Learn the Essential Modes and Editing Features of Emacs Get Going with This Famous Open Source Editor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
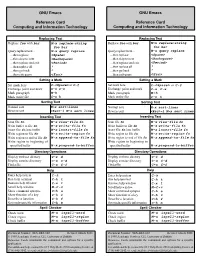
GNU Emacs GNU Emacs
GNU Emacs GNU Emacs Reference Card Reference Card Computing and Information Technology Computing and Information Technology Replacing Text Replacing Text Replace foo with bar M-x replace-string Replace foo with bar M-x replace-string foo bar foo bar Query replacement M-x query replace Query replacement M-x query replace then replace <Space> then replace <Space> then skip to next <Backspace> then skip to next <Backspace> then replace and exit <Period> then replace and exit <Period> then replace all ! then replace all ! then go back ^ then go back ^ then exit query <Esc> then exit query <Esc> Setting a Mark Setting a Mark Set mark here C-<Space> or C-@ Set mark here C-<Space> or C-@ Exchange point and mark C-x C-x Exchange point and mark C-x C-x Mark paragraph M-h Mark paragraph M-h Mark entire file C-x h Mark entire file C-x h Sorting Text Sorting Text Normal sort M-x sort-lines Normal sort M-x sort-lines Reverse sort <Esc>-1 M-x sort lines Reverse sort <Esc>-1 M-x sort lines Inserting Text Inserting Text Scan file fn M-x view-file fn Scan file fn M-x view-file fn Write buffer to file fn M-x write-file fn Write buffer to file fn M-x write-file fn Insert file fn into buffer M-x insert-file fn Insert file fn into buffer M-x insert-file fn Write region to file fn M-x write-region fn Write region to file fn M-x write-region fn Write region to end of file fn M-x append-to-file fn Write region to end of file fn M-x append-to-file fn Write region to beginning of Write region to beginning to specified buffer M-x prepend-to-buffer specified buffer -

Emacspeak — the Complete Audio Desktop User Manual
Emacspeak | The Complete Audio Desktop User Manual T. V. Raman Last Updated: 19 November 2016 Copyright c 1994{2016 T. V. Raman. All Rights Reserved. Permission is granted to make and distribute verbatim copies of this manual without charge provided the copyright notice and this permission notice are preserved on all copies. Short Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::::::: 2 2 Announcing Emacspeak Manual 2nd Edition As An Open Source Project ::::::::::::::::::::::::::::::::::::::::::::: 3 3 Background :::::::::::::::::::::::::::::::::::::::::: 4 4 Introduction ::::::::::::::::::::::::::::::::::::::::: 6 5 Installation Instructions :::::::::::::::::::::::::::::::: 7 6 Basic Usage. ::::::::::::::::::::::::::::::::::::::::: 9 7 The Emacspeak Audio Desktop. :::::::::::::::::::::::: 19 8 Voice Lock :::::::::::::::::::::::::::::::::::::::::: 22 9 Using Online Help With Emacspeak. :::::::::::::::::::: 24 10 Emacs Packages. ::::::::::::::::::::::::::::::::::::: 26 11 Running Terminal Based Applications. ::::::::::::::::::: 45 12 Emacspeak Commands And Options::::::::::::::::::::: 49 13 Emacspeak Keyboard Commands. :::::::::::::::::::::: 361 14 TTS Servers ::::::::::::::::::::::::::::::::::::::: 362 15 Acknowledgments.::::::::::::::::::::::::::::::::::: 366 16 Concept Index :::::::::::::::::::::::::::::::::::::: 367 17 Key Index ::::::::::::::::::::::::::::::::::::::::: 368 Table of Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::: -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Emacspeak User's Guide
Emacspeak User's Guide Jennifer Jobst Revision History Revision 1.3 July 24,2002 Revised by: SDS Updated the maintainer of this document to Sharon Snider, corrected links, and converted to HTML Revision 1.2 December 3, 2001 Revised by: JEJ Changed license to GFDL Revision 1.1 November 12, 2001 Revised by: JEJ Revision 1.0 DRAFT October 19, 2001 Revised by: JEJ This document helps Emacspeak users become familiar with Emacs as an audio desktop and provides tutorials on many common tasks and the Emacs applications available to perform those tasks. Emacspeak User's Guide Table of Contents 1. Legal Notice.....................................................................................................................................................1 2. Introduction.....................................................................................................................................................2 2.1. What is Emacspeak?.........................................................................................................................2 2.2. About this tutorial.............................................................................................................................2 3. Before you begin..............................................................................................................................................3 3.1. Getting started with Emacs and Emacspeak.....................................................................................3 3.2. Emacs Command Conventions.........................................................................................................3 -

Spelling Correction: from Two-Level Morphology to Open Source
Spelling Correction: from two-level morphology to open source Iñaki Alegria, Klara Ceberio, Nerea Ezeiza, Aitor Soroa, Gregorio Hernandez Ixa group. University of the Basque Country / Eleka S.L. 649 P.K. 20080 Donostia. Basque Country. [email protected] Abstract Basque is a highly inflected and agglutinative language (Alegria et al., 1996). Two-level morphology has been applied successfully to this kind of languages and there are two-level based descriptions for very different languages. After doing the morphological description for a language, it is easy to develop a spelling checker/corrector for this language. However, what happens if we want to use the speller in the "free world" (OpenOffice, Mozilla, emacs, LaTeX, ...)? Ispell and similar tools (aspell, hunspell, myspell) are the usual mechanisms for these purposes, but they do not fit the two-level model. In the absence of two-level morphology based mechanisms, an automatic conversion from two-level description to hunspell is described in this paper. previous work and reuse the morphological information. 1. Introduction Two-level morphology (Koskenniemi, 1983; Beesley & Karttunen, 2003) has been applied successfully to the 2. Free software for spelling correction morphological description of highly inflected languages. Unfortunately there are not open source tools for spelling There are two-level based descriptions for very different correction with these features: languages (English, German, Swedish, French, Spanish, • It is standardized in the most of the applications Danish, Norwegian, Finnish, Basque, Russian, Turkish, (OpenOffice, Mozilla, emacs, LaTeX, ...). Arab, Aymara, Swahili, etc.). • It is based on the two-level morphology. After doing the morphological description, it is easy to The spell family of spell checkers (ispell, aspell, myspell) develop a spelling checker/corrector for the language fits the first condition but not the second. -

Hunspell – the Free Spelling Checker
Hunspell – The free spelling checker About Hunspell Hunspell is a spell checker and morphological analyzer library and program designed for languages with rich morphology and complex word compounding or character encoding. Hunspell interfaces: Ispell-like terminal interface using Curses library, Ispell pipe interface, OpenOffice.org UNO module. Main features of Hunspell spell checker and morphological analyzer: - Unicode support (affix rules work only with the first 65535 Unicode characters) - Morphological analysis (in custom item and arrangement style) and stemming - Max. 65535 affix classes and twofold affix stripping (for agglutinative languages, like Azeri, Basque, Estonian, Finnish, Hungarian, Turkish, etc.) - Support complex compoundings (for example, Hungarian and German) - Support language specific features (for example, special casing of Azeri and Turkish dotted i, or German sharp s) - Handle conditional affixes, circumfixes, fogemorphemes, forbidden words, pseudoroots and homonyms. - Free software (LGPL, GPL, MPL tri-license) Usage The src/tools dictionary contains ten executables after compiling (or some of them are in the src/win_api): affixcompress: dictionary generation from large (millions of words) vocabularies analyze: example of spell checking, stemming and morphological analysis chmorph: example of automatic morphological generation and conversion example: example of spell checking and suggestion hunspell: main program for spell checking and others (see manual) hunzip: decompressor of hzip format hzip: compressor of -

INSECURE-Mag-9.Pdf
Another year is almost over and a plethora of information security problems are behind us. To let 2006 go out in style, we bring you a feature packed issue of (IN)SECURE. As the feature interview for this issue we had the pleasure of talking with Kurt Sauer, the CSO at Skype, one of the most well-known companies in the digital world. We’ll be back next year with many new ideas in the pipeline. Stay tuned for coverage from a few conferences including the RSA Conference in San Francisco and the Black Hat Briefings &Training in Amsterdam. If you’re attending, be sure to drop me an e-mail and we’ll grab a drink. We wish you a safe 2007! Mirko Zorz Chief Editor Visit the magazine website at www.insecuremag.com (IN)SECURE Magazine contacts Feedback and contributions: Mirko Zorz, Chief Editor - [email protected] Marketing: Berislav Kucan, Director of Marketing - [email protected] Distribution (IN)SECURE Magazine can be freely distributed in the form of the original, non modified PDF document. Distribution of modified versions of (IN)SECURE Magazine content is prohibited without the explicit permission from the editor. For reprinting information please send an email to [email protected] or send a fax to 1-866-420-2598. Copyright HNS Consulting Ltd. 2006. www.insecuremag.com New enterprise single sign-on authentication software DigitalPersona announced the latest version of its award-winning enterprise product, DigitalPersona Pro 4.0. The new and improved software delivers a complete, accurate and trusted fingerprint Enterprise Single Sign-On (ESSO) solution with more secure authentication, improved manageability and the broadest support available for the world’s leading biometrically-enabled notebooks including models from Lenovo, HP, Dell, and Toshiba. -

Finite State Recognizer and String Similarity Based Spelling
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by BRAC University Institutional Repository FINITE STATE RECOGNIZER AND STRING SIMILARITY BASED SPELLING CHECKER FOR BANGLA Submitted to A Thesis The Department of Computer Science and Engineering of BRAC University by Munshi Asadullah In Partial Fulfillment of the Requirements for the Degree of Bachelor of Science in Computer Science and Engineering Fall 2007 BRAC University, Dhaka, Bangladesh 1 DECLARATION I hereby declare that this thesis is based on the results found by me. Materials of work found by other researcher are mentioned by reference. This thesis, neither in whole nor in part, has been previously submitted for any degree. Signature of Supervisor Signature of Author 2 ACKNOWLEDGEMENTS Special thanks to my supervisor Mumit Khan without whom this work would have been very difficult. Thanks to Zahurul Islam for providing all the support that was required for this work. Also special thanks to the members of CRBLP at BRAC University, who has managed to take out some time from their busy schedule to support, help and give feedback on the implementation of this work. 3 Abstract A crucial figure of merit for a spelling checker is not just whether it can detect misspelled words, but also in how it ranks the suggestions for the word. Spelling checker algorithms using edit distance methods tend to produce a large number of possibilities for misspelled words. We propose an alternative approach to checking the spelling of Bangla text that uses a finite state automaton (FSA) to probabilistically create the suggestion list for a misspelled word. -

Does Hardware Configuration and Processor Load Impact Software Fault Observability?
Does Hardware Configuration and Processor Load Impact Software Fault Observability? Raza Abbas Syed1, Brian Robinson2, Laurie Williams1 1Department of Computer Science, North Carolina State University, Raleigh, NC 27695-8206 {rsyed, lawilli3}@ncsu.edu 2ABB Inc., US Corporate Research, Raleigh, NC 27606 [email protected] Abstract. Intermittent failures and nondeterministic behavior test teams during the product development cycle. For failures complicate and compromise the effectiveness of software detected in test, it is difficult to determine the underlying testing and debugging. To increase the observability of fault when reproducing the failure is not possible. When the software faults, we explore the effect hardware configurations underlying fault cannot be determined, the failure report is and processor load have on intermittent failures and the often closed and no additional effort is spent on it until nondeterministic behavior of software systems. We conducted additional occurrences are detected. For faults detected in the a case study on Mozilla Firefox with a selected set of reported field, developers spent considerable effort in either remotely field failures. We replicated the conditions that caused the debugging the fault or traveling to the customer site itself to reported failures ten times on each of nine hardware determine the fault and fix it. configurations by varying processor speed, memory, hard Nondeterministic behavior in software systems can be drive capacity, and processor load. Using several observability tools, we found that hardware configurations that had less attributed to a number of sources. Testers may not have processor speed and memory observed more failures than enough visibility or control over all of the inputs to the others. -

Deployment Guide for Cisco Directory Connector
Deployment Guide for Cisco Directory Connector First Published: 2017-02-24 Last Modified: 2020-02-05 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: https://www.cisco.com/c/en/us/about/legal/trademarks.html. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1721R) © 2020 Cisco Systems, Inc. All rights reserved. New and Changed Information Date Changes Made July 14, 2020 • Updated information on what to do when trying to claim users in Conflicting User Email Accounts, on page 71. June 18, 2020 • Updated a step in Choose Active Directory Objects to Synchronize to include how to customize attributes for room data (release 3.6). • Updated Directory Connector download link in Install Cisco Directory Connector, on page 17 June 2, 2020 • Added userAccountControl and ds-pwp-account-disabled attributes to the table in Active Directory and Cloud Attributes, on page 28. April 21, 2020 • Added a note in Do a Full Synchronization of Active Directory Users Into the Cloud to clarify that the auto-assign license template only applies to new users, not updated users. February 5, 2020 In the "Do a Full Synchronization of Active Directory Users Into the Cloud" topic, clarified some inaccurate text about deletion. -

The Kate Handbook
The Kate Handbook Anders Lund Seth Rothberg Dominik Haumann T.C. Hollingsworth The Kate Handbook 2 Contents 1 Introduction 10 2 The Fundamentals 11 2.1 Starting Kate . 11 2.1.1 From the Menu . 11 2.1.2 From the Command Line . 11 2.1.2.1 Command Line Options . 12 2.1.3 Drag and Drop . 13 2.2 Working with Kate . 13 2.2.1 Quick Start . 13 2.2.2 Shortcuts . 13 2.3 Working With the KateMDI . 14 2.3.1 Overview . 14 2.3.1.1 The Main Window . 14 2.3.2 The Editor area . 14 2.4 Using Sessions . 15 2.5 Getting Help . 15 2.5.1 With Kate . 15 2.5.2 With Your Text Files . 16 2.5.3 Articles on Kate . 16 3 Working with the Kate Editor 17 4 Working with Plugins 18 4.1 Kate Application Plugins . 18 4.2 External Tools . 19 4.2.1 Configuring External Tools . 19 4.2.2 Variable Expansion . 20 4.2.3 List of Default Tools . 22 4.3 Backtrace Browser Plugin . 25 4.3.1 Using the Backtrace Browser Plugin . 25 4.3.2 Configuration . 26 4.4 Build Plugin . 26 The Kate Handbook 4.4.1 Introduction . 26 4.4.2 Using the Build Plugin . 26 4.4.2.1 Target Settings tab . 27 4.4.2.2 Output tab . 28 4.4.3 Menu Structure . 28 4.4.4 Thanks and Acknowledgments . 28 4.5 Close Except/Like Plugin . 28 4.5.1 Introduction . 28 4.5.2 Using the Close Except/Like Plugin . -

SDL Tridion Docs Release Notes
SDL Tridion Docs Release Notes SDL Tridion Docs 14 July 2019 ii SDL Tridion Docs Release Notes 1 Welcome to Tridion Docs Release Notes 1 Welcome to Tridion Docs Release Notes This document contains the complete Release Notes for SDL Tridion Docs 14. Customer support To contact Technical Support, connect to the Customer Support Web Portal at https://gateway.sdl.com and log a case for your SDL product. You need an account to log a case. If you do not have an account, contact your company's SDL Support Account Administrator. Acknowledgments SDL products include open source or similar third-party software. 7zip Is a file archiver with a high compression ratio. 7-zip is delivered under the GNU LGPL License. 7zip SFX Modified Module The SFX Modified Module is a plugin for creating self-extracting archives. It is compatible with three compression methods (LZMA, Deflate, PPMd) and provides an extended list of options. Reference website http://7zsfx.info/. Akka Akka is a toolkit and runtime for building highly concurrent, distributed, and fault tolerant event- driven applications on the JVM. Amazon Ion Java Amazon Ion Java is a Java streaming parser/serializer for Ion. It is the reference implementation of the Ion data notation for the Java Platform Standard Edition 8 and above. Amazon SQS Java Messaging Library This Amazon SQS Java Messaging Library holds the Java Message Service compatible classes, that are used for communicating with Amazon Simple Queue Service. ANTLR ANTLR is a powerful parser generator that you can use to read, process, execute, or translate structured text or binary files.