Expedition User Guide Version 1.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IAF-01-T.1.O1 Progress on the International Space Station
https://ntrs.nasa.gov/search.jsp?R=20150020985 2019-08-31T05:38:38+00:00Z IAF-01-T.1.O1 Progress on the International Space Station - We're Part Way up the Mountain John-David F. Bartoe and Thomas Holloway NASA Johnson Space Center, Houston, Texas, USA The first phase of the International Space Station construction has been completed, and research has begun. Russian, U.S., and Canadian hardware is on orbit, ard Italian logistics modules have visited often. With the delivery of the U.S. Laboratory, Destiny, significant research capability is in place, and dozens of U.S. and Russian experiments have been conducted. Crew members have been on orbit continuously since November 2000. Several "bumps in the road" have occurred along the way, and each has been systematically overcome. Enormous amounts of hardware and software are being developed by the International Space Station partners and participants around the world and are largely on schedule for launch. Significant progress has been made in the testing of completed elements at launch sites in the United States and Kazakhstan. Over 250,000 kg of flight hardware have been delivered to the Kennedy Space Center and integrated testing of several elements wired together has progressed extremely well. Mission control centers are fully functioning in Houston, Moscow, and Canada, and operations centers Darmstadt, Tsukuba, Turino, and Huntsville will be going on line as they are required. Extensive coordination efforts continue among the space agencies of the five partners and two participants, involving 16 nations. All of them continue to face their own challenges and have achieved significant successes. -
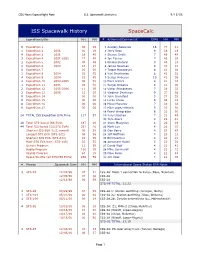
ISS Spacewalk History Spacecalc
CBS News/Spaceflight Now U.S. Spacewalk Statistics 9/15/06 ISS Spacewalk History SpaceCalc Expedition EVAs HH MM # Astronaut/Cosmonaut EVAs HH MM 0 Expedition 1 00 00 1 Anatoly Solovyov 16 77 41 1 Expedition 2 2001 00 19 2 Jerry Ross 9 58 18 4 Expedition 3 2001 18 40 3 Steven Smith 7 49 48 3 Expedition 4 2001-2002 17 49 4 Joe Tanner 7 46 29 2 Expedition 5 2002 09 46 5 Nikolai Budarin 9 46 14 2 Expedition 6 2003 13 17 6 James Newman 6 43 13 0 Expedition 7 00 00 7 Talgat Musabayev 8 43 02 1 Expedition 8 2004 03 55 8 Yuri Onufrienko 8 42 52 4 Expedition 9 2004 15 45 9 Sergei Avdeyev 10 41 59 2 Expedition 10 2004-2005 09 58 10 Piers Sellers 6 41 10 1 Expedition 11 2005 04 58 11 Sergei Krikalev 8 41 08 2 Expedition 12 2005-2006 11 05 12 Victor Afanaseyev 7 38 33 2 Expedition 13 2006 12 25 13 Vladimir Dezhurov 9 37 56 0 Expedition 14 00 00 14 John Grunsfeld 5 37 32 0 Expedition 15 00 00 15 Leroy Chiao 6 36 16 0 Expedition 16 00 00 16 Musa Manarov 7 34 32 0 Expedition 17 00 00 17 Mike Lopez-Alegria 5 33 58 18 Pavel Vinogradov 6 32 50 24 TOTAL ISS Expedition EVA Time 117 57 19 Yury Usachev 7 31 48 20 Tom Akers 4 29 41 28 Total STS-based ISS EVAs 187 20 21 Story Musgrave 4 26 19 44 Total ISS-based ISS/STS EVAs 251 16 22 Mark Lee 4 26 01 Shortest ISS EVA (U.S. -

Patrick G. Forrester (Colonel, U.S
National Aeronautics and Space Administration Lyndon B. Johnson Space Center Houston, Texas 77058 December 2020 Patrick G. Forrester (Colonel, U.S. Army, Ret.) NASA Astronaut Summary: COL Patrick G. Forrester was selected as a NASA astronaut in 1996. The Texas native is a retired Army Colonel and holds a Master’s Degree in Mechanical and Aerospace Engineering. Forrester flew on shuttle missions STS-105, STS-117, and STS-128. STS-105 delivered the Leonardo Multi-Purpose Logistics Module (MPLM) with supplies and equipment to the station and included two spacewalks by Forrester. During STS-117, Forrester conducted two more spacewalks and helped deliver the S3/4 truss segment. For STS-128, he was the prime robotics operator in attaching the Leonardo MPLM. Personal Data: Born March 31, 1957 in El Paso, Texas. Married to the former Diana Lynn Morris of Springfield, Virginia. They have two children. He enjoys baseball and running. Patrick’s mother, Patsy L. Forrester, and father, Colonel (ret.) Redmond V. Forrester are both deceased. Diana’s father, Colonel (ret.) Lurie J. Morris, resides in Hendersonville, North Carolina. Her mother, Bettye Morris, is deceased. Education: Graduated from West Springfield High School, Springfield, Virginia, in 1975; received a Bachelor of Science Degree in Applied Sciences and Engineering from the United States Military Academy, West Point, New York, in 1979, and a Master of Science Degree in Mechanical and Aerospace Engineering from the University of Virginia in 1989. Experience: Forrester graduated from West Point in June 1979 and was commissioned as a Second Lieutenant in the U.S. Army. He entered the U.S. -
C a L E N D a R International Space Station
For more information on the International Space Station, visit: www.nasa.gov/station visit: Station, Space International the on information more For www.nasa.gov National Aeronautics and Space Administration INTERNATIONAL SPACE STATION CALENDAR 2011 A MESSAGE FROM THE PROGRAM MANAGER The International Space Station (ISS) is one of the greatest technological, geopolitical and engineering accomplishments in human 2011 history. The completion of the ISS on-orbit assembly allows for a focus on the multifaceted purpose of the ISS, one of scientific research, technology development, exploration and education. As a National Laboratory, the ISS will provide opportunities beyond NASA to academia, commercial entities and other government agencies to pursue their research and development needs in science, technology development and education. With everyone working together, we look forward to extending human presence beyond and improving life here on Earth. This calendar is designed to show all facets of the ISS using displays of astounding imagery and providing significant historical events with the hope of inspiring the next generation. NASA is appreciative of the commitment that America’s educators demonstrate each and every day as they instruct and shape the young students who will be tomorrow’s explorers and leaders. I hope you enjoy the calendar and are encouraged to learn new and exciting aspects about NASA and the ISS throughout the year. Regards, MICHAEL T. SUFFREDINI ISS Program Manager 1 2 2 3 4 6 5 LOOK HOW FAR WE’VE COME 20 JANUARY NASA has powered us into the 21st century through signature 11 accomplishments that are enduring icons of human achievement. -

ESA's ISS External Payloads
number 8, march 2002 on station The Newsletter of the Directorate of Manned Spaceflight and Microgravity http://www.esa.int/spaceflight in this issue A Promising Start to 2002 aurora Jörg Feustel-Büechl Aurora: A European Roadmap 4 ESA Director of Manned Spaceflight and Microgravity for Solar System Exploration Rolf Schulze I want to highlight two very important milestones for this year. Firstly, the final integration and test of our Columbus virtual campus laboratory for the International Space Station began at The Erasmus Virtual Campus 6 Astrium GmbH in Bremen (D) following the arrival in Dieter Isakeit September of the Pre-Integrated Columbus Assembly (PICA) from Alenia Spazio in Turin (I). I believe that we have a payloads masterpiece of European engineering here, and I am ESA’s ISS External Payloads 8 delighted with the progress so far.We should be seeing some Steve Feltham & Giacinto Gianfiglio very real advance on Columbus by the end of 2002 and look forward to its status then. xeus Secondly, I had the opportunity on 15 January to review ISS Assembly of XEUS 10 the course of the Automated Transfer Vehicle (ATV) project at Jens Schiemann Les Mureaux (F), together with our team and the industries involved in the project under prime contractor EADS-LV.The spoe progress is quite remarkable when we remember the SPOE 12 difficulties of last year. All in all, I think that the technical Rolf-Dieter Andresen, Maurizio Nati achievements so far are satisfactory. One important & Chris Taylor demonstration of this progress is the arrival of the ATV Structural Test Model in ESTEC’s Test Centre, where it will research undergo testing during the whole of this year. -

Expedition 21 and 22 Assembling Science
National Aeronautics and Space Administration PRESS KIT/SEPTEMBER 2009 Expedition 21 and 22 Assembling Science www.nasa.gov This page intentionally blank TABLE OF CONTENTS Section Page MISSION OVERVIEW ............................................................................................................... 1 EXPEDITION 21 & 22 CREW .................................................................................................... 11 EXPEDITION 21/22 MAJOR MILESTONES ............................................................................... 23 EXPEDITION 21/22 SPACEWALKS .......................................................................................... 25 RUSSIAN SOYUZ TMA ............................................................................................................. 27 SOYUZ BOOSTER ROCKET CHARACTERISTICS .................................................................................... 31 PRELAUNCH COUNTDOWN TIMELINE ................................................................................................... 32 ASCENT/INSERTION TIMELINE ............................................................................................................ 33 ORBITAL INSERTION TO DOCKING TIMELINE ...................................................................................... 34 KEY TIMES FOR EXPEDITION 21/22 INTERNATIONAL SPACE STATION EVENTS ................................... 39 EXPEDITION 20/SOYUZ TMA-14 LANDING .......................................................................................... -

The Newsletter of the Directorate of Manned Spaceflight and Microgravity
number 7, december 2001 on station The Newsletter of the Directorate of Manned Spaceflight and Microgravity http://www.esa.int/export/esaHS/ 2001: A Good Year - But Hard Work Lies Ahead Jörg Feustel-Büechl ESA Director of Manned Spaceflight and Microgravity We have had a really excellent 2001 in technical terms. Since the first launch, of Zarya in November 1998, we have had 24 launches either to build up the International Space Station with new equipment and facilities, or to service it – a remarkable achievement. Indeed, there have been 12 launches in 2001 alone! Altogether, we have seen some remarkable hardware progress in the programme and – even better – there have been no major in-orbit problems. So we have created an operational Station with a permanent 3-man crew and we have already seen the first experiments (including European experiments) completed. All in all, the Station is working really well, both in terms of its technical realisation and of the international cooperation between the five Partners. Unfortunately, the rest of the picture is not so rosy.We heard from NASA earlier in 2001 of the likelihood of major cost overruns on their part. So far, overall US costs have been around $25 billion and NASA has announced increases of some $4.8 billion to take Station assembly to completion.The Bush Administration declared this to be unacceptable and initiated a review by the NASA Advisory Council.This Review, chaired by Thomas Young, was tasked to investigate what kind of management, cost and technical changes must be implemented in order to contain the costs within the original funding plan.The outcome includes a number of drastic recommendations not only in management and cost control, but also in the Station’s configuration. -

International Space Station 2008 Calendar the International Space Station (ISS) Is the Largest and Most Complicated Spacecraft Ever Built
NP-2007-10-021-JSC .nasa.gov www December November October September August July June May April March y Februar y Januar National Aeronautics and Space Administration International Space Station 2008 Calendar The International Space Station (ISS) is the largest and most complicated spacecraft ever built. It is allowing NASA to conduct scientific esearr ch to improve life on Earth and to prepare for long-duration space flights to the moon and other destinations. DSecMemTbeWr2T 0 F0 S 8 1 2 3 4 5 6 1988 – STS-27 launch 1973 – Pioneer 10 flyby of 1965 – Gemini VII launch 2001 – STS-108 (ISS, 1990 – STS-35 launch Jupiter. First flyby of outer 1998 – STS-88 (ISS, Unity Expedition 4) launch 1992 – STS-53 launch planet Connecting Module) 1993 – STS-61 (Hubble launch. First U.S. ISS Space Telescope servicing) segment launch 7 8 9 10 11 12 13 1972 – Apollo 17 launch. 2006 – STS-116 (ISS, P5 Final Apollo mission truss) launch 14 15 16 17 18 19 20 1965 – Gemini VI-A 1903 – Wright brothers 1999 – STS-103 (Hubble launch. Gemini VI-A and VII first flight Space Telescope servicing) successfully rendezvous launch 1970 – Venera 7 (U.S.S.R.) first spacecraft to land on another planet (Venus) 21 22 23 24 25 Christmas 26 27 Winter Solstice— 1968 – Apollo 8 becomes Winter begins first crewed mission to 1968 – Apollo 8 launch orbit the moon 28 29 30 31 Orion Statistics: For more information about the Constellation Program, please visit: Crew size 6 (ISS missions) 4 (moon missions) http://www.nasa.gov/mission_pages/constellation/main/index.html Diameter 16.5 feet 5 meters Pressurized volume 692 cubic feet 20 cubic meters 5: 12: 19: 27: NASA’s Constellation Program is currently building the next-generation vehicle that will be launched atop the Ares I rocket. -

Fault-Source/Literacy/Passport-Reading
Passport Reading Journeys Strategic Intervention Program Overview Grades 6–12 AVAILABLE IN BUILDS ENGAGED, MOTIVATED READERS WITH HIGH-INTEREST CONTENT WITH PASSPORT READING JOURNEYS, STUDENTS READ CLOSELY AND INDEPENDENTLY Passport Reading Journeys™ (PRJ) with Updated Content is an engaging literacy solution for middle and high school students reading below grade level. The research-validated reading intervention uses a blended approach with real-world, relevant, captivating content and motivating technology components that support and enhance instruction. FEATURES RELATED BENEFITS Engaging video segments MOTIVATE students to participate in lessons moderated by peers and build background knowledge. Interactive, student-centered PREPARE students for high-stakes exams online technology components and engage them in online literacy activities. Age-appropriate, high-interest ENGAGE students while building reading content and instruction skills and closing the achievement gap. INTEGRATE collaborative learning Students and teachers can opportunities, immediate feedback, and highlight, annotate, write, student self-monitoring using multiple and bookmark digital materials devices anytime, anywhere. Reading activities focused on INSPIRE students to focus on college and career. career and real-world learning Who Needs Passport Reading Journeys? • Students in grades 6–12 who are reading one to three years below grade level • Students with varied needs, including English language learners Implement with a blend 2 www.voyagersopris.com/prj of print and digital or 100% digitally PASSPORT READING JOURNEYS STUDENTS GET PRACTICE IN KEY LITERACY STRANDS PRJ with Updated Content provides sequenced skills, immediate feedback, and opportunities for focused review and guided practice through engaging, high-interest reading Expeditions. The topics motivate students to read more complex content, moving them to grade-level reading comprehension. -

Calendar2010 with the Beginning of a New Year, Construction of the International Space Station Is Nearing Completion
www.nasa.gov NP-2009-10-033-JSC National Aeronautics and Space Administration International Space Station calendar2010 With the beginning of a new year, construction of the International Space Station is nearing completion. As the largest and most complicated spacecraft ever built, this orbiting outpost can support a crew of six, operating 24 hours a day, seven days a week, 365 days a year. It is a shining example of international cooperation for the United States and its space exploration partners. A New Year of Exploration January 2010 SMTWTFS 1 2 3 4 1965 – Gemini VII 1973 – Pioneer 10. Flyby 1998 – STS-88 Unity of Jupiter. First yby of Connecting Module. First outer planet U.S. segment 5 6 7 8 9 10 11 2001 – STS-108 1972 – Apollo 17. Final Expedition 4 Apollo mission 2006 – STS-116 P5 truss 12 13 14 15 16 17 18 1965 – Gemini VI-A and VII successfully rendezvous 1970 – Venera 7 (U.S.S.R.). First spacecraft to land on 1903 – Wright brothers another planet (Venus) rst ight Winter Solstice— Christmas Day 19 20 21 Winter begins 22 23 24 25 1968 – Apollo 8 becomes rst crewed mission to 1968 – Apollo 8 orbit the moon 26 27 28 29 30 31 SMTWTFS SMTWTFS 1 2 3 4 5 6 1 7 8 9 10 11 12 13 2 3 4 5 6 7 8 14 15 16 17 18 19 20 9 10 11 12 13 14 15 January 2011 st rd 21 22 23 24 25 26 27 16 17 18 19 20 21 22 New 1 Full 3 November 2010 5 13 21 28 28 29 30 25 26 27 28 29 For more information about the International Space Station please visit www.nasa.gov Neutral Buoyancy Lab Ascent Training Ground support for the International Space Station involves more than 100,000 people in space agencies, at 500 contractor facilities and in 37 U.S. -

The International Space Station Habitat
( [, Source of Acquisition NASA Jolmson Space Center The International Space Station Habitat l 2 Patricia Mendoza Watson , Mike Engle }NASA Johnson Space Center, Houston Texas 77058, Mail Code OM 2NASA Johnson Space Center, Houston Texas 77058, Mail Code OM Abstract. The International Space Station (ISS) is an engineering project unlike any other. The vehicle is inhabited and operational as construction goes on. The habitability resources available to the crew are the crew sleep quarters, the galley, the waste and hygiene compartment, and exercise equipment. These items are mainly in the Russian Service Module and their placement is awkward for the crew to deal with. ISS assembly will continue with the truss build and the addition of International Partner Laboratories. Also, Node 2 and 3 will be added. The Node 2 module wi ll provide additional stowage volume and room for more crew sleep quarters. The Node 3 module will provide additional Environmental Control and Life Support Capability. The purpose of the ISS is to perform research and a major area of emphasis is the effects of long duration space flight on humans, a result of this research they will determine what are the habitability requirements for long duration space flight. - -- .. .. .._ -- ~.--- _ -- _ ! The International Space Station Habitat Patricia Mendoza Watsonl and Mike Engle2 INA SA, Johnson Space Center, Mail Code OM, Houston TX 77058, 281-483-7770, [email protected] 2NASA, Johnson Space Center, Mai l Code OM, Houston TX 77058, 281-244-0904, [email protected] Abstract. The International Space Station (ISS) is an engineering project unlike any other. -

IODP JOI Alliance FY04 Quarterly Report 2
20 May 2004 1 January–31 March 2004 Quarterly Report 2 Contract No. NSF OCE-0352500 Submitted by the JOI Alliance to The National Science Foundation TABLE OF CONTENTS TABLE OF CONTENTS ..............................................................................................................1 INTRODUCTION.........................................................................................................................3 EXPEDITION OPERATIONS.......................................................................................................3 IODP-USIO Expedition Schedule .....................................................................................3 Expedition Planning and Implementation Activities ...........................................................3 PHASE 1 MOBILIZATION ACTIVITIES .......................................................................................5 Plans for Mobilization.......................................................................................................5 Status of Equipment.........................................................................................................5 Insurance and Indemnification..........................................................................................6 Health, Safety, and Environment (HSE) Procedures.........................................................6 Environmental Assessment..............................................................................................6 TECHNOLOGY DEVELOPMENT................................................................................................7