DOS 3.30 Package?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

File Formats
man pages section 4: File Formats Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 817–3945–10 September 2004 Copyright 2004 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, and Solaris are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which license also covers Sun’s licensees who implement OPEN LOOK GUIs and otherwise comply with Sun’s written license agreements. -

Tutorial for VCS
Tutorial for VCS STEP 1: login to the Linux system on Linuxlab server. Start a terminal (the shell prompt). Click here to open a shell window Fig. 1 The screen when you login to the Linuxlab through equeue STEP 2: In the terminal, execute the following command: module add ese461 You could perform “module avail” in the terminal to find the available modules on Linuxlab. Make sure ese461 is presented when you execute this command. 1.Find the available modules 2.Make sure ese461 is presented 3.This command will set up the work environment for class ESE461 Fig. 2 Build work environment for class ESE461 using module 1 STEP 3: Getting started with Verilog • Creating a new folder (better if you have all the files for a project in a specific folder). • Enter into this new folder and start writing your Verilog script in a new file (.v file). Example code for modeling an counter is here • In addition to model code, Test Bench script has to be given in order to verify the functionality of your model (.v file). Example code of test bench for counter is here. Use gedit to edit the .v files (gedit is a commonly used GUI editor on Linux ) Fig. 3 Open gedit through teminal STEP 4: Compiling and simulating your code • In the terminal, change the directory to where your model and test bench files (Counter.v and Counter_tb.v) are present by using this command: cd <path> For example: cd ~/ESE461/VcsTutorial/ (Remark: ‘~’ means home directory on Linux) • Compile the files by typing in the terminal: vcs <file>.v <file_tb>.v In the above example, it should be: vcs Counter.v Counter_tb.v There should be no error presented in the terminal. -

Club-80 Heft 41 (Bw Ocr).Pdf
Inhaltsverzeichnis * . Autor & Seite Autor & Seite Clubinternes Hardware Zusammenfassung Fragebogenaktion 1-5 Floppy-Tester 65- 66 Jens Neueder Artikel aus Elektor Neues vom Vorstand 6 - 8 Club 80-Neumitglieder aus "CP/M-aktuell"-Usergruppe Auswertung der Fragebogen zur Mitgliederkarteiaktualisierung Nachträge zum Vorwort 9-10 Club 80 Börse 67 Hartmut Obermann Suche... Uwe Schobert Clubinfo H - 12 Termine 13 Jens Neueder Sonstiges Neuigkeiten für CP/M 69 Vorstellung 13 - 14 Alexander Schmid Jörg Lindner Genie News: Neue Preisstrukturen 70- 71 Software Wissenswertes ZCPR oder Z3Plus 72- 73 Literaturrecherche: USA, England, Deutschland 73-85 Austausch von Grafiken DOS -> CP/M 15 - 18 Egbert Schröer Alexander Schmid Wichtige T ip s... Elektrikers 86 Grafik des Gills unter Holte CP/M + 19-26 Alexander Schmid Volker Dose, Egbert Schröer Model 4 intern: Dem Interpreter aufs Bit geschaut 27 - 35 Artikel aus CP Die letzten Seiten Impressum 87 MSDOS-Trick: Command /F 35 Schluß 88 Insider-Info: Windows-Fehler 68 Redaktion Hartmut Obermann Mitgliederadressenliste am INFO-Ende Microsoft Link80 und .SYM-Datei 36 Sonderheft: Wissenswertes rund um den Z280 am INFO-Ende Uwe Schobert Software-Technik und Compilerbau 37-38 Artikel aus PASCAL IMP - ein DFÜ-Programm für CP/M 39-44 Günther W. Braun Internet und UUCP mit CP/M 45- 58 Volker Dose Internet via Genie 59- 62 GE-Mail aud Internet Access 63- 64 Egbert Schröer Fragebogenaktion Auswertung/Zusammenfassung Von 70 versandten Fragebögen erhielten wir bisher 43 mehr oder weniger vorhandene Erfahrungen: ausgefüllt wieder zurück. Die folgenden Seiten geben eine Zusammenfassung 21 Club-Mitglieder würden gern ihre Hard- und/oder Softwareerfahrungen den Eurer Antworten/Angaben wieder. -

Helenos Installer
Charles University in Prague Faculty of Mathematics and Physics BACHELOR THESIS Dominik T´aborsk´y HelenOS Installer Department of Distributed and Dependable Systems Supervisor of the bachelor thesis: Mgr. Martin Dˇeck´y Study programme: Computer Science Specialization: General Computer Science Prague 2013 I wish to thank to my supervisor, my family and anyone who supported me. Special thanks belongs to my father, who has left us just too soon. In memory of Daniel T´aborsk´y. I declare that I carried out this bachelor thesis independently, and only with the cited sources, literature and other professional sources. I understand that my work relates to the rights and obligations under the Act No. 121/2000 Coll., the Copyright Act, as amended, in particular the fact that the Charles University in Prague has the right to conclude a license agreement on the use of this work as a school work pursuant to Section 60 paragraph 1 of the Copyright Act. In ........ date ............ signature of the author N´azev pr´ace: HelenOS instal´ator Autor: Dominik T´aborsk´y Katedra: Katedra distribuovan´ych a spolehliv´ych syst´em˚u Vedouc´ıbakal´aˇrsk´epr´ace: Mgr. Martin Dˇeck´y, Katedra distribuovan´ych a spo- lehliv´ych syst´em˚u Abstrakt: Schopnost sebe sama nainstalovat na trval´e´uloˇziˇstˇeje jedna z vˇec´ı definuj´ıc´ıch pouˇzitelnost syst´emu. V t´eto pr´aci se pod´ıv´ame na naˇse moˇznosti jak toho dos´ahnout v pˇr´ıpadˇeoperaˇcn´ıho syst´emu HelenOS. Budeme se zab´yvat t´ım, jak´em´ame volby, jak´ejsou jejich v´yhody a nev´yhody a koneˇcnˇejak´ejsou jejich implementaˇcn´ı detaily. -
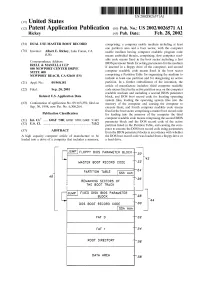
[JUMP FLOPPY Bios PARAMETER BLOCK—\20
US 20020026571A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0026571 A1 Rickey (43) Pub. Date: Feb. 28, 2002 (54) DUAL USE MASTER BOOT RECORD comprising: a computer usable medium including at least one partition area and a boot sector, With the computer (76) Inventor: Albert E. Rickey, Lake Forest, CA usable medium having computer readable program code (Us) means embodied therein, comprising: ?rst computer read able code means ?xed in the boot sector including a ?rst Correspondence Address: BIOS parameter block for setting parameters for the medium IRELL & MANELLA LLP if inserted in a ?oppy drive of the computer; and second 840 NEWPORT CENTER DRIVE SUITE 400 computer readable code means ?xed in the boot sector NEWPORT BEACH, CA 92660 (US) comprising a Partition Table for organizing the medium to include at least one partition and for designating an active (21) Appl. No.: 09/960,181 partition. In a further embodiment of the invention, the article of manufacture includes: third computer readable (22) Filed: Sep. 20, 2001 code means ?xed in the active partition area on the computer readable medium and including a second BIOS parameter Related US. Application Data block, and DOS boot record code for locating operating system ?les, loading the operating system ?les into the (63) Continuation of application No. 09/163,359, ?led on memory of the computer and causing the computer to Sep. 30, 1998, noW Pat. No. 6,308,264. execute them; and fourth computer readable code means ?xed in the boot sector comprising a master boot record code Publication Classi?cation for loading into the memory of the computer the third computer readable code means comprising the second BIOS (51) Int. -

JAMS 7.X User Guide
User Guide JAMS Scheduler 7.3 Copyright Terms and Conditions Copyright Help/Systems LLC and its group of companies. The content in this document is protected by the Copyright Laws of the United States of America and other countries worldwide. The unauthorized use and/or duplication of this material without express and written permission from HelpSystems is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to HelpSystems with appropriate and specific direction to the original content. HelpSystems and its trademarks are properties of the HelpSystems group of companies. All other marks are property of their respective owners. 202108110755 JAMS 7.X User Guide Table of Contents JAMS 7.X Client Features 3 Jobs In JAMS 4 Working with Jobs 5-19 Scheduling Recurring Jobs 20-22 Execution Methods 23-27 Submitting Jobs Manually 28-29 Sequence Jobs 30-34 Managing Sequence Parameters 35-38 Sequence Tasks 39-47 Workflow Jobs 48-51 Workflow Activities 52-59 Migrating JAMS Objects 60-61 File Transfer Features 62-67 Variables 68 Working with Variables 69-71 Elements 72 Documentation Elements 73-74 EventHandler Elements 75-79 Prerequisite Elements 80-83 Result Elements 84-86 Trigger Elements 87-92 Folders 93 Working with Folders 94-104 Dates and Times 105 Date Properties 106-107 Creating Special Date Definitions 108-111 Specifying Dates Using Natural Language 112-114 Named Times in JAMS 115-118 Dashboards and Reports 119 Custom Dashboards 120-129 Creating New Report Templates and Customizing Existing Reports -

OS 386 Multiuser/Multitasking Operating System
OS 386 Multiuser/Multitasking Operating System REFERENCE GUIDE [Q] DIGITAL RESEARCH@ os REFERENCE GUIDE [jill DIGITAL RESEARCH~ COPYRIGHT Copyright © 1987 Digital Research Inc. All rights reserved. No part of this publication may be reproduced, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise without the prior written permission of Digital Research Inc, 60 Garden Court, Box DRI, Monterey, California 93942 DISCLAIMER DIGITAL RESEARCH MAKES NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE CONTENTS HEREOF AND SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE. Further Digital Research Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research Inc to notify any person of such revision or changes. NOTICE TO USER This manual should not be construed as any representation or warranty with respect to the software named herein. Occasionally changes or variations exist in the software that are not reflected in the manual. Generally, if such changes or variations are known to exist and to affect the product significantly, a release note or READ.ME file accompanies the manual and the distribution disks. In that event, be sure to read the release note or READ.ME file before using the product. ii TRADEMARKS Digital Research and its logo, CP/M, and CP/M-86 are registered trademarks of Digital Research Inc. Cardfile, Concurrent, Concurrent DOS 386, Concurrent DOS XM, DR EDIX, DOS Plus and MP/M-86 are trademarks of Digital Research Inc. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

DOS Technical Reference
-------- - ---- Personal Computer - ---- - --- ------ - . - Programming Family DOS Technical Reference 6138536 Preliminary First Edition (February 1985) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent ~ith local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES TIllS PUBLICATION "AS IS" wrrnom WARRANTY OF ANY KIND, EmlER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, 1HE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. lbis publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and!or changes in the product(s) and/or the program(s) described in this pUblication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Products are not stocked at the address below. Requests for copies of this publication and for technical information about IBM Personal Computer products should be made to your authorized IBM Personal Computer dealer, IBM Product Center, or your IBM Marketing Representative. The following paragraph applies only to the United States and Puerto Rico: A Reader's Comment Form is provided at the back of this publication. If the form has been removed. -

Files and Processes (Review)
Files and Processes (review) Files and Processes (review) 1/61 Learning Objectives Files and Processes (review) I Review of files in standard C versus using system call interface for files I Review of buffering concepts I Review of process memory model I Review of bootup sequence in Linux and Microsoft Windows I Review of basic system calls under Linux: fork, exec, wait, exit, sleep, alarm, kill, signal I Review of similar basic system calls under MS Windows 2/61 Files Files and I Recall how we write a file copy program in standard C. Processes (review) #include <stdio.h> FILE *fopen(const char *path, const char *mode); size_t fread(void *ptr, size_t size, size_t nmemb, FILE *stream); size_t fwrite(const void *ptr, size_t size, size_t nmemb, FILE *stream); int fclose(FILE *fp); I We can also use character-based functions such as: #include <stdio.h> int fgetc(FILE *stream); int fputc(int c, FILE *stream); I With either approach, we can write a C program that will work on any operating system as it is in standard C. 3/61 Standard C File Copy Files and Processes (review) I Uses fread and fwrite. I files-processes/stdc-mycp.c 4/61 POSIX/Unix Files Files and Processes (review) I "On a UNIX system, everything is a file; if something is not a file, it is a process." I A directory is just a file containing names of other files. I Programs, services, texts, images, and so forth, are all files. I Input and output devices, and generally all devices, are considered to be files. -

Toolkit Feature Interactive Debug Facility User's Guide
High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page 311. This edition applies to IBM High Level Assembler for z/OS & z/VM & z/VSE Toolkit Feature, Release 6, Program Number 5696-234 and to any subsequent releases until otherwise indicated in new editions. Make sure that you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. IBM welcomes your comments. For information on how to send comments, see “How to send your comments to IBM” on page xv. © Copyright IBM Corporation 1992, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ............... ix Building a module on z/OS ........ 17 Building a module on CMS ........ 17 About this book ........... xi Building a phase on z/VSE ........ 17 Running ASMLANGX ........... 18 Syntax notation ............. xi Extraction file allocation on z/OS ...... 18 Online language extraction on TSO ..... 19 How to send your comments to IBM .. xv Batch language extraction on z/OS ..... 19 If you have a technical problem ....... xv Online language extraction on CMS ..... 20 Batch language extraction on z/VSE ....