Chapter 1: Introduction
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

3S Ägare Hutchison Presenterar INQ1 - Facebookmobil Till Lågt Pris
2008-11-13 11:04 CET 3s ägare Hutchison presenterar INQ1 - facebookmobil till lågt pris 3s ägare Hutchison Whampoa tar nu upp konkurrensen med Sony Ericsson och Nokia och börjar tillverka egna mobiler under namnet INQ. Den första modellen, som presenteras idag, kombinerar Facebook med ett lågt pris. I början av nästa år kommer den att finnas i Sverige. INQ ska inte konkurrera med avancerade smartphones som Apple iPhone, Sony Ericsson X1 eller Nokia N96. I ställer har Hutchison Whampoa valt att rikta in sig på resten av marknaden, de 90 % som vill kunna använda Internet i mobilen precis som på datorn men som inte vill betala en förmögenhet för mobilen för att göra detta. Därför ska INQ tillverka mobiler där det är lätt att använda Internettjänster och som samtidigt är billiga. - INQ erbjuder en helt ny användareupplevelse på mobilen. Vi vill ta de tjänster som människor lärt sig älska på nätet och bygga in dem rakt in i hjärtat på våra mobiler. Borta är alla besvärliga inställningar. Vi gör det lika enkelt att följa dina vänner via Facebook som det är att ringa ett vanligt telefonsamtal, säger Frank Meehan, VD för INQ. - Vi är lyckliga över samarbetet med INQ och väldigt imponerade över vilken bra facebookupplevelse det blir i INQ1. Just nu har vi omkring 15 miljoner mobila facebookanvändare. Antalet har fördubblats de senaste 6 månaderna och vi hoppas att det kommer att öka ändå snabbare tack vare INQ, säger Mark Zuckerberg, koncernchef på Facebook. Förutom Facebook har INQ1 Skype med fria skypesamtal till 360 miljoner människor världen över, Windows Live Messenger och musiktjänsten Last.fm inbyggda. -

Lamadrid Android
ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID THOUGHTS IN BRIEF: FGSDFG FDDFGDF(i) A quick overview of the facts (ii) Business considerations and ANTITRUSTbackground DOMINANT(iii)The POSITION Law : (I) Dominance mokmdokamsdfkmasodmkfosakdmfosdkmf(iv)The Law: (II) Predatory okmsadf allegations IT MARKET(v) The Law: (III) Bundling allegations ANDROID FGSDFG THE FACTS FDDFGDF ANTITRUST DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET • AndroidANDROID is an open source OS licensed on a royalty-free basis. Licensees remain free to do whatever they wish with the code (e.g. downloading,FGSDFG distributing or modifying –forking- it). • OEMs remain free to use Android with or without Google Apps (e.g. NokiaFDDFGDF X). • WhenANTITRUST OEMs wish to offer certain Google apps on top of Android they can enter into a MADA which requires them to (i) preload a minimum set ofDOMINANT apps (GMS); POSITION (ii) place Search widget and GooglePlay icons in a certain way; and (iii) use Google Search as default engine for the searchmokmdokamsdfkmasodmkfosakdmfosdkmf intent. okmsadf • OEMs (and users) remain at all times free to pre-install at any time any nonIT MARKET-Google app (including a non-Google App Store) = no Google walled garden (room for intra-ecosystem competition) ANDROID A MATTER OF DIFFERENT FGSDFG FDDFGDFBUSINESS MODELS ANTITRUST DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET EssentiallyANDROID 3 different business models for mobile operating systems (OSs): i. Apple’s vertically integrated model - Monetization via sales of devices. -

Symbian OS As a Research Platform – Present and Future
Symbian OS as a Research Platform Present and Future Lawrence Simpson Research Department Symbian Copyright © 2008 Symbian Software Ltd. Symbian Platform Symbian OS is a separate platform, specifically designed for mobile & convergent devices. Not an adaptation of Unix or Windows or .... Symbian OS has facilities to support • Small (memory) footprint • Low power consumption • High reliability • “Always on”, but must deal with unplanned shutdown • Diverse range of hardware • Diverse manufacturers – multiple UIs and multiple brands Different UIs on the same underlying system Series 60 (S60) • Provided by Nokia. • Used by Nokia & S60 licensees. • Originally a keypad-based UI ... now supporting touch-screen variants. UIQ • Provided by UIQ – company has sometimes been owned by Symbian, sometimes by Sony Ericsson/Motorola. • Used by Sony Ericsson & Motorola. • Originally mainly a touch-screen UI ... now supporting keypad-only variants. MOAP(S) • Provided through NTT DOCOMO. • Used by several Symbian licensees in Japan. Software in a Symbian Phone – “Habitats of the Symbian Eco-System” User-Installed Applications “In-the-box” Applications (commissioned/written by the phone-maker, built into the phone ROM) User Interface (S60 or UIQ or MOAP) Symbian OS Hardware Adaptation Software (usually from chip-vendors or 3rd parties) Symbian OS component level view developer.symbian.com/main/documentation/technologies/system_models OS designed for Smartphones & Media Phones Core OS Technologies Other Smartphone Technologies • Telephony Services • PIM (calendars, agenda, etc.) • Shortlink (BT, USB) Services • Messaging • Networking (IP) Services • Remote Management • Multimedia (audio & video) • Java / J2ME • Graphics • Security Management • Location-Based Services (LBS) • Multimedia Middleware • Base Services: (Database Utilities, • Application Protocols Localisation, etc.) • GUI Framework • Kernel Symbian programming paradigms • Several paradigms to support mobility, reliability, security, including.. -

Meego Smartphones and Operating System Find a New Life in Jolla Ltd
Jolla Ltd. Press Release July 7, 2012 Helsinki, Finland FOR IMMEDIATE RELEASE MeeGo Smartphones and Operating System Find a New Life in Jolla Ltd. Jolla Ltd. is an independent Finland based smartphone product company which continues the excellent work that Nokia started with MeeGo. The Jolla team is formed by directors and core professionals from Nokia's MeeGo N9 organisation, together with some of the best minds working on MeeGo in the communities. Jussi Hurmola, CEO Jolla Ltd.: "Nokia created something wonderful - the world's best smartphone product. It deserves to be continued, and we will do that together with all the bright and gifted people contributing to the MeeGo success story." Jolla Ltd. will design, develop and sell new MeeGo based smartphones. Together with international private investors and partners, a new smartphone using this MeeGo based OS will be revealed later this year. Jolla Ltd. has been developing a new smartphone product and the OS since the end of 2011. The OS has evolved from MeeGo OS using Mer Core and Qt with Jolla technology including its own brand new UI. The Jolla team consists of a substantial number of MeeGo's core engineers and directors, and is aggressively hiring the top MeeGo and Linux talent to contribute to the next generation smartphone production. Company is headquartered in Helsinki, Finland and has an R&D office in Tampere, Finland. Sincerely, Jolla Ltd. Dr. Antti Saarnio - Chairman & Finance Mr. Jussi Hurmola - CEO Mr. Sami Pienimäki - VP, Sales & Business Development Mr. Stefano Mosconi - CIO Mr. Marc Dillon - COO Further inquiries: [email protected] Jolla Ltd. -
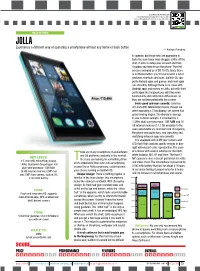
Overall Features Performance Price
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -

Mer: Core OS Mobile & Devices
Mer: Core OS mobile & devices Qt Developer Days - Silicon Valley 2012 Carl Symons Introduction Plasma Active chooses Mer Not just another Linux distribution Focus - device providers Where's Mer? SDKs - apps & platform Get Mer Resources Carl Symons Large company Mktg/BusDev Start-ups } Slightly geeky Grassroots LinuxFest organizer KDE News editor/promo KDE Plasma Active Mer upstream and downstream First LinuxCon September 2009 Portland Moblin is a hot topic Moblin 2.1 for phones introduced MeeGo Announced February 201 0 Moblin & Maemo merger Support for Intel Atom Desktop Summit August 11 , 2011 Berlin; Free Desktop meeting Developer orientation; ExoPCs MeeGo AppStore A real Linux OS LinuxCon - Vancouver August 1 8, 2011 Intel AppUp Developer orientation; ExoPCs MeeGo AppStore show real Linux OS; possibilities Intel AppUp Elements September 28, 2011 National developer conference Tizen announced (led by Intel and Samsung) MeeGo and Qt abandoned HTML5/CSS3 Maemo Reconstructed October 3, 2011 Mer announced The spirit of MeeGo lives on Plasma Active chooses Mer October 5, 2011 No viable alternative Lightweight Mer talent and community Performant Boot time - more than a minute to about 1 5 seconds on Atom tablet Not just another Linux MeeGo - large company dominated; closed governance Mer - Core OS only Packages Focus - Device Providers Complete world class platform for building commercial products Modern, clean Linux Easy to try; easy to port Systems, structures, processes, code to serve device providers Where's Mer? X86, ARM, MIPS NemoMobile -

Downloaded From
Mobile communication and the protection of children Ong, R.Y.C. Citation Ong, R. Y. C. (2010, April 22). Mobile communication and the protection of children. Meijers-reeks. Retrieved from https://hdl.handle.net/1887/15349 Version: Not Applicable (or Unknown) Licence agreement concerning inclusion of doctoral thesis in the License: Institutional Repository of the University of Leiden Downloaded from: https://hdl.handle.net/1887/15349 Note: To cite this publication please use the final published version (if applicable). Mobile Communication and the Protection of Children dissertation series no 2010-10 The research reported in this thesis has been carried out under the auspicies of SIKS, the Dutch Research School for Information and Knowledge Systems. Lay-out: Anne-Marie Krens – Tekstbeeld – Oegstgeest © R.Y.C. Ong / Leiden University Press, 2010 ISBN 978 90 8728 080 2 Behoudens de in of krachtens de Auteurswet van 1912 gestelde uitzonderingen mag niets uit deze uitgave worden verveelvoudigd, opgeslagen in een geautomatiseerd gegevensbestand, of openbaar gemaakt, in enige vorm of op enige wijze, hetzij elektronisch, mechanisch, door fotokopieën, opnamen of enige andere manier, zonder voorafgaande schriftelijke toestemming van de uitgever. Voorzover het maken van reprografische verveelvoudigingen uit deze uitgave is toegestaan op grond van artikel 16h Auteurswet 1912 dient men de daarvoor wettelijk verschuldigde vergoedingen te voldoen aan de Stichting Reprorecht (Postbus 3051, 2130 KB Hoofddorp, www.reprorecht.nl). Voor het overnemen van (een) gedeelte(n) uit deze uitgave in bloemlezingen, readers en andere compilatiewerken (art. 16 Auteurswet 1912) kan men zich wenden tot de Stichting PRO (Stichting Publicatie- en Reproductierechten Organisatie, Postbus 3060, 2130 KB Hoofddorp, www.cedar.nl/pro). -

12 October 2009 the Latest Social Mobile INQ Mini 3G with Twitter
12 October 2009 The Latest Social Mobile INQ Mini 3G with Twitter Coloring Customers’ Social Networking Experience Exclusively Available at 3 Hong Kong Hong Kong, 12 October 2009 - 3 Hong Kong, the mobile operation of Hutchison Telecommunications Hong Kong Limited ( “Hutchison Telecom Hong Kong”), today announced that INQ Mini 3G, the second social mobile developed by INQ Mobile, a Hutchison Whampoa Limited’s company, will be launched tomorrow ( 13 October) . Following the success of the award-winning INQ1, the new INQ Mini 3G is pre-installed with the Twitter function on top of its existing social networking applications like Facebook and Skype. With this new colourful and affordable social mobile, customers can network with friends and update their status anytime anywhere, making their lives more colourful. Integrating the most popular social networking services 3 Hong Kong’s initiatives in bringing the first social mobile INQ to Hong Kong early this year has already spearheaded the wave of mobile social networking. The exclusive launch of INQ Mini 3G, which allows customers to post their personal tweets or update the status of their following and followers via Twitter, brings the experience of mobile social networking to the next level. With the integrated phonebook on one interface and a switcher key, users can instantly switch across different social networking accounts like Twitter, Facebook, Window Live Messenger and Skype, upload photos, update status, post new messages or chat with friends anytime, anywhere. 3 Hong Kong customers can also use Facebook and Twitter, watch YouTube via 3Xplorer under the mobile portal of Planet 3, and also access Windows Live Messenger, Yahoo! Messenger and 3 Community via 3messenger. -

Scarica Qui Il
Allegati - Allegato A: Dispositivi non supportati Marca Modello Acer DA241HL DA241HL– DA241HL a3 Stream– a3 da2 DA222HQL– da2 c4 E310– c4 T603T TD600– T603T k4 E140– k4 K3 E130– K3 k5 E210– k5 DA220HQL DA220HQL– DA220HQL Anydata HKCP778A HKC P778A– HKCP778A PLT8223G Proscan PLT8223G– PLT8223G EGP008 ematic EGP008– EGP008 PRO7D Visual Land Prestige 7D– PRO7D MID7065 Coby MID7065– MID7065 I10A-LE Leader I10A-LE– I10A-LE PLT7223G Proscan PLT7223G– PLT7223G M727MC Nextbook Next7P12– M727MC EGS102 ematic EGS102– EGS102 MD7305 Lazer MD7305 Tablet / AMTC– MD7305 CMP749 iCraig CMP749– CMP749 MID1065 Coby MID1065– MID1065 EGP010 ematic EGP010– EGP010 D2-721G D2-721G– D2-721G GR-TB10S Grundig GR-TB10S Tablet– GR-TB10S MID8065 Coby MID8065– MID8065 DT088 DOPO GMS-718 Tablet / Discovery– DT088 M757ND Nextbook Next7D12 Tablet– M757ND AMLMID710K Proscan PLT7777– AMLMID710K MID7317CP Auchan MID7317CP Tablet – MID7317CP PDM829MD Eviant MT8000– PDM829MD ASP320Q_GSM ASP320Q_ANDi– ASP320Q_GSM EGS004 ematic EGS004– EGS004 TBDG773 Zeki TBDG773– TBDG773 EM63 Carrefour CT720 / Emdoor EM63 Tablet– EM63 PMT5877C Prestigio PMT5877C– PMT5877C Trio_Stealth_G2 Mach_Speed Trio G2 Tablet– Trio_Stealth_G2 M712MC HCL ME TABLET PC U2– M712MC P776A HKC P776A– P776A M909NP Nextbook NX008HI Tablet / Carrefour CT810– M909NP E8-3D DOTPAD DP3D8 / Gadmei– E8-3D TAB-840_G Digix TAB-840_G– TAB-840_G D2-727 D2-727G– D2-727 HS_7DTB14 HS_7DTB14– HS_7DTB14 P886A HKC P886A– P886A M7000ND Nextbook NX007HD Tablet– M7000ND MID7055 COBY MID7055– MID7055 CMP748 iCraig CMP748– CMP748 AML757ND -

Review of Service Composition Interfaces
Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES UNIVERSITY OF TAMPERE D‐2009‐7 TAMPERE 2009 UNIVERSITY OF TAMPERE DEPARTMENT OF COMPUTER SCIENCES SERIES OF PUBLICATIONS D – NET PUBLICATIONS D‐2009‐7, OCTOBER 2009 Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES FIN‐33014 UNIVERSITY OF TAMPERE ISBN 978‐951‐44‐7896‐3 ISSN 1795‐4274 Preface This report was produced in the LUCRE project. LUCRE stands for Local and User-Created Services. The project is part of the Flexible Services research programme, one of the programmes of the Strategic Centre for Science, Technology and Innovation in the ICT field (TIVIT) and funded by Tekes (the Finnish Funding Agency for Technology and Innovation) and the participating organizations. The Flexible Service Programme creates service business activity for global markets. The programme has the aim of creating a Web of Services. The programme creates new types of ecosystems, in which the producers of services, the people that convey the service and the users all work together in unison. As part of such ecosystems, LUCRE will develop an easy-to-use, visual service creation platform to support the creation of context aware mobile services. The goal is to support user-driven open innovation: the end- users (people, local businesses, communities) will be provided with tools to compose new services or to modify existing ones. The service creation platform will build on the technology of existing mashup tools, widget frameworks, and publish/subscribe mechanisms. -

The Symbian OS Architecture Sourcebook
The Symbian OS Architecture Sourcebook The Symbian OS Architecture Sourcebook Design and Evolution of a Mobile Phone OS By Ben Morris Reviewed by Chris Davies, Warren Day, Martin de Jode, Roy Hayun, Simon Higginson, Mark Jacobs, Andrew Langstaff, David Mery, Matthew O’Donnell, Kal Patel, Dominic Pinkman, Alan Robinson, Matthew Reynolds, Mark Shackman, Jo Stichbury, Jan van Bergen Symbian Press Head of Symbian Press Freddie Gjertsen Managing Editor Satu McNabb Copyright 2007 Symbian Software, Ltd John Wiley & Sons, Ltd The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England Telephone (+44) 1243 779777 Email (for orders and customer service enquiries): [email protected] Visit our Home Page on www.wileyeurope.com or www.wiley.com All Rights Reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except under the terms of the Copyright, Designs and Patents Act 1988 or under the terms of a licence issued by the Copyright Licensing Agency Ltd, 90 Tottenham Court Road, London W1T 4LP, UK, without the permission in writing of the Publisher. Requests to the Publisher should be addressed to the Permissions Department, John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England, or emailed to [email protected], or faxed to (+44) 1243 770620. Designations used by companies to distinguish their products are often claimed as trademarks. All brand names and product names used in this book are trade names, service marks, trademarks or registered trademarks of their respective owners.