INSECURE-Mag-18.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Security: What You Need to Know
Linux Security: What you need to know Dr. James Stanger Chief Technology Evangelist CompTIA Your presenter . James Stanger, PhD Chief Technology Evangelist - CompTIA Security+, Network+, MCSE, LPI Linux, Symantec STA Responsible for CompTIA’s cerGficaGons and conGnuing educaGon • Security analyGcs • Risk management • PenetraGon tesGng, risk assessment, and intrusion detecon • Linux and open source Twier: @jamesstanger • Network administraGon • VirtualizaGon CompTIA hub: • Web technologies hps://Gnyurl.com/y94u3v7j • CerGficaGon development • Award-winning author and instructor Poll quesGon(s) 1. What animal is the Linux mascot? 2. What is the Linux mascot’s name? 3. How did this mascot get chosen, anyway? Why Linux is important to security? Linux is table stakes for security • You’ll be securing Linux-based systems – Web servers and databases – Cloud and virtualizaon • Nearly 1 in 3 Azure virtual machines are Linux • Majority of cloud services use Linux • You will use a Linux system to perform audits – End points (e.g., IoT, mobile devices, ICS) – Many tools available – Flexibility, scalability, and cost • Used as foundaonal components for major business and security soluGons by companies worldwide Most open source security – Fortune 500 tools are built naGvely in Linux – SMB Plaorms you’ll be asked to secure • Content management systems – Wordpress – SharePoint (has other uses) • Web servers • Databases • Network infrastructure – Firewalls, routers and VPN servers – Edge devices (e.g., micro datacenters) – Mobile – DNS especially • End -

Easybuild Documentation Release 20210907.0
EasyBuild Documentation Release 20210907.0 Ghent University Tue, 07 Sep 2021 08:55:41 Contents 1 What is EasyBuild? 3 2 Concepts and terminology 5 2.1 EasyBuild framework..........................................5 2.2 Easyblocks................................................6 2.3 Toolchains................................................7 2.3.1 system toolchain.......................................7 2.3.2 dummy toolchain (DEPRECATED) ..............................7 2.3.3 Common toolchains.......................................7 2.4 Easyconfig files..............................................7 2.5 Extensions................................................8 3 Typical workflow example: building and installing WRF9 3.1 Searching for available easyconfigs files.................................9 3.2 Getting an overview of planned installations.............................. 10 3.3 Installing a software stack........................................ 11 4 Getting started 13 4.1 Installing EasyBuild........................................... 13 4.1.1 Requirements.......................................... 14 4.1.2 Using pip to Install EasyBuild................................. 14 4.1.3 Installing EasyBuild with EasyBuild.............................. 17 4.1.4 Dependencies.......................................... 19 4.1.5 Sources............................................. 21 4.1.6 In case of installation issues. .................................. 22 4.2 Configuring EasyBuild.......................................... 22 4.2.1 Supported configuration -

Drukkar P66 Android-X86 4.4 RC P67 Hotshots P68 Rcssmin P68 Gipfel P69 Lynx P69 Flpsed P70 Lynis P68 Nightmaretris P70 Zatacka P71
FOSSPICKS Drukkar p66 Android-x86 4.4 RC p67 HotShots p68 rCSSmin p68 Gipfel p69 Lynx p69 Flpsed p70 Lynis p68 NightmareTris p70 Zatacka p71 Sparkling gems and new releases from the world of FOSSpicks Free and Open Source Software Mike Saunders has spent a decade mining the internet for open source treasures. Here’s the result of his latest haul… Lightweight blog platform Drukkar 2.0 http://drukkar.sourceforge.net ituation: you want to set up entries as simple XML files, and is your own blog. Options: a designed with minimum bandwidth Smillion and one competing overheads, so the “content should blog platforms, each one trying to account for most of your web be more feature-rich, flashy and traffic” as the developer puts it. Web 4.0 than the last. End result: you get tired of trying to work out Nice and simple what’s right for you, give up, and go To install Drukkar, extract its .zip to the pub instead. file directly into a location on your Sounds familiar? Most of us web server (note that it won’t create don’t need whizz-bang WordPress a subdirectory during extraction). installations with all the trimmings Then edit config.xml and set for our day-to-day musings, and the base_url and base_location Drukkar does a splendid job with settings to match your installation minimal requirements. It doesn’t path. Finally, make sure that the need a database or special Apache entries, files and cache directories Drukkar’s default theme, “flat”, is clean and simple. To change the modules or anything like that – its are writable by your web server text on the right, edit inc/sidebar.php. -

Hey Lynis, Audit This by Russ Mcree – ISSA Senior Member, Puget Sound (Seattle), USA Chapter
toolsmith Hey Lynis, Audit This By Russ McRee – ISSA Senior Member, Puget Sound (Seattle), USA Chapter Prerequisites/dependencies solution will include the existing Lynis Unix/Linux operating systems client that we’ll cover here, a management and reporting interface, as well as related plugins. Michael says they’re making great progress and each appy Holidays to all readers, the ISSA community, day brings them closer to an official first version. Specific to and infosec tool users everywhere. As part of De- the plugins, while a work in progress, they create specialized cember’s editorial theme for the ISSA Journal, Di- hooks via the client. As an example, imagine heuristics scan- Hsaster Recovery/Disaster Planning, I thought I’d try to con- ning with correlation at the central node to detect security in- nect tooling and tactics to said theme. I’m going to try and do trusions. Compliance checking for the likes of Basel II, GLBA, this more often so you don’t end up with a web application HIPAA, PCI DSS, and SOX is another likely plugin candidate. hacking tool as part of the forensics and analysis issue. I can The short-term road map consists of finishing the web inter- hear Thom (editor) and Joel (editorial advisory board chair) face, followed by the presenting and supporting documents. now: “Congratulations Russ, it only took you seven years to This will include documentation, checklists, control over- catch up with everyone else, you stubborn git.” views, and materials for system administrators, security pro- Better late than never I always say, so back to it. -

2.6 Auditing Linux/Unix Systems
Processing engine for security health checks Christofer Huynh, Jesper Gustafsson Department of Computer Science © Christofer Huynh, Jesper Gustafsson. LTH School of Engineering Lund University Box 882 SE-251 08 Helsingborg Sweden LTH Ingenjörshögskolan vid Campus Helsingborg Lunds universitet Box 882 251 08 Helsingborg Printed in Sweden. Lunds University Lund 2017 Abstract Computer security is still an often neglected field even though the IT industry is huge and still growing. Making sure that systems are secure is something that is very important but can take a lot of man hours. This thesis contains the research and documentation for an auditing tool created on behalf of a company that specialises in computer security, TrueSec. The audit tool uses the log files that are built from the scripts that TrueSec uses to runs various unix commands as a base, but it has been designed in such a way to allow the addition of other types of logs. The tool was designed with future development in mind. It uses configuration files that are seperated from the code itself to declare rules which the log files are checked against, allowing the tool to evolve with time by adding new rules. At the request of TrueSec a simple web service as a proof of concept for an online service with an authentication model with log in and user roles for uploading log files and storing the output from the audit tool was also developed. Keywords: audit tool, computer security, security audit, analysis engine, security health check 3 Sammanfattning Datasäkerhet är fotfarande ofta ett misskött fält även fast IT- sektorn är stor och fortfarande växer. -

Lynis Enterprise on the Other Hand Has Much More Possibilities to Display Data, Including Extended Reports in Several Formats
Lynis Lynis Installation and Usage • Introduction • Installation • Using Lynis • Basics • Commands, Options, and Arguments • Suggestions and Warnings • Behind the scenes • Profiles • HostIDs Introduction Lynis is an open source security tool. It helps with auditing systems running UNIX-alike systems (Linux, macOS, BSD), and providing guidance for system hardening and compliance testing. This document contains the basics to use the software. Installation The installation of Lynis is explained in the Get Started guide. Using Lynis Basics By running 'lynis' the program is started and will provide the basic parameters available. If you manually extracted Lynis (or used Git), then use './lynis' to start the program from the local directory. The most common command to start Lynis is using audit system command. This still start the security scan. To run Lynis you should meet one requirement: have write access to /tmp (temporary files) Commands, Options, and Arguments Introduction The behavior of programs can influenced with commands, arguments, and options. These terms are often mixed up, so we start with a quick introduction. Commands tell the program what to do. An option tells the program how to do it. If an argument is used, it tell on what it applies. Arguments usually follow an option, like a filename, or a target. Example $ ./lynis audit system --quick --auditor "The Auditor" In this example we tell Lynis to audit (command), with the target system (argument). By using the --quick (option), we tell it not to wait. We used --auditor (option) and defined it as "The Auditor" (argument). Lynis Commands The Lynis tool requires a minimum amount of parameters to run. -

Software Package Licenses
DAVIX 1.0.0 Licenses Package Version Platform License Type Package Origin Operating System SLAX 6.0.4 Linux GPLv2 SLAX component DAVIX 0.x.x Linux GPLv2 - DAVIX Manual 0.x.x PDF GNU FDLv1.2 - Standard Packages Font Adobe 100 dpi 1.0.0 X Adobe license: redistribution possible. Slackware Font Misc Misc 1.0.0 X Public domain Slackware Firefox 2.0.0.16 C Mozilla Public License (MPL), chapter 3.6 and Slackware 3.7 Apache httpd 2.2.8 C Apache License 2.0 Slackware apr 1.2.8 C Apache License 2.0 Slackware apr-util 1.2.8 C Apache License 2.0 Slackware MySQL Client & Server 5.0.37 C GPLv2 Slackware Wireshark 1.0.2 C GPLv2, pidl util GPLv3 Built from source KRB5 N/A C Several licenses: redistribution permitted dropline GNOME: Copied single libraries libgcrypt 1.2.4 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries gnutls 1.6.2 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries libgpg-error 1.5 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries Perl 5.8.8 C, Perl GPL or Artistic License SLAX component Python 2.5.1 C, PythonPython License (GPL compatible) Slackware Ruby 1.8.6 C, Ruby GPL or Ruby License Slackware tcpdump 3.9.7 C BSD License SLAX component libpcap 0.9.7 C BSD License SLAX component telnet 0.17 C BSD License Slackware socat 1.6.0.0 C GPLv2 Built from source netcat 1.10 C Free giveaway with no restrictions Slackware GNU Awk 3.1.5 C GPLv2 SLAX component GNU grep / egrep 2.5 C GPLv2 SLAX component geoip 1.4.4 C LGPL 2.1 Built from source Geo::IPfree 0.2 Perl This program is free software; you can Built from source redistribute it and/or modify it under the same terms as Perl itself. -

Hardening Freebsd: an Approach to a Secure System Remy
Hardening FreeBSD: An Approach to a Secure System Remy Baumgarten University of Hawaii [email protected] October 4th, 2009 Hardening FreeBSD 知己知彼 百戰不殆 If you know both yourself and your enemy, you can win a hundred battles without a single loss. Sun Tzu's The Art of War “Operating System are not broken into; the programs running on the operating system are.” -Micheal W. Lucas General Summary: Hardware and Software Specifications Foreword and Forewarn Who are our Adversaries? Updating and Package Auditing Mailing Lists Permissions Networking and Firewalls Kernel Security Remote Logging Command Logging Secure Remote Access with SOCKS Proxy Forwarding Web Browsing Encryption Auditing Further Reading Hardware Specifications: Intel Core i7 920 Nehalem 2.66GHz 4 x 256KB L2 Cache 8MB L3 Cache LGA 1366 130W Quad-Core Processor ASUS P6T6 WS Revolution LGA 1366 Intel X58 ATX Intel Motherboard CORSAIR XMS3 6GB (3 x 2GB) 240-Pin DDR3 SDRAM DDR3 1333 (PC3 10666) Triple Channel CORSAIR CMPSU-850TX 850W ATX12V 2.2 / EPS12V 2.91 SLI Ready CrossFire Ready Active PFC Power Supply 2x - EVGA 896-P3-1260-TR GeForce GTX 260 896MB 448-bit GDDR3 PCI Express 2.0 x16 HDCP Ready SLI Supported Video Card LG W2452T-TF Black 24" 2ms(GTG) Widescreen LCD Monitor 400 cd/m2 10000:1 DCR with HDCP support LG Black 22X (CAV) DVD+R 8X DVD+RW 16X DVD+R DL 22X (CAV) DVD-R 6X DVD-RW 12X DVD-RAM 16X DVD-ROM 48X CD-R 32X CD-RW 48X CD-ROM 2MB Cache SATA 22X DVD¬±R DVD Burner Antec Nine Hundred Black Steel ATX Mid Tower Computer Case Software Specifications: FreeBSD 7.3 AMD64 Minimal Customized Compiled Kernel Installed Packages of Relevance: tripwire-2.4.1.2 lynis-1.2.6 snort-2.8.4.1_1 john-1.7.2_1 scponly-4.8 munin-main-1.2.6 postfix-2.6.5,1 mysql-server-5.0.86 portupgrade-2.4.6_3,2 portaudit-0.5.13 netcat-1.10_2 nmap-5.00 oinkmaster-2.0_1 Foreword and Forewarn: Security tips are mostly useless unless one understands why and how that tip works with other practices to protect your system from attacks. -

Akraino Release 3: Proposal for Mandatory Tests
Akraino Release 3: Proposal for Mandatory Tests March 12, 2020 Introduction › The Akraino TSC has discussed the Release 3 requirements in the face-to-face meeting (see the following two slides) › This presentation is a proposal for the mandatory tests in Release 3 › Again, the tests are mandatory only as relevant 2 3 4 Proposal For Incubation projects (that For Mature projects additionally: have been in R1 and R2): › HA tests: etcd_ha, ha/*, › Redfish ceph_service › Kubernetes Conformance › 1.17 › Lynis › Vuls › Kubehunter 5 Open questions › Do we still need the OpenStack tests? › What to do with Linux Testing Project? › Is Kubernetes Conformance 1.17 ok for all? › What to do with the results of Lynis/Vuls/Kubehunter? 6 Summary › Docker › K8s › Networking › Docker Bench for Security › Conformance › Helloworld › Hardware › Etcd_ha › OpenStack › Bios_version › HA › Ceph_service › Hp_baremetal › Ha_calico_dns_proxy › Tempest › Redfish › Ha_etcd_api_ctl_sch › Os › Helm › Ha_services › Cyclictest › Helm_chart › Ha_worker › Ltp (Linux Testing Project) › Helm_repository › Kube-hunter › Lynis › Vuls 7 Docker Bench for Security › https://github.com/docker/d ocker-bench-security › “The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production” 8 Redfish › https://github.com/DMTF/Redfish-Usecase-Checkers › “collection of python3 tools to exercise and validate common use cases for Redfish” › https://github.com/DMTF/Redfish-Test-Framework › “a python3 tool and a model for -
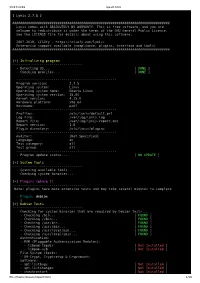
Lynis Report of Ubuntu 18.04
10/17/2019 report.html [ Lynis 2.7.5 ] ################################################################################ Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under the terms of the GNU General Public License. See the LICENSE file for details about using this software. 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ################################################################################ [+] Initializing program ------------------------------------ - Detecting OS... [ DONE ] - Checking profiles... [ DONE ] --------------------------------------------------- Program version: 2.7.5 Operating system: Linux Operating system name: Ubuntu Linux Operating system version: 18.04 Kernel version: 4.15.0 Hardware platform: x86_64 Hostname: pc07 --------------------------------------------------- Profiles: /etc/lynis/default.prf Log file: /var/log/lynis.log Report file: /var/log/lynis-report.dat Report version: 1.0 Plugin directory: /etc/lynis/plugins --------------------------------------------------- Auditor: [Not Specified] Language: en Test category: all Test group: all --------------------------------------------------- - Program update status... [ NO UPDATE ] [+] System Tools ------------------------------------ - Scanning available tools... - Checking system binaries... [+] Plugins (phase 1) ------------------------------------ Note: plugins have more extensive tests and may take several minutes to complete -

Geek Guide > Self-Audit
GEEK GUIDE SELF-AUDIT: CHECKING ASSUMPTIONS AT THE DOOR Table of Contents About the Sponsor .......................................................... 4 Introduction .................................................................... 5 Two Steps Necessary for Security ................................. 7 Verify Configurations ...................................................... 9 Assume Security Has Been Compromised .................. 10 Tools to Scan for Malware ............................................ 11 rkhunter �������������������������������������������������������������������������������������������������12 chkrootkit ����������������������������������������������������������������������������������������������13 LMD�������������������������������������������������������������������������������������������������������14 lynis �������������������������������������������������������������������������������������������������������19 Checking for Stealth Ports ........................................... 22 lsof ��������������������������������������������������������������������������������������������������������23 unhide ���������������������������������������������������������������������������������������������������24 Rootkits ......................................................................... 25 Conclusion .................................................................... 27 GREG BLEDSOE is VP of Operations at Personal, Inc. (http://www.personal.com). He is CEH and CPT certified and has 20 years of hard-fought experience -

Nutzerhandbuch Für Den Dienst „LSDF Online Storage“ Am SCC/KIT
Nutzerhandbuch für den Dienst „LSDF Online Storage“ am SCC/KIT Steinbuch Centre for Computing, KIT Version 2.0, 10. Oktober 2019 Einleitung 1 1 Einleitung ..................................................................................................................................... 3 2 Registrierung ............................................................................................................................... 3 3 Abbestellung ................................................................................................................................ 6 4 Snapshots und Versionierung...................................................................................................... 7 5 Backup ......................................................................................................................................... 7 6 Verzeichnisstruktur ..................................................................................................................... 7 7 Zugangsprotokolle ....................................................................................................................... 9 7.1 Übersicht über die verfügbaren Protokolle......................................................................... 9 7.2 Zugriff über Network File System (NFS) .............................................................................. 9 7.3 Zugriff über Common Internet File System (CIFS) ............................................................... 9 7.3.1 UNIX/Linux Client .....................................................................................................