Mobile Internet for Dummies. We Have a Completely Wnew World for You to Explore and Discover, All Available from the Palm of Your Hand
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SMS) Transit Via SMS Gateways
Carriers providing Short Message Service (SMS) transit via SMS gateways. This list explains which email address to use if one wants to send an email and have it arrive as a text message on someone's phone. The number must contain no punctuation. For instance, to send to a number typically expressed in the United States as 987-555-0100, one would email 9875550100@SMS- gateway. Some carriers have multiple gateways. The SMS gateway refers to Short Message Services which are capable of transmitting plain text messages only. MMS refers to "Multimedia Messaging Services" which are generally capable of carrying messages which include text, pictures and audio [email protected] (SMS), [email protected] (MMS) (Note: AT&T Mobility United States This gateway fails to handle complete phone numbers; the country code must be omitted, leaving only the ten-digit NANP number.) [email protected] AT&T Mobility (formerly [email protected] United States Cingular) [email protected] [email protected] AT&T Enterprise Paging United States [email protected] AT&T Global Smart Messaging United States [email protected] Suite - Powered By Soprano BellSouth United States [email protected] [email protected] (SMS) Bluegrass Cellular United States [email protected] (MMS) Global Telematic Solutions, LLC • PO Box 269 • Meridian, ID 83680 • Tel 855-487-9679 • Fax 855-487-9680 www.gtsfleet.com [email protected] (SMS) Boost Mobile United States [email protected] (MMS) Cellcom United States -

Table of Contents 500 GREAT PROGRAM IDEAS
Table of Contents 500 GREAT PROGRAM IDEAS Compiled by Recreation and Leisure Studies Students Gordon College Presented at Massachusetts Recreation and Park Association State Conference October 23, 2007 Workshop Presenters: Dr. Peggy Hothem Professor of Recreation and Leisure Studies Students: Christine Arruda, Christine Scanlon and Kendra Spotts Adult: Let's Talk An open forum for parents to exchange ideas, learn how to cope with ups and downs of parenthood, and acquire useful information from local guest speakers. Childcare and refreshments provided for participants. Where are Your Teenagers ----- on the Internet? Facebook, MySpace, IM, Textmessaging, and what is coming next? Learn to communicate in their language. (Best Buy and other technology retail stores can be a resource for providing an instructor – usually free of charge) Understanding Japanese Culture A course designed as an introduction to Japanese cuisine. Participants will learn Japanese cooking techniques, ingredients, quality brands, shopping tips, and how to locate Japanese grocers. Also you will prepare entrees. Fit Fitness in your Schedule Various fitness classes to choose from; Coed Body Sculpting, Exercise for the Early Bird, and Ultimate Step and Tone are only a few offered. Shorter sessions allow for greater flexibility for those with tight schedules Digital Camera Club Learn the newest techniques. Meetings consist of presentations by professional photographers, field trips, photo contests and photo demonstrations. A Mile In My Shoes A walking club offering the guidance and direction to start walking into shape! Tally sheets to keep track of walking distance, instructional handouts and fitness instructors will be provided. Each participant will record his/her mileage and receive prizes upon reaching goals. -

Local Password Exploitation Class
Adrian Crenshaw http://Irongeek.com I run Irongeek.com I have an interest in InfoSec education I don’t know everything - I’m just a geek with time on my hands Regular on: http://www.isd-podcast.com/ http://Irongeek.com Pulling stored passwords from web browsers/IM clients and other apps Hash cracking of Windows passwords, as well as other systems Sniffing plain text passwords off the network How passwords on one box can be used to worm though other hosts on a network Hope it get’s you thinking. Exploits are temporary, bad design decisions are forever. http://Irongeek.com There are several reasons why an attacker may want to find local passwords: To escalate privileges on the local host (install games, sniffers, key stroke catchers and other software or just to bypass restrictions). Local passwords can be used to gain access to other systems on the network. Admins may reuse the same usernames and passwords on other network hosts (more than likely if they use hard drive imaging). Similar themes are also often used for password selection. Just for the fun of doing it. http://Irongeek.com Does not organize well, but you need to have these factoids in the back of your head for later. http://Irongeek.com Imaged Systems Uses it on other systems Repeat ad nauseum Attacker grabs local password on one box Grabs passwords from other systems, and installs keyloggers/sniffers to get network credentials for http://Irongeek.com more systems Target Audience: Workstation Installers, System Admins, Security Folk and General Gear-heads. -

Annual Statistical Report
ANNUAL STATISTICAL REPORT Statistical Data on Public Utilities in West Virginia Source: Annual Reports Submitted To The Public Service Commission Of West Virginia ______________________________ Condition at the Close of Year Ended December 31, 2019 or as Otherwise Noted Compiled by: Kathryn Stalnaker, Executive Secretary Division Annual Reports Section – 11/16/2020 WEST VIRGINIA PUBLIC SERVICE COMMISSION 2019 ANNUAL REPORT STATISTICS FISCAL YEAR 07/01/18 - 06/30/19 CALENDAR YEAR 01/01/19 - 12/31/19 TABLE OF CONTENTS Page Number List of Utilities ............................................................................................ 5 – 26 Utilities Summary ............................................................................................ 27 - - - - - - - - - - - - - - - - - - -- - - - Type of Utilities - - - - - - - - - - - - - - - - - - - - - - - - Telephone Companies ....................................................................... 28 - 30 Electric Companies ............................................................................ 31 - 37 Gas Companies .................................................................................. 38- 40 Water Utilities: Privately Owned ................................................................................... 41 Publicly Owned - Municipals .............................................................. 42 - 46 Publicly Owned - Districts ............................................................ 47 - 50 Associations and Authorities ............................................................ -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise April 5, 2008 Palo Alto Networks 2130 Gold Street, Suite 200 Alviso, CA 95002-2130 Main 408.786.0001 Fax 408.786.0006 Sales 866.207.0077 www.paloaltonetworks.com Table of Contents Executive Summary............................................................................................................................. 3 Introduction.......................................................................................................................................... 4 Palo Alto Networks Application Visibility and Risk Report............................................................... 5 Findings ............................................................................................................................................... 5 Major Trends.................................................................................................................................... 5 Consumerization of Enterprise Networks and Applications............................................................. 6 Instant messaging: evasive features bring business and security risks. ..................................... 6 Web mail: rampant use brings delicate balancing act of personal email on company time. ....... 7 Peer-to-peer applications: prevalent on enterprise networks, despite control efforts.................. 8 Web-based file transfer and storage: harmless utility or data sinkhole? ..................................... 8 Media applications: -

TSU Journal of Communication and Media Studies, Vol. 3, No. 1, March 2020
TSU Journal of Communication and Media Studies, Vol. 3, No. 1, March 2020 Impact of Social Media on the Socio-Economic Development of Nigeria 1Bolu John Folayan & 2Maria Kisugu Obun-Andy Abstract Advancements in technology and the internet have greatly influenced the way things are done virtually in all fields of human endeavor. These advancements, no doubt, have influenced the socio-economic developments of nations including Nigeria. The impact of social media on human capacity development has gone beyond the exchange of information; the social media have become powerful communicative forces in the economic, political, religious and educational realms of the society. This study examines the role of social media in the socio- economic development of Nigeria. It explores the potentials of the various social media platforms to the socioeconomic development of Nigeria. Scholarly perspectives and positions in the literature are explored to demonstrate the relevance of social media and their applications in the course of making life better for the masses, particularly the indigent and information have-nots. The study spotlights key areas where successful application of social media can engender the much needed sustainable development of society, using the Nigerian situation as a point of reference. The study further identifies social media platforms that can facilitate this much desired socio-economic development, emphasizing that the goal of developing human and technological potentialities of Nigeria cannot be achieved effectively unless the society adopts IT-driven developmental strategies, especially in an information era like ours. Social media presents viable IT avenues that could be harnessed to spearhead this course. Key words: Social media, Socio-Economic Development, Information Technology and Nigeria. -

Annual Statistical Report
ANNUAL STATISTICAL REPORT Statistical Data on Public Utilities in West Virginia Source: Annual Reports Submitted To The Public Service Commission Of West Virginia ______________________________ Condition at the Close of Year Ended December 31, 2013 or as Otherwise Noted Compiled by: Kathryn Stalnaker, Executive Secretary Division, Annual Reports Section – 12/02/2014 WEST VIRGINIA PUBLIC SERVICE COMMISSION 2013 ANNUAL REPORT STATISTICS FISCAL YEAR 07/01/12 - 06/30/13 CALENDAR YEAR 01/01/13 - 12/31/13 TABLE OF CONTENTS Page Number List of Utilities ............................................................................................ 5 – 26 Annual Report Summary ................................................................................. 27 - - - - - - - - - - - - - - - - - - -- - - - Type of Utilities - - - - - - - - - - - - - - - - - - - - - - - - Telephone Companies ....................................................................... 28 - 30 Electric Companies ............................................................................ 31 - 37 Gas Companies ................................................................................. 38 - 40 Water Utilities: Privately Owned ................................................................................... 41 Publicly Owned - Municipals ......................................................... 42 - 46 Publicly Owned - Districts ............................................................ 47 - 51 Associations and Authorities ............................................................ -
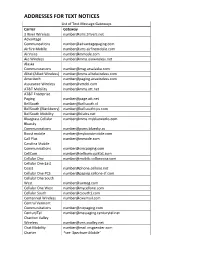
Addresses for Text Notices
ADDRESSES FOR TEXT NOTICES List of Text Message Gateways Carrier Gateway 3 River Wireless [email protected] Advantage Communcations [email protected] AirFire Mobile [email protected] AirVoice [email protected] Aio Wireless [email protected] Alaska Communications [email protected] Alltel (Allied Wireless) [email protected] Ameritech [email protected] Assurance Wireless [email protected] AT&T Mobility [email protected] AT&T Enterprise Paging [email protected] BellSouth [email protected] BellSouth (Blackberry) [email protected] BellSouth Mobility [email protected] Bluegrass Cellular [email protected] Bluesky Communications [email protected] Boost mobile [email protected] Call Plus [email protected] Carolina Mobile Communications [email protected] CellCom [email protected] Cellular One [email protected] Cellular One East Coast [email protected] Cellular One PCS [email protected] Cellular One South West [email protected] Cellular One West [email protected] Cellular South [email protected] Centennial Wireless [email protected] Central Vermont Communications [email protected] CenturyTel [email protected] Chariton Valley Wireless [email protected] Chat Mobility [email protected] Charter *see ‘Spectrum Mobile’ ADDRESSES FOR TEXT NOTICES Cincinnati Bell [email protected] Cingular Wireless [email protected] Cingular (GSM) [email protected] Cingular (TDMA) [email protected] -

For Passive Devices, LLC, and the Father of the Individual Named Herein As Kristyn Kelly Allen, the Applicant (“Applicant”) in Theherein Opposition
IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD In the matter ofApplication Serial No. 78-803,956; International Class: 009 Mark: SNOOPTUNES—Published in the Official Gazette on December 19, 2006 CALVIN BROADUS Opposer vs. Re: Opposition No. 91176834 KRISTYN KELLY ALLEN, dba PASSIVE DEVICES LLC Applicant _j.j____ DECLARATION§S[ IN SUPPORT OF INTERNET EVIDENCE DECLARATION OF ALLEN HEATH I, Allen Heath, declare as follows: 1. I am VP ofBusiness Development and acting chiefoperations of1’icer(“COO”) for Passive Devices, LLC, and the father of the individual named herein as Kristyn Kelly Allen, the applicant (“Applicant”) in theherein Opposition.. I have acted in the capacities of VP of Business Development and acting CO0 for Passive Devices, LLC since the company’s inception in or about 2004. Unless otherwise stated, this declaration is based on my personal knowledge, and if called as a witness could testify competently thereto. 2. Between September 9, 2008 and September 21, 2008, I performed certain searches on the Internet in order to locate and collect evidence relevant to this proceeding. The results of those searches are set forth below. DECLARATION(S) IN SUPPORT OF EVIDENCE 3. On September 17, 2008, I performed intemet searches on the search engine website Google.com, for each of the search queries set forth below. The number of search results for each such internet search is also set out below. Attached hereto as Exhibit “A”, and hereby incorporated herein by this reference, are true and correct printouts of the first page of search results for each said internet search: Search Quegg No. -

Hosting Online Open Houses & Online/Virtual Office Hours
Hosting online open houses & online/virtual office hours A virtual open house can be an information session, webinar, or other interactive program that provides prospective students with the opportunity to ask questions either via video, chat, or audio while a staff member responds to questions and provides program information in real time. These should be planned on adult student- friendly schedules with a variety of available dates and times. The event could be offered on a Tuesday evening, Thursday at noon, and/or a Saturday morning, giving prospective students the ability to “attend” the event either after regular office hours, during a lunch break, or on a weekend from their office, home, or a local library. An online open house event should provide: general information about the program; program requirements; the portfolio process; and financial aid. By making information available to the students on their schedule from a space they consider safe and non- threatening, they will be more open to participation. Prospective students can access the event from anywhere with a computer and an internet connection. Adult learners often juggle many responsibilities between work, home, and their community. Here are some helpful resources to help you reach prospective adult students without breaking the bank or overextending your staff. The services listed below will enable you to host events or hold office hours outside of the traditional work schedule and from anywhere with an internet connection. You aren’t required to use these specific services; these are merely suggestions to assist you in providing online support to your students as a part of the RBA Today program commitment requirements. -

Telecommunications Provider Locator
Telecommunications Provider Locator Industry Analysis & Technology Division Wireline Competition Bureau January 2010 This report is available for reference in the FCC’s Information Center at 445 12th Street, S.W., Courtyard Level. Copies may be purchased by contacting Best Copy and Printing, Inc., Portals II, 445 12th Street S.W., Room CY-B402, Washington, D.C. 20554, telephone 800-378-3160, facsimile 202-488-5563, or via e-mail at [email protected]. This report can be downloaded and interactively searched on the Wireline Competition Bureau Statistical Reports Internet site located at www.fcc.gov/wcb/iatd/locator.html. Telecommunications Provider Locator This report lists the contact information, primary telecommunications business and service(s) offered by 6,493 telecommunications providers. The last report was released March 13, 2009.1 The information in this report is drawn from providers’ Telecommunications Reporting Worksheets (FCC Form 499-A). It can be used by customers to identify and locate telecommunications providers, by telecommunications providers to identify and locate others in the industry, and by equipment vendors to identify potential customers. Virtually all providers of telecommunications must file FCC Form 499-A each year.2 These forms are not filed with the FCC but rather with the Universal Service Administrative Company (USAC), which serves as the data collection agent. The pool of filers contained in this edition consists of companies that operated and collected revenue during 2007, as well as new companies that file the form to fulfill the Commission’s registration requirement.3 Information from filings received by USAC after October 13, 2008, and from filings that were incomplete has been excluded from this report. -

Savvian Wireless Newsletter Q108 Final
WIRELESS DATA SERVICES SECTOR REPORT GCA SAVVIAN, LLC 150 CALIFORNIA STREET, SAN FRANCISCO, CA 94111 | www.gcasavvian.com |415.318.3600 MARKETMARKET HIGHLIGHTSHIGHLIGHTS Inside this issue The 1 st quarter of 2008 saw a number of important events in the mobile data sector, including results of the 700 MHz spectrum auction, company announcements around the CES, Mobile World Congress and CTIA tradeshows, Market Highlights Microsoft’s acquisition of Danger rumored at $500MM and $100MM private capital raises from Modu and SpinVox. Summary Performance In general, GCA Savvian’s wireless indices reflected the broader markets’ struggles in Q1: our wireless carrier index was off 31% while our mobile content and integrated wireless / wireline indices were in line with the Nasdaq, Observations down 13% and 10%, respectively; our infrastructure universe (up 3%) was the only index in positive territory. Trading Data The domino effect following Verizon’s announcement of a $99 per month unlimited calling plan contributed to stock Transaction Activity price declines for service providers as investors fear carriers have started down a slippery slope with respect to their longer-term pricing strategy and risk becoming simply raw bandwidth providers. GCA Savvian Update In Q1, we tracked 21 M&A transactions within our wireless universe representing $335MM in disclosed value and 59 private companies that raised $480MM in venture capital. SUMMARY PERFORMANCE AV / Revenue AV / EBITDA Price / EPS CY 08E CY 09E CY 08E CY 09E CY 08E CY 09E San Francisco Office