WEBRTC MALVERTISING Fighting a New Form of Obfuscated Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

E Cost of Ad Blocking Pagefair and Adobe 2015 Ad Blocking Report
!e cost of ad blocking PageFair and Adobe 2015 Ad Blocking Report Introduction In the third annual ad blocking report, PageFair, with the help of Adobe, provides updated data on the scale and growth of ad blocking so"ware usage and highlights the global and regional economic impact associated with it. Additionally, this report explores the early indications surrounding the impact of ad blocking within the mobile advertising space and how mobile will change the ad blocking landscape. Table of Contents 3. Key insights 8. Effect of ad blocking by industry 13. A"erword 4. Global ad blocking growth 9. Google Chrome still the main driver of ad 14. Background 5. Usage of ad blocking so"ware in the United block growth 15. Methodology States 10. Mobile is yet to be a factor in ad blocking 16. Tables 6. Usage of ad blocking so"ware in Europe growth 17. Tables 7. !e cost of blocking ads 11. Mobile will facilitate future ad blocking growth 12. Reasons to start using an ad blocker PAGEFAIR AND ADOBE | 2015 Ad Blocking Report 2 Key Insights More consumers block ads, continuing the strong growth rates seen during 2013 and 2014. 41% YoY global growth Q2 2014 - Q2 2015 !e "ndings • Globally, the number of people using ad blocking so"ware grew by 41% year over year. • 16% of the US online population blocked ads during Q2 2015. • Ad block usage in the United States grew 48% during the past year, increasing to 45 million monthly active 45 million users (MAUs) during Q2 2015. Average MAUs in the United • Ad block usage in Europe grew by 35% during the past year, increasing to 77 million monthly active users States Q2 2015 during Q2 2015. -

The Impact of Ad-Blockers on Online Consumer Behavior
Marketing Science Institute Working Paper Series 2021 Report No. 21-119 The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri “The Impact of Ad-blockers on Online Consumer Behavior” © 2021 Vilma Todri MSI Working Papers are Distributed for the benefit of MSI corporate and academic members and the general public. Reports are not to be reproduced or published in any form or by any means, electronic or mechanical, without written permission. Marketing Science Institute Working Paper Series The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri Goizueta Business School, Emory University, Atlanta, GA 30322 [email protected] Digital advertising is on track to become the dominant form of advertising but ad-blocking technologies have recently emerged posing a potential threat to the online advertising ecosystem. A significant and increasing fraction of Internet users has indeed already started employing ad-blockers. However, surprisingly little is known yet about the effects of ad-blockers on consumers. This paper investigates the impact of ad- blockers on online search and purchasing behaviors by empirically analyzing a consumer-level panel dataset. Interestingly, the analyses reveal that ad-blockers have a significant effect on online purchasing behavior: online consumer spending decreases due to ad-blockers by approximately $14:2 billion a year in total. In examining the underlying mechanism of the ad-blocker effects, I find that ad-blockers significantly decrease spending for brands consumers have not experienced before, partially shifting spending towards brands they have experienced in the past. I also find that ad-blockers spur additional unintended consequences as they reduce consumers' search activities across information channels. -

Will Ad Blocking Break the Internet?
NBER WORKING PAPER SERIES WILL AD BLOCKING BREAK THE INTERNET? Ben Shiller Joel Waldfogel Johnny Ryan Working Paper 23058 http://www.nber.org/papers/w23058 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 January 2017 Johnny Ryan is an employee of PageFair, a firm that measures the extent of ad blocking and offers ad-recovery technologies that enable publishers to display ads in a manner that adblockers cannot block. Neither Shiller nor Waldfogel has received any compensation for the research in the paper. PageFair was allowed to review the paper for accuracy but did not have control over the paper's findings nor conclusions. The views expressed herein are those of the authors and do not necessarily reflect the views of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer-reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2017 by Ben Shiller, Joel Waldfogel, and Johnny Ryan. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Will Ad Blocking Break the Internet? Ben Shiller, Joel Waldfogel, and Johnny Ryan NBER Working Paper No. 23058 January 2017 JEL No. L81,L82 ABSTRACT Ad blockers allow Internet users to obtain information without generating ad revenue for site owners; and by 2016 they were used by roughly a quarter of site visitors. Given the ad-supported nature of much of the web, ad blocking poses a threat to site revenue and, if revenue losses undermine investment, a possible threat to consumers' access to appealing content. -

Vidyo® Server for Webrtc Click to Collaborate
Datasheet Vidyo® Server for WebRTC Click to Collaborate The Vidyo Server for WebRTC extends the Vidyo platform to include WebRTC capable browsers. Now join Vidyo conferences right from their web browser without any software installation. With a simple click-to-connect link, participants can enjoy up to HD video quality. The Vidyo Server for WebRTC is fully integrated with the Vidyo platform. This means participants joining through WebRTC can enjoy the interoperability delivered by the Vidyo platform including native Vidyo endpoints as well as third party H.323, SIP, and Microsoft® Skype for Business®. Deployed as a virtual machine, the Vidyo Server for WebRTC can be easily managed and scaled to meet demand. Concurrency is determined by flexible VidyoLine licenses that can float between native Vidyo endpoints and WebRTC clients as needed. Calls are secured through encryption using HTTPS, DTLS, and SRTP. Key Features Incredible User Experience Easy to Deploy & Manage • Native WebRTC support for plug-in free • Virtual server for easy deployment in your videoconferencing data center, colocation facility or in the cloud • Support for non-WebRTC browsers via • Dynamically scalable capacity based on VidyoWeb plug-in provisioned resources • Full two-way video communications on • Spin up new instances of Vidyo Server for ChromeBooks WebRTC to rapidly cluster and add capacity • Multipoint video layouts with up to 6 viewable • Simplify administration, configuration and participants maintenance with web-based interface • Click to connect ease of use • Secured media and signaling encryption • HD quality video and content • Automatic firewall and NAT traversal with ICE, • Share content with other participants* (Only TURN, and STUN support available on Chrome. -

Kandy Link — Webrtc Gateway Using the Web to Extend the Value of Service Provider Networks
Kandy Link — WebRTC Gateway Using the Web to Extend the Value of Service Provider Networks The Impact of WebRTC The adoption of the WebRTC standard by all of the major web browser providers creates an enormous opportunity to change the way people communicate. WebRTC makes it possible to engage in a two-way multi-media conversation (voice, video, screen share) without any extra software or purpose-built devices. Any modern device with a mic and speakers is now a full communications endpoint supporting voice, video and col- laboration tools. The simplicity of WebRTC-based communication access is in sharp contrast to traditional communication tools that require users to load a special app or a plugin for each website or ser- vice they use. This issue has gone from annoying to business impacting as many organizations have heightened security policies that preclude users from adding new applications. And since WebRTC leverages HTML5 and HTTPS, its firewall Multiple Deployment Options Kandy Link is deployed in a subscription based, fully managed friendly, meaning it works almost everywhere. model. Users can choose the operational deployment model Bridging the Digital Divide that best fits their use case: Ribbon’s Kandy Link Gateway offers service providers a simple Public Cloud – as a Service and scalable way to connect different generations of communi- No hardware or capital investment – WebRTC services are cation elements and customer experiences. delivered from the public Kandy cloud with access to Kandy’s entire apps portfolio. • Kandy Link can deliver line or station-side SIP services to existing communication elements (as a service, in network Private Cloud or on-premises) while delivering WebRTC-based services to In network or in a 3rd party data center. -
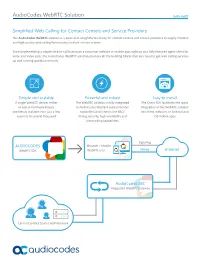
Audiocodes Webrtc Solution DATA SHEET
AudioCodes WebRTC Solution DATA SHEET Simplified Web Calling for Contact Centers and Service Providers The AudioCodes WebRTC solution is a quick and straightforward way for contact centers and service providers to supply intuitive and high-quality web calling functionality to their service centers. From implementing a simple click-to-call button on a consumer website or mobile app, right up to a fully featured agent client for voice and video calls, the AudioCodes WebRTC solution provides all the building blocks that you need to get web calling services up and running quickly and easily. Simple and scalable Powerful and robust Easy to install A single WebRTC device, either The WebRTC solution is fully integrated The Client SDK facilitates the quick virtual or hardware-based, in AudioCodes Mediant session border integration of the WebRTC solution seamlessly scalable from just a few controllers and inherits the SBCs’ into client websites or Android and sessions to several thousand strong security, high availability and iOS mobile apps transcoding capabilities Signaling AUDIOCODES Browser / Mobile WebRTC SDK WebRTC user Media Internet AudioCodes SBC Integrated WebRTC Gateway Carrier/Contact Center VoIP Network AudioCodes WebRTC Solution DATA SHEET Specifications WebRTC Gateway About AudioCodes AudioCodes Ltd. (NasdaqGS: AUDC) is a Deployment leading vendor of advanced voice networking VMWare KVM AWS Mediant 9000 Mediant 4000 method and media processing solutions for the digital workplace. With a commitment to the human 3,000 voice deeply embedded in its DNA, AudioCodes 5,000 WebRTC sessions 2,700 3,500 (20,000 on 1,000 enables enterprises and service providers (20K on roadmap) roadmap) to build and operate all-IP voice networks for unified communications, contact centers 3,000 1,050 integrated and hosted business services. -

Nanostream Webrtc.Live
nanoStream WebRTC.live Product Overview – Document V 1.4, 2017-01 © 2017 nanocosmos gmbh Setup secure online meetings at a distance or stream live events to thousands of worldwide viewers: nanoStream WebRTC.live makes it very easy to create custom live video communication and interactive live streaming applications with low latency. In combination with the nanoStream H5Live Player, nanoStream WebRTC.live offers a seamless user experience for plugin-free live video broadcast on any device. What is nanoStream WebRTC.live? nanoStream WebRTC.live is a product platform developed by nanocosmos based on WebRTC and other streaming technologies like RTMP and H5Live. It is used in a variety of low-latency interactive live streaming use cases. WebRTC.live video chat combined with RTMP broadcasting allows a unified communications strategy for companies - from 1-on-1 discussions with employees at a distance to sharing live events with 10.000 viewers. In addition to secure peer-to-peer communication, the WebRTC.live encoding platform can be used to broadcast live streams to large audiences. The live video broadcast can be integrated into any live streaming infrastructure with the unique WebRTC-RTMP server bridge, or in an end-to-end development with the nanoStream Cloud. What is WebRTC? WebRTC is a technology standard for audio/video-based real time communication. WebRTC video chats and broadcasts function directly within the web browser, with no additional plugin or app download required. The standard is supported by most browser vendors (Google Chrome, Firefox) and currently available plugin-free on all platforms (Windows, MacOS, Android), except Apple iOS. -
Features Guide [email protected] Table of Contents
Features Guide [email protected] Table of Contents About Us .................................................................................. 3 Make Firefox Yours ............................................................... 4 Privacy and Security ...........................................................10 The Web is the Platform ...................................................11 Developer Tools ..................................................................13 2 About Us About Mozilla Mozilla is a global community with a mission to put the power of the Web in people’s hands. As a nonprofit organization, Mozilla has been a pioneer and advocate for the Web for more than 15 years and is focused on creating open standards that enable innovation and advance the Web as a platform for all. We are committed to delivering choice and control in products that people love and can take across multiple platforms and devices. For more information, visit www.mozilla.org. About Firefox Firefox is the trusted Web browser of choice for half a billion people around the world. At Mozilla, we design Firefox for how you use the Web. We make Firefox completely customizable so you can be in control of creating your best Web experience. Firefox has a streamlined and extremely intuitive design to let you focus on any content, app or website - a perfect balance of simplicity and power. Firefox makes it easy to use the Web the way you want and offers leading privacy and security features to help keep you safe and protect your privacy online. Mozilla continues to move the Web forward by pioneering new open source technologies such as asm.js, Emscripten and WebAPIs. Firefox also has a range of amazing built-in developer tools to provide a friction-free environment for building Web apps and Web content. -

A Flexible and Scalable Media Centric Webrtc
An Oracle White Paper May 2014 Towards a Flexible and Scalable Media Centric WebRTC Towards a Flexible and Scalable Media Centric WebRTC Introduction Web Real Time Communications (WebRTC) transforms any device with a browser into a voice, video, and screen sharing endpoint, without the need of downloading, installing, and configuring special applications or browser plug-ins. With the almost ubiquitous presence of browsers, WebRTC promises to broaden the range of communicating devices to include game consoles and set-top boxes in addition to laptops, smartphones, tablets, etc. WebRTC has been described as a transformative technology bridging the worlds of telephony and web. But what does this bridging really imply and have the offerings from vendors fully realized the possibilities that WebRTC promises? In this paper we discuss the importance of WebRTC Service Enablers that help unlock the full potential of WebRTC and the architectures that these elements make possible in this new era of democratization. New Elements in the WebRTC Network Architecture While web-only communications mechanisms would require nothing more than web browsers and web servers, the usefulness of such web-only networks would be limited. Not only is there a need to interwork with existing SIP1 and IMS2 based networks, there is also a need to provide value added services. There are several products in the marketplace that attempt to offer this functionality. But most of the offerings are little more than basic gateways. Such basic gateways perform simple protocol conversions where messages are translated from one domain to another. Such a simplistic gateway would convert call signaling from JSON3, XMPP4, or SIP over WebSockets, to SIP, and might also provide interoperability between media formats. -

A 3D Collaborative Editor Using Webgl and Webrtc
A 3D collaborative editor using WebGL and WebRTC Caroline Desprat Jean-Pierre Jessel Hervé Luga [email protected] [email protected] [email protected] VORTEX team, IRIT UMR5505, University of Toulouse, France Online collaborative 3D design Objectives Collaborative design environments share 3D scenes • pluginless visualization of 3D scenes on the web, across the network. 3D scenes or models are very • exclusive use of client resources for likely to be constructed and reviewed by more than communication, one person, particularly in the context of 3D sci- • message broadcasting: asynchronous and entific visualization [1], CAD (Computer Aided De- granular, sign) [2] or BIM (Building Information Modeling) • real-time collaboration across the network with [3] solutions with various architectures [4] [5]. shared access to 3D models. Question What architecture is the best suited in online 3D collaborative design environments for small teams using exclusively browser’s ressources? Our hybrid architecture for 3D web-based collaboration Web-based editor P2P communication Client visualization, interaction and edition. WebRTC and DataChannels The 3D interface integrates a viewport and pro- vides: WebRTC (Web Real-Time Protocol) allows Da- P2P connections be- • the list of contributors, taChannel protocol for tween web brow-sers to exchange any raw • basic transformations tools (CRUD), data in real-time[6]. • and viewport informations. WebRTC uses signaling mechanism (via WebSocket server) to manage peers, the network configuration and the media capabilities. Server: RESTful architecture Auto-management of the P2P full mesh network of REST architecture (client/server/NoSQL DB users (designed for small teams). queries) benefits distributed hypermedia systems. PeerJS library bootstraps WebRTC API for compat- ibility reasons. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Webrtc the PANACEA for INTUITIVE UBIQUITOUS ONLINE COLLABORATION?
IS WebRTC THE PANACEA FOR INTUITIVE UBIQUITOUS ONLINE COLLABORATION? WebRTC (Web Real Time Communications) is a developing open What is WebRTC? standard for enabling web browsers to support multimedia audio, video chat and other data applications. The WebRTC approach to WebRTC is a standard emerging out of the World Wide Web Consortium online real-time communications aims to remove the hassles and (W3C) and the Internet Engineering Task Force (IETF). This standard issues associated with the current practice of installing vendor-specific holds significant promise as a replacement for the current reliance software plug-ins or browser extensions, and promises to vastly on proprietary browser extensions, troublesome plugin downloads improve the user experience. and for potentially eliminating the need for licensed vendor-supplied soft clients. Interoperability complexities and challenges, as well as costs, are a major obstacle for current vendor solutions. Typically, the end-user WebRTC is about putting real-time communications (RTC) capabilities experience suffers, which has led to low adoption and use in stark into a standard browser, with no download, no plugins and no Flash. contradiction to the web browser-based application market. The standard includes echo-cancellation, packet loss concealment, or all functionality expected in a media stack, prevalent in most IP PBX/UC WebRTC shows promise for not only improving the user experience systems or multimedia endpoints. and adoption of real-time communications, but also for unleashing a new wave of video, voice, and data web applications. The WebRTC standard stipulates a framework for browser-to-browser multimedia communications, independent of platform or operating This paper explores some of the technical components for WebRTC system.