GPM : an Objectbase Project Networking Method by Dr. Gui
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Timeboxing Process Model for Iterative Software Development
The Timeboxing Process Model for Iterative Software Development Pankaj Jalote Department of Computer Science and Engineering Indian Institute of Technology Kanpur – 208016; India Aveejeet Palit, Priya Kurien Infosys Technologies Limited Electronics City Bangalore – 561 229; India Contact: [email protected] ABSTRACT In today’s business where speed is of essence, an iterative development approach that allows the functionality to be delivered in parts has become a necessity and an effective way to manage risks. In an iterative process, the development of a software system is done in increments, each increment forming of an iteration and resulting in a working system. A common iterative approach is to decide what should be developed in an iteration and then plan the iteration accordingly. A somewhat different iterative is approach is to time box different iterations. In this approach, the length of an iteration is fixed and what should be developed in an iteration is adjusted to fit the time box. Generally, the time boxed iterations are executed in sequence, with some overlap where feasible. In this paper we propose the timeboxing process model that takes the concept of time boxed iterations further by adding pipelining concepts to it for permitting overlapped execution of different iterations. In the timeboxing process model, each time boxed iteration is divided into equal length stages, each stage having a defined function and resulting in a clear work product that is handed over to the next stage. With this division into stages, pipelining concepts are employed to have multiple time boxes executing concurrently, leading to a reduction in the delivery time for product releases. -

Basics of Project Planning
BASICS OF PROJECT PLANNING © Zilicus Solutions 2012 Contents The Basics of Project Planning ............................................................................................................. 3 Introduction ..................................................................................................................................... 3 What is Project Planning? ................................................................................................................ 3 Why do we need project planning? ................................................................................................. 3 Elements of project plan .................................................................................................................. 4 1. Project Scope Planning ...................................................................................................... 4 Triangular Constraints (TQR) ............................................................................................................ 5 2. Delivery Schedule Planning ............................................................................................... 5 3. Project Resources Planning ................................................................................................ 6 4. Project Cost Planning ......................................................................................................... 8 5. Project Quality Planning .................................................................................................... 9 -

Intro to BPC Logic Filter
INTRODUCTION TO BPC LOGIC FILTER FOR MICROSOFT PROJECT Prepared For: General Release Prepared By: Thomas M. Boyle, PE, PMP, PSP BPC Project No. 15-001 First issue 29-May-15 (Updated 02-Dec-20) Boyle Project Consulting, PLLC 4236 Chandworth Rd. Charlotte, NC 28210 Phone: 704-916-6765 Project Management and Construction Support Services [email protected] Introduction to – BPC Logic Filter for Microsoft Project 02-Dec-20 TABLE OF CONTENTS 1.0 EXECUTIVE SUMMARY .................................................................................................... 1 2.0 BACKGROUND / MOTIVATION ...................................................................................... 1 2.1 HISTORY ................................................................................................................................... 1 2.2 NEEDS ....................................................................................................................................... 1 3.0 PROGRAM DEVELOPMENT ............................................................................................ 2 3.1 FEATURE DEVELOPMENT ......................................................................................................... 2 3.2 SHARING THE TOOLS .............................................................................................................. 12 4.0 USER APPLICATIONS AND SETTINGS ....................................................................... 12 5.0 SOFTWARE EDITIONS AND LICENSING .................................................................. -

Unit 5 – Project Planning
Unit 5 – Project Planning UNIT OVERVIEW Description of the Unit In this unit, you will explore the necessity of proper project planning and how ‘front end’ planning can ensure project success. You will look at several scenarios that put a structure around project scope, deliverables, scheduling, staffing, resources, and risks to help anchor the planning process. Unit Objectives At the conclusion of this unit, you will be able to: • Understand the necessity of a project plan • Assess resource and budgeting issues • Analyze project risks • Effectively determine project scope • Identify project deliverables Unit Topics • Project schedules based on work breakdown structures • Project resources and schedules based on staff availability • Project budgets • Managing project risks • Triple constraint to achieve project goals Activities and Exercises • Group Exercise 5A: Project Management Scenarios • Group Exercise 5B: Review Project Plans for Unit 3 Scenarios Approximate Time for Unit 1 hour 45 minutes Managing Technology Projects and Technology Resources Participant Guide 5 - 1 Institute for Court Management Unit 5 – Project Planning Managing Technology Projects and Technology Resources Participant Guide 5 - 2 Institute for Court Management Unit 5 – Project Planning ___________________________________ ___________________________________ ___________________________________ ___________________________________ UNIT 5 ___________________________________ Project Planning ___________________________________ ___________________________________ ©2010 -

49R-06: Identifying the Critical Path 2 of 13
49R-06 IDENTIFYING THE CRITICAL PATH SAMPLE AACE® International Recommended Practice No. 49R-06 IDENTIFYING THE CRITICAL PATH TCM Framework: 7.2 – Schedule Planning and Development 9.2 – Progress and Performance Measurement 10.1 – Project Performance Assessment 10.2 – Forecasting Rev. March 5, 2010 Note: As AACE International Recommended Practices evolve over time, please refer to www.aacei.org for the latest revisions. Contributors:SAMPLE Disclaimer: The opinions expressed by the authors and contributors to this recommended practice are their own and do not necessarily reflect those of their employers, unless otherwise stated. Christopher W. Carson, PSP (Author) Paul Levin, PSP Ronald M. Winter, PSP (Author) John C. Livengood, PSP CFCC Abhimanyu Basu, PE PSP Steven Madsen Mark Boe, PE PSP Donald F. McDonald, Jr. PE CCE PSP Timothy T. Calvey, PE PSP William H. Novak, PSP John M. Craig, PSP Jeffery L. Ottesen, PE PSP CFCC Edward E. Douglas, III CCC PSP Hannah E. Schumacher, PSP Dennis R. Hanks, PE CCE L. Lee Schumacher, PSP Paul E. Harris, CCE James G. Zack, Jr. CFCC Sidney J. Hymes, CFCC Copyright © AACE® International AACE® International Recommended Practices AACE® International Recommended Practice No. 49R-06 IDENTIFYING THE CRITCAL PATH TCM Framework: 7.2 – Schedule Planning and Development 9.2 – Progress and Performance Measurement 10.1 – Project Performance Assessment 10.2 – Forecasting March 5, 2010 INTRODUCTION Purpose This recommended practice (RP) for Identifying the Critical Path is intended to serve as a guideline and a resource, not to establish a standard. As a recommended practice of AACE International it provides guidelines for the project scheduler when reviewing a network schedule to be able to determine the critical path and to understand the limitations and assumptions involved in a critical path assessment. -

Planning in Software Project Management
PLANNING IN SOFTWARE PROJECT MANAGEMENT AN EMPIRICAL RESEARCH OF SOFTWARE COMPANIES IN VIETNAM Thesis presented to the Faculty of Economics and Social Sciences at the University of Fribourg (Switzerland) in fulfillment of the requirements for the degree of Doctor of Economics and Social Sciences by Quynh Mai NGUYEN from Vietnam Accepted by the Faculty of Economics and Social Sciences on May 30th, 2006 at the proposal of Professor Dr. Andreas Meier (first advisor) Professor Dr. Jacques Pasquier (second advisor) Professor Dr. Laurent Donzé (third advisor) Fribourg, Switzerland 2006 The Faculty of Economics and Soci al Sciences at the University of Fribourg neither approves nor disapproves the opinions expressed in a doctoral dissertati on. They are to be considered those of the author (decision of the Faculty Council of January 23rd, 1990). To my parents, and To Phuong and Trung, my children ACKNOWLEDGEMENT I would like to express my extreme gratitude to Prof. Dr. Andreas Meier for his guidance, encouragement and helpful supervision during the process of this thesis. I would like to thank Prof. Jacques Pasquier and Prof. Laurent Donzé for their review and comments. My special thanks also go to Dr. Fredric William Swierczek for his invaluable help, advices and suggestions for improvement. Without their help and advice this dissertation could not be completed. I would like to thank my friends, Dr. Bui Nguyen Hung, and Dr. Nguyen Dac Hoa, Mrs. Nguyen Thuy Quynh Loan for their assistance and helpful suggestions and contributions. I would like to thank the government of Switzerland and the Swiss – AIT – Vietnam Management Development Program (SAV) for giving me the scholarship for this PhD program. -
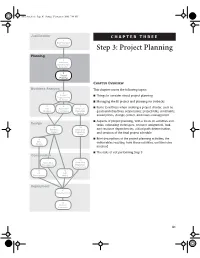
Step 3: Project Planning Planning 2 Enterprise Infrastructure Evaluation
MossAtre.book Page 81 Sunday, February 9, 2003 7:01 PM Justification CHAPTER THREE 1 Business Case Assesment Step 3: Project Planning Planning 2 Enterprise Infrastructure Evaluation 3 Project Planning CHAPTER OVERVIEW Business Analysis This chapter covers the following topics: 4 Project I Things to consider about project planning Requirements Definition I Managing the BI project and planning for setbacks 5 6 7 I Data Application Meta Data Items to address when creating a project charter, such as Analysis Prototyping Repository goals and objectives, scope issues, project risks, constraints, Analysis assumptions, change control, and issues management I Aspects of project planning, with a focus on activities and Design tasks, estimating techniques, resource assignment, task 8 10 Database Meta Data and resource dependencies, critical path determination, Design Repository and creation of the final project schedule Design 9 I Brief descriptions of the project planning activities, the ETL Design deliverables resulting from those activities, and the roles involved I The risks of not performing Step 3 Construction 12 14 Application Meta Data Development Repository Development 11 13 ETL Data Development Mining Deployment 15 Implementation 16 Release Evaluation 81 MossAtre.book Page 82 Sunday, February 9, 2003 7:01 PM 82 Step 3: Project Planning THINGS TO CONSIDER Business Involvement Do we have a strong business sponsor? Do we have a backup business sponsor? Do we have stakeholders with whom we need to communicate regularly? How much time is the -

Comparison Between Critical Path Method (CPM) and Last Planners System (LPS) for Planning and Scheduling METRO Rail Project of Ahmedabad
Comparison between Critical Path Method (CPM) and Last Planners System (LPS) for Planning and Scheduling METRO Rail Project of Ahmedabad Viraj Parekh1 , Karan Asnani1, Yashraj Bhatt1 and Rahul Mulchandani1 1 Civil Engineering Department, Institute of Technology, Nirma University, Ahmedabad, India Abstract. The purpose of this paper is to compare Critical Path Method (CPM) and Last Planner System (LPS) with respect to Planning and Scheduling of METRO Rail Project, Ahmedabad, Gujarat. Critical Path Method emphasises on updating the network for tracking the progress as well as to identify the delays. Last Planner System works on the weekly schedules prepared from the Master Plan and Look-ahead schedules to avoid the delays. One of the stretch from North-South Corridor was selected for the study from Vijaynagar to Usmanpura. The data such as activities, duration of activities, sequence and inter-relation of activities etc. were collected to prepare the network as well as weekly schedules. The network was updated and original network was compared with the up- dated one and the delays were spotted for the stretch selected. Weekly plans were also prepared for the selected stretch from the look-ahead schedule and Master Plan. PPC (Percent Plan Complete) were calculated to track the progress as per planned schedule. The data were collected by conducting interviews of various personnel and visual obser- vations. Both the approaches (CPM and LPS) have been applied on the selected stretch by action research process. The delays were calculated and studied for both the methods and it was observed that Last Planner System is more appropriate to use for big infra- structure projects like this to avoid time-overrun and consecutive cost over-run. -

An Application to PRINCE2
Bringing Model-based Systems Engineering Capabilities to Project Management: an Application to PRINCE2 Diana Coppola1, Andrea D’Ambrogio2, and Daniele Gianni1 1 Dept. of Applied Sciences and Technologies 2 Dept. of Enterprise Engineering Guglielmo Marconi University University of Rome Tor Vergata Rome, Italy Rome, Italy [email protected], [email protected] [email protected] Copyright © held by the author. Abstract—PRINCE2 is arguably one of the most adopted performance indicators and the maturity level of the process-based methods for project management. adopted project management methodology [2]. Currently, PRINCE2 is defined in a textual specification, PRINCE2 is arguably one of the most adopted which describes the principles, the themes, and the standard project management methodologies in various processes that project managers should apply in their systems engineering domains. PRINCE2 has been more management activities. Although the specification is well structured and mature, the specification does not provide and more adopted since 2009, for three reasons: a browsable digital representation that can be interactively used for learning and/or for the specification application 1. the overall trend of business to use a project- during project management activities. This paper aims to based approach to develop products or overcome these limitations with the application of a model- transformations within increasingly collaborative based systems engineering approach to represent the contexts with multiple partners; PRINCE2 specification in a model-based format. This can 2. the overall trend of capitalizing on knowledge of bring several benefits to the specification, including the best practices in project management; availability of a graphical, comprehensive and digitally 3. -

Work Breakdown Structures: the Foundation for Project Management Excellence
WORK BREAKDOWN STRUCTURES: THE FOUNDATION FOR PROJECT MANAGEMENT EXCELLENCE Eric S. Norman, PMP, PgMP Shelly A. Brotherton, PMP Robert T. Fried, PMP John Wiley & Sons, Inc. Work Breakdown Structures: The Foundation for Project Management Excellence E. S. Norman, S.A. Brotherton, R.T. Fried Copyright © 2008 John Wiley & Sons, Inc. ISBN: 978-0-470-17712-9 This book is printed on acid-free paper. Copyright 2008 by John Wiley & Sons, Inc. All rights reserved. Published by John Wiley & Sons, Inc., Hoboken, New Jersey. Published simultaneously in Canada. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978)-750-8400, fax (978)-646-8600, or on the web at www.copyright.com. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748-6008, or online at http://www.wiley.com/go/permissions. Limit of Liability/Disclaimer of Warranty: While the publisher and author have used their best efforts in preparing this book, they make no representations or warranties with respect to the accuracy or completeness of the contents of this book and specifically disclaim any implied warranties of merchantability or fitness for a particular purpose. -

TAILORING PRINCE2 MANAGEMENT METHODOLOGY to SUIT the RESEARCH and DEVELOPMENT PROJECT ENVIRONMENT Marius Simion National Researc
INCD ECOIND – INTERNATIONAL SYMPOSIUM – SIMI 2011 “THE ENVIRONMENT AND THE INDUSTRY” TAILORING PRINCE2 MANAGEMENT METHODOLOGY TO SUIT THE RESEARCH AND DEVELOPMENT PROJECT ENVIRONMENT Marius Simion National Research & Development Institute for Industrial Ecology, 90-92 Panduri Road, district 5, 050663 Bucharest, e-mail: [email protected] Abstract PRINCE (PRojects IN Controlled Environments) is a structured project management method for effective project management. This method was established by the Central Computer and Telecommunications Agency (CCTA) which was an United Kingdom government agency and initially used for information system projects. PRINCE was originally based on PROMPT (a project management method created by Simpact Systems Ltd. in 1975) and in 1989 effectively substituted PROMPT within Government projects. The Office of Government Commerce (the former CCTA) continued to develop the method, and in 1996 PRINCE2 was launched. PRINCE2 is extensively used by the United Kingdom government, and now is a de facto standard widely recognised for all projects not just for information system projects. For any research and development project is possible to apply a product- oriented methodology as PRINCE2 and guide the project by its principles.The originality of the paper consists in adapting and adjusting PRINCE2 to a pre- established project methodology of an authority which finances projects (such as National Authority for Scientific Research- ANCS). PRINCE2 was tailored to suit that methodology and designed the adapted process model diagram. The aim of the paper is not substitution of PRINCE2 processes and products with those of a default methodology but only according them. Applying PRINCE2 320 INCD ECOIND – INTERNATIONAL SYMPOSIUM – SIMI 2011 “THE ENVIRONMENT AND THE INDUSTRY” methodology for any research and development project is a guarantee that the project could be kept under control in terms of time, cost and quality. -

Evaluating Gant Project, Orange Scrum, and Projeqtor Open Source Project Management Tools Using QSOS
Evaluating Gant Project, Orange Scrum, and ProjeQtOr Open Source Project Management Tools using QSOS Catarina Romão Proença1a and Jorge Bernardino1,2 b 1Polytechnic of Coimbra – ISEC, Rua Pedro Nunes, Quinta da Nora, 3030-199 Coimbra, Portugal 2CISUC - Centre of Informatics and Systems of University of Coimbra, Pinhal de Marrocos, 3030-290 Coimbra, Portugal Keywords: Open Source Software, Project Management Tools, Qualification and Selection of Open Source Software, Assessment Methodologies, Gantt Project, Orange Scrum, ProjeQtOr. Abstract: The task of managing a software project is an extremely complex job, drawing on many personal, team, and organizational resources. We realized that exist many project management tools and software being developed every day to help managers to automate the administration of individual projects or groups of projects during their life-cycle. Therefore, it is important to identify the software functionalities and compare them to the intended requirements of the company, to select which software complements the expectations. This paper presents a comparison between three of the most popular open source project management tools: Gantt Project, OrangeScrum, ProjeQtOr. To assess these project management tools is used the Qualification and Selection Open Source (QSOS) methodology. 1 INTRODUCTION differentiates between numerous candidates to meet technical, functional and strategic requirements. For Managing projects involving different groups of such we apply the Qualification and Selection Open people and complex tasks can be challenging. The Source (QSOS) methodology to the open source solution is to use project management software, project management tools. The QSOS methodology which allows more efficient management of projects. describes a formal process to evaluate, compare and Today, there is a large amount of available project select open source solutions.