Download Souvenir
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Slno NEET ROLL CANDNM 1 2812003032 MARIYA JAMES M 2
/ 230 KARNATAKA EXAMINATIONS AUTHORITY 1 Sampige Road,18th Cross,Malleshwaram, Bangalore - 560012 PROVISIONAL LIST OF CANDIDATES REGISTERED FOR UGNEET-2020 -(NON-Karnataka candidates) Note 1.If any candidates has registered for UGNEET-2020 and if not listed in the following list should report to KEA with registration details. 2.Mere registration for UGNEET-2020 does not confirm any right for admission to medical or dental seats , it is subject to fulfilling eligibility conditions. 3. If any discrepancy found should report to KEA immediately. 4. Candidates should not presume that it is a merit list for UGNEET-2020 admissions. -

An Imaginative Film and Monumental by Its Production Values and Cinematic Brilliance in Creating a Fantasy World on Screen
63rd NATIONAL FILM AWARDS FOR 2015 FEATURE FILMS S.No. Name of Award Name of Film Awardees Medal Citation & Cash Prize 1. BEST FEATURE BAAHUBALI Producer: SHOBU Swarna Kamal An imaginative film and FILM YARLAGADDA AND and monumental by its production ARKA values and cinematic brilliance MEDIAWORKS (P) 2,50,000/- LTD. each to in creating a fantasy world on screen. the Producer and Director : S.S Director RAJAMOULI (CASH COMPONENT TO BE SHARED) 2. INDIRA GANDHI MASAAN Producer: Swarna Kamal For his perceptive approach AWARD FOR BEST PHANTOM FILMS and to filmmaking in handling a DEBUT FILM OF A layered story of DIRECTOR Director : NEERAJ 1,25, 000/- people caught up changing GHAYWAN each to social and moral values. the Producer and Director 3. BEST POPULAR BAJRANGI Producer: SALMA Swarna Kamal Tackling an important social FILM PROVIDING BHAIJAAN KHAN, and issue in the simple heart- WHOLESOME SALMAN KHAN, warming & entertaining format. ENTERTAINMENT ROCKLINE 2,00,000/- VENKTESH each to Director : KABIR the Producer and KHAN Director 4. NARGIS DUTT NANAK SHAH Producer: Rajat Kamal and The saga on the life of the FAKIR GURBANI MEDIA AWARD FOR great spiritual master BEST FEATURE PVT. LTD. 1,50,000/- each to advocating the values of peace FILM ON and harmony. NATIONAL the Producer and INTEGRATION Director 5. BEST FILM ON NIRNAYAKAM Producer: JAIRAJ Rajat Kamal and For tackling a relevant and SOCIAL ISSUES FILMS unaddressed issue of 1,50,000/- each curtailing freedom of Director : V.K to movement for the common PRAKASH the Producer and man due to hartals and Director processions. -

Name of the Centre : DAV Bachra No
Name of the Centre : DAV Bachra No. Of Students : 474 SL. No. Roll No. Name of the Student Father's Name Mother's Name 1 19002 AJAY ORAON NIRMAL ORAON PATI DEVI 2 19003 PUJA KUMARI BINOD PARSAD SAHU SUNITA DEVI 3 19004 JYOTSANA KUMARI BINOD KUMAR NAMITA DEVI 4 19005 GAZAL SRIVASTVA BABY SANTOSH KUMAR SRIVASTAVA ASHA SRIVASTVA 5 19006 ANURADHA KUMARI PAPPU KUMAR SAH SANGEETA DEVI 6 19007 SUPRIYA KUMARI DINESH PARSAD GEETA DEVI 7 19008 SUPRIYA KUMARI RANJIT SHINGH KIRAN DEVI 8 19009 JYOTI KUMARI SHANKAR DUBEY RIMA DEVI 9 19010 NIDHI KUMARI PREM KUMAR SAW BABY DEVI 10 19011 SIMA KUMARI PARMOD KUMAR GUPTA SANGEETA DEVI 11 19012 SHREYA SRIVASTAV PRADEEP SHRIVASTAV ANIMA DEVI 12 19013 PIYUSH KUMAR DHANANJAY MEHTA SANGEETA DEVI 13 19014 ANUJ KUMAR UPENDRA VISHWAKARMA SHIMLA DEVI 14 19015 MILAN KUMAR SATYENDRA PRASAD YADAV SHEELA DEVI 15 19016 ABHISHEK KUMAR GUPTA SANT KUMAR GUPTA RINA DEVI 16 19017 PANKAJ KUMAR MUKESH KUMAR SUNITA DEVI 17 19018 AMAN KUMAR LATE. HARISHAKAR SHARMA RINKI KUMARI 18 19019 ATUL RAJ RAJESH KUMAR SATYA RUPA DEVI 19 19020 HARSH KUMAR SHAILENDRA KR. TIWARY SNEHLATA DEVI 20 19021 MUNNA THAKUR HIRA THAKUR BAIJANTI DEVI 21 19022 MD.FARID ANSARI JARAD HUSSAIN ANSARI HUSNE ARA 22 19023 MD. JILANI ANSARI MD.TAUFIQUE ANSARI FARZANA BIBI 23 19024 RISHIKESH KUNAL DAMODAR CHODHARY KAMLA DEVI 24 19025 VISHAL KR. DUBEY RAJEEV KUMAR DUBEY KIRAN DEVI 25 19026 AYUSH RANJAN ANUJ KUMAR DWIVEDI ANJU DWIVEDI 26 19027 AMARTYA PANDEY SATISH KUMAR PANDEY REENA DEVI 27 19028 SHIWANI CHOUHAN JAYPAL SINGH MAMTA DEVI 28 19029 SANDEEP KUMAR MEHTA -
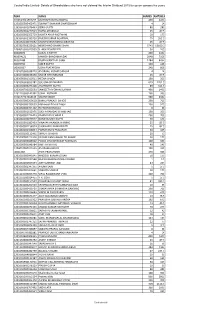
Unclaimed Intdiv13 Website.Pdf
FLNO NAM1 SHARES AMT2013 IN30023911567299 MUTHAPPAN RAJAGOPAL 400 1400 1201060000462471 SUMANT SHANKAR DHARESHWAR 4 14 1201060001076463 RENU GUPTA 80 280 1201060002277519 ISMAIL ZHABIULLA 25 87.5 1201060002352750 MUKTA ANUP MOTWANI 50 175 1201060002395710 RAJESH KUMAR AGARWAL 75 262.5 1201060100195562 MOHAN KESHAWRAO DEOTALE 25 87.5 1203320003229121 NEMCHAND SHAMJI SHAH 3743 13100.5 1204010000013555 V. AKHILESH REDDY . 30 105 K0006892 KUNAL K MEHTA 400 1400 M0004121 MANISH BHAGAWANDAS 2048 7168 R0002488 RAJANI KANTILAL SHAH 1284 4494 S0003784 SUBIR GUPTA 128 448 U0000367 UDAY PRATAPSINH 248 868 1201070000038720 ANURAAG KUMAR SANGHI 4 14 1201070000198190 SAGAR HARI NEMADE 25 87.5 1201090001310515 NEENA SIMON 100 350 1201090003653181 SUGUNA SRIDHARAN 629 2201.5 1201090005243206 AMARNATH GUTTA 89 311.5 1201090700022603 SANGEETA MOHAN SURANA 400 1400 1201120000141961 USHA . KOTHARI 100 350 IN30177414018133 SAMAR SINGH 960 3360 1201060000260618 BIMAL PRAKASH SAHOO 200 700 1201060000293059 Mahaveer Prasad Nagar 150 525 1201060000704202 RAYMOND DSOUZA 8 28 1201060001622976 SUDHA RAMDAS SHANBHAG 100 350 1201060001714423 RAJANI DEVI CHAWLA 200 700 1201060100079577 NAND KUMAR GUPTA 40 140 1201060001082403 VINAYAK ANANDA AHIRRAO 25 87.5 1201060002158974 GAJANAN D RAMANKATTI 25 87.5 1201060002306834 PARSOTAM N PRAJAPATI 30 105 1201060100122461 SMRUTI SHASTRI 20 70 1201090000222328 DEEPAK PANDURANG TELAVANE 50 175 1201090000686502 POOJA CHANDRAKANT MAHAJAN 100 350 1201090003048784 KANTTA MITTAL 40 140 1204010000011655 ANUPAMA REDDY . 100 350 J0001060 -

Annual Report
U&I IMPACT 2018-19 REPORT PARTNERS IN CHANGE OUR STORY STARTS ON A SUNDAY It all began when a couple of friends decided to It was this eagerness to learn, brought about by spend their Sundays doing something off the the simple exchange between mentor and child, beaten track. Instead of a self-indulgent week- that sparked the idea of what is now called, U&I. end, they chose to start helping out at a Govern- This report is a testament to the enduring power ment-run Home for special-needs children. Sun- of kindness and connection. days soon became about engaging with the children at the Home and helping clean the compound. What started out as just a few, turned into a following. With more than 50 volunteers helping every week, the Home was revamped and brought to life. What began as a weekend plan, turned into We are U&I, a volunteer an everyday undertaking. powered NGO built on the foundation that The same two friends began discussing what change happens when more they could do to help underprivileged kids in their neighbourhood. What would be of we work together. value? Computers seemed to be the answer. One of the friends ran his own HR firm - his office space could be used to start computer classes. The evenings would see small groups of kids from nearby slums, crowded around large systems, learning and absorbing all that they could. 1 MISSION Bring education and healthcare to disadvantaged communities across India VISION Building Communities of Change PROGRAMS U&I TEACH U&I CARE 2 1934 1670 49 CHILDREN VOLUNTEERS LEARNING CENTERS 4 HOMES 20 CITIES STRONG 3 THE QUESTION THAT REQUIRES ACTION, NOT AN ANSWER When we first volunteered at the State-run Boys’ But today, let’s focus on the question, Home for special-needs children back in 2011, our “Why not?” intention was very simple: the kids needed help and we had the ability to pitch in. -

NAME E Mail Id All India Rank
NAME E Mail Id All India rank Riya 75****[email protected] 1 PRATIK MITRA pr****[email protected] 2 R SANDEEP REDDY 19****[email protected] 3 Arushima Sahay ar****[email protected] 4 SUBHAM GHOSH gh****[email protected] 5 Kajal Choudhary it****[email protected] 6 anoop pi****[email protected] 7 sahana choudhury ch****[email protected] 8 gautam prakash ga****[email protected] 9 Priya pr****[email protected] 10 RAMEEZ ALI KHAN re****[email protected] 11 ROHIT KASHYAP ro****[email protected] 12 Aakanksha Singh si****[email protected] 13 Swapnil Rankawat SA****[email protected] 14 Anand Singh Patel an****[email protected] 15 VISHAL GUPTA av****[email protected] 16 Apratim Mondal m.****[email protected] 17 Suchismita Samanta su****[email protected] 18 Subhankar Bose su****[email protected] 19 Shaik cs****[email protected] 20 Ankit ni****[email protected] 21 ANKIT SHUKLA sh****[email protected] 22 SURYA KANTA DEY de****[email protected] 23 Vibhor vi****[email protected] 24 mani ag****[email protected] 25 GUNTUPALLI SURYA TEJA su****[email protected] 26 vikash yadav vi****[email protected] 27 prafull mittal pr****[email protected] 28 Vimal vi****[email protected] 29 Syed Saqib Hussain ss****[email protected] 30 Rizwan ri****[email protected] 31 Danish wani Da****[email protected] 32 barjees ba****[email protected] 33 Bhuwan Mishra Bh****[email protected] 34 Shriram Meena sh****[email protected] 35 Venkatesh y k Ve****[email protected] 36 sunny ahmed su****[email protected] 37 krishna kc****[email protected] 38 narendra patiyal pa****[email protected] 39 Akhilesh shukla ak****[email protected] 40 neetika jindal ne****[email protected] 41 ANKIT BANSAL ba****[email protected] 42 riddhi ri****[email protected] 43 JYOTI JT****[email protected] 44 priyawart kumar pr****[email protected] 45 raymondo ra****[email protected] -
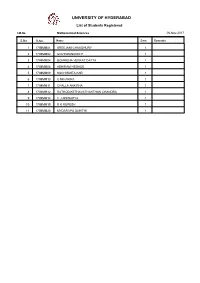
List of Students Onroles
UNIVERSITY OF HYDERABAD List of Students Registered I.M.Sc. Mathematical Sciences 06-Nov-2017 S.No R.No. Name Sem Remarks 1 17IMMM01 SREEJANI CHAUDHURY 1 2 17IMMM02 GOVINDANUNNI P 1 3 17IMMM04 BOMMENA VENKAT DATTA 1 4 17IMMM06 ABHIRAM HEGADE 1 5 17IMMM08 SUCHISMITA KAR 1 6 17IMMM10 G NIHARIKA 1 7 17IMMM11 CHALLA ANKITHA 1 8 17IMMM12 RATHOD KETHAVATH MITHUN CHANDRA 1 9 17IMMM14 C J AISWARYA 1 10 17IMMM19 R K RUPESH 1 11 17IMMM20 MYDARAPU SAHITHI 1 UNIVERSITY OF HYDERABAD List of Students Registered I.M.Sc. Mathematical Sciences 06-Nov-2017 S.No R.No. Name Sem Remarks 1 16IMMM01 ADITYA SARMA PHUKON 3 2 16IMMM08 JAY PRADHAN 3 3 16IMMM09 KODAMANCHILI SAI PAVAN KUMAR 3 4 16IMMM12 NABARUN SAHA 3 5 16IMMM15 PANDI SRIDINESH 3 UNIVERSITY OF HYDERABAD List of Students Registered I.M.Sc. Mathematical Sciences 06-Nov-2017 S.No R.No. Name Sem Remarks 1 15IMMM01 KANIKIREDDY NAGAPOOJITHA 5 2 15IMMM05 ALAPATI CHAITANYA LAKSHMI 5 3 15IMMM07 K TITIKSHA SRINIVAS 5 4 15IMMM09 GOUTHA SAMYUSHA 5 5 15IMMM15 SHILPI MANDAL 5 6 15IMMM17 TAMARANA Y V L PRASANTH 5 7 15IMMM18 ALAAP HASAN 5 8 15IMMM19 SAI KRISHNA AMANCHI 5 9 15IMMM21 TADINADA SRI HARSHITHA 5 UNIVERSITY OF HYDERABAD List of Students Registered I.M.Sc. Mathematical Sciences 06-Nov-2017 S.No R.No. Name Sem Remarks 1 14ILMB18 MANUPRASAD E 7 2 14IMMM01 P R NANDA KUMARI 7 3 14IMMM03 RUDDARRAJU AMRUTHA 7 4 14IMMM13 BODA SWAROOPA 7 UNIVERSITY OF HYDERABAD List of Students Registered I.M.Sc. -
![Af]]SRT\ T`^A]Vev T]RZ^D 4YZ R](https://docslib.b-cdn.net/cover/4491/af-srt-t-a-vev-t-rz-d-4yz-r-3854491.webp)
Af]]SRT\ T`^A]Vev T]RZ^D 4YZ R
6 7 C!# ' : ' : : VRGR $"#(!#1')VCEBRS WWT!Pa!RT%&!$"#1$# 7,8)7'&9+43 8484 & 981:5 "" /;<4=<. "% !E 2088 0F278H";7$IA&7G8 .77.097A7& #80970<.AB) $9B0$9<$82) 70#A9 F27;707#$0BB7& 72A8F .977< .9#7&9 #89#< 9F#8$#G7;F)# 0. 065@ 77& 15 D 2 ! 8 "#:: $55; 31 8)#8097 The Global Times, the points, including the Galwan restored with the Chinese Government mouthpiece of $ !! Valley, Hot Springs and Gogra, troops going back to their hile face-off is still on at China, while reporting Chinese ! ! Wenbin said disengagement positions as in April last. Wsome friction points on Foreign Ministry spokesperson was completed in most areas. Incidentally, the first stand- the Line of Actual Control Wang Wenbin’s observations, " Last Friday, joint secretary off was triggered in the (LAC) in Ladakh and India is also said the disengagement on level officers of the foreign Pangong Tso after the Chinese 8)#8097:;7< asking China to “sincerely” the frontline has completed in .! ! ministries of two countries troops obstructed an Indian implement pacts to defuse ten- most locations following close ! ! ! held talks under the aegis the patrol leading to fisticuffs on ajasthan Chief Minister sion, Beijing on Tuesday communications between the ! Working Mechanism for May 5. The Chinese intruded RAshok Gehlot has sent a QR claimed that the troops from two sides via military and => Consultation and Coordination more than five kms there and revised proposal to Governor both sides have completed dis- diplomatic channels. (WMCC) on border affairs. are yet to withdraw leading to Kalraj Mishra for convening !" engagement and situation is “The situation is now con- 7 ! *! India then asked China to tension in the area. -

Tamil Dubbed Movies List in Tamilyog
Tamil dubbed movies list in tamilyog Continue Filmography and biography of Mahesh Babu, who began his career with the film Raja Kumarudu. He owns the production house G. Mahesh Babu Entertainment Pvt. KeithUstp2790. Mahesh Babu Gattamaneni Krishna (Mahesh Babu) is an Indian film actor and producer, born August 9, 1975, in Chennai, Tamil Nadu, India. ... Ajay, (Mahesh Babu) is an undercover policeman, assigned to catch a dangerous mafia don with whom he has a personal account to settle. Menu. Check out actor Mahesh Babu's filmography and get a full list of all his upcoming films releasing in the coming months, his previous year releases, and the hit and flop movies on Bookmyshow. Tags: Download Mahesh Babu Tamil dubbed Movies Video , Mahesh Babu Tamil called movies HD Song , Mahesh Babu Tamil called the movies He is known for his work mainly in the cinema Telugu. Mahesh Babu has a big fan following among girls; He is one of the most beautiful actors in India. Many of Mahesh Babu's films have been remade into Tamil, Ori and Hindi languages. The list of Hindi named films Mahesh Babu Mahesh Babu is an Indian film actor known for his work exclusively in the telugu cinema. List of Hindi films named (South Indian). Mary Adalat - Mahesh Babu - New Hindi Action Named Movie 2014 - Hindi Films 2014 Full Film. Read more: 15 Best Vijay Sethupathi Movies: No 1 All Time Blockbuster; Mahesh Babu's best films: No 1 is ll Time Blockbuster; List of Nani Movies: Number 1 Will Am azed You List hindi named movies Mahesh Babu My System 2016 - Hindi named full film - Mahesh Babu and Hindi Films 2016 Full Moviemovie - Best Action Films, Movie About Part 4/4. -

NURSE-UR.Pdf
NAME REGN. NO. CATEGORY DOB MARKS Jabara Ram 1704014719 UR 11/02/1993 70 Manprit Singh 1704013396 UR 20/10/1992 69.5 Suresh Khawa 1704014886 UR 20/01/1990 68.75 Rinku Singh 1704008161 UR 10/01/1992 68.5 Swati 1704004627 UR 10/02/1994 68 Bikram 1704017809 UR 20/06/1991 67.5 Sudhanshu Sharma 1704014558 UR 13/05/1988 66.5 Reena 1704015276 UR 04/12/1993 65.75 Arvind Dadheech 1704007487 UR 08/01/1993 65 Gajendra Kumar Sanbhariya 1704013988 UR 11/06/1994 64.5 Devendra Singh Rathore 1704001711 UR 14/08/1990 63.25 Vishnu Praasad Sharma 1704009938 UR 11/03/1991 63.25 Anil Kumar 1704018330 UR 08/04/1992 63 Rajpal Kaur 1704013385 UR 19/12/1992 62.5 Ruksana 1704009900 UR 18/03/1987 61.75 Jomon Chacko 1704005578 UR 05/03/1989 61.75 Poonam Devi 1704000315 UR 07/11/1992 61.5 Kritika Sharma 1704006856 UR 30/03/1993 61.25 Jeetendra Kumar Sharma 1704014612 UR 01/11/1994 60.75 Anil Kumar 1704003536 UR 03/07/1993 60.5 Renu Sharma 1704012148 UR 15/07/1993 60.5 Ram Kishan Rajpurohit 1704001043 UR 10/07/1990 60.25 Preeti 1704004105 UR 01/11/1993 59.75 Deepak Kumar Sharma 1704014144 UR 05/04/1989 59.5 Pavan Kumar Gour 1704001971 UR 30/03/1991 59.5 Sunil Kumar Sharma 1704013115 UR 12/02/1992 59.5 Chhel Singh 1704014661 UR 09/11/1992 59.5 Kapil Kumar 1704004184 UR 16/08/1990 59.25 Bimla Sharma 1704001725 UR 05/10/1991 59 Bhagwan Singh 1704000822 UR 25/05/1993 59 Biji Punnose 1704000506 UR 06/09/1994 59 Anil Kumar 1704011867 UR 08/02/1989 58.75 Mahesh Kumar Sharma 1704010812 UR 21/04/1993 58.75 Bhop Singh 1704015102 UR 07/07/1993 58.75 Aashoo Singh 1704013905 UR -

09072014 MA PS IV-SEM.Pdf
S.NO.AER/2014/313 --------------------- UNIVERSITY OF DELHI ------------------- M.A. PART II (IV SEMESTER) EXAMINATION 2014. --------------------------------------------- POLITICAL SCIENCE ----------------- The following candidates of M.A. Political Science Part II (IV Semester) Examination held in May, 2014 are declared to have passed the Examination for the Degree of M.A. in Political Science:- -------------------------------------------------------------------- Roll No. Name of Marks Obtained Division (Out of 1600) -------------------------------------------------------------------- HINDU COLLEGE ------------- 24867 ABHA PANDEY (W) 973 I D/O LALAN PRASAD PANDEY 24868 AJAY KUMAR 851 II S/O SANTOSH KUMAR 24869 ANIL KUMAR 852 II S/O RAM SWAROOP 24870 ANKIT TOMAR 931 II 24871 ASHISH PHILIP 858 II 24872 BRISTI REKHA MAHANTA (W) 935 II 24873 DEEPALI SUNDER (W) 835 II 24874 DIGVIJAY SINGH 884 II S/O BIJAYNARAYAN SINGH 24875 DIMPI DUTTA (W) 799 III 24876 JATAN KUMAR DEONATH 918 II 24877 KHUSHI LOHIT (W) 953 II 24878 KIRAN LAMBA (W) 929 II 24879 KRISHNAMURARI MUKHERJEE 949 II 24882 MANISH BARMA 861 II 24884 NAVIN KUMAR 836 II S/O SATYANARAYAN PRASAD Contd.P/2 - 2 - UNIVERSITY OF DELHI ------------------- M.A. IN POLITICAL SCIENCE PART II (IV SEMESTER) EXAMINATION 2014. ----------------------------------------------------------------- -------------------------------------------------------------------- Roll No. Name of Marks Obtained Division (Out of 1600) -------------------------------------------------------------------- HINDU COLLEGE ------------- -
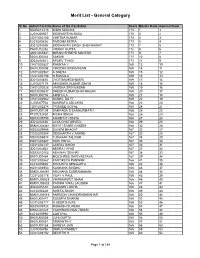
Merit List - General Category
Merit List - General Category Sl.No Admit Card No Name of the Candidate Score Master Rank General Rank 1 ND05U11213 NIDHI MODANI 175 1 1 2 LU01U06927 SIDDHARTHA BASU 175 3 2 3 CD01U02165 CHETNA KUMAR 173 4 3 4 KL01U05836 PAROMA MITRA 173 5 4 5 JD01U04536 SIDDHARTH SINGH SHEKHAWAT 173 7 5 6 PA01U12262 VISHAV GUPTA 172 8 6 7 GN01U03481 MIRANI SHREYE MAHESH 171 9 7 8 BA01U00034 SAKSHI 171 10 8 9 JD02U04941 APURV TYAGI 171 11 9 10 CH01U02827 RAMYAA V 169 13 10 11 BA01U00009 VINODINI SRINIVASAN 169 14 11 12 CH01U02967 A SNEHA 169 15 12 13 CC01U03158 N RAMOLA 169 16 13 14 JD01U04455 JYOTI MAHESHWARI 169 17 14 15 LU01U07119 ABHISHEK KUMAR SINGH 169 18 15 16 CH01U03028 VARSHA SRINIVASAN 169 19 16 17 ND03U09847 DHEER KUMAR BHATNAGAR 169 20 17 18 BA01U00706 AMSHULA 169 21 18 19 CH01U02962 SUSHIL DUTT 169 22 19 20 LU02U07738 NAMRATA ADLAKHA 168 23 20 21 CD01U02274 TRISHEE GOYAL 168 24 21 22 BA01U00109 SAMPADA S BANNURMATH 168 25 22 23 PT01U12430 RICHA SINGH 168 26 23 24 ND03U09756 ANUBHUTI SINHA 168 27 24 25 JD01U04336 JAYA CHATURVEDI 168 29 25 26 MM01U08361 NIYATI SAMIR GANDHI 168 30 26 27 ND03U09966 SUVENI BHAGAT 167 32 27 28 CC02U03388 SIDDHARTH V ANAND 167 33 28 29 ND03U09874 TUSHAAR TALWAR 167 34 29 30 HD01U03887 HARI PRIYA 167 35 30 31 CD01U02137 JASRAJ SINGH 167 36 31 32 JD01U04352 NEERAJ VYAS 167 37 32 33 ND03U10103 ABHINAV SEKHRI 167 38 33 34 BA01U00464 MOLSHREE SHRIVASTAVA 167 39 34 35 CD01U02467 KARTIKEYA PANWAR 166 41 35 36 KL01U05850 SHOURYA SENGUPTA 166 42 36 37 HD01U03903 KUSHANK SINDHU 166 43 37 38 MM01U08491 ARCHANA SUBRAMANIAN