Windows Bitlocker
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bitlocker Encryption for USB Drives Bitlocker Is a Security Feature. the Purpose of Bitlocker Is to Encrypt Your Data
BitLocker Encryption for USB Drives BitLocker is a security feature. The purpose of BitLocker is to encrypt your data. This is extremely necessary for any data that is not to be shared with other persons. This will prevent anyone from being able to access your files. In order to have access to your files, you will need to provide a secure password. This password should be unique only to you. More information is provided below on how to make a unique password in step 2. During this process, step 3 offers the option to save a recovery key. The recovery key is 48 characters long and consist of numbers and letters. This key will be saved to Active Directory and allow the IS Department to access your USB/External drive should you forget your password. To get started I would recommend encrypting the USB/External drive BEFORE adding any files. Once the drive is encrypted and you enter your password it will function as any other USB/External drive. So you may add, edit, or delete your files as you normally would. If you have any trouble following this guide or have any questions please do not hesitate to contact the IS department. You will need a USB or External drive in order to successfully complete this process. Multiple ways to navigate to BitLocker: 1. Control Panel System & Security BitLocker Drive Encryption 2. Search bar type in “BitLocker” Manage BitLocker Steps to encrypt your USB drive: Step 1: Click “Turn on BitLocker” Step 2: Check the “Use a password to unlock the drive” and enter your password. -

Trusted Platform Module (TPM) Quick Reference Guide
Trusted Platform Module (TPM) Quick Reference Guide System builders/integrators should give this Guide to the system owners to assist them in enabling and activating the Trusted Platform Module. Warning of Potential Data Loss ..........................3 Trusted Platform Module (TPM) .........................5 System Requirements ........................................5 Security Precautions ..........................................5 Password Procedures ............................................. 6 Emergency Recovery File Back Up Procedures ........... 7 Hard Drive Image Backup Procedures....................... 7 Clear Text Backup (Optional) .................................. 7 Trusted Platform Module Ownership ..................8 Trusted Platform Module Software Installation..8 Enabling the Trusted Platform Module ...............8 Assuming Trusted Platform Module Ownership..9 Recovery Procedures ........................................10 How to Recover from a Hard Drive Failure ............... 10 How to Recover from a Desktop Board, coin battery or TPM Failure........................................... 10 Clearing Trusted Platform Module Ownership ...11 Support Links ....................................................12 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL® PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER, -

Turning on Bitlocker Drive Encryption on Windows Computers Before You
Turning on BitLocker drive encryption on Windows computers Before you start a couple of VERY important notes... a) Make sure you have backups before you start just in case anything goes wrong (as it’s much harder, usually impossible, to recover data from an encrypted drive - as you would hope and expect). b) Make sure you keep a safe copy of the encryption key And please provide a copy for the IT Office to store for use in the event of a problem or, if you choose to let Microsoft keep it, make sure you know your login details for Microsoft. If you forget the passwords and can not recover a copy of your key you will loose all your files (which is another reason to keep backups). If you reset BitLocker and a new encryption key is set - please remember to provide a copy to the IT Office Windows 7, 8 and 10 have BitLocker Built in, this can be used to encrypt the hard drive. It just needs to be activated following the steps shown below. 1) Enable BitLocker for a Drive The easiest way to enable BitLocker for a drive is to right-click the drive in a File Explorer window, and then choose the “Turn on BitLocker” command. If you don’t see this option on your context menu. Then click on the windows icon and where it says “Type here to search” type in “encryption” and click on “Manage BitLocker” from the list of options that appears. It’s just that simple. The wizard that pops up walks you through selecting several options, which we’ve broken down into the sections that follow. -

Trusted Platform Module (TPM) TCG 1.2 / 2.0
Trusted Platform Module (TPM) TCG 1.2 / 2.0 USER GUIDE Revision 1.20 The information in this user's guide has been carefully reviewed and is believed to be accurate. The vendor assumes no responsibility for any inaccuracies that may be contained in this document, and makes no commitment to update or to keep current the information in this manual, or to notify any person or organization of the updates. Please Note: For the most up-to-date version of this manual, please see our website at www.supermicro.com. Super Micro Computer, Inc. ("Supermicro") reserves the right to make changes to the product described in this manual at any time and without notice. This product, including software and documentation, is the property of Supermicro and/ or its licensors, and is supplied only under a license. Any use or reproduction of this product is not allowed, except as expressly permitted by the terms of said license. IN NO EVENT WILL SUPER MICRO COMPUTER, INC. BE LIABLE FOR DIRECT, INDIRECT, SPECIAL, INCIDENTAL, SPECULATIVE OR CONSEQUENTIAL DAMAGES ARISING FROM THE USE OR INABILITY TO USE THIS PRODUCT OR DOCUMENTATION, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. IN PARTICULAR, SUPER MICRO COMPUTER, INC. SHALL NOT HAVE LIABILITY FOR ANY HARDWARE, SOFTWARE, OR DATA STORED OR USED WITH THE PRODUCT, INCLUDING THE COSTS OF REPAIRING, REPLACING, INTEGRATING, INSTALLING OR RECOVERING SUCH HARDWARE, SOFTWARE, OR DATA. Any disputes arising between manufacturer and customer shall be governed by the laws of Santa Clara County in the State of California, USA. The State of California, County of Santa Clara shall be the exclusive venue for the resolution of any such disputes. -

Microsoft Windows FIPS 140 Validation Security Policy Document
Secure Kernel Code Integrity Security Policy Document Microsoft Windows FIPS 140 Validation Microsoft Windows 10 (Creators Update, Fall Creators Update, April 2018 Update) Microsoft Windows Server (versions 1703, 1709, and 1803) Non-Proprietary Security Policy Document Version Number 1.4 Updated On April 4, 2019 © 2018 Microsoft. All Rights Reserved Page 1 of 24 This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision). Secure Kernel Code Integrity Security Policy Document The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Chapter 2: Windows 7
Chapter 2: Windows 7 When you delete a file, a. A copy of the file will be sent to the desktop b. You send the file to the Recycle Bin. c. The file will not be affected. d. A copy of the file will be stored in your active folder. Which of the following statements is correct about arrange icon on desktop. a. Icons on desktop can be arranged by name. b. Icons on desktop can be arranged by type. c. Icons on desktop can be arranged by size. d. All of the above. Which of the following statements is correct about opening control panel. a. You can open control panel from windows explorer. b. You can open control panel from start menu. c. You can open control panel from my computer. d. All of the above. The documents that is located in start menu store. a. The last 15 files that you have open. b. The last 15 files that you have delete. c. The last 15 files that you have copy. d. None of the above. The desktop is: a. An example of a hardware device. b. A folder. c. A file d. A window. The Shutdown icon on start menu means: a. Close all windows. b. Close the current windows. c. Close your computer. d. None of the above. To open a minimized window, you can click on the:- a. window’s button on the body of the taskbar. b. maximized button on the title bar. c. restore button on the title bar. d. all of the above. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
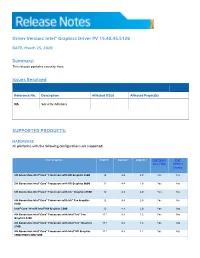
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Pitx-APL V2.0
USER GUIDE pITX-APL V2.0 Doc. Rev. 1.4 Doc-ID: 1065-6365 pITX-APL V2.0 – Rev. 1.4 This page has been intentionally left blank pITX-APL V2.0 – Rev. 1.4 PITX-APL V2.0 – USER GUIDE Disclaimer Kontron would like to point out that the information contained in this manual may be subject to alteration, particularly as a result of the constant upgrading of Kontron products. This document does not entail any guarantee on the part of Kontron with respect to technical processes described in the manual or any product characteristics set out in the manual. Kontron assumes no responsibility or liability for the use of the described product(s), conveys no license or title under any patent, copyright or mask work rights to these products and makes no representations or warranties that these products are free from patent, copyright or mask work right infringement unless otherwise specified. Applications that are described in this manual are for illustration purposes only. Kontron makes no representation or warranty that such application will be suitable for the specified use without further testing or modification. Kontron expressly informs the user that this manual only contains a general description of processes and instructions which may not be applicable in every individual case. In cases of doubt, please contact Kontron. This manual is protected by copyright. All rights are reserved by Kontron. No part of this document may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), without the express written permission of Kontron. -

Active@ NTFS Reader for DOS User Guide
Active Data Recovery Software Active@ NTFS Reader for DOS User Guide Version 1.0 Contents PRODUCT OVERVIEW SYSTEM REQUIREMENTS PRODUCT FEATURES OPERATING PROCEDURES 4.1 Bootable Floppy Disk (Startup Disk) Preparation..............................................................................4 4.2 Program Start and Information Display...............................................................................................5 4.3. Scan and Search for Files and Folders..................................................................................................5 4.4. Previewing Files.......................................................................................................................................6 4.5. Copying Files and Folders......................................................................................................................7 4.6. Using Disk Viewer ..................................................................................................................................8 4.7. Localized File Names Display ...............................................................................................................8 4.8. Long File Names Display.......................................................................................................................9 4.9. Command Line Parameters ...................................................................................................................9 1 PRODUCT OVERVIEW Active@ NTFS Reader is a compact and powerful DOS utility that -

Getting Started with Windows Speech Recognition
Getting Started with Windows™ Speech Recognition (WSR) A. OVERVIEW After reading Part One, the first time user will dictate an E-mail or document quickly with high accuracy. The instructions allow you to create, dictate, and send an E-mail without touching the keyboard. The second part discusses steps to attain highest accuracy. The final part has suggestions for increasing productivity when using Windows™ Speech Recognition. II. PART ONE A. WHY USE SPEECH RECOGNITION? Most people will be able to dictate faster and more accurately than they type. My experience with Windows™ Speech Recognition is the ability to dictate over 80 words a minute with accuracy of about 99%. If you truly can type at 80 words a minute with accuracy approaching 99%, you do not need speech recognition. However, even a good keyboarder will benefit from reduced strain on the hands and arms by using Windows™ Speech Recognition. It takes time to become comfortable with dictation into a computer. There will be moments of frustration as you go through the learning curve. If you are impatient or are a perfectionist, DO NOT read on and do not use Windows™ Speech Recognition. If you have reasonable patience, you will learn to dictate accurately and comfortably. The best strategy is to keep things simple for first several days of using Windows™ Speech Recognition. When you are comfortable with the basics, move to part two of this document. B. THE MICROPHONE A good microphone makes dictation into a computer a pleasure instead of a battle. Good microphones reproduce your voice accurately and block out background noise that distorts the audio signal. -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users.