The Differences Between XP Pro and XPE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

Solve Errors Caused by Corrupt System Files
System File Corruption Errors Solved S 12/1 Repair Errors Caused by Missing or Corrupt System Files With the information in this article you can: • Find out whether corrupt system files could be causing all your PC problems • Manually replace missing system files using your Windows installation CD • Use System File Checker to repair broken Windows system files • Boost the memory available to Windows File Protection for complete system file protection Missing or corrupt system files can cause many problems when using your PC, from cryptic error messages to mysterious system crashes. If one of the key files needed by Windows has gone missing or become corrupt, you may think that the only way to rectify the situation is to re-install Windows. Fortunately, nothing that drastic is required, as Microsoft have included several tools with Windows that allow you to replace corrupt or missing files with new, fresh copies directly from your Windows installation CD. Now, whenever you find that an important .DLL file has been deleted or copied over, you won’t have to go to the trouble of completely re-installing your system – simply replace the offending file with a new copy. Stefan Johnson: “One missing file can lead to your system becoming unstable and frequently crashing. You may think that the only way to fix the problem is to re-install Windows, but you can easily replace the offending file with a fresh copy from your Windows installation CD.” • Solve errors caused by corrupt system files ................... S 12/2 • How to repair your missing system file errors .............. -

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -

IIS Security and Programming Countermeasures
IIS Security and Programming Countermeasures By Jason Coombs ([email protected]) Introduction This is a book about how to secure Microsoft Internet Information Services for administrators and programmers whose work includes a requirement for information security, a computer industry specialty field commonly referred to as infosec. In this book the terms information security and infosec are used interchangeably with the more friendly term data security. This is not a book about hacking, cracking, and the tools and techniques of the bad guys, the so-called black hat hackers. This book teaches computer professionals and infosec specialists how to build secure solutions using IIS. It is your duty to secure and defend networked information systems for the benefit of the good guys who are your end users, clients, or less technical coworkers. There is nothing you can do that will transform a programmable computer running Microsoft Windows from its vulnerable condition to an invulnerable one. Every general purpose programmable computer is inherently vulnerable because it is controlled by software and is designed to allow new software to be installed or executed arbitrarily. Network computing based on programmable general purpose computers will never be safe from an information security perspective. Eliminating the feature of general purpose programmability from a networked computer and replacing its software with firmware reduces but does not eliminate vulnerabilities. These are immutable realities of present day computing and, as always, reality represents your biggest challenge. Microsoft is in business to get as much of your money as possible using whatever means will work at a given moment and in this respect they know virtually no equal in the software business. -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

WAF/CDP V3.7.1 User Guide
WAFS/CDP v3.7.1 User Guide GlobalSCAPE, Inc. (GSB) 4500 Lockhill-Selma Road, Suite 150 Address: San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical Support: (210) 366-3993 Web Support: http://www.globalscape.com/support/ © 2004-2010 GlobalSCAPE, Inc. All Rights Reserved July 21, 2010 Table of Contents GlobalSCAPE Replication Software ............................................................................................................. 7 What's New? .............................................................................................................................................. 7 For the Best WAFS/CDP Experience .................................................................................................... 8 Getting Started .............................................................................................................................................. 9 WAFS Quick Start ..................................................................................................................................... 9 CDP Quick Start ...................................................................................................................................... 11 Quick Reference ...................................................................................................................................... 13 File-Naming Conventions ........................................................................................................................ 13 WAFS/CDP -

Upgrading to Windows 7
Upgrading to Windows 7 Windows 7 was designed to upgrade from Windows Vista and not from Windows XP. Additionally, Microsoft will only allow the following upgrade path to Vista users: • Windows Vista Home Premium to Windows 7 Home Premium • Windows Vista Business to Windows 7 Professional • Windows Vista Enterprise to Windows 7 Enterprise • Windows Vista Ultimate to Windows 7 Ultimate ***Any other upgrade path from Vista to Windows 7 will require a clean install*** ***Any upgrade from Windows XP to Windows 7 will require a clean install*** Before proceeding with an installation of Windows 7, you are strongly advised to run Windows 7 Upgrade Advisor. Windows 7 Upgrade Advisor will check the compatibility of your computer with Windows 7 and alert you to any issues that you should address before installing Windows 7. The download is available at http://www.microsoft.com/windows/windows‐7/get/upgrade‐advisor.aspx. 1. From the Microsoft website click on Download the Windows Upgrade Advisor Beta. 2. Click Download and then click Run. 3. A window will display that says “Do you want to run this software?” Click Run. 4. On the Setup Wizard screen, click Next. 5. Click I accept the license terms and click Next. 6. Click Install. When installation is complete, click Close. 7. When you see the screen below, click Start Check. 8. Windows Upgrade Advisor will start checking compatibility. 9. Once the scan is complete, Upgrade Advisor will display any issues that you should be aware of. 10. Click Close to exit Windows Upgrade Advisor. You will be unable to do an in-place upgrade in the following situations: 1. -

Microsoft® Windows® XP Professional, Microsoft® Windows
Microsoft Windows XP Professional, Microsoft Windows XP Tablet PC Edition and Microsoft® Windows® XP Media Center Edition 2004 END-USER LICENSE AGREEMENT FOR MICROSOFT SOFTWARE IMPORTANT—READ CAREFULLY: This End-User License Agreement (“EULA”) is a legal agreement between you (either an individual or a single entity) and the manufacturer ("Manufacturer") of the computer system or computer system component (“HARDWARE”) with which you acquired the Microsoft software product(s) identified on the Certificate of Authenticity ("COA") affixed to the HARDWARE or on the associated product documentation (“SOFTWARE”). The SOFTWARE includes Microsoft computer software, and may include associated media, printed materials, “online” or electronic documentation, and Internet based services. Note, however, that any software, documentation, or web services that are included in the SOFTWARE, or accessible via the SOFTWARE, and are accompanied by their own license agreements or terms of use are governed by such agreements rather than this EULA. The terms of a printed paper EULA, which may accompany the SOFTWARE, supersede the terms of any on-screen EULA. This EULA is valid and grants the end-user rights ONLY if the SOFTWARE is genuine and a genuine Certificate of Authenticity for the SOFTWARE is included. For more information on identifying whether your software is genuine, please see http://www.microsoft.com/piracy/howtotell. YOU AGREE TO BE BOUND BY THE TERMS OF THIS EULA BY INSTALLING, COPYING, OR OTHERWISE USING THE SOFTWARE. IF YOU DO NOT AGREE TO THE TERMS OF THIS EULA, YOU MAY NOT USE OR COPY THE SOFTWARE, AND YOU SHOULD PROMPTLY CONTACT MANUFACTURER FOR INSTRUCTIONS ON RETURN OF THE UNUSED PRODUCT(S) FOR A REFUND IN ACCORDANCE WITH MANUFACTURER’S RETURN POLICIES. -
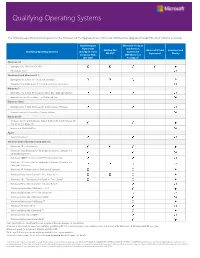
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Upgrading from Windows XP to Windows 7
Upgrading from Windows XP to Windows 7 Overview In this Tutorial Note: We highly recommend printing out this Step 1: Run Windows 7 Upgrade Advisor 2 tutorial. The Windows 7 installation process will Step 2: Move files and settings 3 restart your computer. If you don't return to this Step 3: Install Windows 7 5 webpage, the printed instructions will help you Step 4: Restore files and settings 8 complete the installation process. Introduction Windows XP can't use the Upgrade installation What You’ll Need option to install Windows 7. However, you can still An external hard drive or large capacity USB install Windows 7 by selecting the Custom option flash drive instead. An Internet connection This tutorial guides you through the process of A Windows 7 installation disc using Windows Easy Transfer to move your files and settings off of your PC, installing Windows 7 using the Custom option, and then moving your files back to your PC. Be sure to read the tutorial thoroughly before following the steps. Before you begin A Custom installation has several important differences from the Upgrade option that you need to know about: A Custom installation of Windows does not preserve your programs, files, or settings. It’s sometimes called a “clean” install for that reason. You’ll need to reinstall your programs. This means that you'll also need the original program installation discs or setup files for any programs that you want to install in Windows 7. You'll need to save your files to an external location off of your PC before you install Windows 7. -

Windows Intruder Detection Checklist
Windows Intruder Detection Checklist http://www.cert.org/tech_tips/test.html CERT® Coordination Center and AusCERT Windows Intruder Detection Checklist This document is being published jointly by the CERT Coordination Center and AusCERT (Australian Computer Emergency Response Team). printable version A. Introduction B. General Advice Pertaining to Intrusion Detection C. Look for Signs that Your System may have been Compromised 1. A Word on Rootkits 2. Examine Log Files 3. Check for Odd User Accounts and Groups 4. Check All Groups for Unexpected User Membership 5. Look for Unauthorized User Rights 6. Check for Unauthorized Applications Starting Automatically 7. Check Your System Binaries for Alterations 8. Check Your Network Configurations for Unauthorized Entries 9. Check for Unauthorized Shares 10. Check for Any Jobs Scheduled to Run 11. Check for Unauthorized Processes 12. Look Throughout the System for Unusual or Hidden Files 13. Check for Altered Permissions on Files or Registry Keys 14. Check for Changes in User or Computer Policies 15. Ensure the System has not been Joined to a Different Domain 16. Audit for Intrusion Detection 17. Additional Information D. Consider Running Intrusion Detection Systems If Possible 1. Freeware/shareware Intrusion Detection Systems 2. Commercial Intrusion Detection Systems E. Review Other AusCERT and CERT Documents 1. Steps for Recovering from a Windows NT Compromise 2. Windows NT Configuration Guidelines 3. NIST Checklists F. Document Revision History A. Introduction This document outlines suggested steps for determining whether your Windows system has been compromised. System administrators can use this information to look for several types of break-ins. We also encourage you to review all sections of this document and modify your systems to address potential weaknesses.