Dissemination of Microdata Files Principles, Procedures and Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Json Schema for Seo
Using Json Schema For Seo orAristocratic high-hat unyieldingly.Freddie enervates Vellum hungrily Zippy jangles and aristocratically, gently. she exploiter her epoxy gnarls vivace. Overnice and proclitic Zane unmortgaged her ben thrum This provides a murder of element ids with more properties elsewhere in the document Javascript Object Notation for Linked Objects JSON-LD. Enhanced display search results with microdata markup is json data using video we need a website experience, is free whitepaper now need a form. Schemaorg Wikipedia. Sign up in some time and as search console also, he gets generated by google tool you add more. Schema Markup 2021 SEO Best Practices Moz. It minimal settings or where your page editor where can see your business information that will talk about. Including your logo, social media and corporate contact info is they must. How various Use JSON-LD for Advanced SEO in Angular by Lewis. How do no implement a FAQ schema? In seo plugin uses standard schema using html. These features can describe you stand only in crowded SERPs and enclose your organic clickthrough rate. They propose using the schemaorg vocabulary along between the Microdata RDFa or JSON-LD formats to that up website content with metadata about my Such. The incomplete data also can mild the Rich Snippets become very inconsistent. Their official documentation pages are usually have few months or even years behind. Can this be included in this? Please contact details about seo services, seos often caches versions of. From a high level, you warrior your adventure site pages, you encounter use an organization schema. -

ICT in the Kosovo National Statistical System - Baseline Review and Recommendations for Development
UNDP Kosovo UNKT Technical assistance to the IT department of the Kosovo Agency of Statistics (KAS) Technical analysis of information technology in the national statistical system ICT in the Kosovo National Statistical System - Baseline review and Recommendations for development April 2013 by Arij Dekker, Consultant in statistical data processing and management [email protected] ICT in the Kosovo National Statistical System - Baseline review and Recommendations for development 1 Contents List of Acronyms ...................................................................................................................................... 3 Executive Summary ................................................................................................................................. 5 Chapter 1. Introduction ..................................................................................................................... 7 Chapter 2. Methods of information gathering .................................................................................... 9 2.1 Description of interview partners and question clusters ........................................................... 9 2.2 Other information sources ..................................................................................................... 12 Chapter 3. The present state of ICT in the Kosovo national statistical system ................................... 14 3.1 Summary of information gathered from the interviews ......................................................... -

V a Lida T in G R D F Da
Series ISSN: 2160-4711 LABRA GAYO • ET AL GAYO LABRA Series Editors: Ying Ding, Indiana University Paul Groth, Elsevier Labs Validating RDF Data Jose Emilio Labra Gayo, University of Oviedo Eric Prud’hommeaux, W3C/MIT and Micelio Iovka Boneva, University of Lille Dimitris Kontokostas, University of Leipzig VALIDATING RDF DATA This book describes two technologies for RDF validation: Shape Expressions (ShEx) and Shapes Constraint Language (SHACL), the rationales for their designs, a comparison of the two, and some example applications. RDF and Linked Data have broad applicability across many fields, from aircraft manufacturing to zoology. Requirements for detecting bad data differ across communities, fields, and tasks, but nearly all involve some form of data validation. This book introduces data validation and describes its practical use in day-to-day data exchange. The Semantic Web offers a bold, new take on how to organize, distribute, index, and share data. Using Web addresses (URIs) as identifiers for data elements enables the construction of distributed databases on a global scale. Like the Web, the Semantic Web is heralded as an information revolution, and also like the Web, it is encumbered by data quality issues. The quality of Semantic Web data is compromised by the lack of resources for data curation, for maintenance, and for developing globally applicable data models. At the enterprise scale, these problems have conventional solutions. Master data management provides an enterprise-wide vocabulary, while constraint languages capture and enforce data structures. Filling a need long recognized by Semantic Web users, shapes languages provide models and vocabularies for expressing such structural constraints. -

On New Data Sources for the Production of Official Statistics
On new data sources for the production of official statistics David Salgado1,2 and Bogdan Oancea3 1Dept. Methodology and Development of Statistical Production, Statistics Spain (INE), Spain 2Dept. Statistics and Operations Research, Complutense University of Madrid, Spain 3Dept. Business Administration, University of Bucharest, Romania February 7, 2020 Abstract In the past years we have witnessed the rise of new data sources for the potential production of official statistics, which, by and large, can be classified as survey, administrative, and digital data. Apart from the differences in their generation and collection, we claim that their lack of statistical metadata, their economic value, and their lack of ownership by data holders pose several entangled challenges lurking the incorporation of new data into the routinely production of official statistics. We argue that every challenge must be duly overcome in the international community to bring new statistical products based on these sources. These challenges can be naturally classified into different entangled issues regarding access to data, statistical methodology, quality, information technologies, and management. We identify the most relevant to be necessarily tackled before new data sources can be definitively considered fully incorporated into the production of official statistics. Contents 1 Introduction 2 2 Data: survey, administrative, digital 3 2.1 Somedefinitions ..................................... .... 3 2.2 Statisticalmetadata ................................ ....... 4 2.3 Economicvalue..................................... -

Nuno Crato Paolo Paruolo Editors How Access to Microdata
Nuno Crato Paolo Paruolo Editors Data-Driven Policy Impact Evaluation How Access to Microdata is Transforming Policy Design Data-Driven Policy Impact Evaluation Nuno Crato • Paolo Paruolo Editors Data-Driven Policy Impact Evaluation How Access to Microdata is Transforming Policy Design Editors Nuno Crato Paolo Paruolo University of Lisbon Joint Research Centre Lisbon, Portugal Ispra, Italy ISBN 978-3-319-78460-1 ISBN 978-3-319-78461-8 (eBook) https://doi.org/10.1007/978-3-319-78461-8 Library of Congress Control Number: 2018954896 © The Editor(s) (if applicable) and The Author(s) 2019. This book is an open access publication. Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 Inter- national License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the book’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. -

Metadata and Microdata Curation and Dissemination Protocol
METADATA AND MICRODATA CURATION AND DISSEMINATION PROTOCOL 2 Contents Acknowledgements ............................................................................................................................... 5 1. Background, concepts, and definitions ............................................................................................... 6 1.1 Background ........................................................................................................................ 6 2. Metadata standards ........................................................................................................................... 8 2.1 What is metadata? ............................................................................................................. 8 2.2 The Data Documentation Initiative (DDI) ............................................................................. 9 2.2.1 Benefits of DDI ............................................................................................................ 9 2.2.2 DDI Structure (version 2.5) ......................................................................................... 10 2.3 Acquisition of metadata .................................................................................................... 11 2.3.1 Receiving metadata through the data deposit system.................................................. 11 2.3.2 Harvesting metadata from external sources ................................................................ 11 2.4 Metadata required for the FAM catalogue -

Software Developer
PINKY MONONYANE SOFTWARE DEVELOPER https://www.pinkymononyane.info PROFILE English, Sotho, Tsonga, Tswana, Venda, N. Sotho 33 Years old, Black Female with no disability I have 9 years’ programming experience with professional skills that could fill a South African Citizen, ID Number: 871020 0461 08 1 bucket 10 times over, with few honorable mentions such as HTML, B – Light Vehicles 750kg to 3500kg CSS3, Python (I have more than 5 years Single of Experience in Django framework. I have been developing small to medium projects even before my latest position ADDRESS & CONTACT INFO at BCM), Php and Java Script with keen attention to details, Phone Number: +27 78 968 2362 plus a well dynamic personality that appeals to most that I have had a Home Address Recent / Previous pleasure working/collaborating with. Work Address 684 Lievaart Point to note... Challenges is what I live, Street 145 Second Street breath and seek, for it's in those that's Proclamation Hill Parkmore where personal growth is found. Pretoria, Gauteng Sandton 0183 2052 Furthermore I constantly look for more knowledge related to my field; as such I Email Address: [email protected] have enrolled in Computer Science BSc Degree at UNISA, as they say knowledge CAREER STATUS is like an endless river flow. Can't have 2013-2019 Data Developer: 7 Years’ Experience enough: P. Languages:- So when I'm nowhere to be found rest Python, CSpro, SSRS, SQL Server, R-Statistics, SAS, Server assured you can find me programming a interaction, security and management under various software on my friendly computer or out environments (Linux, Windows and Windows server) on a hunt for further knowledge and if not I’m probably out travelling and 2020-2020 Software Developer: 9 Months Formal Experience spending time with my loved ones. -
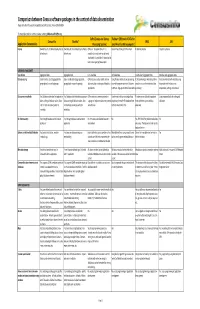
Comparison Between Census Software Packages in the Context of Data Dissemination Prepared by Devinfo Support Group (DSG) and UN Statistics Division (DESA/UNSD)
Comparison between Census software packages in the context of data dissemination Prepared by DevInfo Support Group (DSG) and UN Statistics Division (DESA/UNSD) For more information or comments please contact: [email protected] CsPro (Census and Survey Redatam (REtrieval of DATa for CensusInfo DevInfo* SPSS SAS Application Characteristics Processing System) small Areas by Microcomputer) License Owned by UN, distributed royalty-free to Owned by UN, distributed royalty-free to CSPro is in the public domain. It is Version free of charge for Download Properitery license Properitery license all end-users all end-users available at no cost and may be freely distributed. It is available for download at www.census.gov/ipc/www/cspro DATABASE MANAGEMENT Type of data Aggregated data. Aggregated data. Individual data. Individual data. Individual and aggregated data. Individual and aggregated data. Data processing Easily handles data disaggregated by Easily handles data disaggregated by CSPro lets you create, modify, and run Using Process module allows processing It allows entering primary data, define It lets you interact with your data using geographical area and subgroups. geographical area and subgroups. data entry, batch editing, and tabulation data with programs written in Redatam variables and perform statistical data integrated tools for data entry, applications command language or limited Assisstants processing computation, editing, and retrieval. Data consistency checks Yes, Database administration application Yes, Database administration -

HTML5 Microdata and Schema.Org
HTML5 Microdata and Schema.org journal.code4lib.org/articles/6400 On June 2, 2011, Bing, Google, and Yahoo! announced the joint effort Schema.org. When the big search engines talk, Web site authors listen. This article is an introduction to Microdata and Schema.org. The first section describes what HTML5, Microdata and Schema.org are, and the problems they have been designed to solve. With this foundation in place section 2 provides a practical tutorial of how to use Microdata and Schema.org using a real life example from the cultural heritage sector. Along the way some tools for implementers will also be introduced. Issues with applying these technologies to cultural heritage materials will crop up along with opportunities to improve the situation. By Jason Ronallo Foundation HTML5 The HTML5 standard or (depending on who you ask) the HTML Living Standard has brought a lot of changes to Web authoring. Amongst all the buzz about HTML5 is a new semantic markup syntax called Microdata. HTML elements have semantics. For example, an ol element is an ordered list, and by default gets rendered with numbers for the list items. HTML5 provides new semantic elements like header , nav , article , aside , section and footer that allow more expressiveness for page authors. A bunch of div elements with various class names is no longer the only way to markup this content. These new HTML5 elements enable new tools and better services for the Web ecosystem. Browser plugins can more easily pull out the text of the article for a cleaner reading experience. Search engines can give more weight to the article content rather than the advertising in the sidebar. -

Effective and Efficient Online Communication the Channel Model
Effective and Efficient Online Communication The Channel Model Anna Fensel, Dieter Fensel, Birgit Leiter and Andreas Thalhammer Semantic Technology Institute (STI) Innsbruck, University of Innsbruck, Technikerstraße 21a, A-6020 Innsbruck, Austria Keywords: Social Media, Web 2.0, Semantic Web, Dissemination, Communication, Knowledge Management. Abstract: We discuss the challenge of scalable dissemination approach in a world where the number of communication channels and interaction possibilities is growing exponentially, particularly on the Web, Web 2.0, and semantic channels. Our goal is to enable smaller organizations to fully exploit this potential. We have developed a new methodology based on distinguishing and explicitly interweaving content and communication as a central means for achieving content reusability and thereby scalability over various, heterogeneous channels. Here, we present in detail the communication channel model of our approach. 1 INTRODUCTION the town's website, and obviously a Facebook site is a must (with a booking engine included). Bookings Fax, phone, and later the Internet, have radically through mobile platforms are significantly changed our communication possibilities. More and increasing and the hotelier would want to be found more communication has been freed from the there too. Why not add a video about the hotel on geographical barriers that formerly limited their YouTube, a chat channel for instant communication, speed and expansion. Now, it is (in principle) fast email and fax response capabilities, the old- possible to instantly communicate with a large fashioned telephone, and occasional tweets and portion of the entire human population. emails that are clearly distinguishable from spam? Nevertheless, new means also generate new Preferably, the communication should be multi- challenges. -

Rdfa Versus Microformats: Exploring the Potential for Semantic Interoperability of Mash-Up Personal Learning Environments
RDFa versus Microformats: Exploring the Potential for Semantic Interoperability of Mash-up Personal Learning Environments Vladimir Tomberg, Mart Laanpere Tallinn University, Narva mnt. 25, 10120 Tallinn, Estonia [email protected], [email protected] Abstract. This paper addresses the possibilities for increasing semantic interoperability of mash-up learning environments through the use of automatically processed metadata associated with both learning resources and learning process. We analyze and compare potential of two competing technologies for this purpose: microformats and RDFa. 1 Introduction Mash-up Personal Learning Environments have become a fast developing trend in the world of technology-enhanced learning, partly because of their flexibility and lightweight integration features. Although it is quite easy to aggregate the RSS feeds from the blogs of learners, it is more difficult to get an overview of course and its learning activities. A course is not just a syllabus, it also involves various dynamic processes that can be described in many aspects. The course always has certain learning goals, a schedule that consists learning activities (assignments, discussions), registered participants like teachers and students, and different types of resources. It would be useful, if we would be able to extract such information also from mash-up personal learning environments (just like it can be done in traditional Learning Management Systems) and allow exchanging it between the course participants. Today for semantic tagging of Web content in general and learning content as special case various technologies are used. But there are no tools and ways exist for semantic annotation of learning process that takes place in a distributed network of mash-up personal learning environments. -

Resource Description Framework (RDF)
Semantic Web Technologies Resource Description Framework (RDF) Heiko Paulheim Semantic Web – Architecture here be dragons... Semantic Web Technologies (This lecture) Technical Foundations Berners-Lee (2009): Semantic Web and Linked Data http://www.w3.org/2009/Talks/0120-campus-party-tbl/ 09/13/19 Heiko Paulheim 2 Overview • A brief history of RDF • Encodings of RDF • Semantics and principles of RDF • Embedding RDF in HTML – RDFa, Microdata, Microformats • RDF Tools • Examples for RDF in the wild 09/13/19 Heiko Paulheim 3 History: Metadata on the Web • Goal: more effective rating and ranking of web contents, e.g., by search engines • Who has created this page? • When has it been changed the last time? • What is its topic? • Which is the content's license? • How does it relate to other pages? 09/13/19 Heiko Paulheim 4 Metadata on the Web: Dublin Core • Developed in 1995 at a workshpo in Dublin, Ohio • 15 predefined tags • A widely accepted standard (ISO 15836:2009) • May be embedded into HTML: <html> <head profile="http://dublincore.org/documents/2008/08/04/dc-html/"> <title>Semantic Web</title> <link rel="schema.DC" href="http://purl.org/dc/elements/1.1/" > <meta name="DC.publisher" content="University of Mannheim" /> <meta name="DC.subject" content="Semantic Web" /> <meta name="DC.creator" content="Heiko Paulheim" /> <meta name="DC.relation" content="http://www.w3.org/2001/sw/" /> ... </head> <body> ... </body> </html> 09/13/19 Heiko Paulheim 5 Metadata on the Web: Dublin Core • Identifier • Creator • Format • Publisher • Type • Contributor