1 Je{A1f-Ht-4Ttfitte
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Considerations for Use of Microcomputers in Developing Countrystatistical Offices
Considerations for Use of Microcomputers in Developing CountryStatistical Offices Final Report Prepared by International Statistical Programs Center Bureau of the Census U.S. Department of Commerce Funded by Office of the Science Advisor (c Agency for International Development issued October 1983 IV U.S. Department of Commerce Malcolm Baldrige, Secretary Clarence J. Brown, Deputy Secretary BUREAU OF THE CENSUS C.L. Kincannon, Deputy Director ACKNOWLEDGE ME NT S This study was conducted by the International Statistical Programs Center (ISPC) of the U.S. Bureau of the Census under Participating Agency Services Agreement (PASA) #STB 5543-P-CA-1100-O0, "Strengthening Scientific and Technological Capacity: Low Cost Microcomputer Technology," with the U.S. Agency for International Development (AID). Funding fcr this project was provided as a research grant from the Office of the Science Advisor of AID. The views and opinions expressed in this report, however, are those of the authors, and do not necessarily reflect those of the sponsor. Project implementation was performed under general management of Robert 0. Bartram, Assistant Director for International Programs, and Karl K. Kindel, Chief ISPC. Winston Toby Riley III provided input as an independent consultant. Study activities and report preparation were accomplished by: Robert R. Bair -- Principal Investigator Barbara N. Diskin -- Project Leader/Principal Author Lawrence I. Iskow -- Author William K. Stuart -- Author Rodney E. Butler -- Clerical Assistant Jerry W. Richards -- Clerical Assistant ISPC would like to acknowledge the many microcomputer vendors, software developers, users, the United Nations Statistical Office, and AID staff and contractors that contributed to the knowledge and experiences of the study team. -

Programming Languages, Database Language SQL, Graphics, GOSIP
b fl ^ b 2 5 I AH1Q3 NISTIR 4951 (Supersedes NISTIR 4871) VALIDATED PRODUCTS LIST 1992 No. 4 PROGRAMMING LANGUAGES DATABASE LANGUAGE SQL GRAPHICS Judy B. Kailey GOSIP Editor POSIX COMPUTER SECURITY U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 100 . U56 4951 1992 NIST (Supersedes NISTIR 4871) VALIDATED PRODUCTS LIST 1992 No. 4 PROGRAMMING LANGUAGES DATABASE LANGUAGE SQL GRAPHICS Judy B. Kailey GOSIP Editor POSIX COMPUTER SECURITY U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1992 (Supersedes July 1992 issue) U.S. DEPARTMENT OF COMMERCE Barbara Hackman Franklin, Secretary TECHNOLOGY ADMINISTRATION Robert M. White, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director - ;,’; '^'i -; _ ^ '’>.£. ; '':k ' ' • ; <tr-f'' "i>: •v'k' I m''M - i*i^ a,)»# ' :,• 4 ie®®;'’’,' ;SJ' v: . I 'i^’i i 'OS -.! FOREWORD The Validated Products List is a collection of registers describing implementations of Federal Information Processing Standards (FTPS) that have been validated for conformance to FTPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FTPS identified in this document. The Validated Products List is updated quarterly. iii ' ;r,<R^v a;-' i-'r^ . /' ^'^uffoo'*^ ''vCJIt<*bjteV sdT : Jr /' i^iL'.JO 'j,-/5l ':. ;urj ->i: • ' *?> ^r:nT^^'Ad JlSid Uawfoof^ fa«Di)itbiI»V ,, ‘ isbt^u ri il .r^^iytsrH n 'V TABLE OF CONTENTS 1. -

Datasheet Fujitsu SPARC M10-4S
Datasheet Fujitsu SPARC M10-4S Datasheet Fujitsu SPARC M10-4S Everything your mission critical enterprise application needs in stability, scalability and asset protection Only the best with Fujitsu SPARC Enterprise A SPARC of steel Based on robust SPARC architecture and running the Fujitsu SPARC M10-4S server is the nearest thing you leading Oracle Solaris 11, Fujitsu SPARC M10-4S can get to an open mainframe. Absolutely rock servers are ideal for customers needing highly solid, dependable and sophisticated, but with the scalable, reliable servers that increase their system total Solaris binary compatibility necessary to both utilization and performance through virtualization. protect your investments and enhance your business. The combined leverage of Fujitsu’s expertise in mission-critical computing technologies and Its rich virtualization eco-system of extended high-performance processor design, with Oracle’s partitioning and Solaris Containers coupled with expertise in open, scalable, partition-based network dynamic reconfiguration, means non-stop operation computing, provides the overall flexibility to meet and total resource utilization at no extra cost. any task. Benchmark leading performance with the world’s best applications and outstanding processor scalability just add to the capabilities of this most expandable of system platform. Page 1 of 6 www.fujitsu.com/sparc Datasheet Fujitsu SPARC M10-4S Features and benefits Main features Benefits Supreme performance The supreme performance in all commercial servers Highest performance -
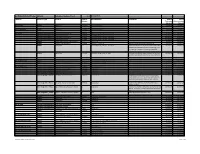
ACTIAN PRODUCTS by Platform Extended Support List
ACTIAN PRODUCTS by Platform Extended Support List As of 30 Jun 2015 \ Platform Product Type Product Product OS Release(s) Comments End of End of Release Extended Obsolescence Support Support DG/UX Intel RDBMS Ingres II EE 2.0/0001 4.20 MU04, MU05 31-Dec-08 31-Dec-13 DG/UX Motorola RDBMS Ingres II EE 2.0/0001 4.1 MU04 to MU06 31-Dec-08 31-Dec-13 HP TRU 64 Application Development OpenROAD Development 5.0/0506 Tru64 4.0f, 4.0g, 5.0a, 5.1, 5.1a, 5.1b 31-Dec-18 31-Dec-23 Application Development OpenROAD Runtime 5.0/0506 Tru64 4.0f, 4.0g, 5.0a, 5.1, 5.1a, 5.1b 31-Dec-18 31-Dec-23 Application Development OpenROAD Development 4.1/0403 Tru64 4.0f, 4.0g, 5.0a, 5.1, 5.1a, 5.1b 31-Mar-14 31-Mar-19 Application Development OpenROAD Runtime 4.1/0403 Tru64 4.0f, 4.0g, 5.0a, 5.1, 5.1a, 5.1b 31-Mar-14 31-Mar-19 RDBMS Ingres 2006 Release 2 Service Pack 2 9.1.2 Tru64 5.1b 31-Dec-16 31-Dec-21 RDBMS Ingres 2.6 Service Pack 6 2.6/0803 Tru64 5.1, 5.1a, 5.1b Marvel is supported running Tru64 5.1b. 31-Dec-14 31-Dec-19 RDBMS Ingres II EE 2.5 Tru64 4.0f, 4.0g, 5.0a, 5.1, 5.1a, 5.1b Customers should use Ingres threads on GS series 31-Dec-12 31-Dec-17 machines with NUMA architecture running Tru64 5.x. -

User Guide Disclaimer
HostAccess User Guide Disclaimer Every effort has been made to ensure that the information contained within this publication is accurate and up-to-date. However, Rogue Wave Software, Inc. does not accept liability for any errors or omissions. Rogue Wave Software, Inc. continuously develops its products and services, and therefore reserves the right to alter the information within this publication without notice. Any changes will be included in subsequent editions of this publication. As the computing industry lacks consistent standards, Rogue Wave Software, Inc. cannot guarantee that its products will be compatible with any combination of systems you choose to use them with. While we may be able to help, you must determine for yourself the compatibility in any particular instance of Rogue Wave Software, Inc. products and your hardware/software environment. Rogue Wave Software, Inc. acknowledges that certain proprietary programs, products or services may be mentioned within this publication. These programs, products or services are distributed under Trademarks or Registered Trademarks of their vendors and/or distributors in the relevant country. Your right to copy this publication, in either hard-copy (paper) or soft-copy (electronic) format, is limited by copyright law. You must obtain prior authorisation from Rogue Wave Software, Inc. before copying, adapting or making compilations of this publication. HostAccess is a trademark of Quovadx Ltd in the United Kingdom and is a registered trademark in the USA. Microsoft is a registered trademark and Windows is a trademark of the Microsoft Corporation. Other brands and their products are trademarks or registered trademarks of their respected holders and should be noted as such. -

THIS MONTH Sony WA -8800 Ten -Band Cassette Recorder
REVIEWED THIS MONTH Sony WA -8800 ten -band cassette recorder YESTERDAY'S SPY SET The 128 Set Revisited BUILD THE LONGWAVER LOOP ANTENNA INDEX TO VOLUME 49 Regular Features for Airband, Scanning, Junior Listeners, SSB Utility Listening, Propagation and Broadcast Enthusiasts Extra Wideband Scanning Power New Models With Even More Facilities! JUST RELEASED. NEW HP2000 Now with continuous coverage featuring a completere -design and new p.c.b. layout Frequency coverage:- 500KHz- 1300MHz with no gaps * 1,000 channel memory * Receives AM -FM- Wideband FM * Search steps selectable from 5KHz to 995KHz * Keypad or rotary tune controls * Switcheable 10dB attenuator Each set is supplied with:- * Full set of high power NiCad rechargeable batteries * UK spec. charger * Three antennas- VHF, UHF, short wave telescopic * Carrying case, belt clip, shoulder strap * Dc cable for car cigar adaptor supply * Earpiece for private listening £269 NEW Nevada MS1000 Mobile/Base Scanner An exciting new scanner with all the specifications of the HP200 aboveplus:- * Switcheable audio squelch * Tape recorder output socket * Automatic tape recorder switching circuit switchestape recorder on when a signal is present * All metal case for improved EMC compatibility £279 Awilable From Authorised Dealers Throughout The UK- t Nevada Communications, 189 London Road, North End, Portsmouth. P02 9AE Send in £2 now *r our LATEST CATALOGUE with full details ofour complete product range (includes a £2 voucher). CA=e5)zr_727x arro VOL. 49 ISSUE 12 DECEMBER 1991 ON SALE NOVEMBER 28 10 Speedbird Concorde Zero One Peter Rouse GU1DKD (Next Issue on sale DECEMBER 20) 12 A Basic RTTY Receive -only Terminal unit - EDITOR: Dick Ganderton, C. -

What's So Great About Fujitsu and PRIMERGY?
Fact Sheet What’s so great about Fujitsu and PRIMERGY Fact Sheet What’s so great about Fujitsu and PRIMERGY? What’s so great about Fujitsu and PRIMERGY? realizing high-speed interconnections are Fujitsu America Inc., a wholly owned subsidiary achievements that will set Fujitsu apart of Fujitsu Limited, the third largest IT Company from competitors. in the world, is pleased to present this overview of our PRIMERGY® server. Customers have found PRIMERGY Servers to be a superior investment. With the Fujitsu mainframe Fujitsu has been in the x86 server market since heritage, they are designed to be the solution 1995 as part of a joint venture with Siemens® for enterprise computing environments. through the creation of the Fujitsu-Siemens PRIMERGY Servers will play a significant Computers partnership. The joint venture role in meeting business objectives with: company played a particularly important role as a product development base for x86 servers. ■ Industry-leading Reliability - Fujitsu The decision to fully consolidate Fujitsu PRIMERGY servers integrate Japanese Siemens Computers and unify PRIMERGY server innovation with German engineering. Our development under the successor company, PRIMERGY servers have an average mean Fujitsu Technology Solutions, accelerates time between failures (MTBF) of over 6 product development and enables us to years and a life expectancy of over 10 years. provide globally standardized products. Fujitsu ■ Cool-safe® Technology - Fujitsu PRIMERGY made the investment to buy Siemens half of servers use an average of 20% less power the joint venture as of April 1, 2009. than our competitor’s servers of a similar model. In fact, the PRIMERGY TX120 Drawing on the long Fujitsu heritage and model cuts energy costs in half over experience of designing rock-solid mainframe standard servers. -

FUJITSU LIMITED Annual Report 2004 Ink Containing Less Than 15% Oil-Based Solvent
FUJITSU LIMITED Annual Report 2004 FUJITSU LIMITED www.fujitsu.com This report is printed on 100% recycled paper with ink containing less than 15% oil-based solvent. Annual Report 2004 CONTENTS Consolidated Financial Highlights ………………………………… 1 To Our Shareholders ……………………………………………… 2 Management Direction ……………………………………… 4 Principal Products and Services ………………………………… 8 Customer Solution Profiles ……………………………………… 10 Software & Services …………………………………………… 14 Platforms …………………………………………………………… 16 Electronic Devices ………………………………………………… 18 Research & Development ……………………………………… 19 Intellectual Property ……………………………………………… 20 Environmental Involvement……………………………………… 22 Social Contribution Activities……………………………………… 23 Management ……………………………………………………… 24 Five-Year Summary………………………………………………… 26 Management's Discussion and Analysis of Operations………… 27 Consolidated Balance Sheets……………………………………… 34 Consolidated Statements of Operations………………………… 36 Consolidated Statements of Shareholders' Equity……………… 37 Consolidated Statements of Cash Flows………………………… 38 Notes to Consolidated Financial Statements…………………… 40 Independent Auditors' Report…………………………………… 56 Principal Subsidiaries and Affiliates……………………………… 57 Shareholders' Data………………………………………………… 57 Cautionary Statement This annual report may contain forward-looking statements that are based on management's current views and assumptions and involve known and unknown risks and uncertainties that could cause actual results, performance or events to differ materially from those expressed or implied in such -

FUJITSU LIMITED Annual Report 2003 Consolidated Financial Highlights 1
FUJITSU LIMITED Annual Report 2003 FUJITSU LIMITED Annual Report 2003 Consolidated Financial Highlights 1 To Our Shareholders 2 At a Glance 8 Customer Solution Profiles 10 Software and Services 14 Platforms 16 Electronic Devices 18 Research & Development 19 Environmental Activities / Community Support 20 Management 22 Five-Year Summary 24 Management's Discussion and Analysis of Operations 25 Consolidated Balance Sheets 30 Consolidated Statements of Operations 32 Consolidated Statements of Shareholders' Equity 33 Consolidated Statements of Cash Flows 34 Notes to Consolidated Financial Statements 35 Independent Auditors' Report 52 Principal Subsidiaries and Affiliates 53 Cautionary Statement This annual report may contain forward-looking statements that are based on management's current views and assumptions and involve known and unknown risks and uncertainties that could cause actual results, performance or events to differ materially from those expressed or implied in such statements. Words such as "anticipates," "believes," "expects," "estimates," "intends," "plans," "projects," and similar expressions which indicate future events and trends identify forward-looking statements. Actual results may differ materially from those projected or implied in the forward-looking statements due to, without limitation, the following factors: general economic and market conditions in the major geographic markets for Fujitsu's services and products, which are the United States, EU, Japan and elsewhere in Asia, particularly as such conditions may effect -

Server, Storage & Integrated Systems Family Guide
Server, Storage & Integrated Systems Family Guide Your fast lane to PRIMERGY / PRIMEQUEST servers, ETERNUS storage and PRIMEFLEX Integrated Systems Windows Server: Power your business 1 Digitalization: Your Data Center is the foundation FUJITSU Business-Centric Data Center We live in a world where people are constantly connected. As individuals we want more intuitive services. Be it large or small and medium-sized businesses, both must adapt to this rising demand and what it means for their ICT. It all depends on what you do with your IT. There can be no ‘one-size-fits-all’ approach to your data center. So we start with your business priorities then match the right mix of products, services and solutions. That way you get an end-to-end approach that can deliver what your enterprise demands.See how Fujitsu can help large or growing businesses achieve their business objectives. On Premise - Hybrid IT - In the Fujitsu Cloud Managed by yourself - Managed by Fujitsu Robust IT - Bimodal - Fast IT Business-Centric Business-Centric Business-Centric COMPUTING STORAGE INTEGRATED SYSTEMS Fujitsu Business-Centric Computing will give you the servers Fujitsu ETERNUS Business-centric Storage supports your Building data center infrastructure is often complex and you need to power any workload and changing business business better to help you achieve your goals. time-consuming. You’ll know the do-it-yourself approach requirements. can be risky and expensive. With Fujitsu Business-Centric Integrated Systems you can make the difference. 2 FUJITSU Server Enterprise Products Ensure your servers serve the business FUJITSU is the leading ICT provider with an entire portfolio of IT products, solutions and services – from notebooks, tablets, PCs and data center solutions up to managed services and cloud solutions. -

Validated Products List, 1993 No. 4
VALIDATED PRODUCTS LIST 1993 No. 4 Programming Languages Database Language SQL Graphics GOSIP POSIX Judy B. Kailey Computer Security Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1993 {Supersedes July 1993 issue) -i)C 100 .U56 NIST //5274 1993 DATE DUE QrUhi j Demco, Inc. 38-293 NISTIR 5274 (Supersedes NISTIR 5220) VALIDATED PRODUCTS LIST 1993 No. 4 Programming Languages Database Language SQL Graphics GOSIP POSiX Judy B. Kailey Computer Security Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1993 (Supersedes July 1993 issue) U.S. DEPARTMENT OF COMMERCE Ronald H. Brown, Secretary TECHNOLOGY ADMINISTRATION Mary L Good, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Arati Prabhakar, Director / FOREWORD The Validated Products List is a collection of registers describing implementations of Federal Information Processing Standards (FIPS) that have been validated for conformance to FIPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FIPS identified in this document. The Validated Products List is updated quarterly. IV TABLE OF CONTENTS 1. INTRODUCTION 1-1 1.1 Purpose 1-1 1.2 Document Organization 1-2 1.2.1 Programming Languages 1-2 1.2.2 Database Language SQL 1-2 1.2.3 Graphics 1-2 1.2.4 GOSIP 1-2 1.2.5 POSIX 1-2 1.2.6 Computer Security 1-2 1.2.7 FIPS Conformance Testing Products 1-2 2. -

Validated Products List: Programming Languages, Database Language
NISTIR 469 (Supersedes NISTIR 4623) VALIDATED PRODUCTS LIST 1991 No. 4 Programming Languages Database Language SQL Graphics ®OSIP Judy B. Kailey POSIX Editor U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1991 (Supersedes July 1991 issue) U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director — QC 100 .U56 NIST //4690 1991 V C.2 NISTIR 4690 (Supersedes NISTIR 4623) - ' J JF VALIDATED PRODUCTS LIST 1991 No. 4 Programming Languages Database Langucige SQL Graphics GOSIP Judy B. Kailey POSIX Editor U.S. DEPARTMENT OF COMMERCE National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1991 (Supersedes July 1991 issue) U.S. DEPARTMENT OF COMMERCE Robert A. Mosbacher, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director FOREWORD The Validated Products List (formerly called the Validated Processor List) is a collection of registers describing implementations of Federal Information Processing Standards (FIPS) that have been tested for conformance to FIPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FIPS identified in this document. The Validated Products List is updated quarterly. TABLE OF CONTENTS 1. INTRODUCTION 1-1 1.1 Purpose 1-1 1.2 Document Organization 1-1 1.2.1 Programming Languages 1-1 1.2.2 Database Language SQL 1-2 1.2.3 Graphics 1-2 1.2.4 GOSIP 1-2 1.2.5 POSIX 1-2 1.2.6 FIPS Conformance Testing Products 1-2 2.