Connection and VPN Bonding Objective Ideas Custom Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Zeroshell-Manual-Spanish.Pdf
Zeroshell HOWTO The multifunctional OS created by [email protected] www.zeroshell.net How to secure my private network ( Author: [email protected] ) Cómo proteger mi red privada: Esta breve guía nos permitirá configurar un firewall de red para nuestra red en menos de una hora. Zeroshell garantizará ourprivate red de ataques externos. Nuestra red privada está conectada a Internet a través de un router.Here xDSL los pasos a seguir: Primera puesta en marcha e inicio de sesión preparar un disco partición donde almacenar nuestras configuraciones de almacenamiento de nuestra configuración de los adaptadores de red de configuración de navegación en Internet Portal Cautivo de activación de servicio DNS del servicio DHCP rutas estáticas a redes remotas a servidores virtuales de Seguridad: control de las políticas por defecto En Zeroshell podemos encontrar muchas otras características importantes para las redes más complejas, lo cual es una solución escalable para nuestra red. Primera puesta en marcha e inicio de sesión: Después de arrancar desde el CD, el sistema es accesible con un navegador en el http seguro: https: / / 192.168.0.75 La aceptación de la conexión segura se nos pide usuario y contraseña para Entrar: Utilice los siguientes: Usuario: admin Contraseña: zeroshell Ahora podemos usar la interfaz web para configurar nuestro servidor de seguridad. Preparación de una partición en el disco para almacenar nuestras configuraciones: Es tan importante para salvar a nuestros Zeroshell cambios que nos permite guardar en un archivo de configuración. Se puede almacenar en un partición de un disco duro. No es necesario farmat las particiones existentes, podemos guardar nuestros archivos de configuración en particiones existentes, tales como: ext3, ReiserFS, ext2 o FAT32. -

Hotspot Feature for Wi-Fi Clients with RADIUS User Authentication on Digi Transport
Application Note 56 Hotspot feature for Wi-Fi clients with RADIUS User Authentication on Digi TransPort. Digi Support November 2015 1 Contents 1 Introduction ......................................................................................................................................... 4 1.1 Outline ......................................................................................................................................... 4 1.2 Assumptions ................................................................................................................................ 4 1.3 Corrections .................................................................................................................................. 4 2 Version .................................................................................................................................................5 3 Configuration .......................................................................................................................................5 3.1 Mobile Interface Configuration .....................................................................................................5 3.2 Ethernet Interface Configuration ................................................................................................. 6 3.2.1 ETH 0 Configuration ................................................................................................................. 6 3.2.2 ETH 12 Logical Interface Configuration .................................................................................... -

PROPOSTA DE PROJETO INTEGRADOR Discente: Rodrigo
PROPOSTA DE PROJETO INTEGRADOR Discente: Rodrigo Neitzke dos Santos Curso: Redes de Computadores E-mail: [email protected] Enderec¸o: Rua Sao˜ Paulo, 731 - Tresˆ vendas - Pelotas CEP: 96065-550 Fone(s): (53) 984047299 T´ITULO Soluc¸ao˜ de firewall com equipamento ARM. MOTIVAC¸ AO/JUSTIFICATIVA˜ Atualmente as redes de computadores ja´ estao˜ ligadas diretamente na criac¸ao˜ de uma empresa[Tanenbaum 1981], pois e´ nesta rede que trafegara´ os dados das aplicac¸oes˜ usadas no am- biente corporativo. Para a seguranc¸a da empresa e uma boa administrac¸ao˜ da seguranc¸a dos sistemas se faz necessario´ o uso de servidores firewall[Neto 2004], que tem a func¸ao˜ de proteger a rede de aces- sos nao˜ autorizados e agregado neste servidor podemos ter outros servic¸os como Roteamento, DHCP, Radius,failover, entre outros. As pequenas e ate´ medias empresas nao˜ costumam insvestir neste tipo de soluc¸ao,˜ em muitos dos casos este servic¸o nao˜ e´ aplicado e existem casos que o proprio´ modem ADSL realiza este servic¸o, no qual podera´ provocar vulnerabilidades e baixo desempenho nesta rede de computadores. Como soluc¸ao˜ de baixo custo para as empresas de pequeno porte, sera´ aplicado um conjunto de hardware embarcado com processador ARM[techtudo ], junto com uma distribuic¸ao˜ linux, no qual proporcionara´ desempenho e varias´ funcionalidades. OBJETIVO GERAL Instalar e configurar um servidor de firewall em equipamento ARM e analisar seu desempenho. OBJETIVOS ESPEC´IFICOS Os objetivos espec´ıficos sao:˜ • Definir modelo do hardware [Orangepi 2018] a ser usado no projeto. • Estudo do sistema linux[Ricciardi ] para criac¸ao˜ do firewall. -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian -

Zeroshell HOWTO
Zeroshell HOWTO The multifunctional OS created by [email protected] www.zeroshell.net How to secure my private network ( Author: [email protected] ) How to secure my private Network : This short guide will let us configure a network firewall for our network in less than one hour. Zeroshell will secure our private network from external attacks. Our private network is connected to internet through a xDSL router. Here the steps to follow : First start and login Preparing a partition disk where to store our configurations Storing our configuration Network adapters configuration Internet surfing Captive Portal activation DNS Service DHCP Service Static routes to remote networks Virtual Servers Security: check default policies In Zeroshell we can find many other important features for more complex networks; this is a great scalable solution for our network. First start and login: After booting from CD, the system is reachable with a browser at the http secure: https://192.168.0.75 Accepting the secure connection we are asked user and password to login: Use these: User: admin Password: zeroshell Now we can use web interface to setup our firewall. Preparing a partition disk where to store our configurations: It’s so important to save our changes that Zeroshell lets us save them in a configuration file. It can be stored in a partition on a hard disk. It’s not necessary to farmat any existing partitions, we can save our configuration files in existing partition such as: ext3, reiserfs, ext2 o fat32. For my own preference I prefer to create a new partition ext3. -

Sintesi Catalogo Competenze 2
Internet of Things Competenze Campi di applicazione • Progettazione e sviluppo di firmware su micro • Monitoraggio ambientale meteorologico di para- controllori a basso e bassissimo consumo quali ad metri climatici e parametri della qualità dell’aria, esempio Arduino, Microchip, NXP, Texas Instru- anche in mobilità ments e Freescale • Monitoraggio ambientale distribuito per l’agricol- • Sviluppo su PC embedded basati su processori tura di precisione ARM e sistema operativo Linux quali ad esempio • Monitoraggio della qualità dell’acqua e dei parame- Portux, Odroid, RaspberryPI ed Nvidia Jetson tri di rischio ambientale (alluvioni, frane, ecc.) • Progettazione e sviluppo di Wired e Wireless Sen- • Monitoraggio di ambienti indoor (scuole, bibliote- sor Networks basate su standard quali ZigBee, che, uffici pubblici, ecc) SimpliciTI, 6LoWPAN, 802.15.4 e Modbus • Smart building: efficienza energetica, comfort am- • Progettazione e sviluppo di sistemi ad alimentazio- bientale e sicurezza ne autonoma e soluzioni di Energy harvesting • Utilizzo di piattaforme microUAV per misure distri- • Ottimizzazione di software e protocolli wireless buite, per applicazioni di fotogrammetria, teleme- per l’uso efficiente dell’energia all’interno di nodi tria e cartografia, per sistemi di navigazione auto- ad alimentazione autonoma matica basata su sensoristica e image processing, • Design e prototipazione (con strumenti CAD, pianificazione e gestione delle missioni stampante 3D, ecc) di circuiti elettronici per l’inte- • Smart Grid locale per l’ottimizzazione -

Application Note 48 WPA Enterprise Wi-Fi Client to Digi Transport
Application Note 48 WPA Enterprise Wi-Fi Client to Digi TransPort September 2016 Contents 1 Introduction ............................................................................................................................................... 4 1.1 Outline ............................................................................................................................................... 4 1.2 Assumptions ...................................................................................................................................... 5 1.1 Corrections ........................................................................................................................................ 5 1.2 Version ............................................................................................................................................... 5 2 Digi TransPort router configuration .......................................................................................................... 6 2.1 Configuration overview ..................................................................................................................... 6 2.2 LAN interface configuration .............................................................................................................. 6 2.3 WAN interface configuration ............................................................................................................. 7 2.4 Wi-Fi Access Point configuration ...................................................................................................... -

Bab 1 Pendahuluan
BAB 1 PENDAHULUAN 1.1 Latar Belakang Network Function Virtualization atau biasa yang disebut NFV merupakan sebuah konsep baru dalam mendesain, menyebarkan, dan mengelola sebuah layanan jaringan dengan cara pembuatan virtual sebuah perangkat jaringan dari yang sebelumnya berbentuk fisik atau perangkat keras sehingga dapat dipakai dan dipindahkan di berbagai lokasi jaringan yang diperlukan tanpa harus melakukan pemasangan alat baru. NFV memungkinkan beberapa perangkat jaringan dapat berjalan pada satu komputer. Perangkat – perangkat jaringan yang divirtualkan pada NFV disebut sebagai VNF (Virtual Network Function). Untuk menjalankan VNF dibutuhkan sebuah hypervisor yang mengatur manajemen hardware yang digunakan. Hypervisor atau yang dikenal sebagai virtual machine management dibagi menjadi 2 tipe, yaitu bare-metal hypervisor dan hosted hypervisor. Bare-metal hypevisor dapat berjalan langsung pada perangkat keras komputer sedangkan hosted hypervisor memerlukan operating system environment (OSE) untuk menjalankannya [1]. Salah satu contoh bare- metal hypervisor adalah XEN. Xen ProjectTM adalah platform virtualisasi open source yang mendukung beberapa cloud terbesar dalam produksi saat ini. Amazon Web Services, Aliyun, Rackspace Cloud Umum, Verizon Cloud dan banyak layanan hosting menggunakan software Xen [2]. Salah satu contoh VNF adalah virtual firewall. Kelebihan virtual firewall dibandingkan firewall fisik adalah mudah dikelola, dapat dipakai sesuai kebutuhan, dan efektivitas biaya [3]. Pada tugas akhir ini virtual firewall yang digunakan adalah OPNsense, pfSense, dan IPFire karena ketiga firewall tersebut bisa didapatkan secara gratis dan bersifat open source serta ketiga firewall tersebut dapat dikonfigurasi melalui web. pfSense merupakan firewall berbasis FreeBSD yang sangat populer untuk solusi keamanan serta user dapat melakukan modifikasi dan mudah dalam instalasi [4]. IPFire adalah sebuah distribusi Linux yang berfokus pada setup yang mudah, penanganan yang yang baik, dan tingkat keamanan yang tinggi [5]. -
GNU/Linux Distro Timeline LEAF Version 10.9 Skolelinux Lindows Linspire Authors: A
1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 Libranet Omoikane (Arma) Gibraltar GNU/Linux distro timeline LEAF Version 10.9 Skolelinux Lindows Linspire Authors: A. Lundqvist, D. Rodic - futurist.se/gldt Freespire Published under the GNU Free Documentation License MEPIS SimplyMEPIS Impi Guadalinex Clonezilla Live Edubuntu Xubuntu gNewSense Geubuntu OpenGEU Fluxbuntu Eeebuntu Aurora OS Zebuntu ZevenOS Maryan Qimo wattOS Element Jolicloud Ubuntu Netrunner Ylmf Lubuntu eBox Zentyal Ubuntu eee Easy Peasy CrunchBang gOS Kiwi Ubuntulite U-lite Linux Mint nUbuntu Kubuntu Ulteo MoLinux BlankOn Elive OS2005 Maemo Epidemic sidux PelicanHPC Inquisitor Canaima Debian Metamorphose Estrella Roja BOSS PureOS NepaLinux Tuquito Trisquel Resulinux BeatriX grml DeadCD Olive Bluewall ASLinux gnuLiNex DeMuDi Progeny Quantian DSL-N Damn Small Linux Hikarunix Damn Vulnerable Linux Danix Parsix Kanotix Auditor Security Linux Backtrack Bioknoppix Whoppix WHAX Symphony OS Knoppix Musix ParallelKnoppix Kaella Shabdix Feather KnoppMyth Aquamorph Dreamlinux Morphix ZoneCD Hiwix Hiweed Deepin Kalango Kurumin Poseidon Dizinha NeoDizinha Patinho Faminto Finnix Storm Corel Xandros Moblin MeeGo Bogus Trans-Ameritech Android Mini Monkey Tinfoil Hat Tiny Core Yggdrasil Linux Universe Midori Quirky TAMU DILINUX DOSLINUX Mamona Craftworks BluePoint Yoper MCC Interim Pardus Xdenu EnGarde Puppy Macpup SmoothWall GPL SmoothWall Express IPCop IPFire Beehive Paldo Source Mage Sorcerer Lunar eIT easyLinux GoboLinux GeeXboX Dragora -
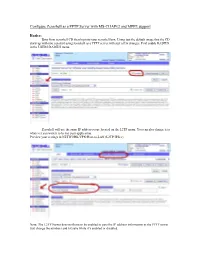
Configure Zeroshell As a PPTP Server with MS-Chapv2 and MPPE Support
Configure Zeroshell as a PPTP Server with MS-CHAPv2 and MPPE support Basics: Boot from zeroshell CD then log into your zeroshell box. Using just the default image that the CD starts up with you can start using zeroshell as a PPTP server with just a few changes. First enable RADIUS in the USERS/RADIUS menu. Zeroshell will use the same IP address scope located on the L2TP menu. You can also change it to whatever you want it to be for your application. Preview your settings in NETWORK/VPN/Host-to-LAN (L2TP/IPSec) Note: The L2TP Server does not have to be enabled to pass the IP address information to the PPTP server. Just change the numbers and hit save while it’s enabled or disabled. Last thing we need to do is enable ssh for the actual configurations that will enable the PPTP server. Use the SYSTEM/Setup/SSH menu to enable this feature. Advanced: This part of the configurations take place in the CLI so if you don’t follow these instructions closely or don’t feel confident using the CLI then you probably shouldn’t be using zeroshell. That statement will either inspire you or strike fear in your heart. Well go and start your ssh session with the zeroshell box and use the shell prompt. We will be working with 2 files to enable and configure the PPTP server. /etc/ pptpd.conf /etc/ppp/ options.pptpd Copy these 2 files to a location that will not get wiped every time you reboot. Use the / Database for any static files that you don’t want mangled after a reboot or service restart. -

Une Box Nano-Serveur Autonome Raspberry Pi3 Mokhtar Ben Henda
Une Box nano-serveur autonome Raspberry Pi3 Mokhtar Ben Henda To cite this version: Mokhtar Ben Henda. Une Box nano-serveur autonome Raspberry Pi3 : Pour diffuser localement des contenus Web y compris dans des milieux non connectés. [Rapport Technique] AUF (Agence Universitaire de la Francophonie); IFIC. 2018. hal-02532371 HAL Id: hal-02532371 https://hal.archives-ouvertes.fr/hal-02532371 Submitted on 5 Apr 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution - ShareAlike| 4.0 International License Pour diffuser localement des contenus Web y compris dans des milieux non connectés Mokhtar BEN HENDA Octobre 2018 0 Table des matières Avant-propos ................................................................................................................................... 2 Introduction des concepts ............................................................................................................... 5 La réplication (mirroring)............................................................................................................ -

Zerotruth Multicp
ZEROTRUTH MULTICP CENTRALIZED MANAGEMENT AND REMOTE ADMINISTRATION OF MULTIPLE CAPTIVE PORTALS TRUTHAHN Nello Dalla Costa - Johnathan Ferrarini http://www.zerotruth.net Revised by Matteo Guglielmi INTRODUCTION ZeroTruth (ZT) (http://www.zerotruth.net) was developed to extend the easy-to-use web inter- face of ZeroShell (ZS) (http://www.zeroshell.org), which is a “linux distribution for servers and em- bedded devices aimed at providing the main network services a LAN requires”, with particular attention to the Captive Portal (CP) network service. ZeroTruth, in a glance, adds a new section to the stock ZeroShell web interface allowing adminis- trators to manage multiple remote captive portals as if they were just one. The idea of creating ZeroTruth originated from one of the most requested features posted on the ZeroShell forum, which was two fold: 1. to manage one or more remote captive portals in a centralized fashion (this feature is available starting from ZeroTruth version 1.0.beta1), 2. to not eclipse the rich set of functions provided by ZeroShell. Out of this broadened interest, the ZeroTruth project was born. ZeroTruth extends the functionality of ZeroShell by adding a new set of functions such as self- registration, profile-shaping, time-limits, squid web-cache and others. Please note that ZeroTruth has profound roots into ZeroShell code therefore, ZeroTruth must be installed side by side with ZeroShell (ZeroTruth cannot be installed on its own). As a technical note, I would recommend to layout the logical network topology in the star con- figuration (see frontpage) in which only one central station (the hub) is configured as server, while all other stations (the spokes) are configured as clients.