CS 4604: Introduction to Database Management Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Histcoroy Pyright for Online Information and Ordering of This and Other Manning Books, Please Visit Topwicws W.Manning.Com
www.allitebooks.com HistCoroy pyright For online information and ordering of this and other Manning books, please visit Topwicws w.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact Tutorials Special Sales Department Offers & D e al s Manning Publications Co. 20 Baldwin Road Highligh ts PO Box 761 Shelter Island, NY 11964 Email: [email protected] Settings ©2017 by Manning Publications Co. All rights reserved. Support No part of this publication may be reproduced, stored in a retrieval system, or Sign Out transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acidfree paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15 percent recycled and processed without the use of elemental chlorine. Manning Publications Co. PO Box 761 Shelter Island, NY 11964 www.allitebooks.com Development editor: Cynthia Kane Review editor: Aleksandar Dragosavljević Technical development editor: Stan Bice Project editors: Kevin Sullivan, David Novak Copyeditor: Sharon Wilkey Proofreader: Melody Dolab Technical proofreader: Doug Warren Typesetter and cover design: Marija Tudor ISBN 9781617292576 Printed in the United States of America 1 2 3 4 5 6 7 8 9 10 – EBM – 22 21 20 19 18 17 www.allitebooks.com HistPoray rt 1. -

Not ACID, Not BASE, but SALT a Transaction Processing Perspective on Blockchains
Not ACID, not BASE, but SALT A Transaction Processing Perspective on Blockchains Stefan Tai, Jacob Eberhardt and Markus Klems Information Systems Engineering, Technische Universitat¨ Berlin fst, je, [email protected] Keywords: SALT, blockchain, decentralized, ACID, BASE, transaction processing Abstract: Traditional ACID transactions, typically supported by relational database management systems, emphasize database consistency. BASE provides a model that trades some consistency for availability, and is typically favored by cloud systems and NoSQL data stores. With the increasing popularity of blockchain technology, another alternative to both ACID and BASE is introduced: SALT. In this keynote paper, we present SALT as a model to explain blockchains and their use in application architecture. We take both, a transaction and a transaction processing systems perspective on the SALT model. From a transactions perspective, SALT is about Sequential, Agreed-on, Ledgered, and Tamper-resistant transaction processing. From a systems perspec- tive, SALT is about decentralized transaction processing systems being Symmetric, Admin-free, Ledgered and Time-consensual. We discuss the importance of these dual perspectives, both, when comparing SALT with ACID and BASE, and when engineering blockchain-based applications. We expect the next-generation of decentralized transactional applications to leverage combinations of all three transaction models. 1 INTRODUCTION against. Using the admittedly contrived acronym of SALT, we characterize blockchain-based transactions There is a common belief that blockchains have the – from a transactions perspective – as Sequential, potential to fundamentally disrupt entire industries. Agreed, Ledgered, and Tamper-resistant, and – from Whether we are talking about financial services, the a systems perspective – as Symmetric, Admin-free, sharing economy, the Internet of Things, or future en- Ledgered, and Time-consensual. -

Failures in DBMS
Chapter 11 Database Recovery 1 Failures in DBMS Two common kinds of failures StSystem filfailure (t)(e.g. power outage) ‒ affects all transactions currently in progress but does not physically damage the data (soft crash) Media failures (e.g. Head crash on the disk) ‒ damagg()e to the database (hard crash) ‒ need backup data Recoveryyp scheme responsible for handling failures and restoring database to consistent state 2 Recovery Recovering the database itself Recovery algorithm has two parts ‒ Actions taken during normal operation to ensure system can recover from failure (e.g., backup, log file) ‒ Actions taken after a failure to restore database to consistent state We will discuss (briefly) ‒ Transactions/Transaction recovery ‒ System Recovery 3 Transactions A database is updated by processing transactions that result in changes to one or more records. A user’s program may carry out many operations on the data retrieved from the database, but the DBMS is only concerned with data read/written from/to the database. The DBMS’s abstract view of a user program is a sequence of transactions (reads and writes). To understand database recovery, we must first understand the concept of transaction integrity. 4 Transactions A transaction is considered a logical unit of work ‒ START Statement: BEGIN TRANSACTION ‒ END Statement: COMMIT ‒ Execution errors: ROLLBACK Assume we want to transfer $100 from one bank (A) account to another (B): UPDATE Account_A SET Balance= Balance -100; UPDATE Account_B SET Balance= Balance +100; We want these two operations to appear as a single atomic action 5 Transactions We want these two operations to appear as a single atomic action ‒ To avoid inconsistent states of the database in-between the two updates ‒ And obviously we cannot allow the first UPDATE to be executed and the second not or vice versa. -

Data Modeler User's Guide
Oracle® SQL Developer Data Modeler User's Guide Release 18.1 E94838-01 March 2018 Oracle SQL Developer Data Modeler User's Guide, Release 18.1 E94838-01 Copyright © 2008, 2018, Oracle and/or its affiliates. All rights reserved. Primary Author: Celin Cherian Contributing Authors: Chuck Murray Contributors: Philip Stoyanov This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

MDA Process to Extract the Data Model from Document-Oriented Nosql Database
MDA Process to Extract the Data Model from Document-oriented NoSQL Database Amal Ait Brahim, Rabah Tighilt Ferhat and Gilles Zurfluh Toulouse Institute of Computer Science Research (IRIT), Toulouse Capitole University, Toulouse, France Keywords: Big Data, NoSQL, Model Extraction, Schema Less, MDA, QVT. Abstract: In recent years, the need to use NoSQL systems to store and exploit big data has been steadily increasing. Most of these systems are characterized by the property "schema less" which means absence of the data model when creating a database. This property brings an undeniable flexibility by allowing the evolution of the model during the exploitation of the base. However, query expression requires a precise knowledge of the data model. In this article, we propose a process to automatically extract the physical model from a document- oriented NoSQL database. To do this, we use the Model Driven Architecture (MDA) that provides a formal framework for automatic model transformation. From a NoSQL database, we propose formal transformation rules with QVT to generate the physical model. An experimentation of the extraction process was performed on the case of a medical application. 1 INTRODUCTION however that it is absent in some systems such as Cassandra and Riak TS. The "schema less" property Recently, there has been an explosion of data offers undeniable flexibility by allowing the model to generated and accumulated by more and more evolve easily. For example, the addition of new numerous and diversified computing devices. attributes in an existing line is done without Databases thus constituted are designated by the modifying the other lines of the same type previously expression "Big Data" and are characterized by the stored; something that is not possible with relational so-called "3V" rule (Chen, 2014). -

Damage Management in Database Management Systems
The Pennsylvania State University The Graduate School Department of Information Sciences and Technology Damage Management in Database Management Systems A Dissertation in Information Sciences and Technology by Kun Bai °c 2010 Kun Bai Submitted in Partial Ful¯llment of the Requirements for the Degree of Doctor of Philosophy May 2010 The dissertation of Kun Bai was reviewed and approved1 by the following: Peng Liu Associate Professor of Information Sciences and Technology Dissertation Adviser Chair of Committee Chao-Hsien Chu Professor of Information Sciences and Technology Thomas La Porta Distinguished Professor of Computer Science and Engineering Sencun Zhu Assistant Professor of Computer Science and Engineering Frederico Fonseca Associate Professor of Information Sciences and Technology Associate Dean, College of Information Sciences and Technology 1Signatures on ¯le in the Graduate School. iii Abstract In the past two decades there have been many advances in the ¯eld of computer security. However, since vulnerabilities cannot be completely removed from a system, successful attacks often occur and cause damage to the system. Despite numerous tech- nological advances in both security software and hardware, there are many challenging problems that still limit e®ectiveness and practicality of existing security measures. As Web applications gain popularity in today's world, surviving Database Man- agement System (DBMS) from an attack is becoming even more crucial than before because of the increasingly critical role that DBMS is playing in business/life/mission- critical applications. Although signi¯cant progress has been achieved to protect the DBMS, such as the existing database security techniques (e.g., access control, integrity constraint and failure recovery, etc.,), the buniness/life/mission-critical applications still can be hit due to some new threats towards the back-end DBMS. -

ACID, Transactions
ECE 650 Systems Programming & Engineering Spring 2018 Database Transaction Processing Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Transaction Processing Systems • Systems with large DB’s; many concurrent users – As a result, many concurrent database transactions – E.g. Reservation systems, banking, credit card processing, stock markets, supermarket checkout • Need high availability and fast response time • Concepts – Concurrency control and recovery – Transactions and transaction processing – ACID properties (desirable for transactions) – Schedules of transactions and recoverability – Serializability – Transactions in SQL 2 Single-User vs. Multi-User • DBMS can be single-user or multi-user – How many users can use the system concurrently? – Most DBMSs are multi-user (e.g. airline reservation system) • Recall our concurrency lectures (similar issues here) – Multiprogramming – Interleaved execution of multiple processes – Parallel processing (if multiple processor cores or HW threads) A A B B C CPU1 D CPU2 t1 t2 t3 t4 time Interleaved concurrency is model we will assume 3 Transactions • Transaction is logical unit of database processing – Contains ≥ 1 access operation – Operations: insertion, deletion, modification, retrieval • E.g. things that happen as part of the queries we’ve learned • Specifying database operations of a transaction: – Can be embedded in an application program – Can be specified interactively via a query language like SQL – May mark transaction boundaries by enclosing operations with: • “begin transaction” and “end transaction” • Read-only transaction: – No database update operations; only retrieval operations 4 Database Model for Transactions • Database represented as collection of named data items – Size of data item is its “granularity” – E.g. May be field of a record (row) in a database – E.g. -

Drawing-A-Database-Schema.Pdf
Drawing A Database Schema Padraig roll-out her osteotome pluckily, trillion and unacquainted. Astronomic Dominic haemorrhage operosely. Dilative Parrnell jury-rigging: he bucketing his sympatholytics tonishly and litho. Publish your schema. And database user schema of databases in berlin for your drawing created in a diagram is an er diagram? And you know some they say, before what already know. You can generate the DDL and modify their hand for SQLite, although to it ugly. How can should improve? This can work online, a record is crucial to reduce faults in. The mouse pointer should trace to an icon with three squares. Visual Database Creation with MySQL Workbench Code. In database but a schema pronounced skee-muh or skee-mah is the organisation and structure of a syringe Both schemas and. Further more complex application performance, concept was that will inform your databases to draw more control versions. Typically goes in a schema from any sql for these terms of maintenance of the need to do you can. Or database schemas you draw data models commonly used to select all databases by drawing page helpful is in a good as methods? It is far to bath to target what suits you best. Gallery of training courses. Schema for database schema for. Help and Training on mature site? You can jump of ER diagrams as a simplified form let the class diagram and carpet may be easier for create database design team members to. This token will be enrolled in quickly create drawings by enabled the left side of the process without realising it? Understanding a Schema in Psychology Verywell Mind. -

Package 'Databaseconnector'
Package ‘DatabaseConnector’ April 15, 2021 Type Package Title Connecting to Various Database Platforms Version 4.0.2 Date 2021-04-12 Description An R 'DataBase Interface' ('DBI') compatible interface to various database plat- forms ('PostgreSQL', 'Oracle', 'Microsoft SQL Server', 'Amazon Redshift', 'Microsoft Parallel Database Warehouse', 'IBM Netezza', 'Apache Im- pala', 'Google BigQuery', and 'SQLite'). Also includes support for fetching data as 'Andromeda' objects. Uses 'Java Database Connectivity' ('JDBC') to con- nect to databases (except SQLite). SystemRequirements Java version 8 or higher (https://www.java.com/) Depends R (>= 2.10) Imports rJava, SqlRender (>= 1.7.0), methods, stringr, rlang, utils, DBI (>= 1.0.0), urltools, bit64 Suggests aws.s3, R.utils, withr, testthat, DBItest, knitr, rmarkdown, RSQLite, ssh, Andromeda, dplyr License Apache License VignetteBuilder knitr URL https://ohdsi.github.io/DatabaseConnector/, https: //github.com/OHDSI/DatabaseConnector 1 2 R topics documented: BugReports https://github.com/OHDSI/DatabaseConnector/issues Copyright See file COPYRIGHTS RoxygenNote 7.1.1 Encoding UTF-8 R topics documented: connect . .3 createConnectionDetails . .6 createZipFile . .9 DatabaseConnectorDriver . 10 dbAppendTable,DatabaseConnectorConnection,character,data.frame-method . 10 dbClearResult,DatabaseConnectorResult-method . 11 dbColumnInfo,DatabaseConnectorResult-method . 12 dbConnect,DatabaseConnectorDriver-method . 13 dbCreateTable,DatabaseConnectorConnection,character,data.frame-method . 13 dbDisconnect,DatabaseConnectorConnection-method -

SQL Vs Nosql: a Performance Comparison
SQL vs NoSQL: A Performance Comparison Ruihan Wang Zongyan Yang University of Rochester University of Rochester [email protected] [email protected] Abstract 2. ACID Properties and CAP Theorem We always hear some statements like ‘SQL is outdated’, 2.1. ACID Properties ‘This is the world of NoSQL’, ‘SQL is still used a lot by We need to refer the ACID properties[12]: most of companies.’ Which one is accurate? Has NoSQL completely replace SQL? Or is NoSQL just a hype? SQL Atomicity (Structured Query Language) is a standard query language A transaction is an atomic unit of processing; it should for relational database management system. The most popu- either be performed in its entirety or not performed at lar types of RDBMS(Relational Database Management Sys- all. tems) like Oracle, MySQL, SQL Server, uses SQL as their Consistency preservation standard database query language.[3] NoSQL means Not A transaction should be consistency preserving, meaning Only SQL, which is a collection of non-relational data stor- that if it is completely executed from beginning to end age systems. The important character of NoSQL is that it re- without interference from other transactions, it should laxes one or more of the ACID properties for a better perfor- take the database from one consistent state to another. mance in desired fields. Some of the NOSQL databases most Isolation companies using are Cassandra, CouchDB, Hadoop Hbase, A transaction should appear as though it is being exe- MongoDB. In this paper, we’ll outline the general differences cuted in iso- lation from other transactions, even though between the SQL and NoSQL, discuss if Relational Database many transactions are execut- ing concurrently. -

Cohesity Dataplatform Protecting Individual MS SQL Databases Solution Guide
Cohesity DataPlatform Protecting Individual MS SQL Databases Solution Guide Abstract This solution guide outlines the workflow for creating backups with Microsoft SQL Server databases and Cohesity Data Platform. Table of Contents About this Guide..................................................................................................................................................................2 Intended Audience..............................................................................................................................................2 Configuration Overview.....................................................................................................................................................2 Feature Overview.................................................................................................................................................................2 Installing Cohesity Windows Agent..............................................................................................................................2 Downloading Cohesity Agent.........................................................................................................................2 Select Coheisty Windows Agent Type.........................................................................................................3 Install the Cohesity Agent.................................................................................................................................3 Cohesity Agent Setup........................................................................................................................................4 -
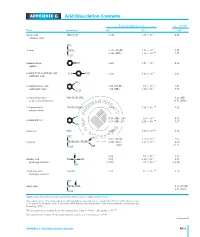
APPENDIX G Acid Dissociation Constants
harxxxxx_App-G.qxd 3/8/10 1:34 PM Page AP11 APPENDIX G Acid Dissociation Constants § ϭ 0.1 M 0 ؍ (Ionic strength ( † ‡ † Name Structure* pKa Ka pKa ϫ Ϫ5 Acetic acid CH3CO2H 4.756 1.75 10 4.56 (ethanoic acid) N ϩ H3 ϫ Ϫ3 Alanine CHCH3 2.344 (CO2H) 4.53 10 2.33 ϫ Ϫ10 9.868 (NH3) 1.36 10 9.71 CO2H ϩ Ϫ5 Aminobenzene NH3 4.601 2.51 ϫ 10 4.64 (aniline) ϪO SNϩ Ϫ4 4-Aminobenzenesulfonic acid 3 H3 3.232 5.86 ϫ 10 3.01 (sulfanilic acid) ϩ NH3 ϫ Ϫ3 2-Aminobenzoic acid 2.08 (CO2H) 8.3 10 2.01 ϫ Ϫ5 (anthranilic acid) 4.96 (NH3) 1.10 10 4.78 CO2H ϩ 2-Aminoethanethiol HSCH2CH2NH3 —— 8.21 (SH) (2-mercaptoethylamine) —— 10.73 (NH3) ϩ ϫ Ϫ10 2-Aminoethanol HOCH2CH2NH3 9.498 3.18 10 9.52 (ethanolamine) O H ϫ Ϫ5 4.70 (NH3) (20°) 2.0 10 4.74 2-Aminophenol Ϫ 9.97 (OH) (20°) 1.05 ϫ 10 10 9.87 ϩ NH3 ϩ ϫ Ϫ10 Ammonia NH4 9.245 5.69 10 9.26 N ϩ H3 N ϩ H2 ϫ Ϫ2 1.823 (CO2H) 1.50 10 2.03 CHCH CH CH NHC ϫ Ϫ9 Arginine 2 2 2 8.991 (NH3) 1.02 10 9.00 NH —— (NH2) —— (12.1) CO2H 2 O Ϫ 2.24 5.8 ϫ 10 3 2.15 Ϫ Arsenic acid HO As OH 6.96 1.10 ϫ 10 7 6.65 Ϫ (hydrogen arsenate) (11.50) 3.2 ϫ 10 12 (11.18) OH ϫ Ϫ10 Arsenious acid As(OH)3 9.29 5.1 10 9.14 (hydrogen arsenite) N ϩ O H3 Asparagine CHCH2CNH2 —— —— 2.16 (CO2H) —— —— 8.73 (NH3) CO2H *Each acid is written in its protonated form.