OO-li092-00, U.S. -

Reviews & Press Quotes
Reviews & Press Quotes “the searchlight “searches “the of the computer at blazing speeds” ultimate search world” machine” “results are “unrivaled amazing” power” “a staggering “an incredible “intuitive and number of ways to austere” tool” search” “raises the bar “fast, clean, in text retrieval” efficient, accurate” “extensive search “tremendously “more parameters” powerful” horsepower” “an inspired “terrific choice” speeds” “stacked with “robust, “big site awards and sophisticated and seeks accolades” powerful” search engine” “indispensable” “astounding” “searches “covers all data “outsmarts lightning fast and sources” (and out maneuvers) accurately to boot” the competition” “industrial “insanely strength” fast” “blindingly “incredibly “the clear fast text search” flexible” winner” www.dtsearch.com 1-800-IT-FINDS ® ® dtSearch — Instantly Search Terabytes of Text dtSearch — Instantly Search Terabytes of Text dtSearch “covers all data sources “Bottom line: dtSearch manages “I go for brute strength, via … powerful Web-based engines for a terabyte of text in a single index something called dtSearch.” searching across lots of data.” and returns results in less than a — The Wall Street Journal (Loose — eWEEK Labs second … Corporate features include Wire column, “Gimme Some of multiple languages, index sharing, That Software?”) and customization. Plus, there’s dtSearch “will help you pick a needle extensive third-party support.” out of a haystack … wade through “I was especially impressed with “For the heavy lifters, I’d lots of bits and bytes -

Constructions of Gender in Computer Magazine Advertisements: Confronting the Literature
University of Wollongong Research Online Faculty of Education - Papers (Archive) Faculty of Arts, Social Sciences & Humanities February 2006 Constructions of Gender in Computer Magazine Advertisements: Confronting the Literature N. F. Johnson University of Wollongong, [email protected] L. Rowan Deakin University J. Lynch Deakin University Follow this and additional works at: https://ro.uow.edu.au/edupapers Part of the Education Commons Recommended Citation Johnson, N. F.; Rowan, L.; and Lynch, J.: Constructions of Gender in Computer Magazine Advertisements: Confronting the Literature 2006. https://ro.uow.edu.au/edupapers/19 Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] Constructions of Gender in Computer Magazine Advertisements: Confronting the Literature Authors: Nicola F. Johnson, Leonie Rowan, Julianne Lynch Deakin University Citation Details: Johnson, N. F., Rowan, L. & Lynch, J. (2006). Constructions of gender in computer magazine advertisements: confronting the literature. Studies in Media and Information Literacy Education, 6 (1), available: http://128.100.205.52/jour.ihtml?lp=simile/issue21/johnson1.html , (date accessed, 23/10/2006). Abstract Previous studies (Sofia, 1998; 2002; Turner & Hovenden, 1997; Weinstein, 1998) discussed the power relations surrounding the advertisements for computers in computing magazines, in particular deconstructing the imagery and text which manifested the dominant digital discourse of power (Millar, 1998). In these studies, the authors found that women were positioned as incapable and impotent users of computers. The authors examined a number of New Zealand and Australian home computing magazines published in 2003 and 2004, looking for evidence of the gendered nature of technology or examples of any form which would constitute discrimination against women or other identity categories. -

Exhibit a (Pdf)
The Facts on Filters A Comprehensive Review of 26 Independent Laboratory Tests of the Effectiveness of Internet Filtering Software By David Burt The Facts on Filters Table of Contents 2 Introduction 3 Filtering in Homes, Businesses, Schools, and Libraries 4 Laboratory Tests of Filtering Software Effectiveness 6 Tests Finding Filters Effective 7 Tests Finding Filters of Mixed Effectiveness 13 Tests Finding Filters Ineffective 15 Conclusion 17 Footnotes 18 N2H2, Inc. • 900 4th Ave • Seattle, WA 98164 • 800.971.2622 • www.n2h2.com 2 The Facts on Filters Introduction In their 1997 decision striking down the Communications Decency Act as unconstitutional, the Supreme Court pointed to filtering software as a less restrictive means for controlling access to pornography on the Internet.1 The years since that 1997 decision have led to steady growth in the use of software filters. According to the latest research, in the year 2001, 74% of public schools2, 43% of public libraries3, 40% of major U.S. corporations4, and 41% of Internet- enabled homes with children5 have adopted filtering software. As filters have become more widely accepted, there has been an ongoing debate in public policy circles regarding the effectiveness of filtering software. The debate over filter effectiveness has often been politicized, frequently with little or no empirical data to document claims made about filtering software. While the debate has continued, a rich body of non-partisan laboratory testing literature has developed. A total of 26 published laboratory tests of filtering software effectiveness have been identified in technology and consumer print publications including PC Magazine, Info World, Network Computing, Internet World, eWeek, and Consumer Reports from 1995-2001. -
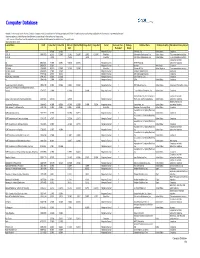
Computer Database
Computer Database Available 24 hours a day via the Internet, Computer Database provides a combination of indexing, abstracts and full text for leading business and technical publications in the computer, telecommunications and electronic industries. Select titles may have different coverage based on the market your library serves. * 10% or more of the articles from this publication may not contain full text because the publisher is not the rights holder Updated January 2, 2015 Journal Name ISSN Index Start Index End Full-text Full-text End Image Start Image End Format Refereed/Peer- Embargo Publisher Name Publisher Country Publication Primary Subject Start Reviewed (Days) 1UP 8/2008 6/2009 Magazine/Journal Ziff Davis, Inc. United States Computers 2.5G-3G 1540-0719 2/2002 11/2007 2/2002 11/2007 2/2002 11/2007 Newsletter Information Gatekeepers, Inc. United States Telecommunications industry 2.5G-4G 7/2008 7/2008 7/2008 Newsletter Information Gatekeepers, Inc. United States Telecommunications industry Computers and office 3D 0953-2331 4/1989 3/1991 4/1989 3/1991 Magazine/Journal EMAP Media Ltd. automation industries 3D Research 2092-6731 3/2010 Magazine/Journal Y Springer Netherlands Computers 3G Mobile 1524-9492 10/2002 11/2003 10/2002 11/2003 Newsletter Informa UK Ltd. United Kingdom Telecommunications industry 68 Micro Journal 0194-5025 1/1983 2/1985 Magazine/Journal Computer Publishing, Inc. Computers 80 Micro 0744-7868 1/1983 6/1988 Magazine/Journal IDG Communications, Inc. Computers A.N.A.L.O.G. Computing 0744-9917 1/1983 11/1985 Magazine/Journal Larry Flynt Pub., Inc. Computers A+ 1054-6456 1/1984 5/1989 Magazine/Journal ZDNet United States Computers Academic and Library Computing 1055-4769 4/1991 5/1992 4/1991 5/1992 Magazine/Journal Y INT Media Group, Inc. -

PC Magazine® Linux® Solutions
PC Magazine® Linux® Solutions Joe Merlino PC Magazine® Linux® Solutions Joe Merlino PC Magazine® Linux® Solutions PC Magazine® Linux® Solutions Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2006 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-471-77769-4 ISBN-10: 0-471-77769-2 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1B/SY/QT/QW/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. The advice and strategies contained herein may not be suitable for every situation. -
Retromagazine 00 Eng.Pdf
EDITORIAL SUMMARY Welcome to our first international issue! RetroMagazine is a well underway project started in Page 3 ◊ The best version of BASIC October 2017 by a small group of Italian retrocomputing Page 6 enthusiasts. ◊ Don’t ever buy a Vectrex! Page 11 Yes, we know, there are many magazines dedicated to ◊ The .d64 format – part 1 retrogames and they are gorgeous; so why the need for an Page 16 additional homebrew fanzine? ◊ Interview with Gideon Zweijtzer How many times reading those publications have you felt Page 20 ◊ Sinclair QL: mistakes, misfortune and so that something was missing? There are lot of nice pictures and a good variety of games, but... where is the code? many regrets Where are the explanations of programming techniques? Page 30 ◊ Cyrus (ZX SPECTRUM) VS. Colossus Where is the real experience of the end users? (ATARI 800XL) The idea behind our project is to reproduce the same Page 33 ◊ HIBERNATED 1 (Amiga/C64) feeling as the glorious magazines back in the day. Page 34 Magazines like Amstrad Computer Users, Bit, Compute!'s ◊ CIVILIZATION (MS DOS) Gazette, Input... They all taught tons of pimply boys the Page 37 basis of coding on their home computers! Those magazines ◊ THE PAWN (All platforms) used to contain a good balance of programming examples, hardware insights and game reviews. People involved in the preparation of this issue In memory of those magazines we adopted the shape of a PDF fanzine, instead of a more modern blog or website, to fully revitalize the spirit of the good old times. • Robin Jubber • Gianluca Girelli Do you remember the feeling while awaiting for the next issue? We want to recreate that and also give a second • Francesco Fiorentini • Leonardo Giordani chance to anybody who missed out on learning these things as a kid. -

300 Baud Issue 02
No. 2 - MAY 2010 #"6% ONLINE DESTINATIONS IN THE ERA OF 300 BAUD BY MICHEAL H. MCCABE ISSUE NO. 2 – MAY 2010 300 Baud: The title of this publication implies something more than simple hobbyist retro- computing. It implies telecommunication – something that we’re all familiar with now Once upon a time, there were three little girls who went to the police academy. And they were each that we have the Internet in all its glory. It begs the question though, with whom were we assigned very... no wait, that’s not right! communicating in the days of 8-bit systems, 300 baud modems, and usurious telephone rates? I hope this article can shed some light on the nearly forgotten online destinations of Once upon a time, there were two guys who were chatting away on the RetroChallenge BBS, who the 1970s and early 1980s. then came up with an idea... that idea was 300 Baud Magazine. And after much huffing and puffing the first issue made it out the door. It wasn’t as easy or as smooth as it should have been, but we made it through. DESTINATION 1: TIMESHARING SERVICES Thank you to everybody who gambled and bought the first issue; a double-thank-you, to the people If we travel back in time a few years, we find that the first real “online destination” for many who told their friends about it and who then bought an issue; and a triple-thank-you to those who got computer hobbyists was a mainframe or minicomputer timesharing system. -

Colonizing Cyberspace: the Formation of Virtual Communities
University of Tennessee, Knoxville TRACE: Tennessee Research and Creative Exchange Masters Theses Graduate School 5-2003 Colonizing Cyberspace: The Formation of Virtual Communities Matthew Jones University of Tennessee - Knoxville Follow this and additional works at: https://trace.tennessee.edu/utk_gradthes Part of the History Commons Recommended Citation Jones, Matthew, "Colonizing Cyberspace: The Formation of Virtual Communities. " Master's Thesis, University of Tennessee, 2003. https://trace.tennessee.edu/utk_gradthes/2039 This Thesis is brought to you for free and open access by the Graduate School at TRACE: Tennessee Research and Creative Exchange. It has been accepted for inclusion in Masters Theses by an authorized administrator of TRACE: Tennessee Research and Creative Exchange. For more information, please contact [email protected]. To the Graduate Council: I am submitting herewith a thesis written by Matthew Jones entitled "Colonizing Cyberspace: The Formation of Virtual Communities." I have examined the final electronic copy of this thesis for form and content and recommend that it be accepted in partial fulfillment of the requirements for the degree of Master of Arts, with a major in History. Janis Appier, Major Professor We have read this thesis and recommend its acceptance: Kathleen Brosnan, Vejas Liulevicius Accepted for the Council: Carolyn R. Hodges Vice Provost and Dean of the Graduate School (Original signatures are on file with official studentecor r ds.) To the Graduate Council: I am submitting herewith a thesis written by Matthew Jones entitled “Colonizing Cyberspace: The Formation of Virtual Communities.” I have examined the final electronic copy of this thesis for form and content and recommend that it be accepted in partial fulfillment of the requirements for the degree of Master of Arts, with a major in History. -

Ad Age Magazine 300 09.20.2004
AD AGE MAIN 09-20-04 B 1 AADB 9/15/04 3:29 PM Page 1 AdAgeSPECIALREPORT 9. 20.04 15TH ANNUAL MAGAZINE ONLINE TOP 10: 1.People 2.Sports Illustrated 3.Time 4.TV Guide Download the full pdf version of this 5. Better Homes & Gardens 6. Parade 7. Newsweek 8. Reader’s Digest Special Report at QwikFIND 9. Good Housekeeping 10.Woman’s Day aap96d Category star Frequency flier People power INSIDE Women’s titles claims 12% of ad pages Monthlies grab half the $32.49 bil. gross ‘People’ tops 300 list stretching from of Top 300 magazines. revenue from advertising, circulation. $1.24 bil. to $18.5 mil. in gross revenue. Page S-2 Page S-2 Pages S-6, S-8 AD AGE MAIN 09-20-04 B 2 AADB 9/15/04 3:28 PM Page 1 September 20, 2004 | Advertising Age |S-2 AdAgeSPECIALREPORT MAGAZINE 300 TOP MAGAZINES BY CATEGORY RANKED BY AD PAGES IN 2003 RANK AD TOTAL AD CIRCULATION MAGAZINE 2003 CATEGORY/TOP MAGAZINE BY AD PAGES PAGES % CHG REVENUE REVENUE REVENUE COUNT Top 300 revenue CONSUMER MAGAZINE CATEGORIES 1 Women’s (49) 41,300.11 7.5 $5,874 $4,233 $1,641 37 InStyle 3,045.65 0.5 356 293 63 2 Home service & home (24) 20,565.89 0.9 2,974 2,143 831 24 a record $32.5 bil. Better Homes & Gardens 2,116.81 10.8 836 663 173 3 Newsweeklies (36A) 19,836.26 0.1 5,460 3,388 2,073 9 Trio of ‘People,’ ‘SI, ‘Time’ in ad pages; business publications slipped 1.8%, People 3,705.31 0.2 1,235 751 484 the continuation of a long slide that began 4 General editorial (22) 17,299.83 2.6 3,808 2,437 1,372 20 immediately after magazines hit their previous The New York Times Magazine 3,363.20 1.5 265 265 0 forge to front of the field high-water mark for ad pages in 2000.