An Automated Approach to the Collatz Conjecture (Explorations with Rewriting Systems, Matrix Interpretations, and SAT)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Collatz Sequences in the Light of Graph Theory
Wirtschafts- und Sozialwissenschaftliche Fakultät Eldar Sultanow | Christian Koch | Sean Cox Collatz Sequences in the Light of Graph Theory Preprint published at the Institutional Repository of the Potsdam University: https://doi.org/10.25932/publishup-43008 https://nbn-resolving.org/urn:nbn:de:kobv:517-opus4-430089 Contents 1 Introduction ......................................................... 3 1.1 Motivation 3 1.2 Related Research 3 2 The Collatz Tree ..................................................... 6 2.1 The Connection between Groups and Graphs 6 2.2 Defining the Tree 7 2.3 Relationship of successive nodes in HC 9 3 Conclusion and Outlook .............................................12 3.1 Summary 12 3.2 Further Research 12 Literature ..........................................................13 1 2 1. IntroductionIntroductionIntrIntroductionIntroductionoduction It is well known that the inverted Collatz sequence can be represented as a graph or a tree. Similarly, it is acknowledged that in order to prove the Collatz conjecture, that one needs to show that this tree covers all (odd) natural numbers. A structured reachability analysis is hitherto not available. This paper does not claim to solve this million dollar problem. Rather, the objective is to investigate the problem from a graph theory perspective. We first define a tree that consists of nodes labeled with Collatz sequence numbers. This tree will then be transformed into a sub-tree that only contains odd labeled nodes. Finally, we provide relationships between successive nodes. 1.1 Motivation The Collatz conjecture is a number theoretical problem, which has puzzled countless re- searchers using myriad approaches. Presently, there are scarcely any methodologies to de- scribe and treat the problem from the perspective of the Algebraic Theory of Automata. -
![Arxiv:2104.10713V3 [Math.NT] 14 Jun 2021 Fact, Paul Erd˝Oshas Claimed That “Mathematics May Not Be Ready for Such Problems” [2]](https://docslib.b-cdn.net/cover/7608/arxiv-2104-10713v3-math-nt-14-jun-2021-fact-paul-erd-oshas-claimed-that-mathematics-may-not-be-ready-for-such-problems-2-417608.webp)
Arxiv:2104.10713V3 [Math.NT] 14 Jun 2021 Fact, Paul Erd˝Oshas Claimed That “Mathematics May Not Be Ready for Such Problems” [2]
Novel Theorems and Algorithms Relating to the Collatz Conjecture Michael R. Schwob1, Peter Shiue2, and Rama Venkat3 1Department of Statistics and Data Sciences, University of Texas at Austin, Austin, TX, 78712 , [email protected] 2Department of Mathematical Sciences, University of Nevada, Las Vegas, Las Vegas, NV, 89154 , [email protected] 3Howard R. Hughes College of Engineering, University of Nevada, Las Vegas, Las Vegas, NV, 89154 , [email protected] Abstract Proposed in 1937, the Collatz conjecture has remained in the spot- light for mathematicians and computer scientists alike due to its simple proposal, yet intractable proof. In this paper, we propose several novel theorems, corollaries, and algorithms that explore relationships and prop- erties between the natural numbers, their peak values, and the conjecture. These contributions primarily analyze the number of Collatz iterations it takes for a given integer to reach 1 or a number less than itself, or the relationship between a starting number and its peak value. Keywords| Collatz conjecture, 3x+1 problem, geometric series, iterations, algo- rithms, peak values 2010 Mathematics Subject Classification| 11B75,11B83,68R01,68R05 1 Introduction In 1937, the German mathematician Lothar Collatz proposed a conjecture that states the following sequence will always reach 1, regardless of the given positive integer n: if the previous term in the sequence is even, the next term is half of the previous term; if the previous term in the sequence is odd, the next term is 3 times the previous term plus 1 [1]. This conjecture is considered impossible to prove given modern mathematics. In arXiv:2104.10713v3 [math.NT] 14 Jun 2021 fact, Paul Erd}oshas claimed that \mathematics may not be ready for such problems" [2]. -

The 3X + 1 Problem: an Annotated Bibliography
The 3x +1 Problem: An Annotated Bibliography (1963–1999) (Sorted by Author) Jeffrey C. Lagarias Department of Mathematics University of Michigan Ann Arbor, MI 48109–1109 [email protected] (January 1, 2011 version) ABSTRACT. The 3x + 1 problem concerns iteration of the map T : Z Z given by → 3x + 1 if x 1 (mod 2) . 2 ≡ T (x)= x if x 0 (mod 2) . 2 ≡ The 3x + 1 Conjecture asserts that each m 1 has some iterate T (k)(m) = 1. This is an ≥ annotated bibliography of work done on the 3x + 1 problem and related problems from 1963 through 1999. At present the 3x + 1 Conjecture remains unsolved. This version of the 3x + 1 bibliography sorts the papers alphabetically by the first author’s surname. A different version of this bibliography appears in the recent book: The Ultimate Challenge: The 3x + 1 Problem, Amer. Math. Soc, Providence, RI 2010. In it the papers are sorted by decade (1960-1969), (1970-1979), (1980-1989), (1990-1999). 1. Introduction The 3x + 1 problem is most simply stated in terms of the Collatz function C(x) defined on integers as “multiply by three and add one” for odd integers and “divide by two” for even integers. That is, arXiv:math/0309224v13 [math.NT] 11 Jan 2011 3x +1 if x 1 (mod 2) , ≡ C(x)= x if x 0 (mod 2) , 2 ≡ The 3x + 1 problem, or Collatz problem , is to prove that starting from any positive integer, some iterate of this function takes the value 1. Much work on the problem is stated in terms of the 3x + 1 function 3x + 1 if x 1 (mod 2) 2 ≡ T (x)= x if x 0 (mod 2) . -

A Clustering Perspective of the Collatz Conjecture
mathematics Article A Clustering Perspective of the Collatz Conjecture José A. Tenreiro Machado 1,*,† , Alexandra Galhano 1,† and Daniel Cao Labora 2,† 1 Institute of Engineering, Polytechnic of Porto, Rua Dr. António Bernardino de Almeida, 431, 4249-015 Porto, Portugal; [email protected] 2 Department of Statistics, Mathematical Analysis and Optimization, Faculty of Mathematics, Institute of Mathematics (IMAT), Universidade de Santiago de Compostela (USC), Rúa Lope Gómez de Marzoa s/n, 15782 Santiago de Compostela, Spain; [email protected] * Correspondence: [email protected]; Tel.: +351-228340500 † These authors contributed equally to this work. Abstract: This manuscript focuses on one of the most famous open problems in mathematics, namely the Collatz conjecture. The first part of the paper is devoted to describe the problem, providing a historical introduction to it, as well as giving some intuitive arguments of why is it hard from the mathematical point of view. The second part is dedicated to the visualization of behaviors of the Collatz iteration function and the analysis of the results. Keywords: multidimensional scaling; Collatz conjecture; clustering methods MSC: 26A18; 37P99 1. Introduction The Collatz problem is one of the most famous unsolved issues in mathematics. Possibly, this interest is related to the fact that the question is very easy to state, but very hard to solve. In fact, it is even complicated to give partial answers. The problem addresses the following situation. Citation: Machado, J.A.T.; Galhano, Consider an iterative method over the set of positive integers N defined in the follow- A.; Cao Labora, D. A Clustering ing way. -
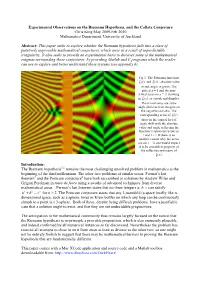
Experimental Observations on the Riemann Hypothesis, and the Collatz Conjecture Chris King May 2009-Feb 2010 Mathematics Department, University of Auckland
Experimental Observations on the Riemann Hypothesis, and the Collatz Conjecture Chris King May 2009-Feb 2010 Mathematics Department, University of Auckland Abstract: This paper seeks to explore whether the Riemann hypothesis falls into a class of putatively unprovable mathematical conjectures, which arise as a result of unpredictable irregularity. It also seeks to provide an experimental basis to discover some of the mathematical enigmas surrounding these conjectures, by providing Matlab and C programs which the reader can use to explore and better understand these systems (see appendix 6). Fig 1: The Riemann functions (z) and (z) : absolute value in red, angle in green. The pole at z = 1 and the non- trivial zeros on x = showing in (z) as a peak and dimples. The trivial zeros are at the angle shifts at even integers on the negative real axis. The corresponding zeros of (z) show in the central foci of angle shift with the absolute value and angle reflecting the function’s symmetry between z and 1 - z. If there is an analytic reason why the zeros are on x = one would expect it to be a manifest property of the reflective symmetry of (z) . Introduction: The Riemann hypothesis1,2 remains the most challenging unsolved problem in mathematics at the beginning of the third millennium. The other two problems of similar status, Fermat’s last theorem3 and the Poincare conjecture4 have both succumbed to solutions by Andrew Wiles and Grigori Perelman in tours de force using a swathe of advanced techniques from diverse mathematical areas. Fermat’s last theorem states that no three integers a, b, c can satisfy an + bn = cn for n > 2. -

Walking Cautiously Into the Collatz Wilderness: Algorithmically, Number Theoretically, Randomly
Walking Cautiously into the Collatz Wilderness : Algorithmically, Number-Theoretically, Randomly Edward G. Belaga, Maurice Mignotte To cite this version: Edward G. Belaga, Maurice Mignotte. Walking Cautiously into the Collatz Wilderness : Algorithmi- cally, Number-Theoretically, Randomly. 2006. hal-00129726 HAL Id: hal-00129726 https://hal.archives-ouvertes.fr/hal-00129726 Preprint submitted on 8 Feb 2007 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. !"#$%&'& ()'*&+)'"$# ),- .*&/%&'"$)0 1/+23'&% 4$"&,$& !"#$% &'() !"#$%&'* +, -./ 01-.'23* 454 !"#$%&' (")*%+),#- .&*+ */0 (+##"*1 !%#203&0,,4 5#'+3%*/6%7"##-8 9)6:03 ;/0+30*%7"##-8 <"&2+6#- 678027 9) :/(0;0!! 0<7 "012=>/ "=;<'--/"" ! 5,#'"'3' -& 6&$*&%$*& ()'*&7+)'"83& 9:),$&7& -& 4'%)#;/3%<= > %3& 6&,&7 !&#$)%'&#= ?@A>BCD 4'%)#;/3%< 1&-&E= ?69F1G " !&72)%'&+&,' -& ()'*&7+)'"83&= H,":&%#"'&7 I/3"# J)#'&3%= > %3& 6&,&7 !&#$)%'&#= ?@A>BCD 4'%)#;/3%< 1&-&E= ?69F1G :1=(7=<; '< -./'2/-=>0( =<3=;.-3 0<7 2=>. /?@/2=A/<-0( 70-0 'B '12 @2/@2=<-3* 8/ @2/3/<- ./2/ </8 -./'2/-=>0( 0<7 /?@/2=A/<-0( 2/31(-3 =< -.2// -

Degree in Mathematics
Degree in Mathematics Title: An algebraic fractal approach to Collatz Conjecture Author: Víctor Martín Chabrera Advisor: Oriol Serra Albó Department: Mathematics Academic year: 2018-2019 Universitat Polit`ecnicade Catalunya Facultat de Matem`atiquesi Estad´ıstica Degree in Mathematics Bachelor's Degree Thesis An algebraic fractal approach to Collatz conjecture V´ıctor Mart´ın Supervised by Oriol Serra Alb´o May, 2019 { Doncs el TFG el faig sobre la Conjectura de Collatz. { Ah, pero` no era alcaldessa? CONVERSA REAL Abstract The Collatz conjecture is one of the most easy-to-state unsolved problems in Mathematics today. It states n that after a finite number of iterations of the Collatz function, defined by C(n) = 2 if n is even, and by C(n) = 3n + 1 if n is odd, one always gets to 1 with independence of the initial positive integer value. In this work, we give an equivalent formulation of the weak Collatz conjecture (which states that all cycles in any sequence obtained by iterating this function are trivial), based on another equivalent formulation made by B¨ohmand Sontacchi in 1978. To such purpose, we introduce the notion of algebraic fractals, integer fractals and boolean fractals, with a special emphasis in their self-similar particular case, which may allow us to rethink some fractals as a relation of generating functions. Keywords Collatz Conjecture, Generating Functions, Fractals, Algebraic Fractals 1 Contents 1 Introduction 3 1.1 Motivation...........................................3 1.1.1 Personal motivation..................................3 1.2 Structure............................................4 1.3 Acknowledgements......................................5 2 Preliminaries 6 2.1 The Collatz function......................................6 2.2 Current status.........................................8 3 Powers of 2 and powers of 3 10 3.1 Towers of Hanoi....................................... -

Convergence Verification of the Collatz Problem
The Journal of Supercomputing manuscript No. (will be inserted by the editor) Convergence verification of the Collatz problem David Barina Received: date / Accepted: date Abstract This article presents a new algorithmic approach for computational convergence verification of the Collatz problem. The main contribution of the paper is the replacement of huge precomputed tables containing O(2N ) entries with small look-up tables comprising just O(N) elements. Our single-threaded CPU implementation can verify 4:2 × 109 128-bit numbers per second on Intel Xeon Gold 5218 CPU computer and our parallel OpenCL implementation reaches the speed of 2:2×1011 128-bit numbers per second on NVIDIA GeForce RTX 2080. Besides the convergence verification, our program also checks for path records during the convergence test. Keywords Collatz conjecture · Software optimization · Parallel computing · Number theory 1 Introduction One of the most famous problems in mathematics that remains unsolved is the Collatz conjecture, which asserts that, for arbitrary positive integer n, a sequence defined by repeatedly applying the function C(n) = 3n+1 if n is odd, or C(n) = n=2 if n is even will always converge to the cycle passing through the number 1. The terms of such sequence typically rise and fall repeatedly, oscillate wildly, and grow at a dizzying pace. The conjecture has never been proven. There is however experimental evidence and heuristic arguments that support it. As of 2020, the conjecture has been checked by computer for all starting values up to 1020 [1]. There is also an extensive literature, [2, 3], on this question. -

Collatz Conjecture
Collatz conjecture by Mikolaj Twar´og April 2020 by Miko laj Twar´og Collatz conjecture April 2020 1 / 22 Many mathematicians tried solving it. Soviet conspiracy aimed to slow down mathematical progress? History Proposed by Lothar Collatz in 1937. by Miko laj Twar´og Collatz conjecture April 2020 2 / 22 Soviet conspiracy aimed to slow down mathematical progress? History Proposed by Lothar Collatz in 1937. Many mathematicians tried solving it. by Miko laj Twar´og Collatz conjecture April 2020 2 / 22 History Proposed by Lothar Collatz in 1937. Many mathematicians tried solving it. Soviet conspiracy aimed to slow down mathematical progress? by Miko laj Twar´og Collatz conjecture April 2020 2 / 22 Paul Erd¨os Introduction \Mathematics is not yet ready for such problems" by Miko laj Twar´og Collatz conjecture April 2020 3 / 22 Introduction \Mathematics is not yet ready for such problems" Paul Erd¨os by Miko laj Twar´og Collatz conjecture April 2020 3 / 22 Collatz conjecture For every n 2 N we eventually reach 1 by repeatedly applying Col to n. Statement Col function ( 3n + 1; for 2 - n Col(n) = n 2; for 2 j n by Miko laj Twar´og Collatz conjecture April 2020 4 / 22 Statement Col function ( 3n + 1; for 2 - n Col(n) = n 2; for 2 j n Collatz conjecture For every n 2 N we eventually reach 1 by repeatedly applying Col to n. by Miko laj Twar´og Collatz conjecture April 2020 4 / 22 For n = 27 we get a sequence consisting of 111 numbers and biggest number 9232. -

The Collatz Problem and Its Generalizations: Experimental Data
The Collatz Problem and Its Generalizations: Experimental Data. Table 1. Primitive Cycles of (3n + d)−mappings. Edward G. Belaga, Maurice Mignotte To cite this version: Edward G. Belaga, Maurice Mignotte. The Collatz Problem and Its Generalizations: Experimental Data. Table 1. Primitive Cycles of (3n + d)−mappings.. 2006. hal-00129727 HAL Id: hal-00129727 https://hal.archives-ouvertes.fr/hal-00129727 Preprint submitted on 8 Feb 2007 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. The Collatz Problem and Its Generalizations: Experimental Data. Table 1. Primitive Cycles of (3n + d) mappings. − Edward G. Belaga Maurice Mignotte [email protected] [email protected] Universit´e Louis Pasteur 7, rue Ren´e Descartes, F-67084 Strasbourg Cedex, FRANCE Abstract. We study here experimentally, with the purpose to calculate and display the detailed tables of cyclic structures of dynamical systems d generated by iterations of the functions T acting, for all d 1 relatively prime to 6, onDpositive integers : d ≥ n , if n is even; T : N N; T (n) = 2 d −→ d 3n+d , if n is odd. ! 2 In the case d = 1, the properties of the system = 1 are the subject of the well-known Collatz, or 3n + 1 conjecture. -

New Lower Bound on Cycle Length for the 3N + 1 Problem
New Lower Bound on Cycle Length for the 3n + 1 Problem T. Ian Martiny Department of Mathematics University of Pittsburgh Pittsburgh, PA 15260 [email protected] April 9, 2015 Collatz Function Definition The function T : N ! N is given by 8n > if n is even <2 T (n) = 3n + 1 > if n is odd : 2 I. Martiny (Pitt) Collatz conjecture lower bound April 9, 2015 2 / 20 Brief History This problem is generally credited to Lother Collatz (hence the common name Collatz Problem). Having distributed the problem during the International Congress of Mathematicians in Cambridge. Helmut Hasse is often attributed with this problem as well, and sometimes the iteration is referred to by the name Hasse's algorithm. Another common name is the Syracuse problem. Other names associated with the problem are S. Ulam, H. S. M. Coxeter, John Conway, and Sir Bryan Thwaites. I. Martiny (Pitt) Collatz conjecture lower bound April 9, 2015 3 / 20 Behavior of function We can look at how the function behaves at certain values: T (5) = 8; T (12) = 6; T (49) = 74 or more interestingly we can look at the sequence of iterates of the function: T (k)(n): (12; 6; 3; 5; 8; 4; 2; 1; 2; 1;:::) (3; 5; 16; 8; 4; 2; 1; 2; 1;:::) (17; 26; 13; 20; 10; 5; 8; 4; 2; 1;:::) (256; 128; 64; 32; 16; 8; 4; 2; 1;:::) I. Martiny (Pitt) Collatz conjecture lower bound April 9, 2015 4 / 20 3n + 1 problem 3n + 1 problem Prove (or find a counter example) that every positive integer, n, eventually reaches the number 1, under iterations of the function T (n). -

The Proof of Collatz Conjecture
The Proof of Collatz Conjecture Hongyuan Ye ( [email protected] ) Zhejiang Bitmap Intelligent Technology Co., Ltd. Jiaxing, Zhejiang 314100 China M.E. Pattern Recognition and Intelligent Control Research Article Keywords: Collatz conjecture, Collatz transform, Collatz even transform, Collatz odd transform, Collatz transform result sequence, Collatz transform times, Strong Collatz conjecture, Strong Collatz transform times, Non-negative integer inheritance decimal tree, Clone node, Collatz-leaf node, Collatz-leaf integer, Collatz-leaf node inheritance. Posted Date: May 22nd, 2020 DOI: https://doi.org/10.21203/rs.3.rs-30443/v1 License: This work is licensed under a Creative Commons Attribution 4.0 International License. Read Full License The Proof of Collatz Conjecture Hongyuan Ye* [Abstract] This paper redefines Collatz conjecture, and proposes strong Collatz conjecture, the strong Collatz conjecture is a sufficient condition for the Collatz conjecture. Based on the computer data structure–tree, we construct the non-negative integer inheritance decimal tree. The nodes on the decimal tree correspond to non-negative integers. We further define the Collatz-leaf node (corresponding to the Collatz-leaf integer) on the decimal tree. The Collatz- leaf nodes satisfy strong Collatz conjecture. Derivation through mathematics, we prove that the Collatz-leaf node (Collatz-leaf integer) has the characteristics of inheritance. With computer large numbers and big data calculation, we conclude that all nodes at depth 800 are Collatz- leaf nodes. So we prove that strong Collatz conjecture is true, the Collatz conjecture must also be true. And for any positive integer N greater than 1, the minimum number of Collatz transform times from N to 1 is log2 N, the maximum number of Collatz transform times is 800 *(N-1).