Administrator Guide HP Thinpro
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Desktop 15 SP2
SUSE Linux Enterprise Desktop 15 SP2 Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Desktop 15 SP2 Introduces basic concepts of system security, covering both local and network security aspects. Shows how to use the product inherent security software like AppArmor, SELinux, or the auditing system that reliably collects information about any security-relevant events. Supports the administrator with security-related choices and decisions in installing and setting up a secure SUSE Linux Enterprise Server and additional processes to further secure and harden that installation. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -

Efficiently Mitigating Transient Execution Attacks Using the Unmapped Speculation Contract Jonathan Behrens, Anton Cao, Cel Skeggs, Adam Belay, M
Efficiently Mitigating Transient Execution Attacks using the Unmapped Speculation Contract Jonathan Behrens, Anton Cao, Cel Skeggs, Adam Belay, M. Frans Kaashoek, and Nickolai Zeldovich, MIT CSAIL https://www.usenix.org/conference/osdi20/presentation/behrens This paper is included in the Proceedings of the 14th USENIX Symposium on Operating Systems Design and Implementation November 4–6, 2020 978-1-939133-19-9 Open access to the Proceedings of the 14th USENIX Symposium on Operating Systems Design and Implementation is sponsored by USENIX Efficiently Mitigating Transient Execution Attacks using the Unmapped Speculation Contract Jonathan Behrens, Anton Cao, Cel Skeggs, Adam Belay, M. Frans Kaashoek, and Nickolai Zeldovich MIT CSAIL Abstract designers have implemented a range of mitigations to defeat transient execution attacks, including state flushing, selectively Today’s kernels pay a performance penalty for mitigations— preventing speculative execution, and removing observation such as KPTI, retpoline, return stack stuffing, speculation channels [5]. These mitigations impose performance over- barriers—to protect against transient execution side-channel heads (see §2): some of the mitigations must be applied at attacks such as Meltdown [21] and Spectre [16]. each privilege mode transition (e.g., system call entry and exit), To address this performance penalty, this paper articulates and some must be applied to all running code (e.g., retpolines the unmapped speculation contract, an observation that mem- for all indirect jumps). In some cases, they are so expensive ory that isn’t mapped in a page table cannot be leaked through that OS vendors have decided to leave them disabled by de- transient execution. To demonstrate the value of this contract, fault [2, 22]. -
SUSE Linux Enterprise Server 9 SP3 for IBM Power
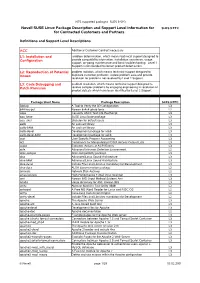
NTS supported packages SLES 9 SP3 Novell SUSE Linux Package Description and Support Level Information for SLES 9 PPC for Contracted Customers and Partners Definitions and Support Level Descriptions ACC Additional Customer Contract necessary L1: Installation and problem determination, which means technical support designed to Configuration provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of Potential problem isolation, which means technical support designed to Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed to Patch Provision resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Package Short Name Package Description SLES 9 PPC 3ddiag A Tool to Verify the 3D Configuration L3 844-ksc-pcf Korean 8x4x4 johab fonts L2 a2ps Converts ASCII Text into PostScript L3 aaa_base SuSE Linux base package L3 aaa_skel Skeleton for default users L3 aalib An ascii art library L3 aalib-64bit An ascii art library L3 aalib-devel Development package for aalib L3 aalib-devel-64bit Development package for aalib L3 acct User Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 acpid Executes Actions at ACPI Events L3 aide Advanced Intrusion Detection Environment L2 alice-compat Alice compatibility package L3 alsa Advanced Linux Sound Architecture L3 alsa-64bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. -

Xview Developer's Notes
XView Developer’s Notes 2550 Garcia Avenue Mountain View, CA 94043 U.S.A. A Sun Microsystems, Inc. Business 1994 Sun Microsystems, Inc. 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product and related documentation are protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or related documentation may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® and Berkeley 4.3 BSD systems, licensed from UNIX System Laboratories, Inc., a wholly owned subsidiary of Novell, Inc., and the University of California, respectively. Third-party font software in this product is protected by copyright and licensed from Sun’s font suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the United States Government is subject to the restrictions set forth in DFARS 252.227-7013 (c)(1)(ii) and FAR 52.227-19. The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applications. TRADEMARKS Sun, the Sun logo, Sun Microsystems, Sun Microsystems Computer Corporation, SunSoft, the SunSoft logo, Solaris, SunOS, OpenWindows, DeskSet, ONC, ONC+, and NFS are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and certain other countries. UNIX is a registered trademark of Novell, Inc., in the United States and other countries; X/Open Company, Ltd., is the exclusive licensor of such trademark. OPEN LOOK® is a registered trademark of Novell, Inc. -

Download Snipping Tool for Windows 10 Snipping Tool
download snipping tool for windows 10 Snipping Tool. Snipping Tool is an easy to use graphic capture application that can help users to very quickly manage image capture of their Windows OS desktop area, with dedicated tools for not only intuitive and detailed area capture but also extensive options for file preparation and exporting. In addition to the local image saving, the app also has built-in support for several major cloud storage locations (including Dropbox , Google Drive , and WebRequest ), an automatically generated shareable link, and even advanced support for the automatic sending of captured desktop area images to FTP server of your choice. While Windows 7 OS (and all newer versions) has a built-in tool for full desktop and area snipping tool for quick capture of screenshots, many users have expressed a need for a bit more comprehensive toolset for managing more advanced types of capture and additional options for screenshot sharing. To provide service that many users desire, Free Snipping Desktop Tool comes with its own feature set. Snipping Tool app can enable anyone to set up their real-time or delayed capture of the entire or predefined desktop area. The captured snips are not just saved to your local storage immediately. You get the chance to review them, and even use built-in highlighting tools to mark them, freely draw on them via the pen tool, or even place some of the available overlay shapes (a wide variation of arrows, rectangles, circles, and more). The user interface of the app features a canvas where your snips are displayed, and a row of 12 main tools, including Upload, Delay, Highlighter tool, Pen tool (both with customizable colors), Shapes, and Reset Snip. -

Bank of Chile Affected by Cyber-Attack Malware Found Pre
JUNE 2018 Bank of Chile Affected By Cyber-Attack On May 28, 2018, the Bank of Chile, the largest bank operating in the country, declared in a public statement that a virus presumably sent from outside of the country affected the bank’s operations. According to the announcement, the virus was discovered by internal IT experts on May 24. It impacted workstations, executives’ terminals, and cashier personnel, causing difficulties in office services and telephone banking. After the emergency, the Bank of Chile activated its contingency protocol by disconnecting some workstations and suspending normal operations to avoid the propagation of the virus. Although the virus severely affected the quality of banking services, the institution assured that the security of transactions, as well as client information and money remained safe at all times. Pinkerton assesses that cyber-attacks targeting financial institutions and international banks form part of a trend that is likely to continue increasing in 2018. So far, Pinkerton Vigilance Network sources had identified Mexico and Chile as the two most impacted by cyber-crimes in Latin America; however, Pinkerton finds that no nation is exempt from becoming a target. Clients are encouraged to review the standard regulations on cyber- security for their banks and its contingency protocols in the event of cyber-attacks. Any unrecognized banking operation or phishing scam should be reported as soon as possible to the Bank of Chile emergency phone line (600) 637 3737. For further information concerning security advise from the Bank of Chile, the following website can be consulted: https://ww3.bancochile.cl/wps/wcm/connect/personas/portal/seguridad/inicio-seguridad#Tab_ Acorden_Respon3. -

Program Name Run Command About Windows Winver Add a Device
List of Run Commands in Win7/8 to Windows Managment By Shree Krishna Maharjan in some commands need to use .msc Program Name Run Command About Windows winver Add a Device devicepairingwizard Add Hardware Wizard hdwwiz Advanced User Accounts netplwiz Authorization Manager azman Backup and Restore sdclt Bluetooth File Transfer fsquirt Calculator calc Certificates certmgr Change Computer Performance Settings systempropertiesperformance Change Data Execution Prevention Settings systempropertiesdataexecutionprevention Change Printer Settings printui Character Map charmap ClearType Tuner cttune Color Management colorcpl Command Prompt cmd Component Services comexp Component Services dcomcnfg Computer Management compmgmt.msc Computer Management compmgmtlauncher Connect to a Network Projector netproj Connect to a Projector displayswitch Control Panel control Create A Shared Folder Wizard shrpubw Create a System Repair Disc recdisc Credential Backup and Restore Wizard credwiz Data Execution Prevention systempropertiesdataexecutionprevention Default Location locationnotifications Device Manager devmgmt.msc Device Pairing Wizard devicepairingwizard Diagnostics Troubleshooting Wizard msdt Digitizer Calibration Tool tabcal DirectX Diagnostic Tool dxdiag Disk Cleanup cleanmgr Disk Defragmenter dfrgui Disk Management diskmgmt.msc Display dpiscaling Display Color Calibration dccw Display Switch displayswitch DPAPI Key Migration Wizard dpapimig Driver Verifier Manager verifier Ease of Access Center utilman EFS REKEY Wizard rekeywiz Encrypting File System -
Creating a Screenshot in Windows 7
BRYN MAWR COLLEGE February 2015 Library & Information Technology Services Creating a Screenshot in Windows 7 You can take screenshots to capture all or part of what is currently on your screen. Screenshots are useful for extracting images, relaying error messages or particular elements of your screen, and creating graphics. There multiple methods for taking screenshots, each with different capabilities. An example screenshot is shown below. Method One: Snipping Tool The Snipping Tool is found within the Start menu under All Programs -> Accessories. Once the Snipping Tool is open, use the drop-down arrow next to the New button to select what you would like to capture: the full screen, a select window, a drawn rectangle, or a free-form shape. If you selected the full screen, it will automatically capture a picture of your entire screen except for the Snipping Tool win- dow. If you select a window, you will need to click on the window you want to capture. Once selected, it will take a picture. If you select a rectangle, you will be given a crosshair cursor, indicating that you should drag and draw a rectangle around the area you would like to be captured. Once you release the cursor after dragging the rectangle, it will take a picture of your selection. If you select a free-form shape, you can then draw a shape on your screen while holding down your cursor (left mouse button). When you release the button, the Snipping Tool will capture everything in that shape. You will then be shown a preview of your capture. -

International Language Environments Guide
International Language Environments Guide Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 806–6642–10 May, 2002 Copyright 2002 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, Java, XView, ToolTalk, Solstice AdminTools, SunVideo and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. SunOS, Solaris, X11, SPARC, UNIX, PostScript, OpenWindows, AnswerBook, SunExpress, SPARCprinter, JumpStart, Xlib The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry.