Incoming Student & Resident Tech Requirements
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Powershell Scripting Language Course Proposal for Tallinn University of Technology
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Riivo Kiljak 178071IABM POWERSHELL SCRIPTING LANGUAGE COURSE PROPOSAL FOR TALLINN UNIVERSITY OF TECHNOLOGY Master’s thesis Supervisor: Siim Vene MSc Tallinn 2019 TALLINNA TEHNIKAULIKOOL¨ Infotehnoloogia teaduskond Riivo Kiljak 178071IABM POWERSHELLI SKRIPTIMISKEELE KURSUSE ETTEPANEK TALLINNA TEHNIKAULIKOOLILE¨ Magistrito¨o¨ Juhendaja: Siim Vene MSc Tallinn 2019 Author’s Declaration of Originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Riivo Kiljak 07.05.2019 3 Abstract In the thesis, a recommendation is made to establish a new course at TalTech. The course is intended to teach the PowerShell scripting language to students, most importantly in the IT Systems Administration programme. Course material is proposed in the form of lecture slides, home assignments and knowledge tests. All three of which are available in the appendices of the paper. Design science is used to pass iterations of improving the content prior the the paper publishing. Academic literature is analysed to determine the included and excluded topics and the teaching methodology. More- over, input is acquired from scrutinising public information on Microsoft’s official PowerShell courses and interviewing subject matter experts who use PowerShell at local companies. The course material is provided written in LATEX which means that it can be conveniently modified, version controlled and distributed in the PDF format. Although the proposed course is seen as an online course hosted on Moodle, argumentation is made suggesting a combination with classroom seminars is likely to result in better learning outcomes at the cost of scalability. -

CONESTOGA CABINET ASSEMBLY INFORMATION What Is Included with Your Cabinets: What Is Not Included with Your Cabinets
CONESTOGA CABINET ASSEMBLY INFORMATION We suggest you view the 4 minute assembly demonstration video on our web site to see how easily our high end custom cabinets are assembled. Before continuing, it is important to realize that Conestoga’s RTA cabinet is targeted at cabinet shops who would rather use this system than build their own custom cabinets from scratch. On one hand, this indicates that it’s a VERY high quality cabinet. On the other hand, it means Conestoga has made some assumptions that its user has certain level of cabinet making skills and knowledge which most homeowners may not possess. As a result, we feel the assembly instructions Conestoga details in their guide are incomplete. Therefore, we have compiled the following assembly information from our years of assembly experience with this product. Remember, as opposed to other Conestoga Re-sellers or sales agents, we actually use the product every day. So, if you have a question that is not answered here, just give us a call and we can talk you through it, send you images from our shop floor, diagrams or even helpful hardware items to assist you. If it gets frustrating, take some time away and give us a call or shoot us an email. Rest assured, we’ll get you through it! What is Included with Your Cabinets: Everything necessary to build the cabinet box. Drawer glides and necessary hardware/screws. Hinges and necessary hardware/screws. Doors, drawer fronts and drawer boxes. What is not included with Your Cabinets: Screws required to mount drawer fronts to the drawer boxes (we use self tapping wood screws 1-1/4” long, available at local home centers or hardware stores. -

Solve Errors Caused by Corrupt System Files
System File Corruption Errors Solved S 12/1 Repair Errors Caused by Missing or Corrupt System Files With the information in this article you can: • Find out whether corrupt system files could be causing all your PC problems • Manually replace missing system files using your Windows installation CD • Use System File Checker to repair broken Windows system files • Boost the memory available to Windows File Protection for complete system file protection Missing or corrupt system files can cause many problems when using your PC, from cryptic error messages to mysterious system crashes. If one of the key files needed by Windows has gone missing or become corrupt, you may think that the only way to rectify the situation is to re-install Windows. Fortunately, nothing that drastic is required, as Microsoft have included several tools with Windows that allow you to replace corrupt or missing files with new, fresh copies directly from your Windows installation CD. Now, whenever you find that an important .DLL file has been deleted or copied over, you won’t have to go to the trouble of completely re-installing your system – simply replace the offending file with a new copy. Stefan Johnson: “One missing file can lead to your system becoming unstable and frequently crashing. You may think that the only way to fix the problem is to re-install Windows, but you can easily replace the offending file with a fresh copy from your Windows installation CD.” • Solve errors caused by corrupt system files ................... S 12/2 • How to repair your missing system file errors .............. -

Information Technology Security Policy
BRAIN UK UK Brain Archive Information Network INFORMATION TECHNOLOGY SECURITY POLICY SOP Reference BUK SOP 3 Version number 1.31 Date created 15 April 2015 Date of last review 15 April 2015 Date of next review 15 April 2017 Author: Name Dr Clare Mitchell Signature Authorised by: Name Prof. James A R Nicoll Signature Ref: 14/SC/0098 UK Brain Archive Information Network (BRAIN UK) SOP 3 v1.31 Date: 15 April 2015 - 1 - THIS PAGE IS BLANK Table of Contents Ref: 14/SC/0098 UK Brain Archive Information Network (BRAIN UK) SOP 3 v1.31 Date: 15 April 2015 - 2 - 1. Purpose 5 2. Policy Declaration 2.1 Data Storage 5 2.2 Backup and Recovery Plan 6 2.3 System access and Passwords 6 2.4 Encryption 6 2.5 Data Transfer 7 2.6 Physical Security 7 2.7 Data Quality and Accuracy 2.7.1 Data Entry 7 2.7.2 Data Modification and Deletion 7 2.8 System Specification 8 3. References 8 4. Supporting Documentation 8 Ref: 14/SC/0098 UK Brain Archive Information Network (BRAIN UK) SOP 3 v1.31 Date: 15 April 2015 - 3 - THIS PAGE IS BLANK Ref: 14/SC/0098 UK Brain Archive Information Network (BRAIN UK) SOP 3 v1.31 Date: 15 April 2015 - 4 - 1. Purpose BRAIN UK processes and maintains a large amount of valuable data. This policy aims to protect such data against loss, unauthorised access and modification, inadvertent destruction and to ensure that the integrity and quality of stored data is maintained. The data processed by BRAIN UK falls into one of two distinct categories: 1. -

Installation Tips
Installation Tips Important Please Read Before Going Further! Installation of Kitchen Cabinets is NOT a Do-It-Yourself project for those without extensive experience in finish carpentry. If you are not a professional carpenter please seek help from a trained professional. This guide is meant to be used as a supplement to carpenters who are trained and familiar with cabinetry installa- tion techniques, it is not meant to be a stand alone installation guide. Version 1.0 - 2009 CABINET INSTALLATION TABLE OF CONTENTS Cabinet installation requires special skills and tools. If you are COMMON INSTALLATION TOOLS uncertain of any part of these basic instructions, terms or lack the minimum listed tools, consult with your cabinet supplier For professional results have the tools you need at hand and for recommended professional cabinet installation mechanics. ready. Here’s a tip: save changeover time by having two An error during installation can result in costly repairs and cordless screwguns – one with a drill bit for predrilling screw delays. holes and another with a screw tip. TERMS TO KNOW • Power Drill • Sand Paper • Drill Bits • Block Plane • Terms and Tools Level: A horizontal plane at right angles to the plumb. • Carpenter’s Levels (2’ & 4’) • Clamps • Carpenter’s Square • Caulking Plumb: A true vertical line. If something is “out of plumb” it •Tape Measure (1”x25’) • Chalk Line is not exactly straight up and down. • Step ladder • Mitre Box • Common Construction Details • Nail Set • Marking Tools Square: All lines parallel and at 90° to each other. • Extension Cord(s) • Stud Finder Rail: A horizontal framing member of a cabinet door. -

Software to Extract Cab Files
Software to extract cab files click here to download You can use WinZip to extract CAB files by following the steps listed below. file extension associated with WinZip program, just double-click on the file. PeaZip offers read-only support (open and extract cab files) for Microsoft Cabinet file format, providing a free alternative utility to open (list content) and www.doorway.ru packages, or disassemble single files from the container, under Windows and Linux operating systems. Moreover, the OS can create, extract, or rebuild cab files. This means you do not require any additional third-party software for this task. All CAB. For a number of years, Microsoft has www.doorway.ru files to compress software that was distributed on disks. Originally, these files were used to minimize the number . The InstallShield installer program makes files with the CAB However, you can also open or extract CAB files with a file decompression tool. Open, browse, extract, or view Microsoft CAB files with Altap Salamander File Manager. High quality software with emphasis on error states. Affordable cost: . Microsoft uses cab files to package software programs. You can view the contents of a cab file by unzipping it and extracting its contents to a. Hi, I need some help www.doorway.ru files. I have to extract a patch for one game, so i used universal extractor for to extract www.doorway.ru Now I have to. cab Extension - List of programs that can www.doorway.ru files. www.doorway.ru, Inventoria Stock Manager, NCH Software, Extract with Express Zip, Low. -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

Pagescope Cabinet User Manual
4343-7733-01 User Manual PageScope Cabinet Table of Contents 1 Introduction 1.1 Welcome to Minolta ......................................................................1-1 1.2 Roadmap of this Manual...............................................................1-2 Where to find what in this User's Manual........................................1-2 Brief Explanation of Special Type Styles and Method of Presentation...................................................................1-3 2 About PageScope Cabinet 2.1 Software Features.........................................................................2-1 3 Installation 3.1 System Requirements ..................................................................3-1 3.2 Installing the Software..................................................................3-2 3.3 Uninstalling the Software.............................................................3-4 4First Steps 4.1 Starting and Closing the Application ..........................................4-1 Starting PageScope Cabinet...........................................................4-1 Closing PageScope Cabinet ...........................................................4-2 4.2 Overview of the Main Window .....................................................4-2 4.3 Setting System Environment .......................................................4-3 Open the “SetUp” Dialog.................................................................4-3 System Index card ..........................................................................4-4 Interval -
UC San Diego Policy & Procedure Manual ______
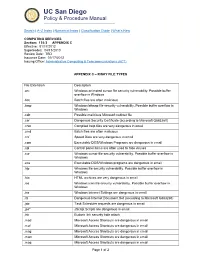
UC San Diego Policy & Procedure Manual _________________________________________________ Search | A–Z Index | Numerical Index | Classification Guide | What’s New COMPUTING SERVICES Section: 135-3 APPENDIX C Effective: 01/17/2012 Supersedes: 04/15/2010 Review Date: TBD Issuance Date: 01/17/2012 Issuing Office: Administrative Computing & Telecommunications (ACT) APPENDIX C – RISKY FILE TYPES File Extension Description .ani Windows animated cursor file security vulnerability. Possible buffer overflow in Windows .bat Batch files are often malicious .bmp Windows bitmap file security vulnerability. Possible buffer overflow in Windows .cab Possible malicious Microsoft cabinet file .cer Dangerous Security Certificate (according to Microsoft Q883260) .chm Complied help files are very dangerous in email .cmd Batch files are often malicious .cnf Speed Dials are very dangerous in email .com Executable DOS/Windows Programs are dangerous in email .cpl Control panel items are often used to hide viruses .cur Windows cursor file security vulnerability. Possible buffer overflow in Windows .exe Executable DOS/Windows programs are dangerous in email .hlp Windows file security vulnerability. Possible buffer overflow in Windows .hta HTML archives are very dangerous in email .ico Windows icon file security vulnerability. Possible buffer overflow in Windows .ins Windows Internet Settings are dangerous in email .its Dangerous Internet Document Set (according to Microsoft Q883260) .job Task Scheduler requests are dangerous in email .jse* JScript Scripts are dangerous -

Diamond Cabinets Installation Guide.Pdf
the helpful guide to cabinet installation table of contents Introduction 2 Tools You’ll Need 3 Step 1 - Preparation 4 Step 2 - Removal 4 Step 3 - Wall Cabinets 4 Step 4 - Make a “Map” 5 Step 5 - Mark for Base 6 Step 6 - Installation of Wall Cabinets 7 Step 7 - Install Base Cabinets 9 Lazy Susan Installation 10 Specialty Cabinets Installation 10 Step 8 - Putting on the Counter Top 11 Step 9 - Door and Drawer Alignment 12 Step 10 - Putting on the Hardware 13 Wood Dust Caution 13 Warped Door Policy 14 Care and Cleaning 15 Trouble Shooting 15 1 This booklet covers the basic guidelines of installation and is a great help when installing yourself. However, you should be aware that each project will have some unique characteristics and no installation guide could cover them all. As the installer, you are fully responsible for your finished product. MasterBrand Cabinets disclaims all responsibility for any damages arising from cabinet installation. In addition, the warranty on your cabinets becomes void if the cabinets are in any way modified, improperly installed or damaged prior or during installation. Thank you for purchasing Diamond Cabinetry! 2 tools you’ll need Figure 1 • Steel tape measure • Stud finder • Carpenter’s level at least 24" in length • Patching plaster and putty knife • Chalk line or string • Small carpenter’s saw • A few cedar shakes, shingles or • Claw hammer other suitable tapered pieces of wood for shims • Assortment of straight blade and Phillips head screwdrivers • Scribing tool and pencil 7 3 • Variable speed drill with /32", /16" 1 and /4" drill bits and screwdriver attachments IMPORTANT • Step ladder Shut off water to the sink and dishwasher. -

Risk Control Bulletin Laptop Computer Security
Risk Control Bulletin Laptop Computer Security RISK CONTROL Laptop Security conducted in 2009 was that the average value of a lost laptop was $49,246. This value is based on seven cost components: replacement Laptop computers are vital tools used by a wide population of cost, detection, forensics, data breach, lost intellectual property technology-industry workers. Since laptop computers and handheld costs, lost productivity and legal, consulting and regulatory expenses. devices are not typically used in a fixed, securable location, additional Occurrence of a data breach represents 80 percent of the cost. measures are needed to protect them. Therefore, it is important to take additional steps to prevent losses • A formal security policy detailing end-user responsibility for related to data breaches associated with the theft of data storage securing these devices and the data they contain is essential. devices and media. Devices should never be left unattended. • Cable locks and docking stations should be used but only when • First, carefully evaluate the need for storage of sensitive information the device is left in a secure location, such as an office, for short on any type of portable device or removable media. In many cases, periods. it will be determined that the need for storing information on these difficult-to-secure devices is not worth the benefit given today’s - These security methods are easily compromised and higher threat environment. security options should be used when leaving a laptop in an office overnight (locked in storage area, file cabinet, etc…) • Where possible, prohibit such storage in an information security policy but also evaluate technical means of preventing this data • Travel procedures should address common high risk situations: leakage—disabling or monitoring usage of USB ports, content - Avoid storage in automobiles. -

Windows Powershell Best Practices Windows Powershell Best Practices
Windows PowerShell Best Practices Windows PowerShell Best Practices Expert recommendations, pragmatically applied Automate system administration using Windows PowerShell best practices—and optimize your operational efficiency. With this About the Author practical guide, Windows PowerShell expert and instructor Ed Ed Wilson, MCSE, CISSP, is a well-known Wilson delivers field-tested tips, real-world examples, and candid scripting expert and author of “Hey Windows Scripting Guy!”—one of the most popular advice culled from administrators across a range of business and blogs on Microsoft TechNet. He’s written technical scenarios. If you’re an IT professional with Windows several books on Windows scripting PowerShell experience, this book is ideal. for Microsoft Press, including Windows PowerShell 2.0 Best Practices and Windows PowerShell Scripting Guide. Discover how to: PowerShell • Use Windows PowerShell to automate Active Directory tasks • Explore available WMI classes and methods with CIM cmdlets • Identify and track scripting opportunities to avoid duplication • Use functions to encapsulate business logic and reuse code • Design your script’s best input method and output destination • Test scripts by checking their syntax and performance • Choose the most suitable method for running remote commands • Manage software services with Desired State Configuration Wilson BEST PRACTICES microsoft.com/mspress ISBN 978-0-7356-6649-8 U.S.A. $59.99 55999 Canada $68.99 [Recommended] 9 780735 666498 Operating Systems/Windows Server Celebrating 30 years! Ed Wilson 666498_Win_PowerShell_Best_Practices.indd 1 4/11/14 10:30 AM Windows PowerShell Best Practices Ed Wilson 666498_book.indb 1 12/20/13 10:50 AM Published with the authorization of Microsoft Corporation by: O’Reilly Media, Inc.