Monero Mining: Cryptonight Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Auditing Wallets in Cryptonote
Auditing wallets in CryptoNote sowle <[email protected]> Zano project, https://zano.org Cryptocurrency wallet auditing is the ability for a third party (the "auditor") to watch the transactions and to be able to calculate the correct balance without an ability to spend a coin. This article explores several possible implementations of expansion cryptocurrency protocol CryptoNote 2.0 [1] with such ability. In the original CryptoNote protocol auditing is only partially possible with the help of the tracking key, namely, an auditor is able to distinguish incoming transactions in the blockchain, but the full set of secret keys is required to filter out outgoing transactions. This article is intended for readers familiar with the general blockchain technology and “classic” cryptocurrencies, as well as with the basics of cryptography on elliptic curves. 1. Introduction What is CryptoNote? Surprisingly, most people interested in blockchain technology have never heard anything about CryptoNote, in spite of the fact that the technology has more than 300 forks, including Monero as the most famous. Back in 2014 in the cryptocurrency community there were mentions [2] about a project, titled Bytecoin. That project did not originate as a Bitcoin or other known project fork, having its own original codebase. It was very unusual at the time. Bytecoin general conception was to be an implementation of a privacy-technology named CryptoNote. There were two main privacy mechanisms: stealth-addresses and inputs` mixing-in with the help of ring signatures (at the time it was called "blockchain mixer"). Since Zcash existed only on paper / in theory at that time, CryptoNote became a competitive technology and has provoked much controversy in the cryptocurrency community. -

Beauty Is Not in the Eye of the Beholder
Insight Consumer and Wealth Management Digital Assets: Beauty Is Not in the Eye of the Beholder Parsing the Beauty from the Beast. Investment Strategy Group | June 2021 Sharmin Mossavar-Rahmani Chief Investment Officer Investment Strategy Group Goldman Sachs The co-authors give special thanks to: Farshid Asl Managing Director Matheus Dibo Shahz Khatri Vice President Vice President Brett Nelson Managing Director Michael Murdoch Vice President Jakub Duda Shep Moore-Berg Harm Zebregs Vice President Vice President Vice President Shivani Gupta Analyst Oussama Fatri Yousra Zerouali Vice President Analyst ISG material represents the views of ISG in Consumer and Wealth Management (“CWM”) of GS. It is not financial research or a product of GS Global Investment Research (“GIR”) and may vary significantly from those expressed by individual portfolio management teams within CWM, or other groups at Goldman Sachs. 2021 INSIGHT Dear Clients, There has been enormous change in the world of cryptocurrencies and blockchain technology since we first wrote about it in 2017. The number of cryptocurrencies has increased from about 2,000, with a market capitalization of over $200 billion in late 2017, to over 8,000, with a market capitalization of about $1.6 trillion. For context, the market capitalization of global equities is about $110 trillion, that of the S&P 500 stocks is $35 trillion and that of US Treasuries is $22 trillion. Reported trading volume in cryptocurrencies, as represented by the two largest cryptocurrencies by market capitalization, has increased sixfold, from an estimated $6.8 billion per day in late 2017 to $48.6 billion per day in May 2021.1 This data is based on what is called “clean data” from Coin Metrics; the total reported trading volume is significantly higher, but much of it is artificially inflated.2,3 For context, trading volume on US equity exchanges doubled over the same period. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
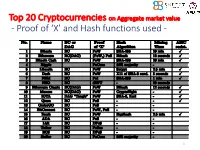
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

State of the Art: the Monero Cryptocurrency Mining Malware Detection Using Supervised Machine Learning Algorithms
International Journal of Applied Science and Engineering State of the art: The monero cryptocurrency mining malware detection using supervised machine learning algorithms Wilfridus Bambang Triadi Handaya1*, Mohd Najwadi Yusoff 2, Aman Jantan2 1 Department of Informatics, Universitas Atma Jaya Yogyakarta, Daerah Istimewa Yogyakarta, Indonesia 2 School of Computer Sciences, Universiti Sains Malaysia, Penang, Malaysia ABSTRACT Today’s evolving information technology trend is fuelling increasingly various cybercrime. Various cybercrime types, such as malware attacks and data breach activities, organizations, and countries, occur every day. Malware is one of the biggest cyber threats on the Internet today. Every year, the number of data breaches continues to increase. Mining is a complete cryptocurrency network’s computing process to verify transaction records, called blockchains, and receive digital coins in return. This mining process requires severe hardware and significant CPU resources to create cryptocurrencies. A statistic published by Statista in mid-2020 about the most detected crypto-mining malware types influencing corporate networks global from January to June 2020, it can be seen that cryptocurrency mining activity leading to the pool of Monero amounts to 46% derived from the use of XMRig. Malware detection is like an endless war between malware authors and malware prevention vendors. This trend change also makes the procedures and forms of analysis must adapt. From previously done manually with various tools for static analysis, to be OPEN ACCESS subsequently replaced with automatic analysis through the application of machine learning algorithms. Received: October 9, 2020 Revised: December 20, 2020 Keywords: Malware detection, XMRig, Monero, Cryptocurrencies, Mining. Accepted: January 6, 2021 Corresponding Author: Wilfridus Bambang Triadi Handaya 1. -

Hybrid Public/Anonymous Transactions on Monero, Cryptonote X-Cash
Hybrid public/anonymous transactions on Monero, Cryptonote X-Cash Zach Hildreth October 7, 2019 Abstract This yellow paper details the technical concepts and implementation of hybrid transactions (also known as FlexPrivacy c ), a feature enabling public and private transactions on the X- Cash public blockchain. In the first part, the paper aims at detailing how the hybrid transactions operate from a user’s perspective with some real-world use cases. A parallel is made between the digital money system and the economic behaviors associated with the current FIAT system. Secondly, a deeper understanding of the technology is given, explaining the implication on a blockchain perspective, as well as the edge cases and their approaches. Lastly, the last part consists in an in-depth approach of the mathematical concepts and technical implementation of the hybrid transaction in the X-Cash blockchain. Contents 1 Public transactions in the ringCT 4 2 Privacy in the inputs 4 3 A brief understanding of cryptonote transactions 4 4 Creation of a public address 6 5 How stealth addresses/outputs are decoded 6 6 How public transactions are created 7 1 Summary of the public transaction feature The hybrid transaction feature allows users to send and receive public or private transactions on the X-Network Blockchain X-Cash, which is based on the CryptoNote protocol. This feature is implemented on a per transaction basis where users can directly switch the privacy type by choosing the setting before attempting to send a transaction. In a public transaction, the following additional information is made public: • Sender’s address • Receiver’s address • Amount sent • Change amount sent back to the sender’s address However, the public transaction does not compromise the sender’s or receiver’s wallet full bal- ances nor the real mixin (number of signatures in the ring signature that authorizes the transaction) that provided the X-Cash balance. -

Coinbase Explores Crypto ETF (9/6) Coinbase Spoke to Asset Manager Blackrock About Creating a Crypto ETF, Business Insider Reports
Crypto Week in Review (9/1-9/7) Goldman Sachs CFO Denies Crypto Strategy Shift (9/6) GS CFO Marty Chavez addressed claims from an unsubstantiated report earlier this week that the firm may be delaying previous plans to open a crypto trading desk, calling the report “fake news”. Coinbase Explores Crypto ETF (9/6) Coinbase spoke to asset manager BlackRock about creating a crypto ETF, Business Insider reports. While the current status of the discussions is unclear, BlackRock is said to have “no interest in being a crypto fund issuer,” and SEC approval in the near term remains uncertain. Looking ahead, the Wednesday confirmation of Trump nominee Elad Roisman has the potential to tip the scales towards a more favorable cryptoasset approach. Twitter CEO Comments on Blockchain (9/5) Twitter CEO Jack Dorsey, speaking in a congressional hearing, indicated that blockchain technology could prove useful for “distributed trust and distributed enforcement.” The platform, given its struggles with how best to address fraud, harassment, and other misuse, could be a prime testing ground for decentralized identity solutions. Ripio Facilitates Peer-to-Peer Loans (9/5) Ripio began to facilitate blockchain powered peer-to-peer loans, available to wallet users in Argentina, Mexico, and Brazil. The loans, which utilize the Ripple Credit Network (RCN) token, are funded in RCN and dispensed to users in fiat through a network of local partners. Since all details of the loan and payments are recorded on the Ethereum blockchain, the solution could contribute to wider access to credit for the unbanked. IBM’s Payment Protocol Out of Beta (9/4) Blockchain World Wire, a global blockchain based payments network by IBM, is out of beta, CoinDesk reports. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Impossibility of Full Decentralization in Permissionless Blockchains
Impossibility of Full Decentralization in Permissionless Blockchains Yujin Kwon*, Jian Liuy, Minjeong Kim*, Dawn Songy, Yongdae Kim* *KAIST {dbwls8724,mjkim9394,yongdaek}@kaist.ac.kr yUC Berkeley [email protected],[email protected] ABSTRACT between achieving good decentralization in the consensus protocol Bitcoin uses the proof-of-work (PoW) mechanism where nodes earn and not relying on a TTP exists. rewards in return for the use of their computing resources. Although this incentive system has attracted many participants, power has, CCS CONCEPTS at the same time, been significantly biased towards a few nodes, • Security and privacy → Economics of security and privacy; called mining pools. In addition, poor decentralization appears not Distributed systems security; only in PoW-based coins but also in coins that adopt proof-of-stake (PoS) and delegated proof-of-stake (DPoS) mechanisms. KEYWORDS In this paper, we address the issue of centralization in the consen- Blockchain; Consensus Protocol; Decentralization sus protocol. To this end, we first define ¹m; ε; δº-decentralization as a state satisfying that 1) there are at least m participants running 1 INTRODUCTION a node, and 2) the ratio between the total resource power of nodes Traditional currencies have a centralized structure, and thus there run by the richest and the δ-th percentile participants is less than exist several problems such as a single point of failure and corrup- or equal to 1 + ε. Therefore, when m is sufficiently large, and ε and tion. For example, the global financial crisis in 2008 was aggravated δ are 0, ¹m; ε; δº-decentralization represents full decentralization, by the flawed policies of banks that eventually led to many bank which is an ideal state. -

Exploring the Interconnectedness of Cryptocurrencies Using Correlation Networks
Exploring the Interconnectedness of Cryptocurrencies using Correlation Networks Andrew Burnie UCL Computer Science Doctoral Student at The Alan Turing Institute [email protected] Conference Paper presented at The Cryptocurrency Research Conference 2018, 24 May 2018, Anglia Ruskin University Lord Ashcroft International Business School Centre for Financial Research, Cambridge, UK. Abstract Correlation networks were used to detect characteristics which, although fixed over time, have an important influence on the evolution of prices over time. Potentially important features were identified using the websites and whitepapers of cryptocurrencies with the largest userbases. These were assessed using two datasets to enhance robustness: one with fourteen cryptocurrencies beginning from 9 November 2017, and a subset with nine cryptocurrencies starting 9 September 2016, both ending 6 March 2018. Separately analysing the subset of cryptocurrencies raised the number of data points from 115 to 537, and improved robustness to changes in relationships over time. Excluding USD Tether, the results showed a positive association between different cryptocurrencies that was statistically significant. Robust, strong positive associations were observed for six cryptocurrencies where one was a fork of the other; Bitcoin / Bitcoin Cash was an exception. There was evidence for the existence of a group of cryptocurrencies particularly associated with Cardano, and a separate group correlated with Ethereum. The data was not consistent with a token’s functionality or creation mechanism being the dominant determinants of the evolution of prices over time but did suggest that factors other than speculation contributed to the price. Keywords: Correlation Networks; Interconnectedness; Contagion; Speculation 1 1. Introduction The year 2017 saw the start of a rapid diversification in cryptocurrencies. -

What Keeps Stablecoins Stable?
What Keeps Stablecoins Stable? Richard K. Lyons and Ganesh Viswanath-Natraj∗ First version: December 21, 2019 (posted SSRN) This version: May 3, 2020 Abstract We take this question to be isomorphic to, "What Keeps Fixed Exchange Rates Fixed?" and address it with analysis familiar in exchange-rate economics. Stablecoins solve the volatility problem by pegging to a national currency, typically the US dollar, and are used as vehicles for exchanging national currencies into non-stable cryptocurrencies, with some stablecoins having a ratio of trading volume to outstanding supply exceeding one daily. Using a rich dataset of signed trades and order books on multiple exchanges, we examine how peg-sustaining arbitrage stabilizes the price of the largest stablecoin, Tether. We find that stablecoin issuance, the closest analogue to central-bank intervention, plays only a limited role in stabilization, pointing instead to stabilizing forces on the demand side. Following Tether’s introduction to the Ethereum blockchain in 2019, we find increased investor access to arbitrage trades, and a decline in arbitrage spreads from 70 to 30 basis points. We also pin down which fundamentals drive the two-sided distribution of peg- price deviations: Premiums are due to stablecoins’ role as a safe haven, exhibiting, for example, premiums greater than 100 basis points during the COVID-19 crisis of March 2020; discounts derive from liquidity effects and collateral concerns. Keywords: Cryptocurrency, stablecoins, fixed exchange rates, monetary policy, intervention JEL Classifications: E5, F3, F4, G15, G18 ∗UC Berkeley Haas School of Business and NBER ([email protected]), and Warwick Business School ([email protected]), respectively.