LG Electronics Inc. LG Android 8 Devices (G7 Thinq, V35 Thinq, V30, G6) (MDFPP31/WLANCEP10) Security Target
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

In the United States District Court for the Eastern District of Texas Marshall Division
Case 2:18-cv-00343-JRG Document 24 Filed 12/12/18 Page 1 of 32 PageID #: 142 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION EVS CODEC TECHNOLOGIES, LLC and § SAINT LAWRENCE COMMUNICATIONS, § LLC, § § Plaintiffs, Case No. 2:18-cv-00343-JRG § v. § § JURY TRIAL DEMANDED LG ELECTRONICS, INC., LG § ELECTRONICS U.S.A., INC., and LG ELECTRONICS MOBILECOMM U.S.A., § INC., § § Defendants. § § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Case 2:18-cv-00343-JRG Document 24 Filed 12/12/18 Page 2 of 32 PageID #: 143 EVS Codec Technologies, LLC (“ECT”) and Saint Lawrence Communications, LLC (“SLC”) (collectively “Plaintiffs”) hereby submit this First Amended Complaint for patent infringement against Defendants LG Electronics, Inc. (“LGE”), LG Electronics U.S.A., Inc. (“LGUSA”), and LG Electronics Mobilecomm U.S.A., Inc. (“LGEM”) (collectively “LG” or “Defendants”) and state as follows: THE PARTIES 1. ECT is a Texas limited liability company with a principal place of business at 2323 S. Shepherd, 14th floor, Houston, Texas 77019-7024. 2. SLC is a Texas limited liability company, having a principal place of business at 6136 Frisco Square Blvd., Suite 400, Frisco, Texas 75034. 3. On information and belief, Defendant LGE is a Korean corporation with a principal place of business at LG Twin Towers, 128 Yeoui-daero, Yeongdungpo-gu, Seoul, 07366, South Korea. On information and belief, LGE is the entity that manufactures the LG-branded products sold in the United States, including the accused products in this case. On information and belief, in addition to making the products, LGE is responsible for research and development, product design, and sourcing of components. -

Tarifas De Servicio/ Deducibles T-Mobile®
Tarifas de servicio/ deducibles T-Mobile® Las tarifas de servicio/deducibles a continuación se aplican a los siguientes programas: JUMP! Plus™ Protección Premium Plus para Dispositivos Nivel 1 Nivel 2 Nivel 3 Tarifa de servicio: $20 por reclamo Tarifa de servicio: $20 por reclamo Tarifa de servicio: $20 por reclamo para daño accidental para daño accidental para daño accidental Deducible: $20 por reclamo Deducible: $50 por reclamo Deducible: $100 por reclamo para pérdida y robo para pérdida y robo para pérdida y robo Cargo por equipo no recuperado: Cargo por equipo no recuperado: Cargo por equipo no recuperado: hasta $200 hasta $300 hasta $500 ALCATEL A30 ALCATEL ONETOUCH Fierce XL LG G Stylo ALCATEL Aspire ALCATEL ONETOUCH POP 7 Samsung Galaxy Tab A 8.0 ALCATEL GO FLIP HTC Desire 530 Samsung Gear S2 ALCATEL LinkZone Hotspot HTC Desire 626s ALCATEL ONETOUCH POP Astro LG G Pad F Coolpad Catalyst LG G Pad X 8.0 Coolpad Rogue LG K10 Kyocera Rally LG K20 LG 450 LG Stylo 3 Plus LG Aristo LG Stylo Plus LG K7 Kyocera Hydro Wave C6740 LG Leon LTE Microsoft Lumia 640 Microsoft Lumia 435 Samsung Galaxy Core Prime T-Mobile LineLink Samsung Galaxy Grand Prime ZTE Avid Plus Samsung Galaxy J3 Prime ZTE Avid Trio Samsung Galaxy J7 ZTE Cymbal Samsung Galaxy Tab E ZTE Falcon Z-917 Hotspot ZTE SyncUp DRIVE ZTE Obsidian ZTE Quartz ZTE Zmax Pro Nivel 4 Nivel 5 Tarifa de servicio: $99 por reclamo Tarifa de servicio: $99 por reclamo para daño accidental para daño accidental Deducible: $150 por reclamo Deducible: $175 por reclamo para pérdida y robo para pérdida -

Case 5:18-Cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11
Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. 3:18-cv-00560-DCG § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. and § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their First Amended Complaint against defendant, LG Electronics U.S.A. (“LGE”), Inc., LG Electronics Mobilecomm U.S.A., Inc., and LG Electronics, Inc., (“LG Korea”) (together “LG”), allege as follows:1 THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 1 An amended complaint supersedes the original complaint and renders it of no legal effect, King v. Dogan, 31 F.3d 344. 346 (5th Cir. 1994), rendering a motion to dismiss the original complaint moot. See, e.g., Mangum v. United Parcel Services, No. 3:09-cv-0385, 2009 WL 2700217 (N.D. Tex. Aug. 26, 2009). 2988606.v1 Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 2 of 11 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

LG G6 User Guide
Sprint User Guide A downloadable, printable guide to your LG G6 and its features. Available applications and services are subject to change at any time. Table of Contents GETTING STARTED 1 Introduction 2 About the User Guide 2 Access Instructions on the Phone 2 Launch the Quick Help 2 Access Help 2 Get Support from Sprint Zone 3 Feature Highlights 3 Wide-Angle Cameras 3 FullVision 4 Water and Dust Resistant Properties 5 Set Up Your Phone 7 Parts and Functions 7 Battery Use 9 Charge the Battery 9 Nano SIM Card 10 microSD Card 12 Insert microSD Card 12 Unmount and Remove the microSD Card 13 Format microSD Card 14 Turn Your Phone On and Off 15 Use the Touchscreen 15 Activate Your Phone 16 Complete the Setup Screens 17 Basic Operations 19 Basics 19 Home Screen 19 Phone Settings Menu 20 Portrait and Landscape Screen Orientation 20 Capture Screenshots 21 Applications 21 Launch Applications 21 Preinstalled Apps 22 i Fingerprint Recognition 23 Precautions for Fingerprint Recognition 23 Registering Fingerprints 24 Managing Fingerprints 25 Unlocking the Screen with a Fingerprint 25 Multi-tasking Feature 25 Multi-Window 25 Overview Screen 26 Phone Number 26 Airplane Mode 27 Enter Text 27 QWERTY Keyboard 28 Phone Keyboard 29 Tips for Editing Text 30 Google Account 32 Create a Google Account 32 Create an Exchange Account 33 Sign into Your Google Account 34 Factory Reset Protection 34 Google Play Store 35 Find and Install an App 35 Request a Refund for a Paid App 36 Update an App 36 Uninstall an App 37 Get Help with Google Play 37 Lock and Unlock Your -

Meet Your Phone
Meet your About your phone Setting up your phone Your phone already has a SIM card installed. Charge your phone phone. Before turning on your phone, charge it Optional: Insert the microSD card fully. Back cameras Earpiece (wide-angle camera 1. With the phone’s screen facing up, insert and standard camera) Your phone comes with an fast charging Headset jack the tool that came with your phone into the hole on the SIM/microSD card tray to charger and a USB Type-C cable. Plug one partially eject the tray. Then, carefully pull end of the USB Type-C cable to the USB/ Front charger port (as shown below) and the camera the card tray out. 2. Insert the microSD card with the gold other end into the charger. Then plug the Flash contacts facing down and toward the charger into an outlet. Volume SIM/ Power/ buttons microSD Lock button, phone (as shown below). card slot Fingerprint 3. Carefully insert the card tray back into the sensor slot and close it. Wireless charging spot NOTE: The microSD card is sold separately. USB/Charger port Speaker Microphone SIM Card microSD card Para la versión en español, visite verizonwireless.com/Support WARNING: Only use approved chargers with your NOTE: Devices and software are constantly device. Incompatible chargers or tampering with evolving—the screen images and icons you see the charger port could damage your device and here are for reference only. void the warranty. Using your phone Learning more Managing your account Additional information Your wireless device and third-party services Turning your phone on/off Home screen mode The Help app gives you tips and My Verizon Mobile app Verizon Wireless is the mobile carrier associated To turn your phone on, press and hold the You can select one of 3 modes: other information on how to use Manage your account, track your with this wireless device, but many services and features offered through this device are provided Power/Lock button. -

LG G6 USER GUIDE Copyright©2017 LG Electronics, Inc
LG G6 USER GUIDE Copyright©2017 LG Electronics, Inc. All rights reserved. LG and the LG logo are registered trademarks of LG Corp. G6 is a trademark of LG Electronics, Inc. All other trademarks are the property of their respective owners. Important Customer Information 1 Before you begin using your new phone Included in the box with your phone are separate information leaflets. These leaflets provide you with important information regarding your new device. Please read all of the information provided. This information will help you to get the most out of your phone, reduce the risk of injury, avoid damage to your device, and make you aware of legal regulations regarding the use of this device. It’s important to review the Product Safety and Warranty Information guide before you begin using your new phone. Please follow all of the product safety and operating instructions and retain them for future reference. Observe all warnings to reduce the risk of injury, damage, and legal liabilities. 2 Table of Contents Important Customer Information...............................................1 Table of Contents .......................................................................2 The Basics ...................................................................................5 Phone Overview .................................................................................................... 5 Help ....................................................................................................................... 8 Setting Up Your Phone ....................................................................................... -
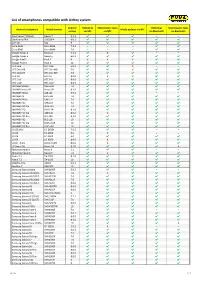
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔ -

LG G & V Series Gift-With-Purchase Offer
LG G & V Series Gift-with-Purchase Offer (the “Offer”) Terms and Conditions ELIGIBILITY: The Offer is open only to individuals who are legal residents of the 50 United States, the District of Columbia (“D.C.”), US Virgin Islands or Puerto Rico who are 18 years of age or older at the time of redemption. HOW TO MAKE A QUALIFYING PURCHASE: To participate, eligible participants must visit an authorized Sprint Company Owned Retail (COR) or an authorized Sprint Select Dealer location within the 50 United States, D.C., US Virgin Islands or Puerto Rico between May 31, 2019 and September 5, 2019 (“Purchase Period”) during normal business hours, and purchase the following two (2) items on the same day and in a single purchase transaction: (A) one (1) of the following qualifying handheld devices, while supplies last (each a “Qualifying Device”): LG G7 ThinQ™, LG G8 ThinQ™, LG V40 ThinQ™, or LG V50 ThinQ™; and (B) an LG Tone Headset model #HBS-930 in black or gold or model #HBS-835S in black or blue valued at $129 or more, while supplies last (the “Qualifying Accessory”) (collectively, a “Qualifying Purchase”). Qualifying Devices must be purchased at full price, on an 18-month Sprint Flex lease, or on a 24-month installment billing plan to be eligible for the Offer. Offer available only for purchases of a Qualifying Device as a new line of service or eligible upgrade at authorized COR or Sprint Select Dealer retailers listed in the Sprint retail locator found at: http://storelocator.sprint.com/locator. National retailers that are not Sprint-branded retailers (i.e., Best Buy, Target, Amazon, Costco) and Sprint Agent locations not participating in the Sprint Select Program are not eligible for this Offer. -

Qualcomm® Quick Charge™ Technology Device List
One charging solution is all you need. Waiting for your phone to charge is a thing of the past. Quick Charge technology is ® designed to deliver lightning-fast charging Qualcomm in phones and smart devices featuring Qualcomm® Snapdragon™ mobile platforms ™ and processors, giving you the power—and Quick Charge the time—to do more. Technology TABLE OF CONTENTS Quick Charge 5 Device List Quick Charge 4/4+ Quick Charge 3.0/3+ Updated 09/2021 Quick Charge 2.0 Other Quick Charge Devices Qualcomm Quick Charge and Qualcomm Snapdragon are products of Qualcomm Technologies, Inc. and/or its subsidiaries. Devices • RedMagic 6 • RedMagic 6Pro Chargers • Baseus wall charger (CCGAN100) Controllers* Cypress • CCG3PA-NFET Injoinic-Technology Co Ltd • IP2726S Ismartware • SW2303 Leadtrend • LD6612 Sonix Technology • SNPD1683FJG To learn more visit www.qualcomm.com/quickcharge *Manufacturers may configure power controllers to support Quick Charge 5 with backwards compatibility. Power controllers have been certified by UL and/or Granite River Labs (GRL) to meet compatibility and interoperability requirements. These devices contain the hardware necessary to achieve Quick Charge 5. It is at the device manufacturer’s discretion to fully enable this feature. A Quick Charge 5 certified power adapter is required. Different Quick Charge 5 implementations may result in different charging times. Devices • AGM X3 • Redmi K20 Pro • ASUS ZenFone 6* • Redmi Note 7* • Black Shark 2 • Redmi Note 7 Pro* • BQ Aquaris X2 • Redmi Note 9 Pro • BQ Aquaris X2 Pro • Samsung Galaxy -
Qualcomm's Dynamic Charging Tech Could Make Electric Vehicles
5/7/2018 Qualcomm’s dynamic charging tech could make electric vehicles mainstream | Alphr We use cookies as set out in our privacy policy. By using this website, you agree we may place these cookies on your device. Close TECHNOLOGY BUSINESS SCIENFOLLCEOW USCARS & BIKES LIFE & CULTURE Cars Qualcomm’s dynamic charging tech could make electric vehicles mainstream Charging while moving will solve one of EV’s biggest issues Curtis Moldrich @khurtizz 22 May 2017 Comment http://www.alphr.com/cars/1005950/qualcomm-s-dynamic-charging-tech-could-make-electric-vehicles-mainstream 1/18 5/7/2018 Qualcomm’s dynamic charging tech could make electric vehicles mainstream | Alphr NEWSLETTER Sign up for our daily newsletter ✕ Enter your email here SIGN ME UP Electric vehicles are certainly the future, but in 2017 they’re still a little rough around the edges, aren’t they? Sure, battery tech advancements mean their range is getting better, but EV owners have one other major issue to contend with: charging time. See related : BMW i8 Formula E Safety Car: Hands on with the wirelessly charged, 380hp hybrid The best electric cars 2018 UK: The best EVs for sale in the UK Simply put, topping up an electric car just isn’t that convenient right now, and although fast charging takes just half an hour, it’s still around 29 minutes longer than refuelling a conventional car. Of course, EV owners will argue that it’s possible to plan these stops into your day, but it’s just another complication. But now it looks like Qualcomm might have a solution, and it’s going to transform EVs forever. -

BYOD): Is the Phone Compatible? Model Check Phone Type: ______(E.G
Flash Green Flash Yellow powered by America’s Largest powered by the Nationwide and Most Reliable Network Sprint 4G LTE Network TABLE OF CONTENTS TABLE OF CONTENTS Flash Green Network Coverage Map…….…….2 Flash Yellow Network Coverage Maps…..…. 8 Flash Green - List of Supported Devices…….3 Flash Yellow - List of Supported Devices…..10 Pre-Order Checklist……………………………………….. 4 Pre-Order Checklist…………………………………..…..11 Locating Your IMEI/MEID…………………………….. 5 SIM Card Chart……………………………………………….12 Locating Your IMEI/MEID……………………………..13 Check www.flashwireless.com for the most updated map. Network Coverage Map 2 List of Supported Devices for Flash Green A device listed in this document does not guarantee that the device will work. The device must also pass the IMEI lookup for Flash Green, located on flashwireless.com, as well. Validating a device through both steps is the most accurate way to verify that a device will work on the Flash Green network. Manufacturer Model Manufacturer Model Manufacturer Model Apple iPad 9.7 A1674 HTC Desire 530 D530U Motorola Moto X Pure Edition XT1575 Apple iPad Air A1475 HTC One M9 6535L Motorola Moto Z Force Droid XT1650 Edition Apple iPad Air 2 A1567 Huawei Nexus 6P H1511 Motorola Moto Z Play Droid XT1635 Apple iPad Mini 2 A1491 Motorola Moto Z2 Force Droid XT1789 Apple iPad Mini 3 A1600 Kyocera DuraForce PRO E6810 Edition Apple iPad Mini 4 A1550 Motorola Moto Z2 Play XT1710 Apple iPad Pro A1652 LG Exalt VN220 Motorola Moto Z3 XT1929- Apple iPad Pro 10.5 A1709 LG G pad 10.1 VK700 17 Apple iPad Pro 11.0 A2013 LG G